What is the default behavior of the Zone-Based Firewall (ZBFW) for traffic originating from the ION device itself (e.g., DNS queries, NTP sync, or Controller connectivity) destined for the "Internet" zone?
An ION 3000 device at a remote branch has suffered a critical hardware failure and must be replaced via the RMA process. The administrator has received the replacement unit.
What is the correct procedure to transfer the configuration and license from the defective unit to the replacement unit to ensure minimal downtime and retention of historical data?
In a Prisma SD-WAN deployment, what is the defining characteristic of a "Standard VPN" compared to a "Secure Fabric Link"?
Which statements accurately describes how the Prisma SD-WAN zone-based firewall functions within a branch network?
Which component of Prisma SD-WAN is responsible for distributing User-IP and user-group mappings to branch devices that match the corresponding source IPs?
An organization has created a custom internal application definition for "Inventory_App" on the Prisma SD-WAN controller based on its destination IP address and port (L3/L4 rule). The application server IP has just changed.
After updating the custom application definition on the controller, how is this change propagated to the branch ION devices?
User-ID integration is configured for a Prisma SD-WAN deployment. Branch-1 has the user-to-IP mappings available, and User-1 is mapped to IP-1.
To which two use cases can User-ID based zone-based firewall policies be applied? (Choose two.)
There are periodic complaints about the poor performance of a real-time application.
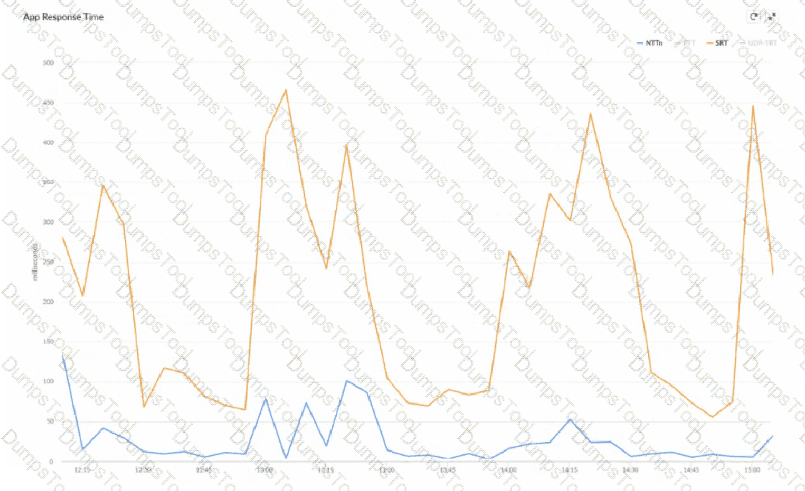
What can be inferred about the performance issue, based on the Network Transfer Time (NTT) and Server Response Time (SRT) image below?
A network engineer is troubleshooting a user complaint regarding "slow application performance" for an internal web application. While viewing the Flow Browser in the Prisma SD-WAN portal, the engineer notices that the Server Response Time (SRT) is consistently high (over 500ms), while the Network Transfer Time (NTT) and Round Trip Time (RTT) are low (under 50ms).
What does this data indicate about the root cause of the issue?
What is the primary function of the "CloudBlade" platform in a Prisma SD-WAN deployment when integrating with third-party services or Prisma Access?
Which specialized hardware feature is available on the ION 9000 series but NOT on the ION 3000 series, making it suitable for high-throughput Data Center deployments?
A network administrator notices that a branch ION device is experiencing high CPU utilization due to a suspected TCP SYN Flood attack originating from a compromised host on the local LAN.
Which specific security feature should be configured and applied to the "LAN" zone to mitigate this Denial of Service (DoS) attack?
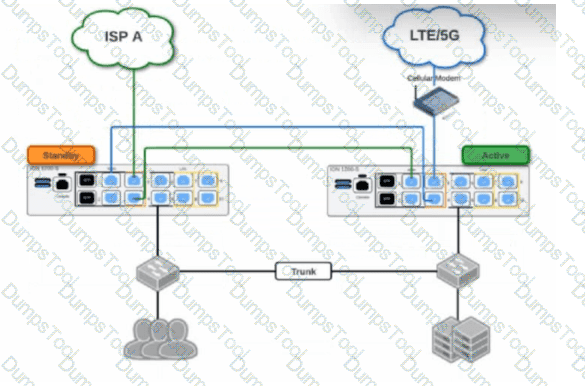
Based on the HA topology image below, which two statements describe the end-state when power is removed from the ION 1200-S labeled “Active”, assuming that the ION labeled “Standby” becomes the active ION? (Choose two.)
A network engineer is troubleshooting an ION device that is showing as "Offline" in the Prisma SD-WAN portal, despite the site reporting that local internet access is working. The engineer has console access to the device.
Which CLI command should be used to specifically validate the device's ability to resolve the controller's hostname and establish a secure connection to it over a specific interface?
What does Prisma SD-WAN use for monitoring and operations to deliver flow data and application visibility?
Which component of the Prisma SD-WAN solution is responsible for the deep application identification (App-ID) and the generation of flow metrics (Network Transfer Time, Server Response Time) at the branch?
When configuring a Path Policy rule for a "Real-Time Video" application, the administrator wants to ensure the traffic uses the path with the lowest packet loss.
How does the Prisma SD-WAN ION determine the "Packet Loss" metric for a given path when there is no active user traffic flowing on that link?
By default, how many days will Prisma SD-WAN VPNs stay operational before the keys expire when an ION device loses connection with the controller?