You are conducting a security audit. While reviewing configuration files and logs, you notice logs accepting POP3 traffic, but you do not see a rule allowing POP3 traffic in the Rule Base. Which of the following is the most likely cause?
You are using SmartView Tracker to troubleshoot NAT entries. Which column do you check to view the NAT'd source port if you are using Source NAT?
In SmartDashboard, you configure 45 MB as the required free hard-disk space to accommodate logs. What can you do to keep old log files, when free space falls below 45 MB?
Is it possible to track the number of connections each rule matches in a Rule Base?
Your Security Gateways are running near performance capacity and will get upgraded hardware next week. Which of the following would be MOST effective for quickly dropping all connections from a specific attacker’s IP at a peak time of day?
Sally has a Hot Fix Accumulator (HFA) she wants to install on her Security Gateway which operates with GAiA, but she cannot SCP the HFA to the system. She can SSH into the Security Gateway, but she has never been able to SCP files to it. What would be the most likely reason she cannot do so?
A third-shift Security Administrator configured and installed a new Security Policy early this morning. When you arrive, he tells you that he has been receiving complaints that Internet access is very slow. You suspect the Security Gateway virtual memory might be the problem. Which SmartConsole component would you use to verify this?
Which of the following describes the default behavior of an R77 Security Gateway?
Exhibit:

You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office.
What is the correct order for pushing SIC certificates to the Gateway before shipping it?
The INSPECT engine inserts itself into the kernel between which two OSI model layers?
Which of the following uses the same key to decrypt as it does to encrypt?
You can include External commands in SmartView Tracker by the menu Tools > Custom Commands.
The Security Management Server is running under GAiA, and the GUI is on a system running Microsoft Windows. How do you run the command traceroute on an IP address?
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources’ servers should have its own Policy Package. These rules must be installed on this machine and not on the Internet Firewall.
How can this be accomplished?
You enable Hide NAT on the network object, 10.1.1.0 behind the Security Gateway’s external interface. You browse to the Google Website from host, 10.1.1.10 successfully. You enable a log on the rule that allows 10.1.1.0 to exit the network.
How many log entries do you see for that connection in SmartView Tracker?
Your bank’s distributed R77 installation has Security Gateways up for renewal.
Which SmartConsole application will tell you which Security Gateways have licenses that will expire within the next 30 days?
Your Security Management Server fails and does not reboot. One of your remote Security Gateways managed by the Security Management Server reboots.
What occurs with the remote Gateway after reboot?
Which of the following commands can provide the most complete restoration of a R77 configuration?
You plan to create a backup of the rules, objects, policies, and global properties from an R77 Security Management Server. Which of the following backup and restore solutions can you use?
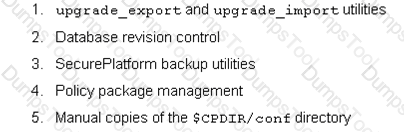
You have created a Rule Base for firewall, websydney. Now you are going to create a new policy package with security and address translation rules for a second Gateway. What is TRUE about the new package’s NAT rules?
Exhibit:
Which command allows Security Policy name and install date verification on a Security Gateway?
Exhibit:

Of the following, what parameters will not be preserved when using Database Revision Control?
Your perimeter Security Gateway’s external IP is 200.200.200.3. Your network diagram shows:
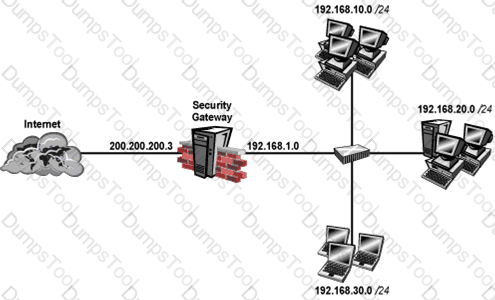
Required. Allow only network 192.168.10.0 and 192.168.20.0 to go out to the Internet, using 200.200.200.5.
The local network 192.168.1.0/24 needs to use 200.200.200.3 to go out to the Internet.
Assuming you enable all the settings in the NAT page of Global Properties, how could you achieve these requirements?
Which SmartView Tracker mode allows you to read the SMTP e-mail body sent from the Chief Executive Officer (CEO) of a company?
Peter is your new Security Administrator. On his first working day, he is very nervous and enters the wrong password three times. His account is locked.
What can be done to unlock Peter’s account? Give the BEST answer.
Which of these components does NOT require a Security Gateway R77 license?
How do you recover communications between your Security Management Server and Security Gateway if you lock yourself out through a rule or policy mis-configuration?
You are working with multiple Security Gateways that enforce an extensive number of rules. To simplify security administration, which one of the following would you choose to do?
In a distributed management environment, the administrator has removed all default check boxes from the Policy > Global Properties > Firewall tab. In order for the Security Gateway to send logs to the Security Management Server, an explicit rule must be created to allow the Security Gateway to communicate to the Security Management Server on port ______.
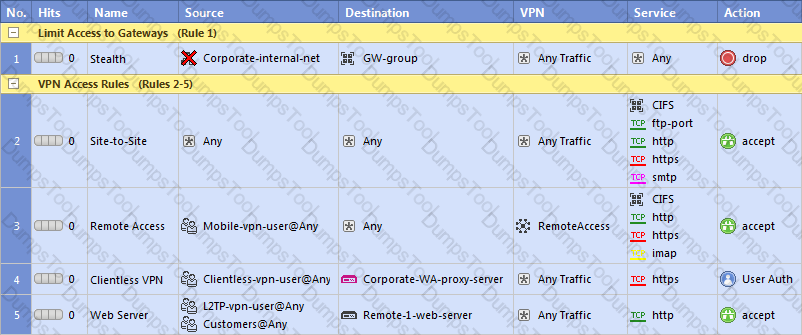
As you review this Security Policy, what changes could you make to accommodate Rule 4?
Exhibit:
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server and backups of your Security Management Server.
What is the correct procedure for rebuilding the Gateway quickly?
Which of the following statements accurately describes the command snapshot?
You need to back up the routing, interface, and DNS configuration information from your R77 GAiA Security Gateway. Which backup-and-restore solution do you use?
To check the Rule Base, some rules can be hidden so they do not distract the administrator from the unhidden rules. Assume that only rules accepting HTTP or SSH will be shown. How do you accomplish this?
Which command would provide the most comprehensive diagnostic information to Check Point Technical Support?
You need to completely reboot the Operating System after making which of the following changes on the Security Gateway? (i.e. the command cprestart is not sufficient.)
1. Adding a hot-swappable NIC to the Operating System for the first time.
2. Uninstalling the R77 Power/UTM package.
3. Installing the R77 Power/UTM package.
4. Re-establishing SIC to the Security Management Server.
5. Doubling the maximum number of connections accepted by the Security Gateway.
Over the weekend, an Administrator without access to SmartDashboard installed a new R77 Security Gateway using GAiA. You want to confirm communication between the Gateway and the Management Server by installing the Security Policy. What might prevent you from installing the Policy?
In a distributed management environment, the administrator has removed the default check from Accept Control Connections under the Policy > Global Properties > FireWall tab. In order for the Security Management Server to install a policy to the Firewall, an explicit rule must be created to allow the server to communicate to the Security Gateway on port ______.
What CLI utility allows an administrator to capture traffic along the firewall inspection chain?
Study the Rule base and Client Authentication Action properties screen -
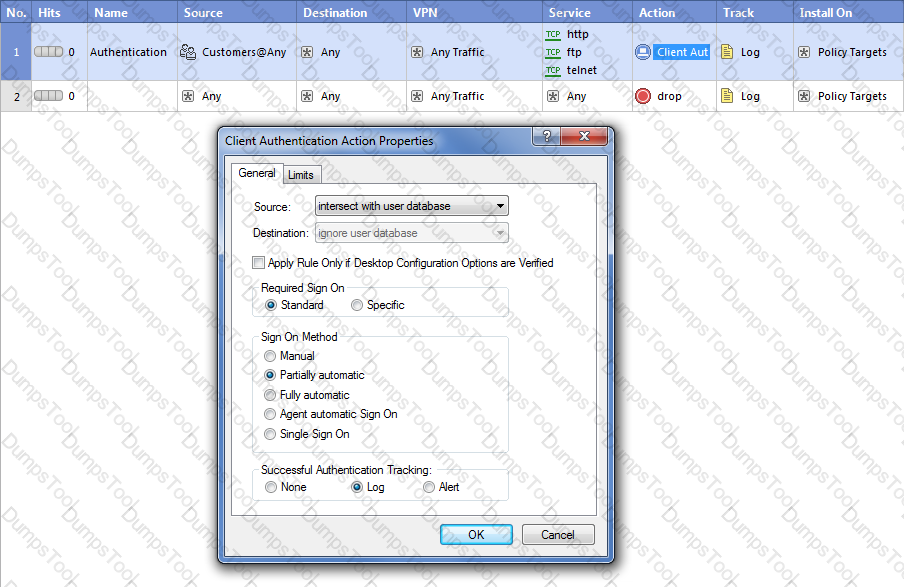
After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user?
Which port must be allowed to pass through enforcement points in order to allow packet logging to operate correctly?
Which of the following are available SmartConsole clients which can be installed from the R77 Windows CD? Read all answers and select the most complete and valid list.