A security needs to deploy a file named boardconfig.mk to some company devices. the file contains the following information:
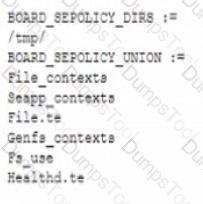
Much of the following represents the goal of this file?
Which of the following is the primary cybersecurity-related difference between the goals of a risk assessment and a business impact analysts?
A software development company recently implemented a new policy and control ruleset. The control ruleset defines the following:
• Account naming standards
• Password complexity standards
• SOLC practices
• Encryption baselines and standards
A review of the current applications used and developed by the company shows many production and mission-critical applications are not compliant with the new policies and control ruleset. Which of the following actions should be performed''
A security technician wants to learn about the latest zero-day threats and newly discovered vulnerabilities but does not have the budget to purchase a commercial threat intelligence service. Which of the following would BEST meet the needs of the security technician? (Select TWO)
The Chief Information Officer (CIO) asks the systems administrator to improve email security at the company based on the following requirements:
1. Do not use two-factor authentication.
2. Protect the contents of a user's mailbox.
3. Be able to sign emails digitally.
4. Protect internal users from spoofing.
5. Secure communications in transit.
6. Use a hierarchically validated certifier for key exchange.
7. Do not use additional plug-in.
8. Have minimal impact to the end-user experience.
Which of the following, when used together, should the systems administrator implement to BEST meet the objectives? (Select TWO).
A security analyst is investigating an alert arising from an impossible travel pattern Within the span of 30 minutes, the email system saw successful authentication from two IP addresses, which geolocate more than 500mi (806km) away from each other Before locking the account which of the following actions should the analyst take?
A Chief Information Security Officer (CISO) wants to set up a SOC to respond to security threats and events more quickly. The SOC must have the following capacities:
• Real-time response
• Visualization
• Threat intelligence integration
• Cross-referencing from multiple sources
• Deduplication
Which of the following technologies would BEST meet these requirements?
Following a major security modem that resulted in a significant loss of revenue and extended loss of server availability, a new Chief Information Security Officer (CISO) conducts a root cause analysis. Which of the following additional steps should the CISO take to mitigate the chance of a recurrence?
A developer implements the following code snippet:
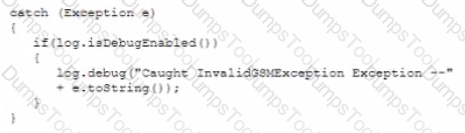
Which of the following vulnerabilities does this code snippet resolve?
While standing a proof-of-concept solution with a vendor, the following direction was given of connections to the default environments.
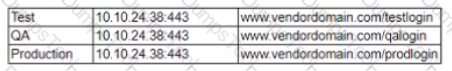
Which of the following is using used to secure the three environments from overlap if all of them reside on separate serves in the same DM2?
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, report come In that a previously vulnerability has returned. Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
The latest security scan of a web application reported multiple high vulnerabilities in session management Which of the following is the BEST way to mitigate the issue?
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees’ devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees’ devices into the network securely?
Developers are working on anew feature to add to a social media platform. Thew new feature involves users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned about various types of abuse that might occur due to this new feature. The DPO state the new feature cannot be released without addressing the physical safety concerns of the platform’s users. Which of the following controls would BEST address the DPO’s concerns?
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix.
Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Select two.)
A networking administrator was recently promoted to security administrator in an organization that handles highly sensitive data. The Chief Information Security Officer (CISO) has just asked for all IT security personnel to review a zero-day vulnerability and exploit for specific application servers to help mitigate the organization’s exposure to that risk. Which of the following should the new security administrator review to gain more information? (Choose three.)
An SQL database is no longer accessible online due to a recent security breach. An investigation reveals that unauthorized access to the database was possible due to an SQL injection vulnerability. To prevent this type of breach in the future, which of the following security controls should be put in place before bringing the database back online? (Choose two.)
A systems administrator at a medical imaging company discovers protected health information (PHI) on a general purpose file server. Which of the following steps should the administrator take NEXT?
A hospital uses a legacy electronic medical record system that requires multicast for traffic between the application servers and databases on virtual hosts that support segments of the application. Following a switch upgrade, the electronic medical record is unavailable despite physical connectivity between the hypervisor and the storage being in place. The network team must enable multicast traffic to restore access to the electronic medical record. The ISM states that the network team must reduce the footprint of multicast traffic on the network.
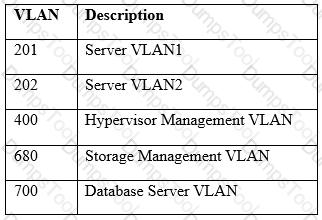
Using the above information, on which VLANs should multicast be enabled?
A company has created a policy to allow employees to use their personally owned devices. The Chief Information Officer (CISO) is getting reports of company data appearing on unapproved forums and an increase in theft of personal electronic devices. Which of the following security controls would BEST reduce the risk of exposure?
A regional business is expecting a severe winter storm next week. The IT staff has been reviewing corporate policies on how to handle various situations and found some are missing or incomplete. After reporting this gap in documentation to the information security manager, a document is immediately drafted to move various personnel to other locations to avoid downtime in operations. This is an example of:
A security administrator is reviewing the following output from an offline password audit:
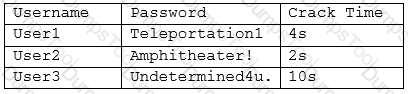
Which of the following should the systems administrator implement to BEST address this audit finding? (Choose two.)
A remote user reports the inability to authenticate to the VPN concentrator. During troubleshooting, a security administrate captures an attempted authentication and discovers the following being presented by the user's VPN client:
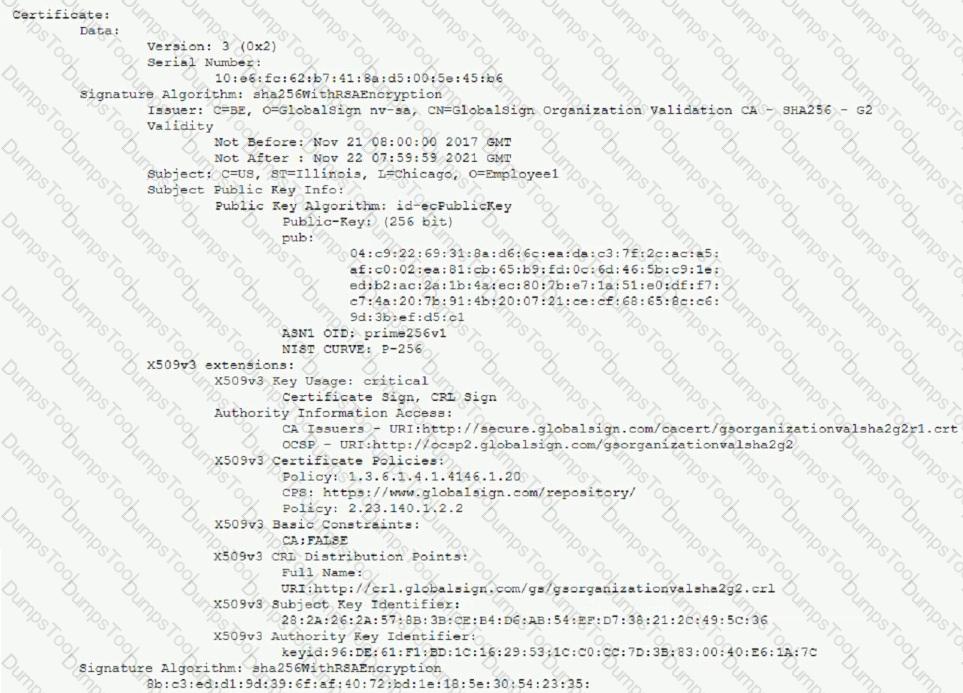
Which of the following BEST describes the reason the user is unable to connect to the VPN service?
The Chief Executive Officer (CEO) of a fast-growing company no longer knows all the employees and is concerned about the company's intellectual property being stolen by an employee. Employees are allowed to work remotely with flexible hours, creating unpredictable schedules. Roles are poorly defined due to frequent shifting needs across the company. Which of the following new initiatives by the information security team would BEST secure the company and mitigate the CEO's concerns?
An internal application has been developed to increase the efficiency of an operational process of a global manufacturer. New code was implemented to fix a security bug, but it has caused operations to halt. The executive team has decided fixing the security bug is less important than continuing operations.
Which of the following would BEST support immediate rollback of the failed fix? (Choose two.)
Joe, a penetration tester, is assessing the security of an application binary provided to him by his client. Which of the following methods would be the MOST effective in reaching this objective?
A university’s help desk is receiving reports that Internet access on campus is not functioning. The network administrator looks at the management tools and sees the 1Gbps Internet is completely saturated with ingress traffic. The administrator sees the following output on the Internet router:
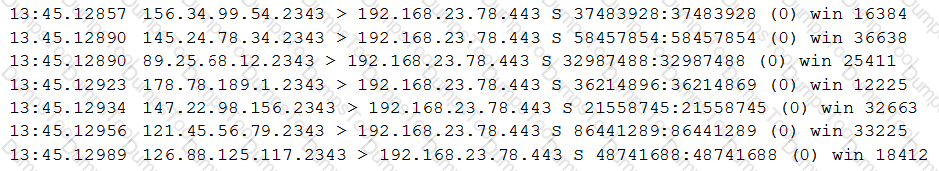
The administrator calls the university’s ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?
As part of an organization's ongoing vulnerability assessment program, the Chief Information Security Officer (CISO) wants to evaluate the organization's systems, personnel, and facilities for various threats As part of the assessment the CISO plans to engage an independent cybersecurity assessment firm to perform social engineering and physical penetration testing against the organization's corporate offices and remote locations. Which of the following techniques would MOST likely be employed as part of this assessment? (Select THREE).
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created.
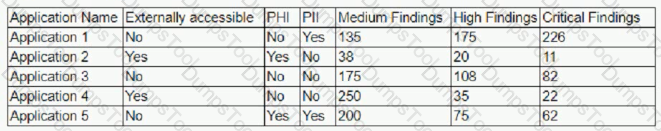
The findings are then categorized according to the following chart:
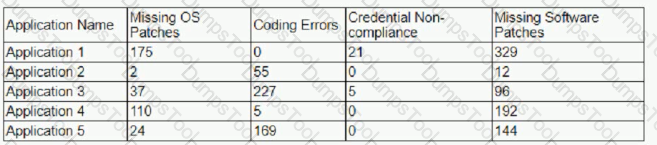
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)
A new security policy states all wireless and wired authentication must include the use of certificates when connecting to internal resources within the enterprise LAN by all employees.
Which of the following should be configured to comply with the new security policy? (Choose two.)
An organization designs and develops safety-critical embedded firmware (inclusive of embedded OS and services) for the automotive industry. The organization has taken great care to exercise secure software development practices for the firmware Of paramount importance is the ability to defeat attacks aimed at replacing or corrupting running firmware once the vehicle leaves production and is in the field Integrating, which of the following host and OS controls would BEST protect against this threat?
During a recent incident, sensitive data was disclosed and subsequently destroyed through a properly secured, cloud-based storage platform. An incident response technician is working with management to develop an after action report that conveys critical metrics regarding the incident.
Which of the following would be MOST important to senior leadership to determine the impact of the breach?
A project manager is working with a software development group to collect and evaluate user scenarios related to the organization’s internally designed data analytics tool. While reviewing stakeholder input, the project manager would like to formally document the needs of the various stakeholders and the associated organizational compliance objectives supported by the project.
Which of the following would be MOST appropriate to use?
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation-states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
A company has decided to replace all the T-1 uplinks at each regional office and move away from using the existing MPLS network. All regional sites will use high-speed connections and VPNs to connect back to the main campus. Which of the following devices would MOST likely be added at each location?
A security engineer is attempting to inventory all network devices Most unknown devices are not responsive to SNMP queries. Which of the following would be the MOST secure configuration?
A financial institution’s information security officer is working with the risk management officer to determine what to do with the institution’s residual risk after all security controls have been implemented. Considering the institution’s very low risk tolerance, which of the following strategies would be BEST?
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
Ann, a corporate executive, has been the recent target of increasing attempts to obtain corporate secrets by competitors through advanced, well-funded means. Ann frequently leaves her laptop unattended and physically unsecure in hotel rooms during travel. A security engineer must find a practical solution for Ann that minimizes the need for user training. Which of the following is the BEST solution in this scenario?
A security engineer is performing an assessment again for a company. The security engineer examines the following output from the review:
Which of the following tools is the engineer utilizing to perform this assessment?
A technician receives the following security alert from the firewall's automated system:
Match_Time: 10/10/16 16:20:43
Serial: 002301028176
Device_name: COMPSEC1
Type: CORRELATION
Scrusex: domain\samjones
Scr: 10.50.50.150
Object_name: beacon detection
Object_id: 6005
Category: compromised-host
Severity: medium
Evidence: host repeatedly visited a dynamic DNS domain (17 time)
After reviewing the alert, which of the following is the BEST analysis?
An analyst is investigating behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the “compose” window.
Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
A company is updating its acceptable use and security policies to allow personal devices to be connected to the network as king as certain security parameters can be enforced Which of the following describes this new policy change?
An ICS security engineer is performing a security assessment at a bank in Chicago. The engineer reviews the following output:

Which of the following tools is the engineer using the provide this output?
While the code is still in the development environment, a security architect is testing the code stored in the code repository to ensure the top ten OWASP secure coding practices are being followed. Which of the following code analyzers will produce the desired results?
Following a recent outage a systems administrator is conducting a study to determine a suitable bench stock of server hard drives. Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep on hand?
A security administrator is advocating for enforcement of a new policy that would require employers with privileged access accounts to undergo periodic inspections and review of certain job performance data. To which of the following policies is the security administrator MOST likely referring?
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization’s existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:
An external red team member conducts a penetration test, attempting to gain physical access to a large organization's server room in a branch office. During reconnaissance, the red team member sees a clearly marked door to the server room, located next to the lobby, with a tumbler lock.
Which of the following is BEST for the red team member to bring on site to open the locked door as quickly as possible without causing significant damage?
A company deploys a system to use device and user certificates for network authentication Previously, the company only used separate certificates to send receive encrypted email. Users have begun notifying the help desk because they cannot read encrypted email Which of the following is the MOST likely cause of the issues7
A security analyst is reviewing the security of a company's public-facing servers After some research the analyst discovers the following on a public pastebin website.
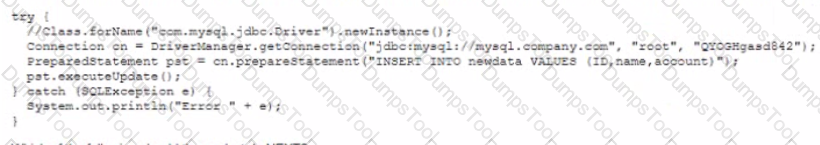
Which of the following should the analyst do NEXT?
As part of an organization’s compliance program, administrators must complete a hardening checklist and note any potential improvements. The process of noting improvements in the checklist is MOST likely driven by:
A factory-floor system uses critical legacy, and unsupported application software to enable factory operations A latent vulnerability was recently exposed, which permitted attackers to send a specific string of characters followed by arbitrary code for execution Patches are unavailable, as the manufacturer is no longer m business Which of the following would be the BEST approach the company should take to mitigate the risk of this vulnerability and other latent vulnerability exploits'' (Select TWO)
A security assessor is working with an organization to review the policies and procedures associated with managing the organization’s virtual infrastructure. During a review of the virtual environment, the assessor determines the organization is using servers to provide more than one primary function, which violates a regulatory requirement. The assessor reviews hardening guides and determines policy allows for this configuration. It would be MOST appropriate for the assessor to advise the organization to:
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in secure environment?
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)
An architect was recently hired by a power utility to increase the security posture of the company’s power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
An attacker exploited an unpatched vulnerability in a web framework, and then used an application service account that had an insecure configuration to download a rootkit The attacker was unable to obtain root privileges Instead the attacker then downloaded a crypto-currency mining program and subsequently was discovered The server was taken offline, rebuilt, and patched. Which of the following should the security engineer suggest to help prevent a similar scenario in the future?
A newly hired systems administrator is trying to connect a new and fully updated, but very customized, Android device to access corporate resources. However, the MDM enrollment process continually fails. The administrator asks a security team member to look into the issue.
Which of the following is the MOST likely reason the MDM is not allowing enrollment?
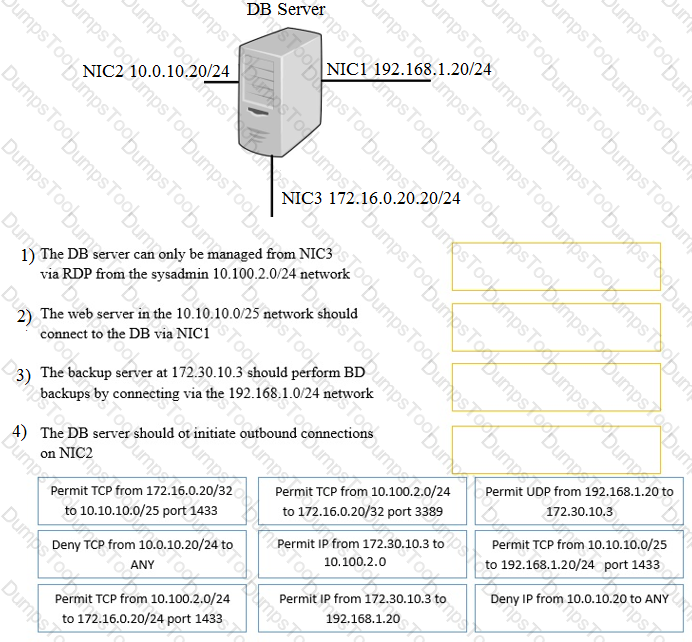
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.
A security engineer is attempting to convey the importance of including job rotation in a company’s standard security policies. Which of the following would be the BEST justification?
A web developer has implemented HTML5 optimizations into a legacy web application. One of the modifications the web developer made was the following client side optimization:
localStorage.setItem(“session-cookie”, document.cookie);
Which of the following should the security engineer recommend?
A network printer needs Internet access to function. Corporate policy states all devices allowed on the network must be authenticated. Which of the following is the MOST secure method to allow the printer on the network without violating policy?
A large enterprise with thousands of users is experiencing a relatively high frequency of malicious activity from the insider threats. Much of the activity appears to involve internal reconnaissance that results in targeted attacks against privileged users and network file shares. Given this scenario, which of the following would MOST likely prevent or deter these attacks? (Choose two.)
A security engineer is employed by a hospital that was recently purchased by a corporation. Throughout the acquisition process, all data on the virtualized file servers must be shared by departments within both organizations. The security engineer considers data ownership to determine:
An engineer is assisting with the design of a new virtualized environment that will house critical company services and reduce the datacenter’s physical footprint. The company has expressed concern about the integrity of operating systems and wants to ensure a vulnerability exploited in one datacenter segment would not lead to the compromise of all others.
Which of the following design objectives should the engineer complete to BEST mitigate the company’s concerns? (Choose two.)
Which of the following is MOST likely to be included in a security services SLA with a third-party vendor?
A security is assisting the marketing department with ensuring the security of the organization’s social media platforms. The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A company makes consumer health devices and needs to maintain strict confidentiality of unreleased product designs Recently unauthorized photos of products still in development have been for sale on the dark web. The Chief Information Security Officer (CISO) suspects an insider threat, but the team that uses the secret outdoor testing area has been vetted many times and nothing suspicious has been found Which of the following is the MOST likely cause of the unauthorized photos?
An employee decides to log into an authorized system. The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
While an employee is on vacation, suspicion arises that the employee has been involved in malicious activity on
the network. The security engineer is concerned the investigation may need to continue after the employee
returns to work. Given this concern, which of the following should the security engineer recommend to maintain
the integrity of the investigation?
A legal services company wants to ensure emails to clients maintain integrity in transit Which of the following would BEST meet this requirement? (Select TWO)
An e-commerce company that provides payment gateways is concerned about the growing expense and time associated with PCI audits of its payment gateways and external audits by customers for their own compliance reasons The Chief Information Officer (CIO) asks the security team to provide a list of options that will:
1. Reduce the overall cost of these audits
2. Leverage existing infrastructure where possible
3. Keep infrastructure costs to a minimum
4. Provide some level of attestation of compliance
Which of the following will BEST address the CIO"s concerns? (Select TWO)
A new employee is plugged into the network on a BYOD machine but cannot access the network Which of the following must be configured so the employee can connect to the network?
During an audit, it was determined from a sample that four out of 20 former employees were still accessing their email accounts An information security analyst is reviewing the access to determine if the audit was valid Which of the following would assist with the validation and provide the necessary documentation to audit?
An international e-commerce company has identified attack traffic originating from a whitelisted third party’s IP address used to mask the third party’s internal network. The security team needs to block the attack traffic without impacting the vendor’s services. Which of the following is the BEST approach to identify the threat?
A security analyst has been assigned incident response duties and must instigate the response on a Windows device that appears to be compromised. Which of the following commands should be executed on the client FIRST?
A)
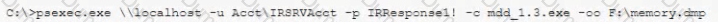
B)
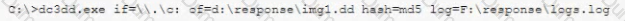
C)
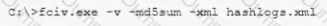
D)

An attacker wants to gain information about a company's database structure by probing the database listener. The attacker tries to manipulate the company's database to see if it has any vulnerabilities that can be exploited to help carry out an attack. To prevent this type of attack, which of the following should the company do to secure its database?
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights. Which of the following documents will MOST likely contain these elements
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following:
* End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow solders to securely communicate with families
* Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications
* A host-based whitelist of approved websites and applications that only allow mission-related tools and sites
* The use of satellite communication to include multiple proxy servers to scramble the source IP address
Which of the following is of MOST concern in this scenario?
A security analyst is attempting to identify code that is vulnerable to butler and integer overflow attacks. Which of the following code snippets is safe from these types of attacks?
A)
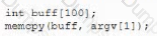
B)

C)
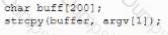
D)
A healthcare company wants to increase the value of the data it collects on its patients by making the data available to third-party researchers for a fee Which of the following BEST mitigates the risk to the company?
Which of the following is the MOST likely reason an organization would decide to use a BYOD policy?
A large industrial system’s smart generator monitors the system status and sends alerts to third-party
maintenance personnel when critical failures occur. While reviewing the network logs, the company’s security manager notices the generator’s IP is sending packets to an internal file server’s IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
A security administrator receives reports that several workstations are unable to access resources within one network segment. A packet capture shows the segment is flooded with ICMPv6 traffic from the source fe80::21ae;4571:42ab:1fdd and for the destination ff02::1. Which of the following should the security administrator integrate into the network to help prevent this from occurring?
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
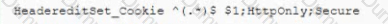
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
A vulnerability scan with the latest definitions was performed across Sites A and B.
Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
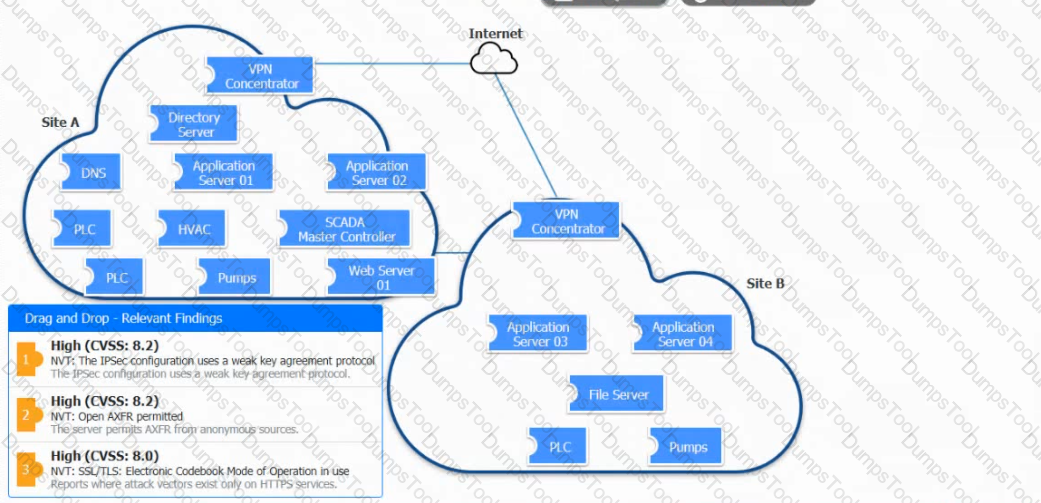
A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of assets, such as workstation, servers, and laptops. Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the company?
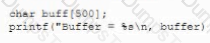
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
A creative services firm has a limited security budget and staff. Due to its business model, the company sends and receives a high volume of files every day through the preferred method defined by its customers. These include email, secure file transfers, and various cloud service providers. Which of the following would BEST reduce the risk of malware infection while meeting the company's resource requirements and maintaining its current workflow?
A company is trying to resolve the following issues related to its web servers and Internet presence:
• The company's security rating declined on multiple occasions when it failed to renew a TLS certificate on one or more infrequently used web servers
• The company is running out of public IPs assigned by its ISP
• The company is implementing a WAF. and the WAF vendor charges by back-end hosts to which the WAF routes
Which of the following solutions will help the company mitigate these issues'? (Select TWO).
A company is transitioning to a new VDI environment, and a system engineer is responsible for developing a sustainable security strategy for the VDIs.
Which of the following is the MOST appropriate order of steps to be taken?
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure. The organization’s server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk:

Which of the following should be included in the auditor’s report based on the above findings?