A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset:
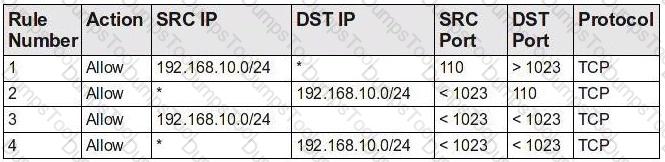
Which choice describes the next step to take now that this ruleset has been enabled?
At the beginning of an IPsec session, which activity occurs during the Internet Key Exchange (IKE)?
Consider the following image of a packet capture:
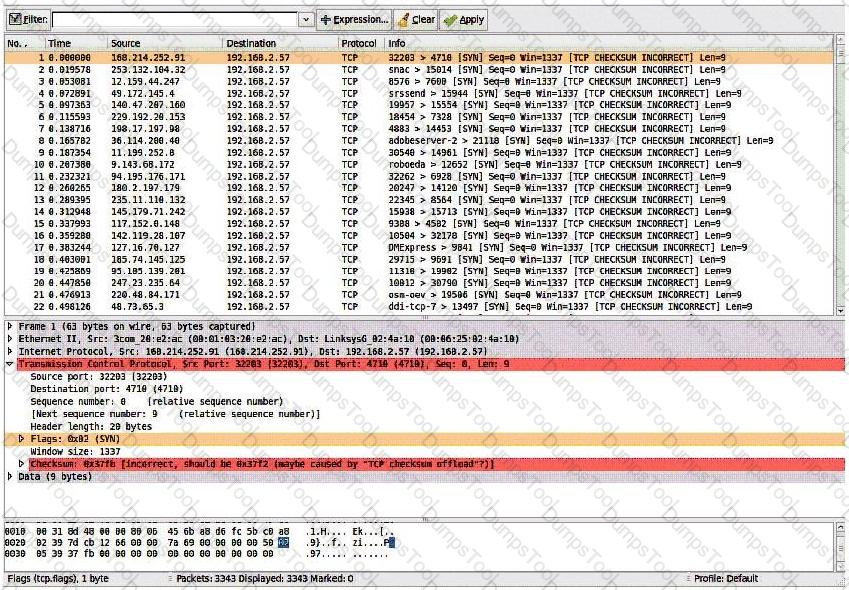
This packet capture has recorded two types of attacks. Which choice lists both attack types?