A Developer has created a software package to be deployed on multiple EC2 instances using IAM roles.
What actions could be performed to verify IAM access to get records from Amazon Kinesis Streams? (Select TWO.)
An IAM role is attached to an Amazon EC2 instance that explicitly denies access to all Amazon S3 API actions. The EC2 instance credentials file specifies the IAM access key and secret access key, which allow full administrative access.
Given that multiple modes of IAM access are present for this EC2 instance, which of the following is correct?
A developer is building a highly secure healthcare application using .. application requires writing temporary data to /tmp storage on an AWS Lambda function.
How should the developer encrypt this data?
A three-tier application hosted on AWS uses Amazon RDS for MYSQL as its database. A developer must ensure the database credentials are stored and accessed securely.
What is the MOST secure way for the developer to achieve this?
A developer tested an application locally and then deployed it to AWS Lambda While testing the application remotely the Lambda function fails with an access denied message. How can this issue be addresksed?
A company requires objects that are stored in Amazon S3 to be encrypted The company is currently using server-side encryption with AWS KMS managed encryption keys (SSE-KMS) A developer needs to optimize the cost-effectiveness of the encryption mechanism without negatively affecting performance
What should the developer do to meet these requirements?
A movie fan club hosts a serverless web application in an Amazon S3 bucket. The application uses an AWS Lambda function that is exposed by an Amazon API Gateway API. The function queries an Amazon DynamoDB table to list actors sorted by movie. In the DynamoDB table. Actor is the primary key, Movie is the sort key, and Role and Year are attributes.
In the web application, a developer wants to add a page that is named Phase 1 that lists only the movies that were released between 2008 and 2012. The developer needs to fetch the Phase 1 items in a way that minimizes the impact on the DynamoDB table.
Which solution will meet these requirements?
A company is using Amazon Cognito user pools for sign-up and login functionality for a web application. The company is using Amazon RDS for the application's data persistence and is using Amazon API Gateway and AWS Lambda for the application's API functionality. Users must provide their first name, last name, email address, and phone number to sign up. All API endpoints have a Cognito user pool authorizer to guard against unauthenticated requests.
A developer wants to show a personalized welcome screen to users after they log in. The welcome screen needs to show the user's first name and the user's previous login date. According to company policy. developers who work on the web application cannot store any personally identifiable information in RDS instances.
Which solution should the developer implement to meet these requirements?
An application is running on a cluster of Amazon EC2 instance. While trying to read objects stored within a single Amazon S3 bucket that are encrypted with server-side encryption with AWS KMS managed keys (SSE-KMS), the application receives the following error:
Service : AWSKMS: Status Code: 400: Code : ThrottlingException
Which combination of steps should be taken to prevent this failure? (Select TWO.)
An e-commerce site allows returning users to log in to display customized web pages. The workflow is shown in the image below:

An application is running on EC2 instances. Amazon RDS is used for the database that stores user accounts and preferences. The website freezes or is slow to load while waiting for the login step to complete. The remaining components of the site are well-optimized.
Which of the following techniques will resolve this issue? (Select Two.)
A company is migrating a single-server, on-premises web application to AWS. The company intends to use multiple servers behind an Elastic Load Balancer (ELB) to balance the load, and will also store session data in memory on the web server. The company does not want to lose that session data if a server fails or goes offline, and it wants to minimize user’s downtime.
Where should the company move session data to MOST effectively reduce downtime and make users’ session data more fault tolerant?
A developer is creating a serverless application that uses an AWS Lambda function. The developer will use AWS Cloud Formation to deploy the application. The application will write logs to Amazon 3loudWatch Logs. The developer has created a log group in a Cloud Format ion template for the application to use. The developer needs to modify the CloudFormation template to make the name of the log [jroup available to the application at runtime.
Which solution will meet this requirement?
A developer is attempting to use the Amazon S3 PutObject API operation to upload an object to an S3 bucket that has default encryption enabled. The developer receives a 400 Bad Request error.
What is the MOST likely cause of this error?
A company has an internal website that gives users the ability to access contract Idata that is stored in an Amazon RDS DB instance The number of contracts has increased and several users have reported slow retrieval of the contract data
The company wants to set up a cache to improve the latency A developer must create a solution that ensures data resiliency The data must be encrypted and must be partitioned by department
Which solution will meet these requirements?
A company has three AWS Lambda functions that are written in Node js The Lambda functions include a mix of custom code and open-source modules When bugs are occasionally detected in the open-source modules, all three Lambda functions must be patched.
What is the MOST operationally efficient solution to deploy a patched open-source library for all three Lambda functions?
A developer from AnyCompany's AWS account needs access to the Example Corp AWS account AnyCompany uses an identity provider that is compatible with OpenID Connect.
What is the MOST secure way for Example Corp to allow developer access?
A company has a three-tier application that is deployed in Amazon Elastic Container Service (Amazon ECS). The application is using an Amazon RDS for MySQL DB Instance The application performs more database reads than writes.
During times of peak usage. the application's performance degrades. When this performance degradation occurs, the DB instance's ReadLatency metric in Amazon CloudWatch increases suddenly
How should a developer modify the application to improve performance?
A developer is creating a role to access Amazon S3 buckets To create the role, the developer uses the AWS CLI create-role command. Which policy should be added to allow the Amazon EC2 service to assume the role?
A developer converted an existing program to an AWS Lambda function in the console. The program runs properly on a local laptop, but shows an "Unable to import module" error when tested in the Lambda console
Which of the following can fix the error?
A developer is building a new application that uses an Amazon DynamoDB table. The specification states that all items that are older than 48 hours must be removed
Which solution will meet this requirement?
A developer implemented a static website hosted in Amazon S3 that makes web service requests hosted in Amazon API Gateway AWS Lambda. The site is showing an error that reads
"No ' Access-Control-Allow Origin' header is present on the requested resource Origin 'null' is therefore not allowed access " What should the developer do to resolve this issue?
A company's fleet of Amazon EC2 instances receives data from millions of users through an API. The servers batch the data, add an object for each user, and upload the objects to an S3 bucket to ensure high access rates The object attributes are Customer ID, Server ID, TS-Server (TimeStamp and Server ID) the size of the object, and a timestamp A developer wants to find all the objects for a given user collected during a specified time range
After creating an S3 object created event, how can the developer achieve this requirement^
A company has a web application In an Amazon Elastic Container Service (Amazon ECS) cluster running hundreds of secure services in AWS Fargate containers. The services are in target groups routed by an Application Load Balancer (ALB) Application users log in to the website anonymously, but they must be authenticated using any OpenID Connect protocol-compatible identity provider (IdP) to access the secure services
Which authentication approach would meet these requirements with the LEAST amount of effort?
A company has an AWS Lambda function that runs hourly, reads log files that are stored in Amazon S3, and forwards alerts to Amazon Simple Notification Service (Amazon SNS) topics based on content A developer wants to add a custom metric to the Lambda function to track the number of alerts of each type for each run The developer needs to log this information in Amazon CloudWatch in a metnc that is named Lambda/AlertCounts
How should the developer modify the Lambda function to meet this requirement with the LEAST operational overhead1?
A development team is building a new application that will run on Amazon EC2 and use Amazon DynamoDB as a storage layer The developers all have assigned IAM user accounts in the same IAM group The developers currently can launch EC2 instances and they need to be able to launch EC2 instances with an instance role allowing access to Amazon DynamoDB.
Which AWS I AM changes are needed when creating an instance role to provide this functionality^
A developer is trying to monitor an application's status by running a cron job that returns 1 if the service is up and 0 if the service is down. The developer created code that uses an AWS CLI put-metric-alarm command to publish the custom metrics to Amazon CloudWatch and create an alarm However the developer is unable to create an alarm as the custom metrics do not appear m the CloudWatch console.
What is causing this issue?
A developer Is working with a Docker application that needs to be quickly deployed using AWS without changing the infrastructure or configuring health checks. The application should be configured so that changes and updates can be made automatically without any downtime
Which solution will meet these requirements?
An application is processing clickslream data using Amazon Kinesis. The clickstream data feed into Kinesis experiences periodic spikes. The PutRecords API call occasionally fails and the logs show that the failed call returns the response shown below.
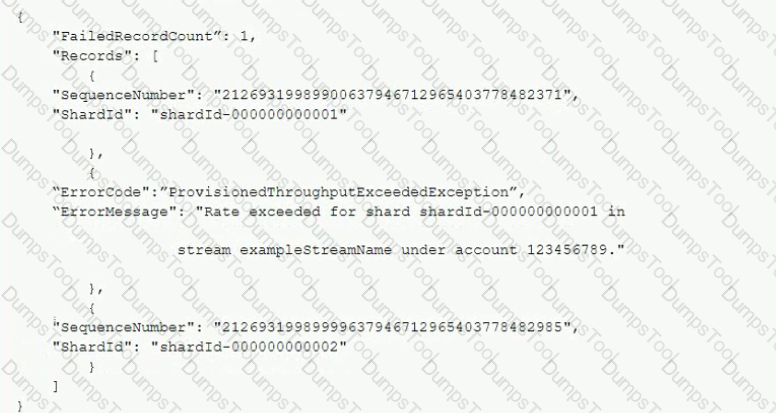
Which techniques will help mitigate this exception? (Select TWO.)
A developer is using AWS CodeDeploy to automate a company's application deployments to Amazon EC2.
Which application specification file properties are required to ensure the software deployments do not fail? {Select TWO.)
A company is concerned that a malicious user could deploy unauthorized changes to the code for an AWS Lambda function. What can a developer do to ensure that only trusted code is deployed to Lambda?
A company has a serverless application that uses AWS Lambda functions and AWS Systems Manager parameters to store configuration data. The company moves the Lambda functions inside the VPC and into private subnets. The Lambda functions are now producing errors in their attempts to access Systems Manager parameters.
Which solution will allow the Lambda functions to access Systems Manager parameters inside the VPC?
A company has an online order website that uses Amazon DynamoDB to store item inventory. A sample of the inventory object is as follows:
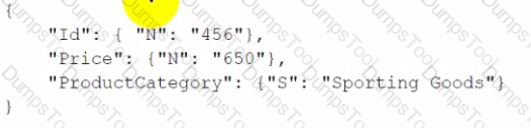
A developer needs to reduce all inventory prices by 100 as long as the resulting price would not be less than 500. What should the developer do to make this change with the LEAST number of calls to DynamoDB?
A developer has built an application running on AWS Lambda using AWS Serverless Application Model (AWS SAM).
What is the correct sequence of steps to successfully deploy the application?
A developer is writing a web application that allows users to sign in. The application will run on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances will run in an Auto Scaling group across multiple Availability Zones.
How can the developer ensure that users stay signed in when the Auto Scaling group is scaled down?
A company that has multiple offices uses an Amazon DynamoDB table to store employee payroll information. Item attributes consist of employee names, office identifiers, and cumulative daily hours worked. The most frequently used query extracts a report of an alphabetical subset of employees for a specific office.
Which design of the DynamoDB table primary key will have the MINIMUM performance impact?
A company is building a serverless application that uses AWS Lambda. The application includes Lambda functions that are exposed by Amazon API Gateway The functions will use several large third-party libraries, and the build artifacts will exceed 50 MB in size.
Which combination of steps should a developer take to prepare and perform the deployment? (Select TWO.)
A developer wants to implement authentication using Amazon Cognito user pools for an existing API in Amazon API Gateway. After creating the Amazon Cognito user pool, the developer tests the GET request to the API. Unauthenticated requests to the API return a 200 OK status response.
Which combination of additional steps are required to complete the authentication implementation? (Select TWO.)
A company is expanding the compatibility of its photo-sharing mobile app to hundreds of additional devices with unique screen dimensions and resolutions. Ph are stored in Amazon S3 in their original format and resolution. The company uses an Amazon CloudFront distribution to serve the photos. The app includes th dimension and resolution of the display as GET parameters with every request.
A developer needs to implement a solution that optimizes the photos that are served to each device to reduce load time and increase photo quality.
Which solution will meet these requirements MOST cost-effectively?
A developer is migrating to Amazon Cognito from a custom user management solution that stores user information in a database. The developer has created a…… Amazon Cognito user pool. The developer needs to migrate the existing user information to the user pool without forcing users to change their passwords.
Which solution will meet these requirements?
A developer is migrating a Windows-based legacy application from on premises to AWS. The application will run on Amazon EC2 instances that run Amazon Linux. The application stores a large number of files in an NFS drive. The migration solution must minimize downtime and application code changes.
Which solution should the developer use to migrate the application data?
A development team set up a pipeline to launch a test environment. The developers want to automate tests for their application. The team created an AWS CodePipeline stage to deploy the application to a test environment in batches using AWS Elastic Beanstalk. A later CodePipeline stage contains a single action that uses AWS CodeBuild to run numerous automated Selenium-based tests on the deployed application. The team must speed up the pipeline without removing any of the individual tests.
Which set of actions will MOST effectively speed up application deployment and testing?
A developer is creating a photo website. Amazon Route 53 hosts the website's domain. The developer wants to store the application code and images in an Amazon S3 bucket. The developer also wants to jse Amazon CloudFront to deliver the images to users.
the developer has created the S3 bucket and a CloudFront distribution. The developer wants the images to be accessed only through the website's domain. Users must not use the S3 URLs.
Which solution will meet these requirements?
A company is using an Amazon API Gateway REST API endpoint as a webhook lo publish events from an on-premises source control management (SCM) system to Amazon EventBridge. The company has configured an EventBridge rule to listen for the events and to control application deployment m a central AWS account. The company needs to receive the same events across multiple receiver AWS accounts
How can a developer meet these requirements without changing the configuration of the SCM system?
A developer has created a Java application that makes HTTP requests directly to AWS services. Application logging shows 5xx HTTP response codes that occ irregular intervals. The errors are affecting users.
How should the developer update the application to improve the application's resiliency?
A developer has an application container, an AWS Lambda function, and an Amazon Simple Queue Sen/ice (Amazon SOS) queue. The Lambda function uses the SOS queue as an event source. The Lambda function makes a call to a third-party machine learning API when the function is invoked. The response from the third-party API can take up to 60 seconds to return.
the Lambda function's timeout value is currently 65 seconds. The developer has noticed that the Lambda function sometimes processes duplicate messages from the SOS queue.
What should the developer do to ensure that the Lambda function does not process duplicate messages?
A developer is designing a serverless application for an ecommerce website. An Amazon API Gateway API exposes.....
user operations. The website features shopping carts for the users. The shopping carts must be stored for extended..... the front-end application.
The load on the application will vary significantly based on the time of day and the promotional sales that are offered..... scale automatically to meet these changing demands.
Which solution will meet these requirements?
A Developer decides lo store highly secure data in Amazon S3 and wants to implement server-side encryption (SSF) with granular control of who can access the master key Company policy requires that the master key be created, rotated, and disabled easily when needed, all for security reasons.
Which solution should be used to moot these requirements?
A developer wants to build an application that will allow new users to register and create new user accounts. The application must also allow users with social media accounts to log in using their social media credentials.
Which AWS service or feature can be used to meet these requirements?
A company needs to distribute firmware updates to its customers around the world.
Which service will allow easy and secure control of the access to the downloads at the lowest cost?
A Developer is creating a template that uses AWS CloudFormation to deploy an application. This application is serverless and uses Amazon API Gateway, Amazon DynamoDB, and AWS Lambda.
Which tool should the Developer use to define simplified syntax for expressing serverless resources?
An AWS Lambda function must access an external site by using a regularly rotated user name and password. These items must be kept securely and cannot be stored in the function code.
What combination of AWS services can be used to accomplish this? (Choose two.)
A company is running a Docker application on Amazon ECS. The application must scale based on user load in the last 15 seconds.
How should a Developer instrument the code so that the requirement can be met?
A developer wants to ensure the Amazon EC2 instances in AWS Elastic Beanstalk execute a certain set of commands before the application is ready to use Which Elastic Beanstalk feature will allow the developer to accomplish this?
A Developer wants to upload data to Amazon S3 and must encrypt the data in transit.
Which of the following solutions will accomplish this task? (Choose two.)
An AWS Lambda function generates a 3MB JSON file and then uploads it to an Amazon S3 bucket daily. The file contains sensitive information, so the Developer must ensure that it is encrypted before uploading to the bucket.
Which of the following modifications should the Developer make to ensure that the data is encrypted before uploading it to the bucket?
A Developer is developing an application that manages financial transactions. To improve security, multi-factor authentication (MFA) will be required as part of the login protocol.
What services can the Developer use to meet these requirements?
You run an ad-supported photo sharing website using S3 to serve photos to visitors of your site. At some point you find out that other sites have been linking to the photos on your site, causing loss to your business.
What is an effective method to mitigate this?
An organization is using Amazon API Gateway to provide a public API called "Survey" for collecting user feedback posts about its products The survey API has "DEV" and "PROD" stages and consists of one resource "/feedback" which allows users to retrieve/create/update single feedback posts.
Aversion-controlled Swagger file is used to define a new API that retrieves multiple feedback posts To add the new API resource "/listFeedbackForProduct" the developer makes changes to the Swagger file defining an API uploads the fie to the organization's version control system, and uses the API Gateway Import API feature to apply the changes to the Survey API After successful import the developer runs the tests against the DEV stage and finds that resource VlistFeedbackForProduct" is not available.
What is MOST likely the reason for resource not being available?
A developer is creating an application to process a large number of requests Requests must be processed in order, and each request should be processed only once How should Amazon SQS be deployed to achieve this?
A company is building a compute-intensive application that will run on a fleet of Amazon EC2 instances. The application uses attached Amazon EBS disks for storing data. The application will process sensitive information and all the data must be encrypted.
What should a developer do to ensure the data is encrypted on disk without impacting performance?
A developer is writing a new serverless application for a company. Several other developers must collaborate on the code for this application, and the company expects frequent changes to the code. The developer needs to deploy the code from source control to AWS Lambda with the fewest number of manual steps.
Which strategy for the build and deployment should the developer use to meet these requirements?
A developer is working on an AWS Lambda function that accesses Amazon DynamoDB The Lambda function must retrieve an item and update some of its attributes. or create the item if it does not exist The Lambda function has access to the primary key.
Which IAM permissions should the developer request for the Lambda function to achieve this functionality?
A developer is testing a Docker-based application that uses the AWS SDK to interact with Amazon DynamoDB In the local development environment, the application has used IAM access keys The application is now ready for deployment onto an ECS duster.
How should the application authenticate with AWS services in production?
A Developer created a new AWS account and must create a scalable AWS Lambda function that meets the following requirements for concurrent execution:
Which step must be taken prior to deployment to prevent errors?
An application is being developed to audit several AWS accounts. The application will run in Account A and must access AWS services in Accounts B and C.
What is the MOST secure way to allow the application to call AWS services in each audited account?
A developer is writing a web application that must share secure documents with end users The documents are stored in a private Amazon S3 bucket The application must allow only authenticated users to download specific documents when requested, and only for a duration of 15 minutes
How can the developer meet these requirements?
The upload of a 15 GB object to Amazon S3 fails. The error message reads: “Your proposed upload exceeds the maximum allowed object size.”
What technique will allow the Developer to upload this object?
A developer has built an application running on AWS Lambda using AWS Serverless Application Model (AWS SAM). What is the correct order of execution to successfully deploy the application?
A development team wants to immediately build and deploy an application whenever there is a change to the source code. Which approaches could be used to trigger the deployment? (Select TWO.)
A company is migrating from a monolithic architecture to a microservices-based architecture. The Developers need to refactor the application so that the many microservices can asynchronously communicate with each other without impacting performance.
Use of which managed AWS services will enable asynchronous message passing? (Choose two.)
NO:
A developer is setting up Amazon API Gateway for their company's products The API will be used by registered developers to query and update their environments. The company wants to limit the amount of requests end users can send for both cost and security reasons Management wants to offer registered developers the option of buying larger packages that allow for more requests.
How can the developer accomplish this with the LEAST amount of overhead management?
A developer needs to create an application that supports Security Assertion Markup Language (SAML) and Facebook authentication It must also allow access to AWS services, such as Amazon DynamoDB.
Which AWS service or feature will meet these requirements with the LEAST amount of additional coding?
A Developer is building a three-tier web application that should be able to handle a minimum of 5000 requests per minute. Requirements state that the web tier should be completely stateless while the application maintains session state for the users.
How can session data be externalized, keeping latency at the LOWEST possible value?
An on-premises legacy application is caching data files locally and writing shared images to local disks.
What is necessary to allow for horizontal scaling when migrating the application to AWS?
A developer is preparing a deployment package using AWS Cloud Formation. The package consists of two separate templates: one for the infrastructure and one for the application. The application has to be inside the VPC that is created from the infrastructure template
How can the application stack refer to the VPC created from the infrastructure template?
A startup s photo-sharing site is deployed in a VPC. An ELB distributes web traffic across two subnets. ELB session stickiness is configured to use the AWS-generated session cookie, with a session TTL of 5 minutes. The webserver Auto Scaling Group is configured as: min-size=4, max-size=4.
The startups preparing for a public launch, by running load-testing software installed on a single EC2 instance running in us-west-2a. After 60 minutes of load-testing, the webserver logs show:
Which recommendations can help ensure load-testing HTTP requests are evenly distributed across the four webservers? Choose 2 answers
An application reads data from an Amazon DynamoDB table. Several times a day, for a period of 15 seconds, the application receives multiple ProvisionedThroughputExceeded errors.
How should this exception be handled?
A Developer is writing a Linux-based application to run on AWS Elastic Beanstalk. Application requirements state that the application must maintain full capacity during updates while minimizing cost.
Which type of Elastic Beanstalk deployment policy should the Developer specify for the environment?
A Developer is designing a fault-tolerant environment where client sessions will be saved.
How can the Developer ensure that no sessions are lost if an Amazon EC2 instance fails?
company needs a fully-managed source control service that will work in AWS. The service must ensure that revision control synchronizes multiple distributed repositories by exchanging sets of changes peer-to-peer. All users need to work productively even when not connected to a network.
Which source control service should be used?
Company B provides an online image recognition service and utilizes SQS to decouple system components for scalability The SQS consumers poll the imaging queue as often as possible to keep end-to-end throughput as high as possible. However, Company B is realizing that polling in tight loops is burning CPU cycles and increasing costs with empty responses.
How can Company B reduce the number of empty responses?
A game stores user game data in an Amazon DynamoDB table. Individual users should not have access to other users’ game data. How can this be accomplished?
A Developer is creating a mobile application that will not require users to log in.
What is the MOST efficient method to grant users access to AWS resources?
A Developer wants to use AWS X-Ray to trace a user request end-to-end throughput the software stack. The Developer made the necessary changes in the application tested it, and found that the application is able to send the traces to AWS X-Ray. However, when the application is deployed to an EC2 instance, the traces are not available.
Which of the following could create this situation? (Select two.)
You are inserting 1000 new items every second in a DynamoDB table. Once an hour these items are analyzed and then are no longer needed. You need to minimize provisioned throughput, storage, and API calls.
Given these requirements, what is the most efficient way to manage these Items after the analysis?