What does an attacker use to determine which network ports are listening on a potential target device?
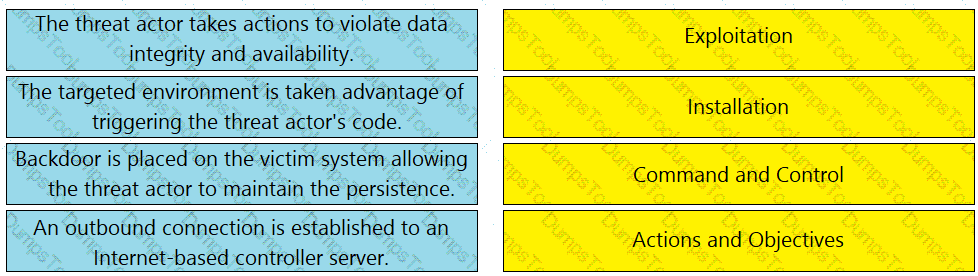
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Refer to the exhibit.
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
Refer to the exhibit.
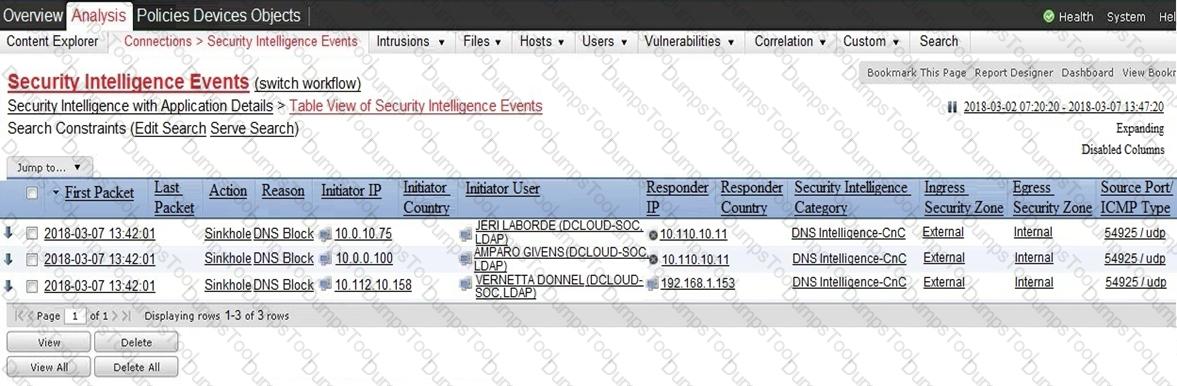
Which two elements in the table are parts of the 5-tuple? (Choose two.)
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
Which metric is used to capture the level of access needed to launch a successful attack?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
What is a collection of compromised machines that attackers use to carry out a DDoS attack?
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
What is the impact of false positive alerts on business compared to true positive?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
Which attack method is being used when an attacker tries to compromise a network with an authentication system that uses only 4-digit numeric passwords and no username?
What is the difference between the rule-based detection when compared to behavioral detection?
Refer to the exhibit.
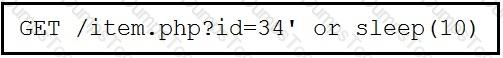
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Which information must an organization use to understand the threats currently targeting the organization?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
A company receptionist received a threatening call referencing stealing assets and did not take any action assuming it was a social engineering attempt. Within 48 hours, multiple assets were breached, affecting the confidentiality of sensitive information. What is the threat actor in this incident?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
Why should an engineer use a full packet capture to investigate a security breach?
Which two components reduce the attack surface on an endpoint? (Choose two.)
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
Which system monitors local system operation and local network access for violations of a security policy?
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
What specific type of analysis is assigning values to the scenario to see expected outcomes?
Which type of data must an engineer capture to analyze payload and header information?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
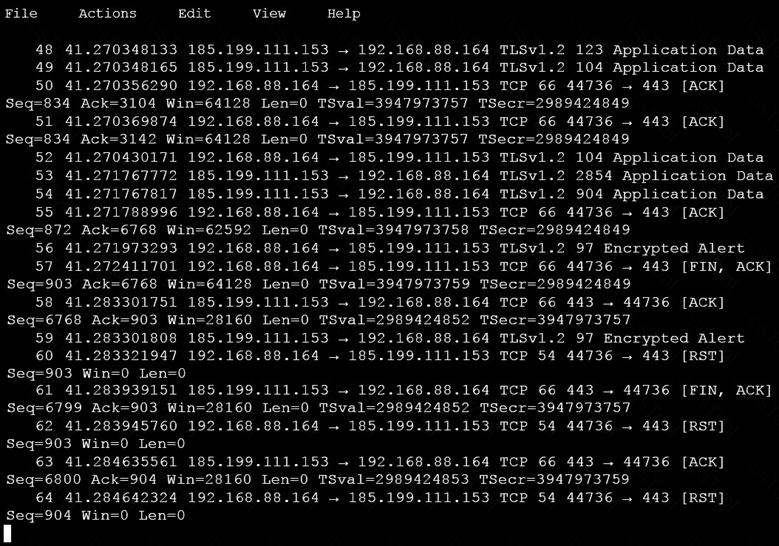
Which obfuscation technique is the attacker using?
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.

Drag and drop the technology on the left onto the data type the technology provides on the right.
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Refer to exhibit.
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
Which type of data consists of connection level, application-specific records generated from network traffic?
What is a difference between signature-based and behavior-based detection?
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Refer to the exhibit.
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?
Drag and drop the elements from the left into the correct order for incident handling on the right.
Refer to the exhibit.
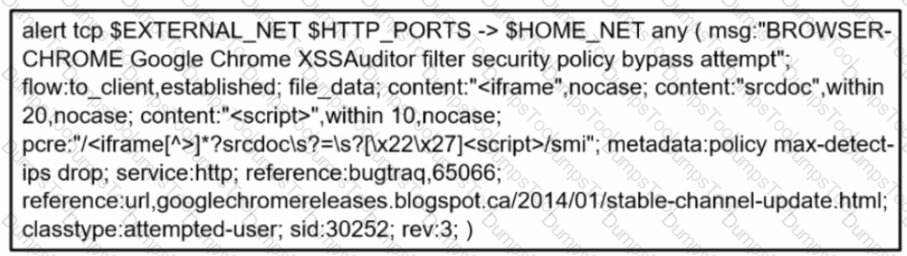
A company's user HTTP connection to a malicious site was blocked according to configured policy What is the source technology used for this measure'?
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
Refer to the exhibit.
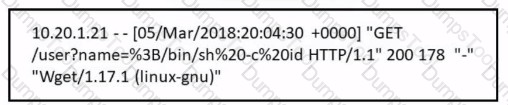
Which attack is being attempted against a web application?
Refer to the exhibit.
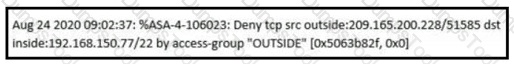
An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
An engineer received a flood of phishing emails from HR with the source address HRjacobm@companycom. What is the threat actor in this scenario?
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
Which regular expression is needed to capture the IP address 192.168.20.232?
What causes events on a Windows system to show Event Code 4625 in the log messages?
Which type of data collection requires the largest amount of storage space?
An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company's website after they register and identify themselves. Which type of protected data is accessed by customers?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
Which step in the incident response process researches an attacking host through logs in a SIEM?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
Refer to the exhibit.
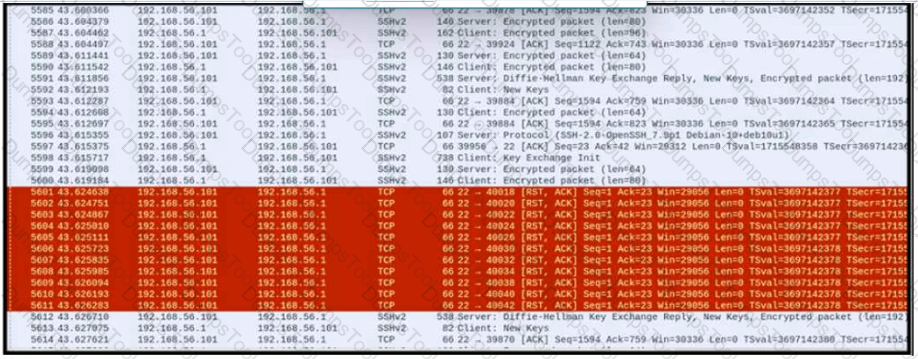
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?