You have a Microsoft Exchange Online tenant.
You plan to use a third-party service to archive all the email messages that are sent and received by the Exchange mailboxes.
You need to copy all the sent and received messages automatically to the third-party service.
What should you configure?
You need to configure the Exchange organization to meet the security requirements for sending email messages to distribution groups.
Which cmdlet should you run?
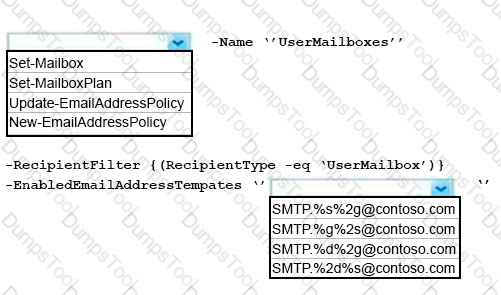
You need to configure the environment to support the planned changes for email addresses.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend an Office 365 solution that meets the technical requirements for email from adatum.com.
Which two components should you recommend configuring from the Exchange admin center in Exchange Online? Each correct presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to recommend a solution for the public folders that supports the planned changes and meets the technical requirements.
What should you recommend?
You must prevent HelpDeskUser1 from repeating the same mistake.
You need to identify which management role provided HelpDeskUser1 with the necessary permissions to make the mistake identified in the problem statement.
Which two cmdlets should you run? Each correct answer presents part of the solution.
You need to recommend a solution that meets the security requirements for protecting users.
What should you recommend?
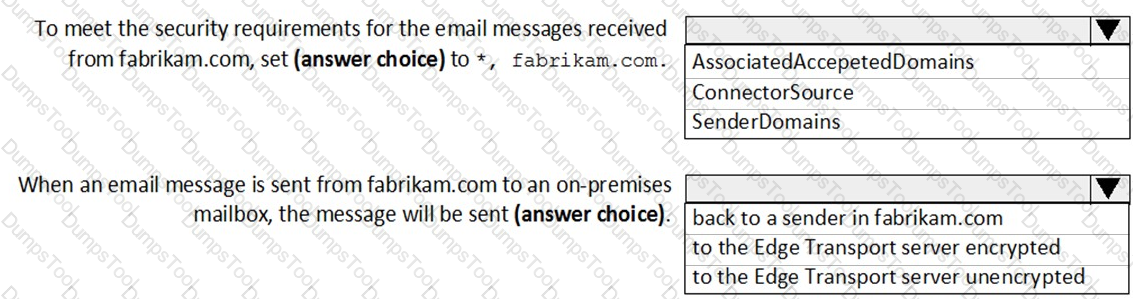
Use the drop-down menus to select the answer choice that complete each statement based on the information presented in the Exchange Online Connector exhibit.
NOTE: Each correct selection is worth one point.
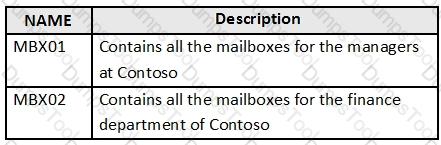
Your company named Contoso, Ltd. has a Microsoft Exchange Server 2019 organization that contains the mailbox databases shown in the following table.
You need to assign an offline address book (OAB) named Managers to all the users in a group named Managers.
How should you complete the PowerShell script? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement a solution that meets the technical requirements for the retention of junk email, sent items, and deleted items.
What is the minimum number of retention policies and retention tags you should use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a procedure for closing the Brussels office that meets the technical requirements.
What should you recommend?
You need to recommend a solution to retain the items in the public folders. The solution must support the
planned changes.
What should you recommend?
Joni Sherman reports that the Microsoft Outlook client on her Windows 10 device fails to start.
You need to troubleshoot the issue.
From the device, you start the Microsoft Remote Connectivity Analyzer.
What should you run next?
You discover that email messages sent to contoso.com are NOT delivered through Contoso Connector.
You need to ensure that all email sent to contoso.com is delivered through Contoso Connector.
Which connector setting should you modify?
Which contacts can sign in to and access resources in the adatum.com tenant?
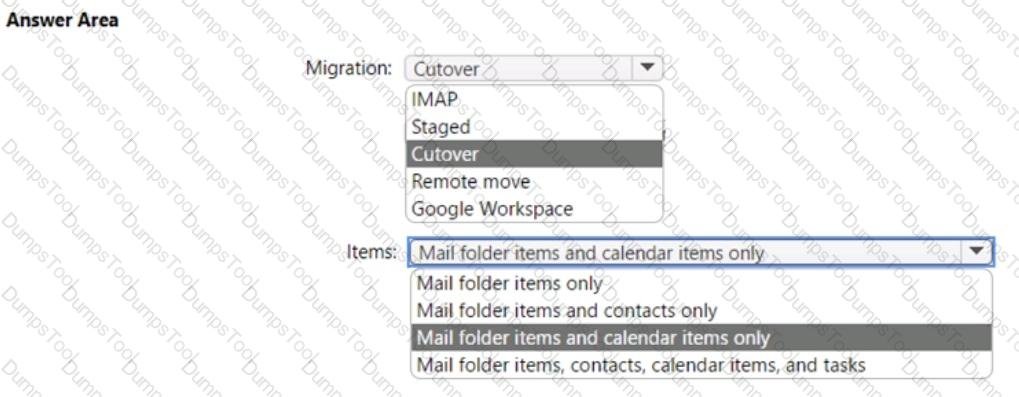
You need to migrate 10 Microsoft Outlook.com users to the adatum.com tenant.
Which type of migration should you perform, and which items can be migrated? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Allan Deyoung must perform a message trace of the email messages sent by Isaiah Langer and provide a report that contains all the messages sent during the last 30 days.
You need to ensure that Allan Deyoung can perform the message trace.
What should you do?
You need to ensure that Allan Deyoung can create a new public folder for the sales department.
Which two actions should you perform first? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You need to ensure that Alex Wilber can recover deleted items when using Outlook on the web.
Which two actions should you perform? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to email a list of configuration changes to the Exchange Online environment that were recently performed by Allan Deyoung.
What should you do?
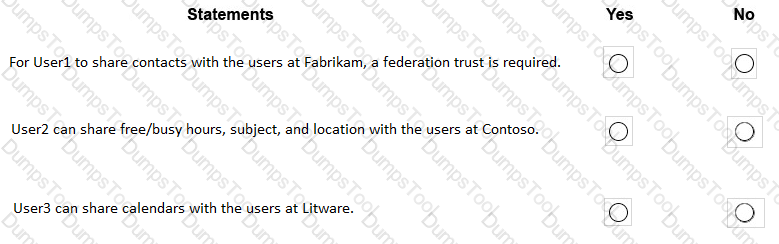
Lynne Robbins and the users in the sales department plan to collaborate on a project with a partner company named Contoso, Ltd. that has an email domain named contoso.com.
You need to ensure that only the sales department users can share all their calendar free/busy
information with the users in contoso.com.
How should you configure the organization relationship?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

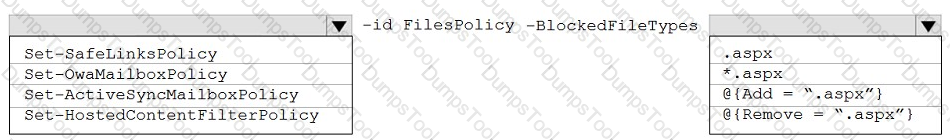
You need to modify FilesPolicy to prevent users from downloading ASPX files. The solution must meet the technical requirements.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to generate a report for the mobile devices that meets the technical requirements.
Which PowerShell cmdlet should you use?
You need to configure the new smartboard to support the planned changes.
Which three settings should you configure? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
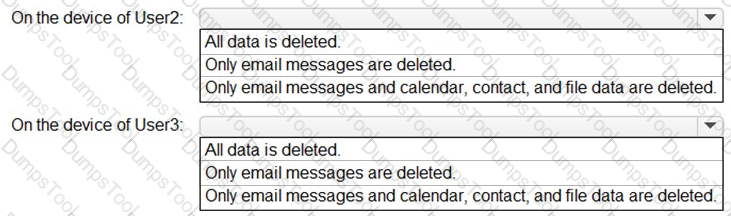
You need to perform a remote wipe of the devices of User2 and User3.
You run the following commands.
Clear-MobileDevice -id User2-Device
-NotificationEmailAddress "admin@Fabrikam.com"
Clear-MobileDevice -id User3-Device
-NotificationEmailAddress "admin@Fabrikam.com"
What occurs on each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
User3 leaves the company.
You need to ensure that Admin1 and Admin2 can access the mailbox of User3. The solution must meet the technical requirements.
What should you do?
You need to encrypt email between Fabrikam and Litware to support the planned changes.
What should you configure in the Exchange admin center?
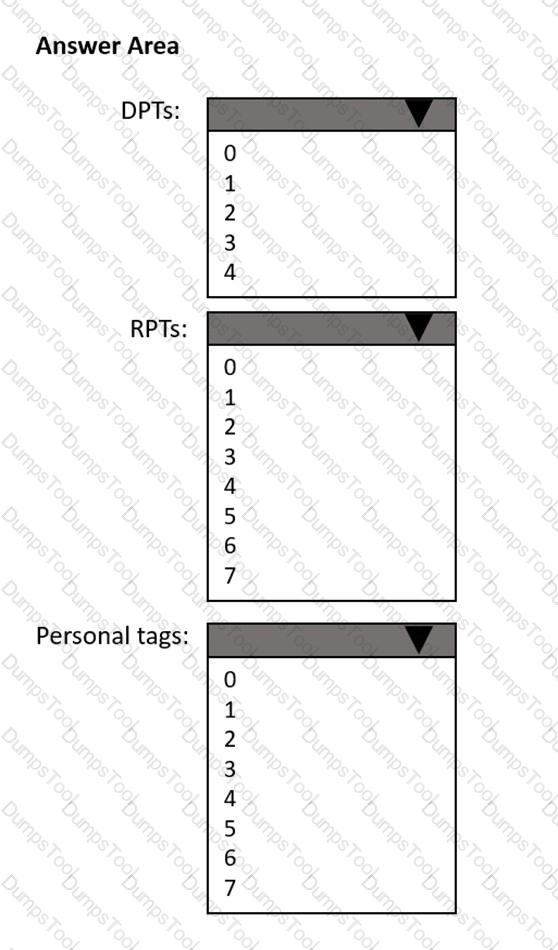
How many default policy tags (DPTs), retention policy tags (RPTs), and personal tags should you create to meet the retention requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to identify which users clicked the links in the phishing emails.
What should you do?
You need to identify the contents of the FabrikamProject public folder to meet the technical requirements.
Which PowerShell cmdlet should you run?
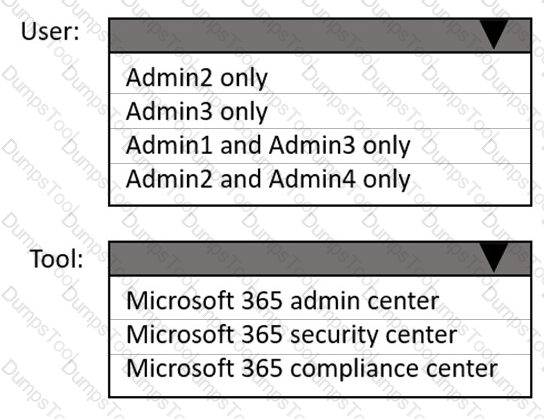
You need to ensure that In-Place Archiving is enabled for the marketing department users.
Which user should perform the change, and which tool should the user use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Online tenant that contains 1,000 mailboxes.
All the users in the sales department at your company are in a group named Sales.
The company is implementing a new policy to restrict the use of email attachments for the users in the Sales group.
You need to prevent all email messages that contain attachments from being delivered to the users in the Sales group.
Solution: You modify the permissions granted to the Sales group.
Does this meet the goal?
You have a Microsoft Exchange Online tenant that contains a user named User1. User1 must perform the following tasks:
• Manage audit logs.
• Track email messages in the Exchange organization.
• Manage transport rules for the Exchange organization.
You need to recommend to which role group to add User1. The solution must follow the principle of least privilege. What should you recommend?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft Exchange Server 2019 organization that contains 200 mailboxes.
You need to add a second email address to each mailbox. The address must have a syntax that uses the first letter of each user’s last name, followed by the user’s first name, and then @fabrikam.com.
Solution: You convert all the mailboxes to shared mailboxes, and then you run the Set-Mailbox cmdlet and specify the –EmailAddressPolicyEnabled $false parameter.
Does this meet the goal?
You have a hybrid deployment of Microsoft Exchange Server 2019.
Users in your company's sales department have on-premises mailboxes and PST files.
You need to migrate the PST files to archive mailboxes. The archive mailboxes must reside in Exchange Online.
What should you do first?
You have a Microsoft Exchange Online tenant.
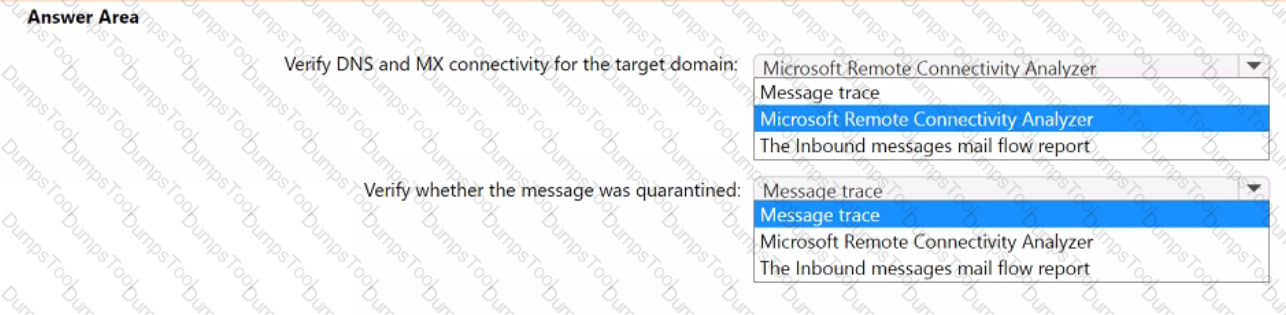
A user reports that an expected email message from an internet recipient was never delivered, and the sender never received a non-delivery report (NDR).
You need to troubleshoot inbound message delivery to meet the following requirements:
• Verify DNS and MX connectivity for the target domain.
• Verify whether the message was quarantined.
What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
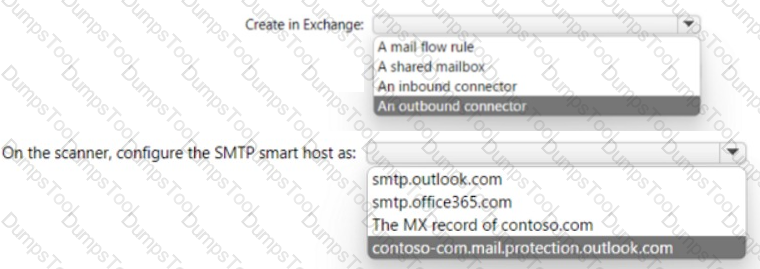
have a Microsoft Exchange Online tenant.
All mailboxes ug a suffix of
All email is routed to and from the tenant through a third-party email filtering service.
You have the following network-connected
You to ensure that the scanners can send email to external recipients via Exchange. solution must NOT require that credentials be from the scanners
You have a Microsoft Exchange Server 2019 organization.
You need to ensure that all email is retained for one year, and then moved to an archive mailbox.
What should you use?
You have a Microsoft Exchange Online tenant.
Users report that legitimate email messages are delivered to their Junk Email folder.
You plan to use the Microsoft Remote Connectivity Analyzer to identify the cause of the issue.
Which test should you run?
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username: admin@abc.com
Microsoft 365 Password: xxxxxx
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only.
Lab Instance: XXXXXX
Users report that email disclaimers are no longer being appended to email messages sent to external recipients.
You need to ensure that all email sent to external recipients contains your corporate disclaimer.
To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft Exchange Online tenant that contains a user named Used.
You need to ensure that User1 is notified whenever mail flow is interrupted for more than one hour.
What should you do in the Exchange admin center?