Under which category does an application that is approved by the IT department, such as Office 365, fall?
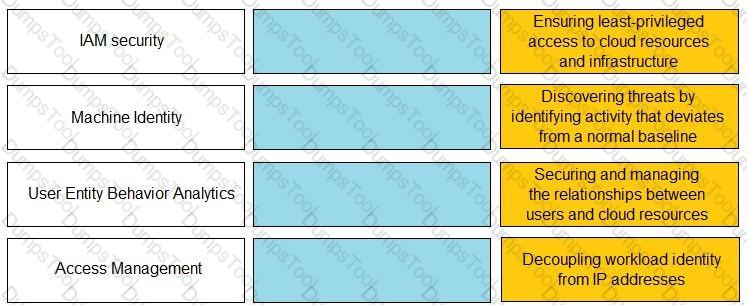
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which capability of a Zero Trust network security architecture leverages the combination of application, user, and content identification to prevent unauthorized access?
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
Which three layers of the OSI model correspond to the Application Layer (L4) of the TCP/IP model?
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
What are the two most prominent characteristics of the malware type rootkit? (Choose two.)
Which aspect of a SaaS application requires compliance with local organizational security policies?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
Identify a weakness of a perimeter-based network security strategy to protect an organization's endpoint systems.
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
In a traditional data center what is one result of sequential traffic analysis?
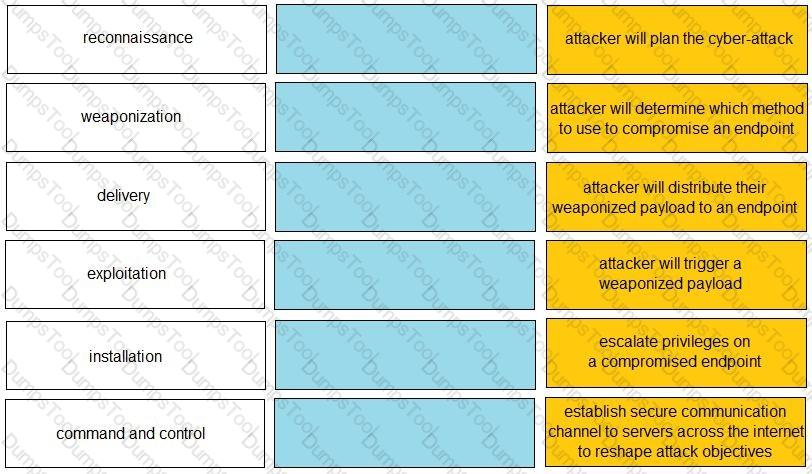
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which action must Secunty Operations take when dealing with a known attack?
The seventy of an attack needs to be escalated.
What needs to be in place in order for the security operations team to properly inform various units within the enterprise of the issue?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?