A MySQL Server has been running an existing application successfully for six months. The my.cnf is adjusted to contain this additional configuration:
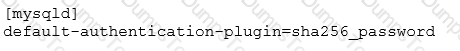
The MySQL Server is restarted without error.
What effect will the new configuration have on existing account?
You have created a backup of the ‘sales’ database with the command:
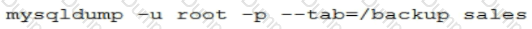
Which two procedures can be used to restore the ‘orders’ table from the backup?
The Performance Schema includes these tables related to status variables:
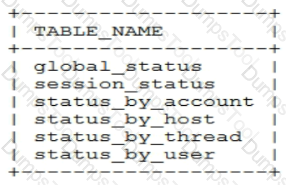
Which two facts are true about these tables? (Choose two.)
Due to an authentication plug-in that is used on the server, passwords are required to be sent as clear text as opposed to the usual encrypted format.
Which two methods would allow the mysql client to connect to the server and send clear text passwords? (Choose two.)
You have successfully provisioned the latest MySQL 5.7 database instance on a physical host, to be added to an existing farm for use in a modern, high volume, ACID-compliant, OLTP website, which serves hundreds of DML transactions per second.
The default values of which two key variables do you change to ensure seamless operation of the database? (Choose two.)
When you examine a new MySQL installation with default configuration, you find a file called ibdata1 in the database directory. Which two statements are true about this file? (Choose two.)
You have a MySQL replication setup and you intentionally stop the SQL thread on the slave.
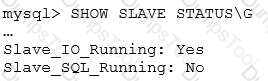
What are two reasons that you may stop the SQL thread on the slave while keeping the I/O thread running? (Choose two.)
Consider that local disk files are accessible via MySQL with commands such as:
mysql> LOAD DATA LOCAL INFILE ‘/etc/passwd’ INTO TABLE mypasswords;
What change could be made to stop any breach via this insecurity?
Consider:
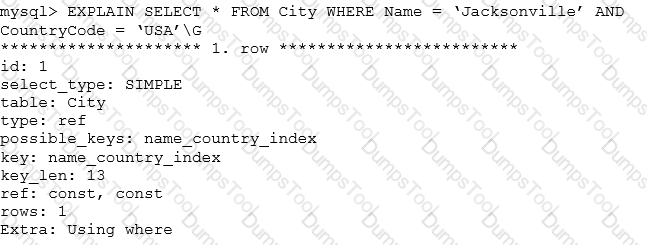
Which statement best describes the meaning of the value for the key_len column?
The following grants were executed:
GRANT CREATE ROUTING ON sales.* TO ‘webadmin’@’%’;
GRANT ALTER ON PROCEDURE sales.myproc TO ‘webadmin’@’%’;
A user successfully connects to the database as webadmin and created a stored procedure named get_reports. The next day, the user logs in again as webadmin and wants to delete the stored procedure named get_reports, and therefore, issues the following statement:
USE sales;
DROP PROCEDURE IF EXISTS get_reports;
What is the result of executing the statement?
Which three statements correctly describe MySQL InnoDB Cluster? (Choose three.)