What is typically NOT a function of the APIs created within the framework called API-led connectivity?
What is the most performant out-of-the-box solution in Anypoint Platform to track transaction state in an asynchronously executing long-running process implemented as a Mule application deployed to multiple CloudHub workers?
A company deployed an API to a single worker/replica in the shared cloud in the U.S. West Region.
What happens when the Availability Zone experiences an outage?
What Anypoint Platform Capabilities listed below fall under APIs and API Invocations/Consumers category? Select TWO.
An organization is implementing a Quote of the Day API that caches today's quote.
What scenario can use the GoudHub Object Store via the Object Store connector to persist the cache's state?
A REST API is being designed to implement a Mule application.
What standard interface definition language can be used to define REST APIs?
4 Production environment is running on a dedicated Virtual Private Cloud (VPC) on CloudHub 1,0, and the security team guidelines clearly state no traffic on HTTP.
Which two options support these security guidelines?
Choose 2 answers
Which component monitors APIs and endpoints at scheduled intervals, receives reports about whether tests pass or fail, and displays statistics about API and endpoint
performance?
Refer to the exhibit.
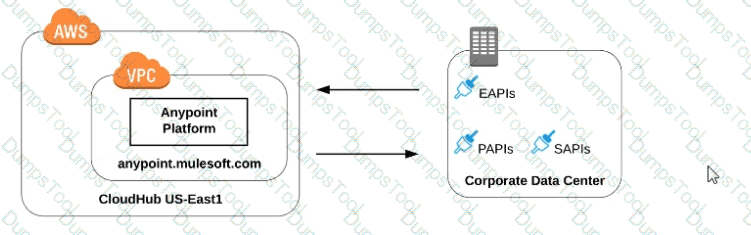
what is true when using customer-hosted Mule runtimes with the MuleSoft-hosted Anypoint Platform control plane (hybrid deployment)?
A large lending company has developed an API to unlock data from a database server and web server. The API has been deployed to Anypoint Virtual Private Cloud
(VPC) on CloudHub 1.0.
The database server and web server are in the customer's secure network and are not accessible through the public internet. The database server is in the customer's AWS
VPC, whereas the web server is in the customer's on-premises corporate data center.
How can access be enabled for the API to connect with the database server and the web server?
An existing Quoting API is defined in RAML and used by REST clients for interacting with the quoting engine. Currently there is a resource defined in the RAML that allows the creation of quotes; however, a new requirement was just received to allow for the updating of existing quotes.
Which two actions need to be taken to facilitate this change so it can be processed?
Choose 2 answers
An application updates an inventory running only one process at any given time to keep the inventory consistent. This process takes 200 milliseconds (.2 seconds) to
execute; therefore, the scalability threshold of the application is five requests per second.
What is the impact on the application if horizontal scaling is applied, thereby increasing the number of Mule workers?
A large organization with an experienced central IT department is getting started using MuleSoft. There is a project to connect a siloed back-end system to a new
Customer Relationship Management (CRM) system. The Center for Enablement is coaching them to use API-led connectivity.
What action would support the creation of an application network using API-led connectivity?
A Rate Limiting policy is applied to an API implementation to protect the back-end system. Recently, there have been surges in demand that cause some API client
POST requests to the API implementation to be rejected with policy-related errors, causing delays and complications to the API clients.
How should the API policies that are applied to the API implementation be changed to reduce the frequency of errors returned to API clients, while still protecting the back-end
system?
An organization requires several APIs to be secured with OAuth 2.0, and PingFederate has been identified as the identity provider for API client authorization, The
PingFederate Client Provider is configured in access management, and the PingFederate OAuth 2.0 Token Enforcement policy is configured for the API instances required by the
organization. The API instances reside in two business groups (Group A and Group B) within the Master Organization (Master Org).
What should be done to allow API consumers to access the API instances?
An online store's marketing team has noticed an increase in customers leaving online baskets without checking out. They suspect a technology issue is at the root cause of the baskets being left behind. They approach the Center for Enablement to ask for help identifying the issue. Multiple APIs from across all the layers of their application network are involved in the shopping application.
Which feature of the Anypoint Platform can be used to view metrics from all involved APIs at the same time?
A Mule 4 API has been deployed to CloudHub and a Basic Authentication - Simple policy has been applied to all API methods and resources. However, the API is still accessible
by clients without using authentication.
How is this possible?
A Platform Architect inherits a legacy monolithic SOAP-based web service that performs a number of tasks, including showing all policies belonging to a client. The service connects to two back-end systems — a life-insurance administration system and a general-insurance administration system — and then queries for insurance policy information within each system, aggregates the results, and presents a SOAP-based response to a user interface (UI).
The architect wants to break up the monolithic web service to follow API-led conventions.
Which part of the service should be put into the process layer?
An API has been updated in Anypoint Exchange by its API producer from version 3.1.1 to 3.2.0 following accepted semantic versioning practices and the changes have been communicated via the API's public portal.
The API endpoint does NOT change in the new version.
How should the developer of an API client respond to this change?
Due to a limitation in the backend system, a system API can only handle up to 500 requests per second. What is the best type of API policy to apply to the system API to avoid overloading the backend system?
Refer to the exhibit. An organization needs to enable access to their customer data from both a mobile app and a web application, which each need access to common fields as well as certain unique fields.
The data is available partially in a database and partially in a 3rd-party CRM system.
What APIs should be created to best fit these design requirements?
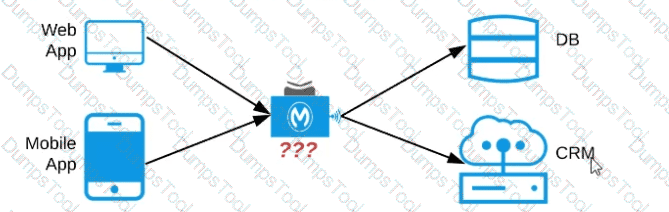
A) A Process API that contains the data required by both the web and mobile apps, allowing these applications to invoke it directly and access the data they need thereby providing the flexibility to add more fields in the future without needing API changes
B) One set of APIs (Experience API, Process API, and System API) for the web app, and another set for the mobile app
C) Separate Experience APIs for the mobile and web app, but a common Process API that invokes separate System APIs created for the database and CRM system
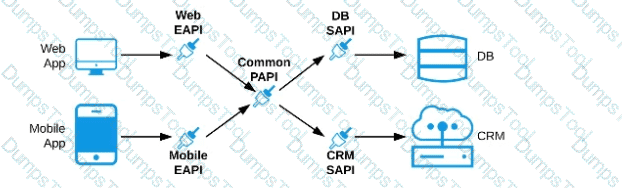
D) A common Experience API used by both the web and mobile apps, but separate Process APIs for the web and mobile apps that interact with the database and the CRM System
Which statement is true about Spike Control policy and Rate Limiting policy?
Question 10: Skipped
An API implementation returns three X-RateLimit-* HTTP response headers to a requesting API client. What type of information do these response headers indicate to the API client?
A company stores financial transaction data in two legacy systems. For each legacy system, a separate, dedicated System API (SAPI) exposes data for that legacy system. A Process API (PAPI) merges the data retrieved from ail of the System APIs into a common format. Several API clients call the PAPI through its public domain name.
The company now wants to expose a subset of financial data to a newly developed mobile application that uses a different Bounded Context Data Model. The company wants to follow MuleSoft's best practices for building out an effective application network.
Following MuleSoft's best practices, how can the company expose financial data needed by the mobile application in a way that minimizes the impact on the currently running API clients, API implementations, and support asset reuse?
The Line of Business (LoB) of an eCommerce company is requesting a process that sends automated notifications via email every time a new order is processed through the
customer's mobile application or through the internal company's web application. In the future, multiple notification channels may be added: for example, text messages and
push notifications.
What is the most effective API-led connectivity approach for the scenario described above?
An API implementation is deployed to CloudHub.
What conditions can be alerted on using the default Anypoint Platform functionality, where the alert conditions depend on the end-to-end request processing of the API implementation?
An API implementation is updated. When must the RAML definition of the API also be updated?
A Platinum customer uses the U.S. control plane and deploys applications to CloudHub in Singapore with a default log configuration.
The compliance officer asks where the logs and monitoring data reside?
The asset version 2.0.0 of the Order API is successfully published in Exchange and configured in API Manager with the Autodiscovery API ID correctly linked to the
API implementation, A new GET method is added to the existing API specification, and after updates, the asset version of the Order API is 2.0.1,
What happens to the Autodiscovery API ID when the new asset version is updated in API Manager?
A business process is being implemented within an organization's application network. The architecture group proposes using a more coarse-grained application
network design with relatively fewer APIs deployed to the application network compared to a more fine-grained design.
Overall, which factor typically increases with a more coarse-grained design for this business process implementation and deployment compared with using a more fine-grained
design?
An enterprise is embarking on the API-led digital transformation journey, and the central IT team has started to define System APIs. Currently there is no Enterprise
Data Model being defined within the enterprise, and the definition of a clean Bounded Context Data Model requires too much effort.
According to MuleSoft's recommended guidelines, how should the System API data model be defined?
A customer has an ELA contract with MuleSoft. An API deployed to CloudHub is consistently experiencing performance issues. Based on the root cause analysis, it is
determined that autoscaling needs to be applied.
How can this be achieved?
An API is protected with a Client ID Enforcement policy and uses the default configuration. Access is requested for the client application to the API, and an approved
contract now exists between the client application and the API
How can a consumer of this API avoid a 401 error "Unauthorized or invalid client application credentials"?
The responses to some HTTP requests can be cached depending on the HTTP verb used in the request. According to the HTTP specification, for what HTTP verbs is this safe to do?
How are an API implementation, API client, and API consumer combined to invoke and process an API?