In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT ________.
To view the policy installation history for each gateway, which tool would an administrator use?
Which two Identity Awareness commands are used to support identity sharing?
Please choose correct command syntax to add an “emailserver1” host with IP address 10.50.23.90 using GAiA management CLI?
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Fill in the blank: An identity server uses a ___________ for user authentication.
Which of the following blades is NOT subscription-based and therefore does not have to be renewed on a regular basis?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Which options are given on features, when editing a Role on Gaia Platform?
Fill in the blank: RADIUS protocol uses ______ to communicate with the gateway.
You have two rules, ten users, and two user groups in a Security Policy. You create database version 1 for this configuration. You then delete two existing users and add a new user group. You modify one rule and add two new rules to the Rule Base. You save the Security Policy and create database version 2. After a while, you decide to roll back to version 1 to use the Rule Base, but you want to keep your user database. How can you do this?
Can a Check Point gateway translate both source IP address and destination IP address in a given packet?
According to Check Point Best Practice, when adding a non-managed Check Point Gateway to a Check Point security solution what object SHOULD be added? A(n):
What Check Point tool is used to automatically update Check Point products for the Gaia OS?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don’t have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
Which information is included in the “Extended Log” tracking option, but is not included in the “Log” tracking option?
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
Fill in the blanks: Default port numbers for an LDAP server is ______ for standard connections and _______ SSL connections.
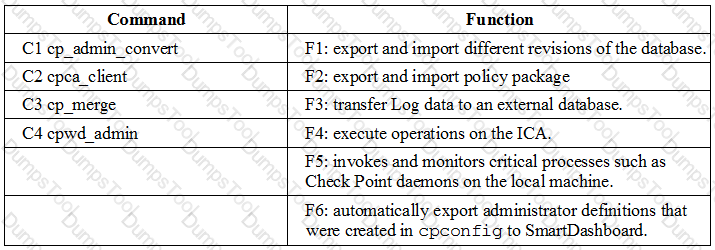
Match the following commands to their correct function. Each command has one function only listed.
What must a Security Administrator do to comply with a management requirement to log all traffic accepted through the perimeter Security Gateway?
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers?
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
Which one of the following is the preferred licensing model? Select the Best answer.
Which of the following uses the same key to decrypt as it does to encrypt?
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
Which of the following is NOT a valid option when configuring access for Captive Portal?
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
During the Check Point Stateful Inspection Process, for packets that do not pass Firewall Kernel Inspection and are rejected by the rule definition, packets are:
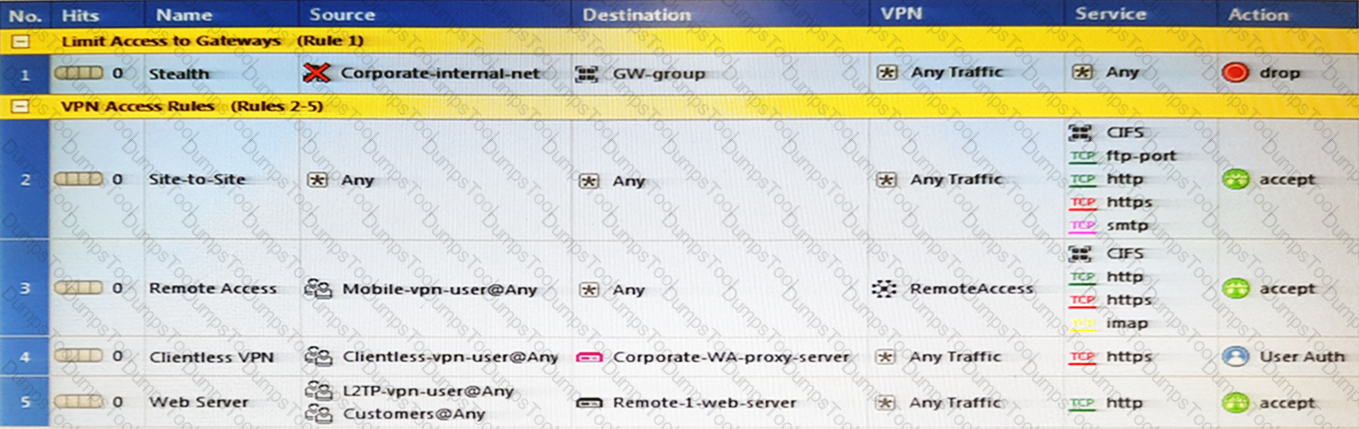
As you review this Security Policy, what changes could you make to accommodate Rule 4?
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
Harriet wants to protect sensitive information from intentional loss when users browse to a specific URL: https://personal.mymail.com, which blade will she enable to achieve her goal?
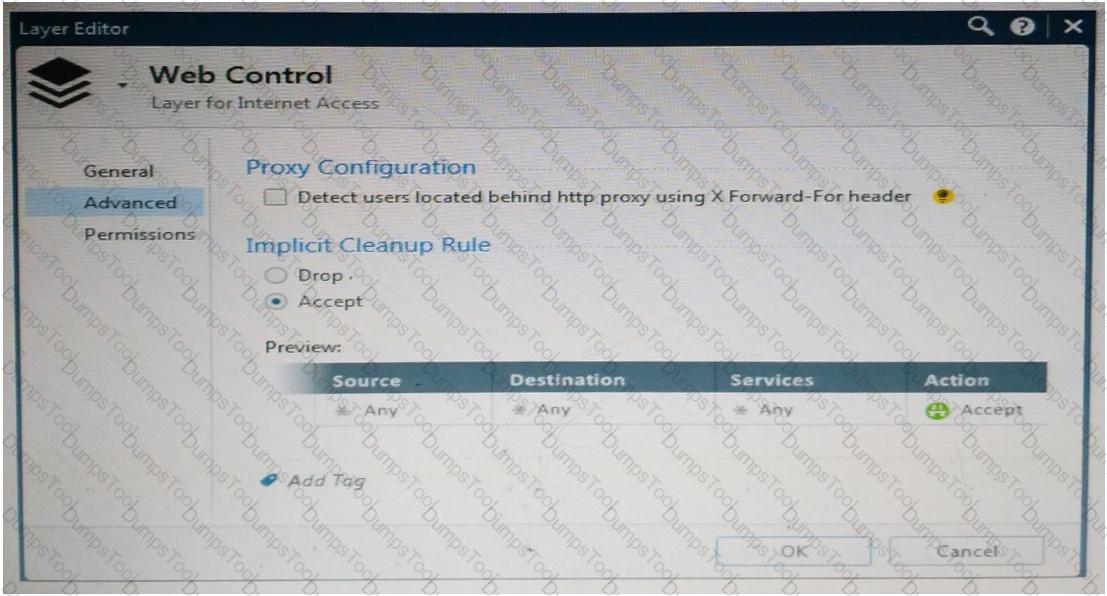
Web Control Layer has been set up using the settings in the following dialogue:
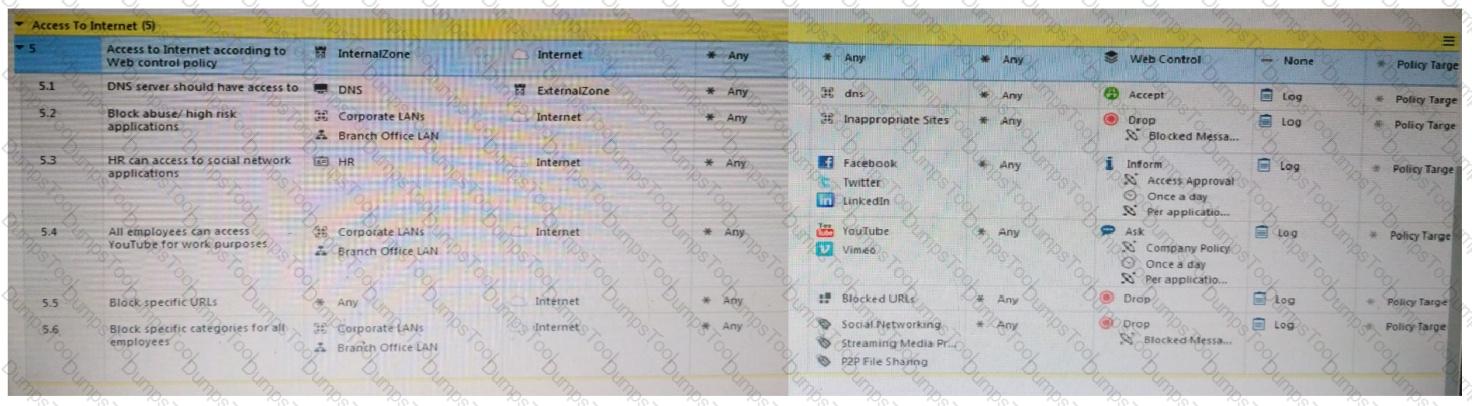
Consider the following policy and select the BEST answer.
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer.
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp.
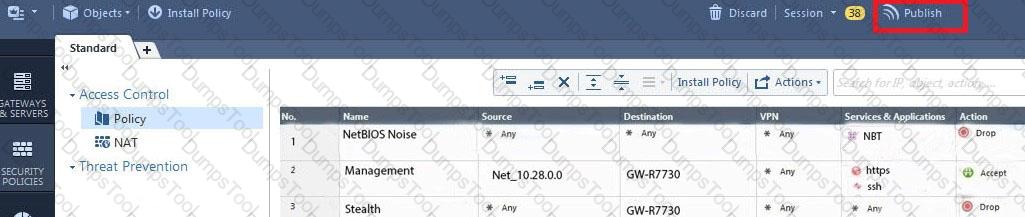
How will you describe the new “Publish” button in R80 Management Console?
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
Which of the following are available SmartConsole clients which can be installed from the R77 Windows CD? Read all answers and select the most complete and valid list.
If there is an Accept Implied Policy set to “First”, what is the reason Jorge cannot see any logs?
Fill in the blank: A(n) _____ rule is created by an administrator and is located before the first and before last rules in the Rule Base.
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
Phase 1 of the two-phase negotiation process conducted by IKE operates in ______ mode.
When attempting to start a VPN tunnel, in the logs the error 'no proposal chosen' is seen numerous times. No other VPN-related log entries are present. Which phase of the VPN negotiations has failed?
Fill in the blank: A _______ is used by a VPN gateway to send traffic as if it were a physical interface.
Which of the following is NOT an element of VPN Simplified Mode and VPN Communities?
What is the potential downside or drawback to choosing the Standalone deployment option instead of the Distributed deployment option?
The security Gateway is installed on GAiA R80 The default port for the WEB User Interface is _______ .
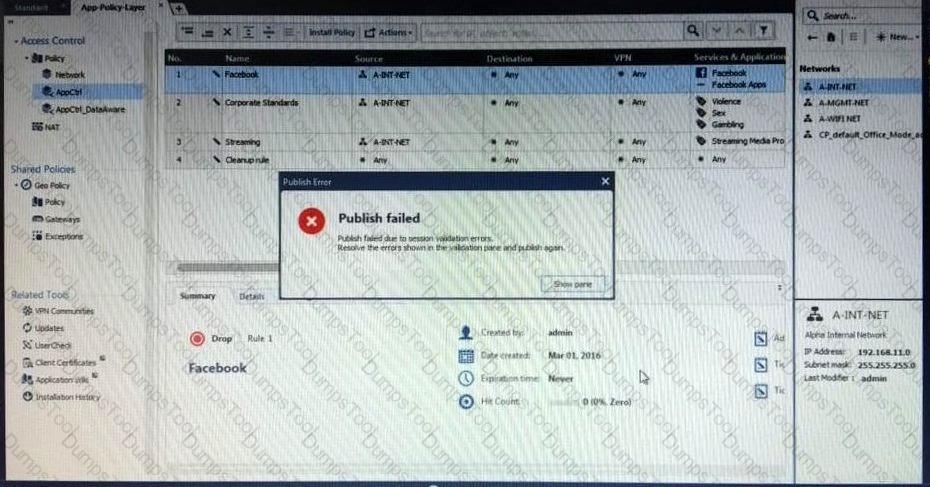
Administrator Kofi has just made some changes on his Management Server and then clicks on the Publish button in SmartConsole but then gets the error message shown in the screenshot below.
Where can the administrator check for more information on these errors?
Fill in the blank: The R80 feature ________ permits blocking specific IP addresses for a specified time period.