How many workdays occur from the start of the Product Testing to the Product Available milestone?
In the normal schedule, excluding Activity 1000. what activity(s) are concurrent with Activity 3001?
Select the most appropriate explanation for use of a winter/wet weather seasonal calendar for use in this project?
The Scope of Work divides the major deliverables into smaller more manageable components for all of the following EXCEPT to:
Which letter of the alphabet best approximates the graphical shape of a project's cumulative cost baseline, or budgeted cost of work scheduled?
In an earned value-based system, a schedule performance index of less than one for the project indicates the project is:
Total float is defined as the amount of time an activity can be delayed without impacting
Scenario: You are providing construction management services for a small office building project. Your duties include reviewing and approving the contractor's baseline schedule. The contractor has submitted the first baseline schedule for the project.
The contractor subsequently submits a CPM schedule for its baseline schedule submittal. As part of your review, you look at the durations for each activity in the schedule. How do you determine if a duration of 10 work days for drywall installation is accurate?
Based on the stated costs, what percentage of the total cost comes from the 2000 series of activities?
The schedule or budget at completion less the estimate at completion is___________.
As a change to the network for the current update, activity 6002 is required to begin ten days after the beginning of activity 6001. Which is the simplest logic organization?
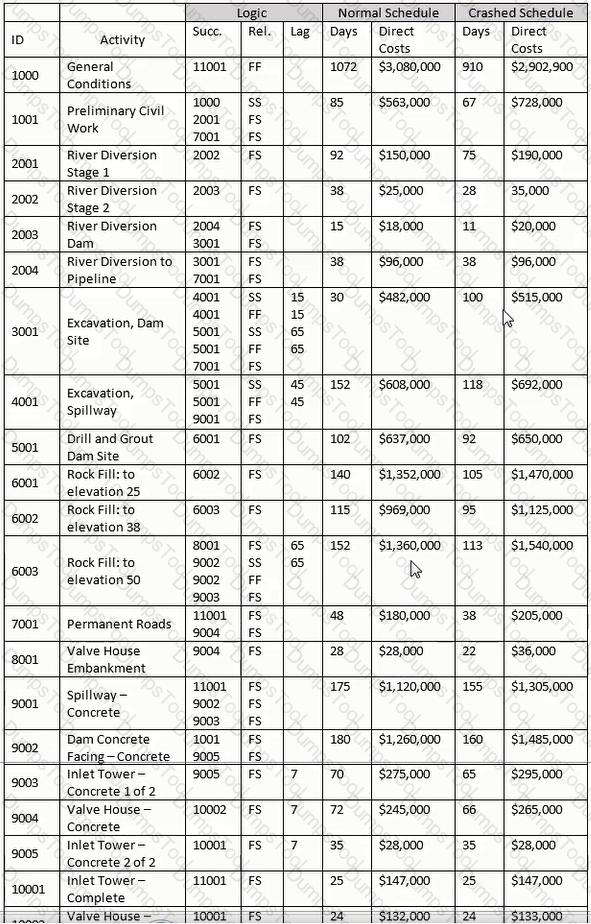
In a "crashed" schedule, which is a chain of activities that precede activity 2004?
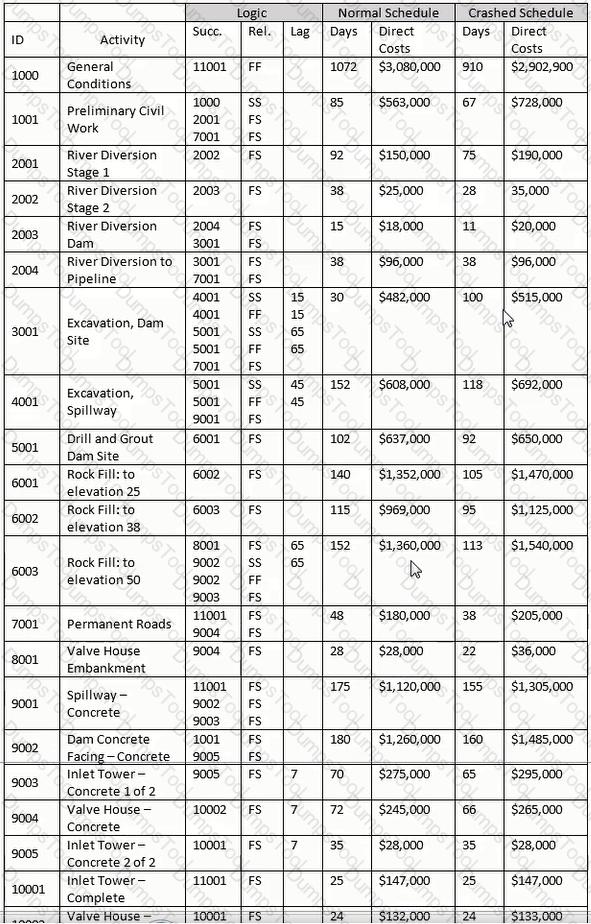
Due to a testing delay, release of the product for manufacture is delayed by 5 workdays and the product manual misses its print window at the printer. If the printer is delayed by 10 workdays, what is the delay to produce release?
If a detailed estimate is NOT available to assist in the formulation of activity durations but unit quantities have been identified, what information can be utilized to estimate work package/activity durations?
When reconstructing a CPM schedule electronically from a hardcopy, which of the following is NOT required to determine the critical path?
Which of the following are NOT considerations or constraints of the planning process for construction scheduling?
When should the project documents be reviewed to assess their impact on the organization and administration of a project?
Which of the following types of delay will NOT result in a time extension and additional compensation for a contractor?
Using the "normal" schedule, what is the early finish date of activity 10002 and its total float?
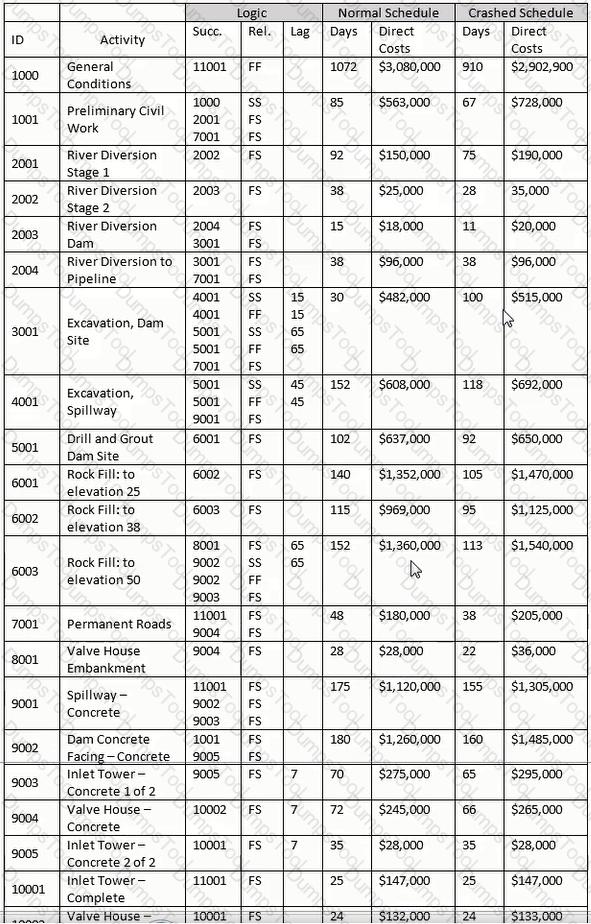
The characteristic of the precedence diagramming method that models construction projects differently than the arrow diagramming method is that it____________.
Scenario: You are providing construction management services for a small office building project. Your duties include reviewing and approving the contractor's baseline schedule. The contractor has submitted the first baseline schedule for the project.
The contractor has included several reports with its submittal, including a report that sorts all activities by total float. What is the value of this report?
During proofing of the product manual, a problem was discovered requiring 15 days additional time to affect a correction. How can the date of availability be maintained?
Using the "normal" schedule, theoretically construct a hammock for activities 6001-6003. What is the duration of the hammock?
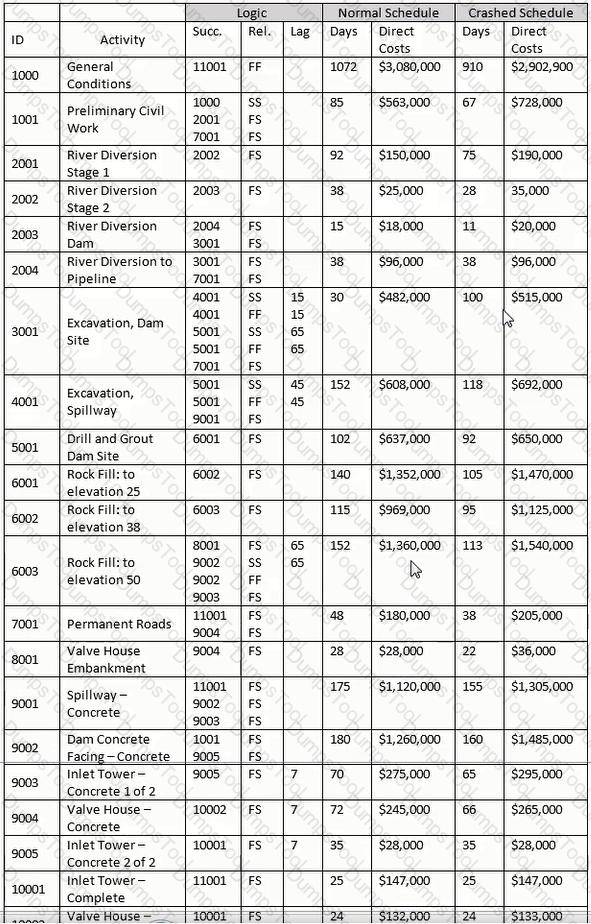
Which of the following will NOT affect the total float calculation of a non-resource leveled schedule?
Using the crashed schedule, if you start Activity 2002 on 12 August 2021. what is the finish date for Activity 2002?
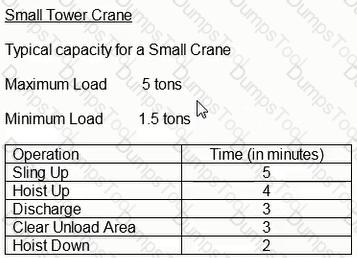
Using one crane capable of 30 lifts per day. for 3 column pours requiring 28 lifts each, plus assorted work in the area requiring an additional 150 lifts, what are the lowest planned workdays for this work?
Assuming activities 2001 through 2004 comprise the same WBS element, construct a WBS summary activity for activities 2001 through 2004. Use the normal schedule, what is the cost of the activity?
The addition of which of the following relationships would cause a logic loop?
Using the "normal" schedule, and assuming you are billing on the last day of the month for previous month and for appropriate partial months, how many invoices will you have for this project?
Using the normal schedule, what is the early finish date and total float of Activity 10002?
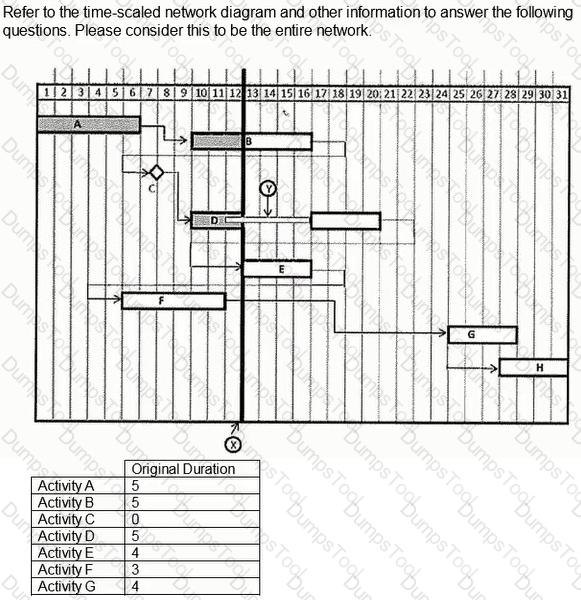
What day would Activity C complete if the duration of Activity A was reduced by five days?
If all other work proceeds according to the Baseline plan, how many times will the critical path change?
What is the actual duration as of the status date or data date of Activity B?
You are the project manager of the AHQ project. This project is scheduled to last for six months and will require S345.000 to complete. If the project completes earlier than scheduled your organization will receive a bonus of S5 000 per day of early completion Management has asked you to develop an aggressive schedule to realize as much of the bonus as possible but management does not want you to increase the costs of the project beyond $1,000 per day of the bonus realization. Which of the following approaches will likely add costs to the project?
Activity durations are normally estimated in an intuitive and subjective way. All of the following will improve duration accuracy EXCEPT
Which of the following are NOT normally included in the project scope statement, either directly or by reference?