An administrator recently added VLAN 205 CRM in Prism Element. The workloads attached to the associated NICs are unable to establish network connectivity.
Which Layer 2 protocol allows the administrator to troubleshoot this issue from Prism Element?
An administrator recently added in 3 nodes to an existing 5 node cluster. While 1 node came with its own block, the other 2 nodes where added to an existing share. After adding the nodes, the administrator sees that the hardware tab displays the correct number of nodes, but incorrect position in the diagram tab.
What should the administrator do to resolve the issue?
An administrator wants to utilize Network Visualization to monitor the physical and logical network on the Nutanix cluster. The first-hop switch has LLDP enabled. The network switch information is still not being displayed.
What is causing this problem?
An administrator attempts to reinstall a VM's Guest OS but is unable to change the Legace BIOS boot Priority.
Based on the exhibit, what is causing this issue?
A CEO asks the IT administrator to provide a list of required resources to protect current workloads and the two new SQL servers from a disaster. The Nutanix environment is managed by Prism Central.
Which option explains how to meet the CEO's request?

An Administrator Notices that the Data Resiliency status of some components has been reduced to 0, making it impossible to support a node failure in the cluster.
What failed Component Caused this Issue?
An administrator wants to view VMs with NGT Installed and Filter by their installed guest operating systems.
How can this task most quickly be accomplished within prism central?
An administrator is monitoring the Nutanix v5.15-based AOS cluster performance logs and notices that a SQL server VM is greatly exceeding its intended maximum IOPS. The administrator has confirmed that a QoS policy was previously created for the group of VMs this server is a member of.
What are two reasons that this VM would exceed its maximum configured IOPS from the QoS Policy? (Choose two.)
Refer to the exhibit.
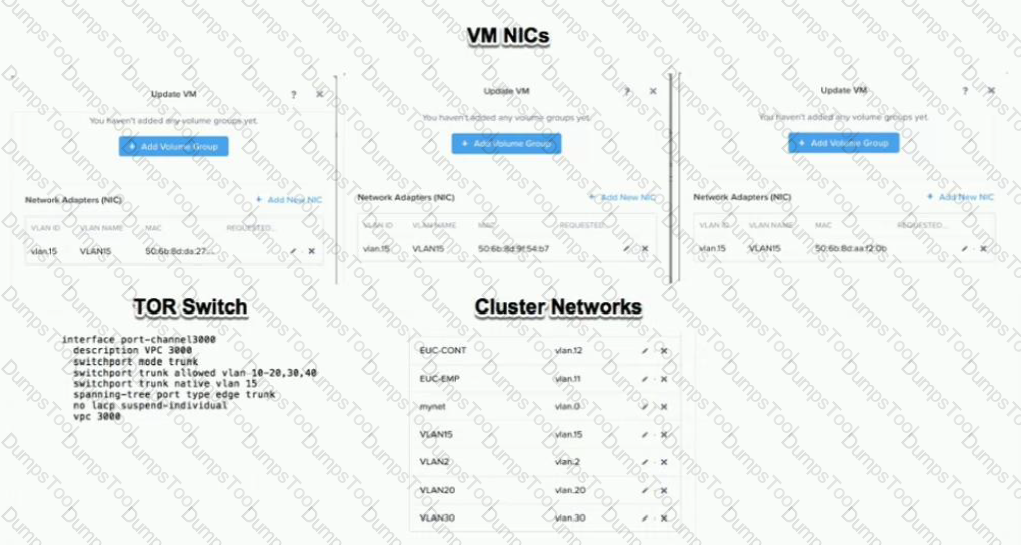
An administrator is commissioning a Nutanix Enterprise Cloud. Once the user VMs have been deployed and are running, the administrator finds that VMs on the same host are able to communicate, but are unable to communicate between hosts.
What must be changed to enable full inter-VM communications?
An administrator needs to determine current CPU usage across multiple clusters.
Which method should the administrator use to generate this type of report?
A new Nutanix cluster is ready for production on a remote site with no IT staff. Changes to the infrastructure will cost money and probably cause a cluster stop. The administrator needs to perform a health check on the environment that should include:
• Network connectivity checks
• Network performance status
• Storage performance status
Which tool should be used to perform this test?
An administrator is deploying an application that requires maximum I/O throughput for scratch data. The administrator is concerned that the throughput requirement is greater than what can be provided by a single cluster node.
What should the administrator do to meet this requirement?
An administrator has Created a new VM, but When accessing the console to monitor the guest install, the administrator sees the effect shown in the exhibit.
What is the likely cause of this issue?
A VDI environment based on AHV Cluster is not performing well. The current environment is using only one bridge (Bridge0). The administrator needs to verify if nodes are using all network cards associated to Bridge0.
Which two menus should be used to check the current configuration? (Choose two.)
An administrator needs to evaluate if the existing configuration of Protection Domains meets the specified corporate recovery policy for SQL Data. The corporate policy requires that all SQL Servers be recoverable at the DR site within 30 minutes, and must result in a maximum of 60 minutes of data loss. SQL data must be required.
The protection domain is configured as follows:
• Application consistent snapshots are enabled
• The SQL server VMs are assigned to the Protection Domain as their own Consistency Group
• The Protection Domain schedule is configured as snapshots taken every 90 minutes from 7 am until 8 pm
What must be changed to meet the required policy?
An administrator needs to replace the self-signed certificate on a cluster. Which two requirements must be met as part of the process? (Choose two.)
Nutanix Support Asked an administrator to provide AHV logs to help solve a support request.
Which task should be performed to provide log files to the support team?
Refer to the exhibit.
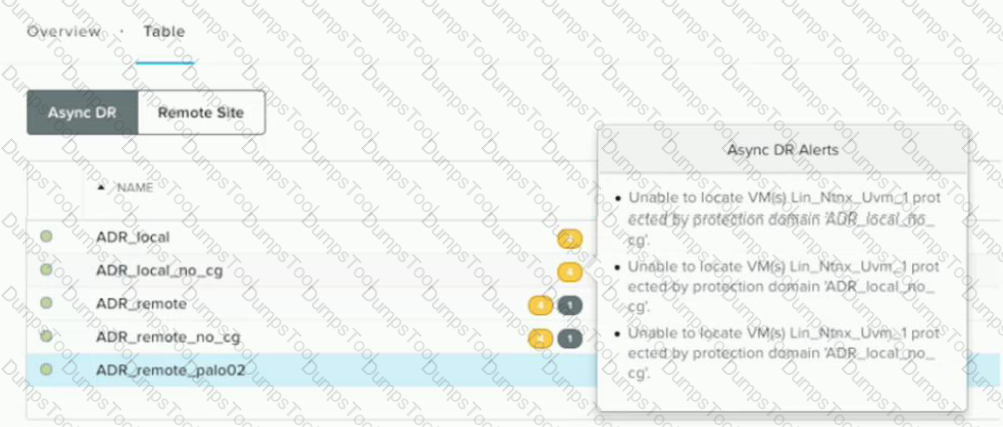
After performing ESXi to AHV conversion on a cluster, the alerts shown in the exhibit display on Prism. What should the administrator do to resolve this issue efficiently?