You are managing a WebLogic domain that has the default built-in diagnostic module configured for each server in the domain.
You have the following requirements:
What are two approaches you can apply to achieve this result? (Choose two.)
What is the first action to take during a Rolling Update? (Choose the best answer.)
You are developing and managing distributed destination applications for which you do not need to create or designate destination members.
Which configuration steps in the Administration Console will help you to create and target a Uniform Distributed Topic so that you can rely on WLS to create the necessary members on the JMS servers to which a JMS module is already targeted? (Choose the best answer.)
You are planning to use WebLogic JMS for implementing my enterprise messaging architecture. Which messaging paradigm is invalid in this context? (Choose the best answer.)
You are required to configure SSL for an instance of WebLogic Server in a production environment. You have already created your self-signed certificate within the myKeyStore.jks keystore. You must now obtain a new digital certificate from a trusted Certificate Authority.
Which command do you use to start the process? (Choose the best answer.)
Your application includes a message driven bean (MDB) that is listening to messages on a JMS Queue. You need to ensure that every message is processed exactly once by the MDB.
Which configuration allows you to achieve this requirement? (Choose the best answer.)
Your application has an auditing requirement that says that all audit events that have a severity of FAILURE must be logged and a notification must be sent to the application’s monitoring tier. The monitoring tier is implemented as a stateless session bean that provides an entry point called auditlog. The development team has provided you with the code that calls the monitoring tier.
How can you meet this requirement using WebLogic Server auditing? (Choose the best answer.)
I am configuring the security policy for my JMS module. I am specifying some security conditions for the module.
Which two security conditions are valid in this context? (Choose two.)
A Web Module needs specific tuning. The Development team fine tunes the module in the deployment descriptor (weblogic.xml) as follows:
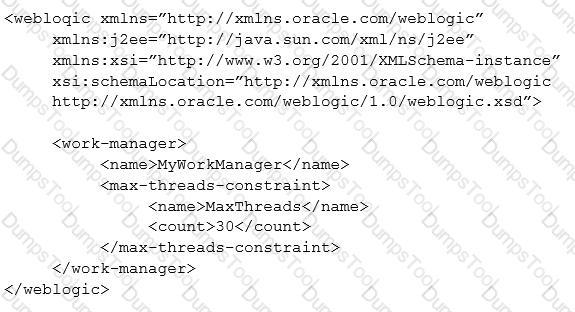
Which two are true? (Choose two.)
Which two statements are true about the role of cluster master in whole server migration? (Choose two.)
Some of the messages entering a JMS queue are expiring and are being removed from the queue. You need better insight regarding these expired messages.
Which mechanism helps achieve this? (Choose the best answer.)
You need to update a database accessed by an application that uses a WebLogic server data source. It has been decided that the data source on WLS should first be shut down.
You have been asked to advise as to whether they should execute a shutdown() or a forceShutdown() on the corresponding JDBCDataSourceRuntimeMBean.
Which two statements are true regarding the impact on the application that is using that data source? (Choose two.)