Is ARP used in the IPv6 protocol?
False
True
In IPv6, the Address Resolution Protocol (ARP) is not used. Instead, IPv6 uses the Neighbor Discovery Protocol (NDP), which is part of the ICMPv6 suite. NDP handles address resolution, router discovery, and reachability.
MTCNA Course Material – IPv6 Address Resolution:
“IPv6 replaces ARP with Neighbor Discovery Protocol. NDP uses ICMPv6 to perform tasks like address resolution and router discovery.”
René Meneses MTCNA Study Guide – IPv6 Fundamentals:
“There is no ARP in IPv6. It uses NDP messages for neighbor solicitation and advertisement.”
Thus, ARP is not used in IPv6.
Final Answer: AQUESTION NO: 152 [Monitoring and Management – SNMP Protocol]
Which of the following protocols / ports are used for SNMP (Simple Network Management Protocol)?
A. TCP 162
B. UDP 162
C. UDP 161
D. TCP 25
E. TCP 123
F. TCP 161
Answer: B, C
SNMP uses the following ports:
UDP 161: Used for SNMP agent queries (GET, SET, etc.)
UDP 162: Used by SNMP managers to receive trap notifications
MTCNA Course Material – SNMP and Monitoring:
“SNMP uses UDP 161 for polling devices and UDP 162 for traps.”
MikroTik Wiki – SNMP:
“SNMP communication uses UDP ports 161 (queries) and 162 (traps). TCP is not used for SNMP by default.”
Option breakdown:
A: TCP 162 → incorrect (SNMP traps use UDP)
B:✔UDP 162
C:✔UDP 161
D: TCP 25 = SMTP
E: TCP 123 = NTP (incorrect protocol and transport)
F: TCP 161 = incorrect transport
Final Answer: B, CQUESTION NO: 153 [ARP – MikroTik Specific Behavior]
If arp=reply-only is configured on an interface, what will this interface do?
A. Accept all IP/MAC combinations listed in /ip arp as static entries
B. Accept all IP addresses listed in /ip arp as static entries
C. Add new MAC addresses in /ip arp list
D. Accept all MAC addresses listed in /ip arp as static entries
E. Add new IP addresses in /ip arp list
Answer: A
Setting arp=reply-only on an interface disables the normal dynamic ARP process. The router will only respond to ARP requests for IP/MAC pairs that are explicitly listed in /ip arp with type=static. No dynamic entries will be added.
MikroTik Wiki – ARP Modes:
“reply-only – the interface will only reply to ARP requests if there is a static entry. It will not add any new entries.”
MTCNA Course Material – ARP Configuration:
“When reply-only is set, the interface will not send ARP requests and will only respond to those IP/MAC combinations configured as static entries.”
Option breakdown:
A:✔Correct—replies only to statically configured IP/MAC pairs
B: Incorrect — ARP entries must have both IP and MAC
C/E: No new dynamic entries are added in reply-only mode
D: MAC addresses alone are not matched — ARP matches IP/MAC pairs
Final Answer: AQUESTION NO: 154 [RouterOS Tools – Configuration Export]
Mark all correct statements about /export (rsc file).
A. Exports logs from /log print
B. Exports full configuration of the router
C. Exports only part of the configuration (for example /ip firewall)
D. Exports scripts from /system script
E. Exported files could not be edited
Answer: B, C, D
The /export command in RouterOS allows exporting configuration as a script (.rsc file). It can:
Export the full configuration
Export a specific section (e.g., /ip firewall)
Include scripts under /system script if specified
It does not export logs and the exported .rsc file is plain text and can be edited.
MTCNA Course Material – Configuration Management:
“/export outputs configuration to a text file. You can export the full config or a specific menu, and it includes scripts if present.”
MikroTik Wiki – Export Command:
“You can use /export to generate editable .rsc files. Use /export file=name or /ip firewall export.”
Option breakdown:
A:❌Logs are not exported
B:✔Full config export is default
C:✔You can target specific sections (e.g., /ip dhcp-server)
D:✔Scripts are included if present
E:❌Exported files are editable text files
Final Answer: B, C, D
What is the main reason the OSI model was created?
To create a layered model larger than the DoD model.
So application developers can change only one layer's protocols at a time.
So different networks could communicate.
So Cisco could use the model.
The OSI (Open Systems Interconnection) model was developed by the ISO (International Standards Organization) to provide a universal standard for network communications. Its primary goal is to enable interoperability between different systems and vendors by establishing a common networking framework.
MTCNA Course Material – OSI Model Purpose:
“The OSI model helps standardize networking so that different systems and networks can communicate.”
René Meneses MTCNA Study Guide – OSI Principles:
“The model was designed to guide product developers and facilitate communication between heterogeneous network systems.”
Other options:
A: The OSI was not intended to be “larger” than DoD model
B: Helpful benefit, but not the main reason for creation
D: Incorrect and vendor-specific (not factual)
Final Answer: CQUESTION NO: 126 [Networking Fundamentals – VLAN Concepts]
What does a VLAN do?
A. Acts as the fastest port to all servers.
B. Provides multiple collision domains on one switch port.
C. Breaks up broadcast domains in a layer 2 switch internetwork.
D. Provides multiple broadcast domains within a single collision domain.
Answer: C
VLANs (Virtual Local Area Networks) segment a Layer 2 switch network into separate broadcast domains. Without VLANs, all devices on a switch share a single broadcast domain. VLANs allow traffic isolation by logically grouping ports, improving security and performance.
MTCNA Course Material – VLAN Fundamentals:
“VLANs allow you to logically segment a switch network. Each VLAN creates a separate broadcast domain.”
René Meneses MTCNA Study Guide – VLAN Behavior:
“Switches normally operate in a single broadcast domain. VLANs break this up without requiring physical segmentation.”
Breakdown:
A: Not related to VLAN function
B: Switch ports are already separate collision domains
D: Reverse of what VLANs actually do
Final Answer: CQUESTION NO: 127 [VLAN Management – VTP and Cisco Switching]
Which one of the following is true regarding VLANs?
A. Two VLANs are configured by default on all Cisco switches.
B. VLANs only work if you have a complete Cisco switched internetwork. No off-brand switches are allowed.
C. You should not have more than 10 switches in the same VTP domain.
D. VTP is used to send VLAN information to switches in a configured VTP domain.
Answer: D
VTP (VLAN Trunking Protocol) is a Cisco proprietary protocol used to manage and propagate VLAN information throughout a switch fabric. It helps maintain consistency across switches by distributing VLAN configurations from a VTP server to client switches in the same domain.
Cisco Switching Guide – VTP Concepts:
“VTP advertises VLAN definitions on a LAN to ensure consistency. It reduces misconfigurations by centralizing VLAN management.”
René Meneses MTCNA Study Guide – VLAN and VTP Notes:
“VTP sends VLAN updates across switches in the same VTP domain. Switches must be compatible and share the domain name.”
Breakdown:
A: Only VLAN 1 exists by default
B: VLANs are not Cisco-exclusive
C: There is no limit of 10 switches in a VTP domain
D:✔Correct
Final Answer: DQUESTION NO: 128 [RouterOS]
If your router is facilitating a CSU/DSU, which of the following commands do you need to use to provide the router with a 64000bps serial link?
A. RouterA(config)#bandwidth 64
B. RouterA(config-if)#bandwidth 64000
C. RouterA(config-if)#clock rate 64
D. RouterA(config-if)#clock rate 64000
Answer: D
In Cisco IOS, the clock rate command is used on the DCE (Data Communications Equipment) end of a serial link to provide timing to the connected DTE (Data Terminal Equipment) device. To configure a 64 kbps link, the correct syntax is:
RouterA(config-if)#clock rate 64000
Cisco IOS Configuration Guide – Serial Interfaces:
“When the router acts as DCE, use the command clock rate [bps] under the serial interface to set the speed. For 64kbps, use 64000.”
René Meneses MTCNA Guide – WAN Configuration (Cisco Compatibility):
“Use clock rate 64000 for CSU/DSU simulation. Bandwidth command is for routing metrics only.”
Option analysis:
A: bandwidth 64 → Sets routing metric, not actual interface speed
B: bandwidth 64000 → Same; metric only
C: clock rate 64 → Incorrect value
D:✔Correct and syntactically valid
Final Answer: D────────────────────────────────────────────────────────────
If 'check-gateway' is enabled for an ECMP route and one of the gateways is unreachable, then:
ECMP is going to send packets to all gateways even if one is unreachable
The unreachable gateway is not going be used in Round Robin algorithm
The ECMP route becomes inactive
When multiple gateways are used in an ECMP (Equal Cost Multi-Path) configuration, the check-gateway option ensures that RouterOS will actively monitor the health of each gateway using ping (or ARP). If a gateway becomes unreachable, RouterOS temporarily removes it from the active ECMP gateway list.
A.✘Incorrect – Unreachable gateways are excluded from packet forwarding.
B.✔Correct – Only reachable gateways are used in the ECMP round robin logic.
C.✘Incorrect – The entire ECMP route remains active; only the failed gateway is excluded.
Extract from MTCNA Course Material – ECMP Routing:
“With check-gateway enabled, RouterOS will exclude unreachable gateways from ECMP rotation.”
Extract from MikroTik Wiki – Check-Gateway Option:
“When a gateway is unreachable, it is skipped in ECMP logic until it becomes reachable again.”
Extract from René Meneses Study Guide – ECMP and Gateway Monitoring:
“Check-gateway helps prevent blackholing by skipping dead gateways. The route remains active.”
==================================
If you wish to block user access to MSN messenger, which chain should the firewall rule be placed in?
input
process
forward
output
In MikroTik’s firewall, the correct chain depends on the traffic direction and whether the traffic is destined for or originating from the router itself.
To block access to MSN (or any other service being accessed by a user from the LAN to the Internet), you must filter transit traffic. This is done in the forward chain.
A. input → Used for traffic destined to the router (e.g., WinBox, SSH).
B.✘process → Invalid option (does not exist in RouterOS).
C.✔forward → Used for user traffic passing through the router (e.g., LAN client to MSN servers on the Internet).
D. output → Used for traffic originating from the router itself (e.g., ping from router to external IP).
Extract from Official MTCNA Course Material – Firewall Chains:
“Use the forward chain to filter traffic passing through the router (LAN to WAN). Blocking access to external services like Facebook or MSN belongs here.”
Extract from René Meneses MTCNA Study Guide – Firewall Chains:
“To block Internet services for users, configure rules in the forward chain. Input is only for traffic targeting the router.”
Extract from MikroTik Wiki – Firewall Overview:
“forward: filters all traffic going through the router. For user access restrictions, place rules here.”
MikroTik RouterOS commands can be run once a day by:
/system watchdog
/system cron
/system scheduler
MikroTik RouterOS uses the /system scheduler to execute scripts or commands at defined times or intervals. It allows for automation of tasks such as backups, reboots, updates, and more.
Evaluation:
A. /system watchdog →❌Used for hardware monitoring and rebooting if the system freezes.
B. /system cron →❌Not available in MikroTik RouterOS (RouterOS doesn’t use cron syntax).
C. /system scheduler →✅Correct. Built-in RouterOS feature for scheduled command execution.
MTCNA Course Manual – System Scheduler Section:
“Use /system scheduler to run scripts or commands at regular intervals or specific times.”
René Meneses Guide – Automating Tasks:
“Scheduler is the only built-in time-based job handler in RouterOS.”
Terry Combs Notes – Script Automation:
“RouterOS uses scheduler, not cron. Schedule by time or interval.”
Answer: CQUESTION NO: 67 [Firewall / Tools]
Where can you monitor (see addresses and ports) real-time connections which are processed by the router?
A. Firewall Connection Tracking
B. Firewall Counters
C. Tool Torch
D. Queue Tree
Answer: A
Firewall Connection Tracking (also known as conntrack) is used to monitor real-time connections that pass through the router. It shows source and destination IPs, ports, protocols, connection states (established, new, related), and more.
Let’s evaluate the options:
A.✅Correct – Shows live connection table with IPs, ports, and statuses
B.❌Shows rule match counters only — no detailed connection info
C.❌Torch shows per-interface traffic; useful for bandwidth, but not a connection list
D.❌Queue Tree is used for traffic shaping, not for viewing connections
MTCNA Course Manual – Firewall Concepts:
“Connection tracking shows all active sessions through the router with IP and port details.”
René Meneses Guide – Firewall Tools:
“Use connection tracking to diagnose connection states and NAT behavior.”
Terry Combs Notes – Monitoring Tools:
“conntrack is your real-time connection monitor. Torch is per-interface, not per-flow.”
Answer: AQUESTION NO: 68 [Wireless]
How many wireless clients can connect, when wireless card is configured to mode=bridge?
A. 1
B. 100
C. 2007
D. 2
Answer: A
In MikroTik RouterOS, if a wireless card is configured to mode=bridge (also referred to as "station-bridge"), it can only be used to connect a single client device (MAC address) behind it. This is due to limitations in how 802.11 bridges MAC addresses.
So:
A.✅Correct – Only 1 MAC address can pass via wireless bridge mode (unless using WDS or 4-address mode)
B, C →❌Too many clients for bridge mode
D.❌Incorrect – Still only one client allowed per interface in bridge mode
MTCNA Wireless Module – Wireless Modes:
“Bridge mode allows one client only unless extended bridging protocols are used.”
René Meneses Guide – Wireless Bridging:
“mode=bridge = one MAC behind the station. Use WDS for multiple MACs.”
Terry Combs Notes – Wireless Modes:
“Station-bridge mode works like Ethernet, but only supports one MAC address unless using WDS.”
Answer: AQUESTION NO: 69 [Routing]
In the Route List, the identification DAb for a route stands for:
A. direct - active - bgp
B. direct - acknowledge - backup
C. dynamic - active - backup
D. dynamic - active - bgp
Answer: D
In MikroTik RouterOS, route flags provide quick insight into how the route was created and its status:
D = Dynamic → The route was added dynamically by a protocol (like BGP, OSPF, RIP)
A = Active → This route is currently being used
b = BGP → Indicates that the route was learned via the BGP routing protocol
Therefore, DAb means:
→ D = Dynamic
→ A = Active
→ b = BGP
MTCNA Routing Section – Route Flags Explanation:
“D = dynamically added, A = currently active, b = learned via BGP.”
René Meneses Guide – Understanding Route Lists:
“DAb → dynamic + active + BGP route. Route is learned and installed via BGP.”
Terry Combs Notes – Route Symbols:
“Check the route list: b = BGP, o = OSPF, r = RIP, s = static, c = connected.”
Action=redirect is applied in:
chain=srcnat
chain=forward
chain=dstnat
The redirect action is only valid in the dstnat chain. It is used to redirect traffic to a service running on the router itself (e.g., redirecting HTTP to a local proxy server).
A.✘srcnat – Not compatible with redirect
B.✘forward – Redirect doesn’t apply in this chain
C.✔dstnat – This is the correct and only supported chain for action=redirect
Extract from Official MTCNA Course Material – NAT Actions:
“The redirect action is used within the dstnat chain to forward packets to the router’s local services.”
Extract from MikroTik Wiki – NAT Rule Actions:
“Redirect is used in dstnat chain and changes destination address to a local router IP and port.”
===========
What is marked by connection-state=established matcher?
Packet belongs to an existing connection, for example a reply packet or a packet which belongs to already replied connection
Packet is related to, but not part of an existing connection
Packet does not correspond to any known connection
Packet begins a new TCP connection
The connection-state=established matcher in MikroTik’s firewall refers to packets that are part of an already active connection. These packets are neither new nor related — they are directly associated with a known connection that has been previously accepted or initiated.
MikroTik uses Connection Tracking (enabled by default) to determine the state of each packet:
new: Packet begins a new connection (e.g., TCP SYN)
established: Packet belongs to a previously established connection (reply or subsequent packets)
related: Packet is not part of the connection, but is related (e.g., FTP data channel)
invalid: Packet that does not match any known or valid connection
Therefore:
A.✅Correct. “Established” means part of an ongoing, known connection.
B.❌This describes “related”
C.❌This describes “invalid”
D.❌This describes “new”
MTCNA Course Manual – Firewall and Connection Tracking:
“Established – Packet that belongs to an existing connection. This includes replies and ongoing streams.”
René Meneses Study Guide – Firewall Fundamentals:
“Use connection-state=established to allow traffic that is part of previously accepted sessions.”
Terry Combs Notes – Connection States:
“Established = trusted, ongoing session. Essential for return traffic.”
Answer: AQUESTION NO: 32 [PPP]
PPP Secrets are used for:
A. PPPoE clients
B. L2TP clients
C. IPSec clients
D. PPP clients
E. PPTP clients
F. Router users
Answer: A, B, D, E
PPP Secrets is a user authentication mechanism used in MikroTik RouterOS for various PPP-based services. These include:
PPP (Point-to-Point Protocol)
PPPoE (PPP over Ethernet)
PPTP (Point-to-Point Tunneling Protocol)
L2TP (Layer 2 Tunneling Protocol)
Each client authenticates with a username/password combination defined under PPP → Secrets. PPP Secrets is not used for:
IPSec clients →❌They use peer configurations and policies
Router users (Winbox/WebFig) →❌Use system → users, not PPP secrets
MTCNA PPP Chapter – Secrets Authentication:
“PPP Secrets are used for all PPP services: PPP, PPPoE, L2TP, and PPTP. It defines usernames, passwords, profiles, and IP bindings.”
René Meneses Guide – Tunnels and PPP:
“Any PPP-based tunnel uses PPP secrets for login validation. This includes local dial-in and remote VPN tunnels.”
Terry Combs Notes – PPP Authentication Table:
“PPP Secrets = for PPP, PPPoE, PPTP, and L2TP. Not for IPSec or Winbox.”
Answer: A, B, D, EQUESTION NO: 33 [Licensing]
How long is level 1 (free) license valid?
A. 1 month
B. 24 hours
C. 1 year
D. Infinite time
Answer: D
Level 1 license in MikroTik RouterOS is a free license type. It is included with every installation but has very limited functionality. Despite the limitations, it is valid for an unlimited duration.
Features available in level 1:
Basic configuration
One active user session
Ideal for lab/testing with CHR
Incorrect options:
A. 1 month →❌Not time-based
B. 24 hours →❌No expiration limit
C. 1 year →❌Invalid
D.✅Correct → Valid forever, but feature-limited
MTCNA Course Material – Licensing Section:
“Level 1 license is free and does not expire. It provides minimal feature access.”
René Meneses Study Guide – License Levels:
“Level 1 is permanent but restrictive. Great for evaluation or learning.”
Terry Combs Notes – RouterOS Licensing Table:
“Level 1 license = lifetime access to basic RouterOS functionality.”
Answer: DQUESTION NO: 34 [NAT]
What is the correct action for a NAT rule on a router that should intercept SMTP traffic and send it over to a specified mail server?
A. tarpit
B. dst-nat
C. passthrough
D. redirect
Answer: B
To forward traffic from one destination to another (such as from the public IP to an internal mail server), the dst-nat action is used in MikroTik NAT rules.
dst-nat: Modifies the destination IP address and/or port of the packet. Used to forward traffic to an internal resource.
tarpit: Captures and holds TCP connections (used for spam traps or slowing down bots) →❌
passthrough: Used in mangle rules; allows the packet to be evaluated by the next rule →❌
redirect: Redirects traffic to the router itself (e.g., proxy or DNS services) →❌
So, for external SMTP traffic (e.g., TCP port 25), we use a dst-nat rule that forwards the traffic to the internal mail server.
MTCNA NAT Section – Destination NAT:
“To forward SMTP traffic from a public address to a private server, use dst-nat with appropriate port and IP.”
René Meneses Guide – Practical NAT Examples:
“Use dst-nat for port forwarding. Redirect is for internal services like DNS or web proxy.”
Terry Combs Notes – NAT Action Summary:
“dst-nat = most common for external-to-internal mapping (e.g., mail servers, web servers).”
To use masquerade, you need to specify:
action=accept, out-interface, chain=src-nat
action=masquerade, out-interface, chain=src-nat
action=masquerade, in-interface, chain=src-nat
action=masquerade, out-interface, chain=dst-nat
Masquerading is a form of source NAT (src-nat) where the router dynamically replaces the source address of outgoing packets with the IP address of the router’s outgoing interface. This is commonly used when internal LAN clients access the internet through a single public IP.
Key points for masquerade configuration:
Use chain=src-nat (because it modifies the source address)
Use action=masquerade
Specify the out-interface (i.e., the WAN interface)
MTCNA Course Material – NAT Section:
“To configure masquerading, use chain=src-nat and action=masquerade. Specify out-interface to define the traffic direction.”
René Meneses MTCNA Study Guide – NAT Examples:
“Masquerade automatically uses the IP address of the specified out-interface. Required parameters: chain=src-nat, action=masquerade, out-interface.”
MikroTik Wiki – Source NAT / Masquerade:
“Masquerade is a special form of src-nat. You must use it in chain=src-nat and define the out-interface for which NAT will be applied.”
Option A: Incorrect action=accept (used in filter rules, not NAT)
Option C: in-interface is not applicable here
Option D: chain=dst-nat is used for destination NAT, not source NAT
Only Option B is fully correct.
Final Answer: BQUESTION NO: 94 [Tools]
In which situations can Netinstall NOT be used to install a RouterBOARD?
A. The router does not have an operating system
B. The router is connected only to a wireless network
C. You do not know the password of the router
D. The router is connected only to a secondary Ethernet port
Answer: B
Netinstall works over a wired Ethernet connection and uses PXE or Etherboot to install RouterOS over the network. It cannot function over wireless, as wireless interfaces do not support PXE booting or Netinstall protocols.
MTCNA Course Material – Netinstall Overview:
“Netinstall requires a direct Ethernet connection between the PC and the router. Wireless interfaces are not supported for Netinstall procedures.”
René Meneses MTCNA Guide – Netinstall:
“Netinstall only works over Ethernet. You cannot Netinstall a device connected only through Wi-Fi.”
MikroTik Wiki – Netinstall Prerequisites:
“Router must be connected via Ethernet. Wireless and USB interfaces are not supported.”
Other options:
A: This is a typical use case (installing RouterOS when OS is missing)
C: Netinstall bypasses password (not needed)
D: Netinstall can work via any Ethernet port, provided it's accessible
Final Answer: BQUESTION NO: 95 [Monitoring and Logging]
MikroTik RouterOS is sending logs to an external syslog server. Which protocol and port is used by RouterOS for sending logs (by default)?
A. UDP 514
B. UDP 21
C. UDP 113
D. TCP 110
Answer: A
RouterOS uses the industry-standard syslog protocol for remote logging. By default, syslog uses UDP port 514.
MTCNA Course Material – Logging Section:
“For sending logs to a remote syslog server, RouterOS uses the syslog protocol on UDP port 514 by default.”
René Meneses MTCNA Guide – Monitoring & Logging:
“External logging is done using UDP port 514, which is the standard syslog protocol port.”
MikroTik Wiki – Logging Configuration:
“To send logs to a remote server, configure an action of type remote with a remote address and use UDP port 514 unless otherwise changed.”
Other ports:
UDP 21 = FTP (not logging)
UDP 113 = Ident protocol
TCP 110 = POP3
Only UDP 514 is correct.
Final Answer: AQUESTION NO: 96 [RouterBOARD Hardware]
Can you manually add drivers to RouterOS in case your PCI Ethernet card is not recognized, and you suspect it is a driver issue?
A. Yes
B. No
Answer: B
RouterOS is a closed, embedded Linux-based system. It does not support adding custom drivers or compiling modules manually. You must use supported hardware that is natively compatible with RouterOS.
MTCNA Course Material – RouterBOARD Compatibility:
“RouterOS supports a fixed set of drivers. You cannot install third-party drivers or modules.”
René Meneses MTCNA Guide – Hardware Limitations:
“Custom drivers cannot be added to RouterOS. Use only supported network interface cards as listed by MikroTik.”
MikroTik Wiki – Hardware Support:
“RouterOS does not allow manual driver installation. All drivers are precompiled and built into the system image.”
Therefore, if your PCI Ethernet card is not recognized, you must replace it with a compatible model — you cannot add a driver manually.
Which type of encryption could be used to establish a connection with a simple passkey without using a 802.1X authentication server?
WPA PSK/WPA2 PSK
WPA EAP/WPA2 EAP
Wireless encryption modes differ in how they authenticate clients:
WPA/WPA2 PSK (Pre-Shared Key): Uses a passphrase shared by all clients. No external authentication server (like RADIUS or 802.1X) is required. Simple and suitable for home or small networks.
WPA/WPA2 EAP: Uses 802.1X (Enterprise mode) and requires a centralized authentication server.
Option analysis:
A.✔Correct – Pre-Shared Key does not require 802.1X server
B.✘Incorrect – Requires EAP-based authentication with 802.1X infrastructure
Extract from Official MTCNA Course Material – Wireless Security:
“WPA PSK/WPA2 PSK uses a pre-shared password. WPA/WPA2 EAP requires 802.1X authentication with a RADIUS server.”
Extract from René Meneses MTCNA Study Guide – Wireless Encryption:
“To use a simple password for connecting wireless clients, select WPA2-PSK. It does not require server-based authentication.”
Extract from Terry Combs Notes – Wireless Security Profiles:
“WPA2 PSK = password-based; WPA2 EAP = 802.1X based. Use PSK for fast, simple authentication.”
You need to reboot a RouterBoard after importing a previously exported rsc file to activate the new configuration.
True
False
Importing an .rsc (exported) file immediately applies the configuration commands line by line. There is no need to reboot the router for the new settings to take effect. Some services may require restarting manually (e.g., DHCP server), but the RouterOS itself does not require a reboot after import.
Option analysis:
A.✘False–Reboot is not required
B.✔True–Import applies settings immediately during execution
Extract from MTCNA Course Material – Import Functionality:
“Import is immediate and command-by-command. No reboot is necessary unless instructed in the script.”
Extract from René Meneses Study Guide – Import and Export:
“When you import an .rsc file, the configuration takes effect as each command is executed. Reboot is not needed.”
Extract from MikroTik Wiki – Configuration Restore:
"The import file is executed in real-time. Any settings changed are applied immediately."
==================================
Mark all packages required for PPPoE server on MikroTik RouterOS
ppp
user-manager
radius
synchronous
system
The PPPoE server functionality in RouterOS relies primarily on the PPP package, which includes support for protocols like PPP, PPPoE, PPTP, L2TP, SSTP, etc. The system package is also always required, as it contains the core OS components.
Option breakdown:
A.✔ppp – Required. Contains all PPP and PPPoE server/client implementations.
B.✘user-manager – Optional. Used for advanced AAA (authentication/accounting), not required for basic PPPoE.
C.✘radius – Optional. Used for external authentication, not essential unless RADIUS integration is needed.
D.✘synchronous – Used for legacy synchronous interfaces (e.g., serial or modem), not for PPPoE.
E.✔system – Required for all RouterOS functions.
Extract from Official MTCNA Course Material – RouterOS Packages:
“To enable PPPoE server functionality, you need the ppp and system packages. Radius and User Manager are optional.”
Extract from René Meneses MTCNA Study Guide – PPPoE Deployment:
“Only the ppp and system packages are strictly required. Additional features like radius are for centralized authentication.”
Extract from MikroTik Wiki – RouterOS Package Descriptions:
“ppp: required for PPP, PPTP, L2TP, PPPoE; system: required core package. user-manager and radius are optional.”
===========
Select which of the following are 'Public IP addresses':
172.168.254.2
172.28.73.21
11.63.72.21
10.110.50.37
192.168.0.1
IP addresses are categorized as either public or private. According to the IANA (Internet Assigned Numbers Authority), the following are reserved for private use:
10.0.0.0 to 10.255.255.255 (Class A Private)
172.16.0.0 to 172.31.255.255 (Class B Private)
192.168.0.0 to 192.168.255.255 (Class C Private)
Any IP outside of these ranges is considered public and routable on the global internet.
Evaluation of each option:
A. 172.168.254.2 → This is in the 172.16.0.0 – 172.31.255.255 range → Private
B. 172.28.73.21 → Also falls in the same private 172.16.0.0/12 range → Private
C. 11.63.72.21 → Outside all private ranges → Public✅
D. 10.110.50.37 → In the 10.0.0.0/8 range → Private
E. 192.168.0.1 → In the 192.168.0.0/16 private range → Private
Extract from René Meneses MTCNA Study Guide:
“Private IP ranges include 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. These are non-routable over the public internet.”
Extract from Terry Combs Notes:
“Only IPs outside of the above ranges are considered public and routable. Watch out for 172.X.X.X — not all are public; only 172.0.0.0–172.15.255.255 and 172.32.0.0+ are public.”
MikroTik Wiki – IP Addressing Reference:
“Private addresses are not globally routable. They are used inside local networks and must be NATed for internet access.”
===========
What is the correct action to be specified in the NAT rule to hide a private network when communicating to the outside world?
masquerade
allow
passthrough
tarpit
In MikroTik RouterOS, the masquerade action is used in source NAT (srcnat) rules to hide internal/private IP addresses behind a router’s public IP address. This is typically done for internet access from a LAN where the devices have private IP addresses (e.g., 192.168.x.x).
Masquerade dynamically changes the source IP of outgoing packets to the IP address of the router’s outbound interface, allowing multiple internal devices to share a single public IP.
Let’s evaluate the options:
A. masquerade →✅Correct. Used to perform source NAT for hiding private addresses.
B. allow →❌Not a valid NAT action.
C. passthrough →❌Used in mangle rules to continue processing additional rules, not for NAT.
D. tarpit →❌Used to delay TCP connections (often in firewall, not NAT).
MTCNA Course Manual – NAT Chapter:
“Masquerade is a special form of source NAT where the router replaces the source IP with the IP address of the outgoing interface.”
René Meneses Guide – NAT Configuration:
“Use masquerade on the router’s WAN interface to give internet access to private clients.”
Terry Combs Notes – NAT Rule Actions:
“Masquerade = dynamic src-nat. Useful when public IP is dynamic or unknown.”
Answer: AQUESTION NO: 62 [PPP / AAA]
Router A and B are both running as PPPoE servers on different broadcast domains of your network. It is possible to set Router A to use "/ppp secret" accounts from Router B to authenticate PPPoE customers.
A. true
B. false
Answer: B
/ppp secret accounts are local to each RouterOS device. These credentials are stored in the router’s own configuration and cannot be shared directly between routers.
To centralize authentication across multiple routers, a RADIUS server must be used. With RADIUS, multiple MikroTik routers can authenticate users against a single, centralized user database.
Without RADIUS or another external AAA system:
Each router maintains its own /ppp secret list
Router A cannot directly read or use the /ppp secrets from Router B
Evaluation:
A.❌False. There is no built-in mechanism for Router A to access secrets on Router B.
B.✅Correct. You must use RADIUS if you want shared authentication across routers.
MTCNA PPP Module – Authentication Methods:
“/ppp secrets are stored locally on the router. For shared user authentication, configure RADIUS.”
René Meneses Study Guide – PPPoE and RADIUS:
“To authenticate clients on multiple routers with a central database, RADIUS is required.”
Terry Combs Notes – PPP Secrets vs RADIUS:
“Local secrets cannot be accessed remotely. Use RADIUS to centralize authentication.”
Answer: B
A client that has successfully connected to a wireless network is considered to be which of the following? Choose all that apply:
Authenticated
Associated
Unauthenticated
Unassociated
For a client to exchange data over a wireless network, it must complete two key steps:
Association – Establishes the basic radio link between client and access point
Authentication – Verifies credentials (e.g., WPA2 handshake)
When both are complete, the client is both authenticated and associated.
A.✔Authenticated – Encryption and access control is complete
B.✔Associated – Wireless radio link is established
C.✘Unauthenticated – Incorrect; client is verified
D.✘Unassociated – Incorrect; client is linked to AP
Extract from MTCNA Course Material – Wireless Client States:
“A connected client is associated (Layer 2) and authenticated (security/credentials verified).”
Extract from Terry Combs MTCNA Notes – Wireless States:
“Authenticated and associated are required for data transfer. Unassociated = disconnected.”
===========
In RouterOS queue configurations the word “total” usually represents:
download
upload + download
download - upload
upload
In MikroTik queues (especially in simple queues), the "total" limit typically refers to the combined rate of upload and download traffic — i.e., the total bandwidth usage. This is useful when you want to control the full traffic flow for a client or subnet.
A.✘Incorrect – Not just download
B.✔Correct – Total = Download + Upload combined
C.✘Incorrect
D.✘Incorrect – Upload alone is not referred to as "total"
Extract from MTCNA Course Material – Simple Queues:
“The total max-limit or total rate represents both upload and download combined.”
Extract from René Meneses MTCNA Study Guide – Queue Types:
“Use total max-limit to limit overall bandwidth. Individual directions can also be configured.”
Extract from MikroTik Wiki – Simple Queue Options:
“total-max-limit defines the sum of incoming and outgoing traffic rates.”
A PC with IP 192.168.1.2 can access internet, and static ARP has been set for that IP address on gateway. When the PC Ethernet card failed, the user changed it with a new card and set the same IP for it. What else should be done? [multiple answers]
Old static ARP entry on gateway has to be updated for the new card
Nothing – it will work as before
MAC-address of the new card has to be changed to MAC address of old card
Another IP has to be added for Internet access
When static ARP is configured, the router explicitly binds an IP address to a specific MAC address. This means:
If the MAC address of the device changes (as it does when a new network card is installed), and the IP remains the same, the router will not allow the device to communicate, because the MAC address in the ARP table no longer matches the new hardware.
Options explained:
A.✔Correct. The old ARP entry must be updated to reflect the new MAC address if the IP is reused.
B.✘Incorrect. The communication will fail if the ARP table still holds the outdated MAC for that IP.
C.✔Correct. Alternatively, if the new NIC supports MAC address modification, setting the MAC address to match the old one would make the static ARP entry valid again.
D.✘Incorrect. There's no need to change the IP if the static ARP entry is updated.
Extract from Official MTCNA Course Material – ARP Section:
"Static ARP entries tie IPs to MAC addresses. If the MAC changes but the static ARP entry remains unchanged, the device cannot communicate with the router."
Extract from René Meneses MTCNA Study Guide – ARP:
"When using static ARP, any MAC change must be reflected in the router's ARP table; otherwise, packets will be dropped."
Extract from MikroTik Wiki – ARP Modes:
"Static entries require matching MAC addresses. If the client's MAC changes, the ARP table must be updated or communication will fail."
===========
NAT rule is going to catch SMTP traffic and send it to a specific mail server. What is the correct action for a NAT rule?
passthrough
dst-nat
redirect
tarpit
To redirect SMTP (port 25) traffic from users to a specific internal or external SMTP server, you must use dst-nat. This modifies the destination address and port to point to the desired mail server.
A.✘passthrough – Allows the packet to be evaluated by other NAT rules; it doesn't alter traffic
B.✔dst-nat – Rewrites destination IP/port; this is what is needed to redirect SMTP to a specific server
C.✘redirect – Sends traffic to the router itself; not suitable for external redirection
D.✘tarpit – Used for slowing down malicious TCP connections, not redirection
Extract from MTCNA Course Material – NAT Types:
“Use dst-nat to change the destination IP address. This is suitable for port forwarding or service redirection.”
Extract from René Meneses Study Guide – NAT Rules:
“To redirect traffic to a specific server, use action=dst-nat and specify the new destination address.”
===========
What does this simple queue do (check the image)?
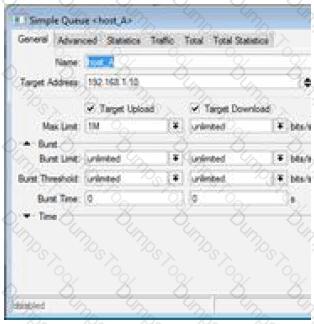
The screenshot shows a Simple Queue named "host_A" with:
Target Address: 192.168.1.10
Target Upload: Checked
Target Download: Checked
Max Limit: 1M (upload), unlimited (download)
Queue guarantees upload data rate of one megabit per second for host 192.168.1.10
Queue limits host 192.168.1.10 download data rate to one megabit per second.
Queue limits host 192.168.1.10 upload data rate to one megabit per second.
Queue guarantees download data rate of one megabit per second for host 192.168.1.10
The “Max Limit” value in MikroTik Simple Queues defines the maximum allowed bandwidth. In this case:
Target Address: 192.168.1.10
Target Upload = 1M → The host can upload at a maximum of 1 Mbps
Target Download = unlimited → No restriction on download
This does not “guarantee” bandwidth — it enforces a ceiling. A guaranteed rate would require "Limit-at" to be set.
Evaluation:
A.❌This queue limits, it does not guarantee a minimum bandwidth.
B.❌Download is set to unlimited — no limitation.
C.✅Upload is limited to 1 Mbps — correct.
D.❌Download rate is unlimited — no guarantee or limit.
MTCNA Course Manual – Simple Queue Explanation:
“Max-limit sets the maximum throughput for upload/download. It’s a ceiling, not a guarantee.”
René Meneses Guide – Simple Queues Explained:
“In this case, upload is capped at 1M. No burst or download limit is applied.”
Terry Combs Notes – Queue Properties:
“Always distinguish between 'limit-at' (minimum guarantee) and 'max-limit' (maximum cap).”
From which of the following locations can you obtain Winbox?
Router’s webpage
Files menu in your router
Via the console cable
mikrotik.com
Winbox is a small, native Windows utility provided by MikroTik for graphical administration of RouterOS devices. It is typically downloaded from MikroTik's official website.
A. Router’s webpage → Incorrect. While the router’s WebFig interface may allow configuration, it does not offer a Winbox download.
B. Files menu → Incorrect. The Files menu is for storing backups or firmware packages, not distributing Winbox.
C. Console cable → Incorrect. Console access is CLI only; no GUI utilities can be transferred through it.
D. mikrotik.com → Correct. The only official and secure location to download Winbox is the MikroTik website.
Extract from Official MTCNA Course Material – RouterOS Introduction:
“Winbox can be downloaded from the official MikroTik website. It provides a GUI frontend for managing RouterOS.”
Extract from René Meneses MTCNA Study Guide – RouterOS Access Methods:
“You can download Winbox from mikrotik.com under the Software Tools section.”
Extract from Terry Combs MTCNA Notes – Access Methods:
“Winbox is a Windows application that must be downloaded from MikroTik’s website. It is not available directly from the router.”
===========
Which of the following is NOT a valid MAC Address?
80:GF:AA:67:13:5D
95:B5:DD:EE:78:8A
88:0C:00:99:5F:EF
EA:BA:AA:EE:FF:CB
13:16:86:53:89:43
AMAC (Media Access Control) addressis aunique identifier assigned to network interfacesfor communications at the data link layer (Layer 2 of the OSI model). A MAC address is:
Always48 bits(6 bytes) long
Represented in12 hexadecimal characters
Grouped into6 pairsseparated by colons or dashes (e.g., 00:1A:2B:3C:4D:5E)
Contains onlyhexadecimal characters (0-9, A-F)
Extract fromRené Meneses MTCNA Study Guide:
“A MAC address is a 48-bit value, represented as 6 groups of two hexadecimal digits (00 to FF). Any character outside this range is not valid. For example, 80:GF:AA:67:13:5D is invalid because ‘G’ is not a valid hexadecimal digit.”
Extract fromTerry Combs MTCNA Notes – MAC Addressing Section:
“Valid MAC addresses contain only 0-9 and A-F. A common mistake in training exams is to insert an invalid character like G or H into a MAC, which instantly makes it incorrect.”
Extract fromMikroTik Wiki – MAC Address Format Page:
“MAC addresses are six octets long and use hexadecimal format only. Hexadecimal numbers go from 0–9 and A–F. If a character appears outside that range, the address is invalid.”
Now let’s evaluate each option:
Option A: 80:GF:AA:67:13:5D❌Contains the letter"G", whichdoes not belong to the hexadecimal system. That makes this addressinvalid.
Option B: 95:B5:DD:EE:78:8A✅All characters are valid hex (9, 5, B, D, E, 7, 8, A)
Option C: 88:0C:00:99:5F:EF✅All valid characters.
Option D: EA:BA:AA:EE:FF:CB✅Hex only — valid.
Option E: 13:16:86:53:89:43✅Also valid hex — no issue.
So,Option A is the only invalid MAC address.
In MikroTik RouterOS, Layer 3 communication between 2 hosts can be achieved by using an address subnet of:
/31
/29
/32
/30
In traditional IPv4 subnetting, a /30 is often used to connect two hosts directly, giving two usable IPs. However, MikroTik RouterOS (and as per RFC 3021) supports the use of /31 subnet masks for point-to-point links. A /31 provides exactly two IP addresses — which are both usable — and is ideal for conserving IP space on router-to-router links.
Subnet details for /31:
Total addresses: 2
Usable addresses: 2 (both can be assigned to endpoints, no broadcast)
Evaluation:
A. /31 →✅Supported by MikroTik for point-to-point links (2 hosts only)
B. /29 → Provides 6 usable IPs; more than needed for 2 hosts
C. /32 → Single host only; no communication possible with second device
D. /30 → Valid, but less efficient than /31
MTCNA Course Manual – IP Addressing and Point-to-Point Communication:
“MikroTik RouterOS allows the use of /31 subnets for point-to-point communication. Both IPs are usable.”
René Meneses MTCNA Guide – IP & Routing Concepts:
“For links between exactly two devices, /31 saves address space and is supported by MikroTik.”
Terry Combs Notes – Subnet Efficiency:
“Use /30 or /31 for point-to-point links. MikroTik supports /31 fully, unlike older systems.”
Answer: AQUESTION NO: 17 [Monitoring and Logging]
Which of the following protocols/ports are used for SNMP (Simple Network Management Protocol)?
A. TCP 25
B. TCP 161
C. UDP 162
D. TCP 162
E. TCP 123
F. UDP 161
Answer: C, F
SNMP uses UDP as its transport protocol. The standard ports are:
UDP port 161 → used for SNMP queries (polling)
UDP port 162 → used for SNMP traps (asynchronous alerts)
Incorrect options:
A. TCP 25 → SMTP (email), not related to SNMP
B. TCP 161 → SNMP does not use TCP
D. TCP 162 → Incorrect; SNMP traps use UDP
E. TCP 123 → NTP (Network Time Protocol)
Correct answers:
C. UDP 162✅
F. UDP 161✅
MTCNA Course – Monitoring Tools & SNMP:
“SNMP operates over UDP. Port 161 is used for polling, and port 162 is used for traps.”
René Meneses MTCNA Guide – SNMP Overview:
“SNMP uses UDP 161 and 162 for communication between manager and agents.”
Terry Combs Notes – Protocol and Port Summary:
“Remember: SNMP = UDP 161/162. Do not confuse with TCP-based protocols.”
Answer: C, FQUESTION NO: 18 [RouterOS Introduction]
Which of the following are valid IP addresses?
A. 10.10.14.0
B. 192.168.256.1
C. 192.168.13.255
D. 1.27.14.254
Answer: A, C, D
An IPv4 address is a 32-bit number divided into 4 octets. Each octet must be between 0 and 255.
Let’s evaluate:
A. 10.10.14.0 →✅Valid; .0 is legal, may represent a network or host depending on subnet
B. 192.168.256.1 →❌Invalid; 256 exceeds the max octet value (0–255)
C. 192.168.13.255 →✅Valid broadcast or host IP, depending on subnet
D. 1.27.14.254 →✅All octets are within valid range
MTCNA Training Manual – IP Basics:
“Each octet must be between 0 and 255. Addresses like 192.168.256.1 are invalid.”
René Meneses Guide – Valid IP Criteria:
“Watch for octets above 255 — they are illegal in IPv4.”
Terry Combs Notes – Address Format Validation:
“Decimal format must be checked — 256, 999, or negative values break IPv4 standards.”
Answer: A, C, DQUESTION NO: 19 [Routing]
The network address is:
A. The first address of the subnet
B. The first usable address of the subnet
C. The last address of the subnet
Answer: A
The network address is the first IP address in a subnet. It identifies the entire network segment and cannot be assigned to any host.
For example, in 192.168.1.0/24:
192.168.1.0 → Network Address (non-assignable)✅
192.168.1.1 – 192.168.1.254 → Usable host addresses
192.168.1.255 → Broadcast address
Clarifying:
A. First address of the subnet →✅Correct
B. First usable address →❌That would be second address
C. Last address of the subnet →❌That’s the broadcast
MTCNA Course Manual – Subnet Addressing:
“The first address in a subnet is reserved as the network ID. It cannot be assigned to a host.”
René Meneses Guide – Network and Broadcast Addresses:
“Network address = first IP in block, broadcast = last. Usable range lies in between.”
Terry Combs Notes – Host and Network Addressing:
“Always subtract 2 IPs: one for network and one for broadcast. Never assign .0 (network address) to a host.”
Mark all the features that can be used for limiting client registrations to your access point:
access-list
wpa
WDS
registration-table
MikroTik allows you to control which clients can connect to your access point through:
WPA/WPA2 security – prevents unauthorized devices from authenticating.
Access List – filters by MAC address and signal strength.
Option breakdown:
A.✔access-list – Used to accept/reject client MACs and customize access settings.
B.✔wpa – WPA/WPA2 passphrase restricts who can join the network.
C.✘WDS – Wireless Distribution System, used for bridging, not access control.
D.✘registration-table – A monitoring tool showing currently connected clients; it doesn’t restrict connections.
Extract from Official MTCNA Course Material – Wireless Access Control:
“Use WPA/WPA2 for secure authentication. Access List lets you accept or reject clients based on MAC or signal level.”
Extract from René Meneses MTCNA Study Guide – Wireless Security & Filtering:
“You can limit client access using WPA security and Access List. Registration Table only shows connected users.”
Extract from Terry Combs Notes – Wireless Configuration:
“Access control = WPA + Access List. WDS is for bridging, and registration-table is read-only.”
What flavor of Network Address Translation can be used to have one IP address allow many users to connect to the global Internet?
NAT
Static
Dynamic
PAT
PAT (Port Address Translation) is a subtype of NAT that maps multiple private IP addresses to a single public IP address using different port numbers. It is the most common form of NAT used in home and business networks to allow multiple internal hosts to access the internet using one public IP address.
MTCNA Course Material – NAT Concepts:
“PAT (also known as NAT overload) allows multiple devices to share a single public IP address. It uses different port numbers to distinguish sessions.”
Cisco IOS NAT Configuration Guide:
“PAT translates multiple local IP addresses to one public IP address by assigning different port numbers to each session.”
Other options:
A: Generic term — not specific enough
B: Static NAT maps one private IP to one public IP
C: Dynamic NAT maps private IPs to a pool of public IPs, not one-to-many
Final Answer: DQUESTION NO: 149 [IPv6 – Addressing Standards]
How long is an IPv6 address?
A. 32 bits
B. 128 bytes
C. 64 bits
D. 128 bits
Answer: D
IPv6 addresses are 128 bits in length, represented as eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). This allows for a vastly larger address space compared to IPv4 (32 bits).
MTCNA Course Material – IPv6 Basics:
“An IPv6 address is 128 bits long, providing 3.4×10^38 possible addresses. It is written in hexadecimal format.”
René Meneses MTCNA Study Guide – IPv6 Addressing:
“IPv6 = 128 bits, not bytes. Address includes a 64-bit network prefix and 64-bit interface identifier.”
Other options:
A: 32 bits is IPv4
B: 128 bytes = 1024 bits — incorrect
C: 64 bits = only half of an IPv6 address
Final Answer: DQUESTION NO: 150 [IP Addressing – Subnetting]
How many usable IP addresses are there in a 23-bit (255.255.254.0) subnet?
A. 512
B. 510
C. 508
D. 254
Answer: B
A /23 subnet provides 2^9 = 512 total addresses.
Subtract 2 (network address + broadcast address)
512 – 2 = 510 usable IP addresses
MTCNA Course Material – Subnet Calculations:
“For any subnet, usable hosts = 2^(32 – subnet mask bits) – 2.”
René Meneses MTCNA Study Guide – IP Subnetting:
“/23 provides 512 total addresses; usable = 510 after subtracting network and broadcast.”
Option Breakdown:
A: Total addresses (512)
B:✔Usable addresses (510)
C: Incorrect (508 is for /23 minus 4 — not relevant here)
D: 254 is usable for /24
Which default route will be active?
/ip route
add disabled=no distance=10 dst-address=0.0.0.0/0 gateway=1.1.1.1
add disabled=no distance=5 dst-address=0.0.0.0/0 gateway=2.2.2.2
Route via gateway 2.2.2.2
Route via gateway 1.1.1.1
In MikroTik RouterOS (and in routing in general), the "distance" value determines the priority of a route. The route with the lowest distance will be preferred.
Here:
Route to 0.0.0.0/0 via 1.1.1.1 has distance = 10
Route to 0.0.0.0/0 via 2.2.2.2 has distance = 5 → lower, so preferred✅
Unless the lower-distance route is invalid or unreachable, it will always be selected.
MTCNA Course Manual – Static Routing:
“The lower the distance value, the higher the route’s priority. Routes are selected based on administrative distance first.”
René Meneses Study Guide – Route Distance:
“A route with distance 1 is preferred over a route with distance 2. It does not matter which was added first.”
Terry Combs Notes – Routing Behavior:
“RouterOS evaluates the distance (priority) before anything else. Smallest value wins.”
Answer: AQUESTION NO: 44 [Firewall]
What does the firewall action "Redirect" do? Select all true statements.
A. Redirects a packet to a specified port on the router
B. Redirects a packet to a specified IP
C. Redirects a packet to the router
D. Redirects a packet to a specified port on a host in the network
Answer: A, C
The redirect action in MikroTik’s NAT firewall rules is used to force traffic (usually from LAN clients) to a local service on the router — for example, redirecting all DNS queries to the router’s DNS server, or forcing web traffic to a proxy.
Details:
It changes the destination IP to the router's IP automatically (without needing to specify it)
It also allows port redirection (e.g., dst-port=80 → to 3128 for proxy)
Evaluation:
A.✅True — You can redirect to a specific port on the router
B.❌False — Redirect does not change destination IP to an arbitrary host; for that, use dst-nat
C.✅True — Redirect forces traffic to the router itself
D.❌False — dst-nat is used to forward packets to internal hosts, not redirect
MTCNA Course Manual – NAT Actions:
“Redirect action changes destination to the router itself. This is useful for forcing traffic through router services.”
René Meneses Guide – NAT Behavior:
“Redirect = router-local services like DNS or proxy. Use dst-nat for remote hosts.”
Terry Combs Notes – Firewall Actions:
“Use redirect when you want to intercept traffic and handle it locally on the router.”
Answer: A, CQUESTION NO: 45 [PPP / Tunnels]
Which port does PPTP use by default?
A. TCP 1721
B. UDP 1723
C. TCP 1723
D. UDP 1721
Answer: C
PPTP (Point-to-Point Tunneling Protocol) uses:
TCP port 1723 for control and session initiation
GRE (Generic Routing Encapsulation) protocol (protocol number 47) for tunneling
No UDP port is used by PPTP.
Evaluation:
A. TCP 1721 →❌Invalid port
B. UDP 1723 →❌Incorrect protocol (TCP is used, not UDP)
C.✅TCP 1723 → Correct
D.❌Invalid (wrong protocol and port)
MTCNA Tunneling Section – PPTP Overview:
“PPTP uses TCP port 1723 for control and GRE protocol for tunneling traffic.”
René Meneses MTCNA Guide – PPTP Characteristics:
“PPTP = TCP/1723 + GRE (not a port, but a protocol). Allow both on firewall.”
Terry Combs Notes – VPN Protocol Reference:
“PPTP: TCP 1723. GRE must be permitted for tunnel data.”
Answer: CQUESTION NO: 46 [Firewall]
Which firewall chain should you use to filter ICMP packets from the router itself?
A. input
B. postrouting
C. forward
D. output
Answer: D
MikroTik RouterOS uses firewall chains to process packets based on direction:
input: For packets destined to the router itself (from outside)
output: For packets originating from the router (e.g., router pings)
forward: For packets passing through the router between interfaces
postrouting: Used for NAT and marking, not filtering
Therefore:
To block/allow ICMP (ping) generated by the router (e.g., netwatch, DNS probes), use the output chain
To block incoming pings to the router, use input
To block pings between LAN and WAN, use forward
MTCNA Firewall Module – Chain Responsibilities:
“To control traffic originating from the router itself, use the output chain. For example, when the router itself sends ICMP requests.”
René Meneses Guide – Firewall Chains Explained:
“output is for locally generated traffic. input is for inbound traffic to the router.”
Terry Combs Notes – Chain Use Cases:
“Ping from router = output. Ping to router = input. Ping between networks = forward.”
In WinBox when clicking the 'Backup' button in the Files window, the following happens (select all that apply):
Backup file is created. Name contains the router identity, the date and time of its creation
Backup file is saved to the computer desktop
Backup file will contain usernames and passwords of the router
Optionally backup name and password can be specified
The “Backup” function in WinBox (located under Files → Backup) creates a binary backup file (.backup) of the router’s full configuration, including sensitive data like usernames, passwords, IPsec keys, wireless keys, etc.
A.✔Correct – By default, the backup file name includes the router identity and timestamp.
B.✘Incorrect – The file is saved on the router’s internal storage (Files menu), not on the user’s computer. You must download it manually to store it locally.
C.✔Correct – Unlike an “Export” file, a .backup file includes all configuration, including encrypted credentials.
D.✔Correct – You can specify a name and optionally a password to encrypt the backup.
Extract from MTCNA Course Material – Backup & Restore:
“The backup file includes all settings and can be encrypted with a password. It is saved on the router under the Files menu.”
Extract from René Meneses Study Guide – Backup Options:
“A .backup file contains everything including usernames and secrets. You can assign a filename and encryption password.”
Extract from Terry Combs Notes – Backup and Export:
“Backup saves a full binary copy. Use the download button to copy it to your PC.”
===========
Which computers would be able to communicate directly (without any routers involved)?
192.168.17.15/29 and 192.168.17.20/28
10.5.5.1/24 and 10.5.5.100/25
10.10.0.17/22 and 10.10.1.30/23
192.168.0.5/26 and 192.168.0.100
To determine if two hosts can communicate directly, their IP addresses must:
Belong to the same subnet
Have matching subnet boundaries (based on their masks)
Let’s evaluate each:
A. 192.168.17.15/29 → Subnet: 192.168.17.8 – 192.168.17.15
192.168.17.20/28 → Subnet: 192.168.17.16 – 192.168.17.31
→ Different subnets →❌
B. 10.5.5.1/24 → Subnet: 10.5.5.0 – 10.5.5.255
10.5.5.100/25 → Subnet: 10.5.5.0 – 10.5.5.127
→ Different masks → Host with /25 may treat others outside /25 as unreachable →❌
C. 10.10.0.17/22 → Range: 10.10.0.0 – 10.10.3.255
10.10.1.30/23 → Range: 10.10.0.0 – 10.10.1.255
→ Both addresses fall within same larger /22 range →✅
D. 192.168.0.5/26 → Subnet: 192.168.0.0 – 192.168.0.63
192.168.0.100 → Not enough info; assume default /24
→ /26 and /24 will not overlap fully → likely unreachable →❌
MTCNA Course Manual – IP Subnetting:
“Hosts can communicate directly if they are in the same IP range and have the same subnet mask. Different subnet boundaries require routing.”
René Meneses Guide – Mask Comparison:
“Be cautious of overlapping address ranges. Matching IPs in same range with differing subnet masks may fail to communicate.”
Terry Combs Notes – Direct Connectivity Rules:
“Same subnet mask and same address block = direct communication. If masks differ, communication needs a router.”
The DoD model (also called the TCP/IP stack) has four layers. Which layer of the DoD model is equivalent to the Network layer of the OSI model?
Application
Host-to-Host
Internet
Network Access
The TCP/IP or DoD model includes the following layers:
Application
Host-to-Host
Internet
Network Access
The Internet layer in the DoD model is responsible for logical addressing and routing — matching the function of the OSI model's Layer 3 (Network Layer), which handles IP addressing and packet forwarding.
MTCNA Course Material – TCP/IP vs OSI Model:
“The Internet layer of the TCP/IP model maps directly to the OSI’s Network Layer and is responsible for logical addressing and routing.”
René Meneses MTCNA Study Guide – Layer Mapping Table:
“TCP/IP Internet Layer = OSI Network Layer. Handles IP routing, addressing.”
Other mappings:
Application = OSI Layers 5–7
Host-to-Host = OSI Layer 4 (Transport)
Network Access = OSI Layers 1–2
Final Answer: CQUESTION NO: 114 [RouterOS Introduction – ARP]
Which of the following allows a router to respond to an ARP request that is intended for a remote host?
A. Gateway DP
B. Reverse ARP (RARP)
C. Proxy ARP
D. Inverse ARP (IARP)
Answer: C
Proxy ARP allows a router to answer ARP requests on behalf of another device. It is often used in networks where hosts don't have proper default gateways but still need to communicate with devices in different subnets.
MTCNA Course Material – ARP Types:
“Proxy ARP allows a router to respond to an ARP request for an IP address that is not on the local subnet, effectively acting as a proxy.”
René Meneses MTCNA Guide – ARP Configuration:
“Proxy ARP is useful for bridging two IP networks or for clients that do not have default gateways defined.”
MikroTik Wiki – ARP Modes:
“When Proxy ARP is enabled, the router replies to ARP requests for hosts that are not on the same subnet.”
Other options:
A: Gateway DP is not a standard term or protocol.
B: RARP maps MAC to IP — outdated and not used in this context.
D: Inverse ARP is used in Frame Relay, not Ethernet/IP networks.
Final Answer: CQUESTION NO: 115 [DHCP]
You want to implement a mechanism that automates the IP configuration, including IP address, subnet mask, default gateway, and DNS information. Which protocol will you use to accomplish this?
A. SMTP
B. SNMP
C. DHCP
D. ARP
Answer: C
DHCP (Dynamic Host Configuration Protocol) is specifically designed to assign IP configuration details automatically to clients on a network, including:
IP address
Subnet mask
Default gateway
DNS servers
MTCNA Course Material – DHCP Server Function:
“DHCP is a service that dynamically assigns IP settings to clients, removing the need for manual configuration.”
René Meneses MTCNA Study Guide – DHCP Operation:
“DHCP provides automatic configuration of network parameters including IP, mask, DNS, and gateway.”
Other options:
A: SMTP is for email
B: SNMP is for monitoring
D: ARP resolves IP-to-MAC addresses
Final Answer: CQUESTION NO: 116 [DHCP]
Which of the following describe the DHCP Discover message?
It uses FF:FF:FF:FF:FF:FF as a layer 2 broadcast.
It uses UDP as the Transport layer protocol.
It uses TCP as the Transport layer protocol.
It does not use a layer 2 destination address.
A. 1 only
B. 1 and 2
C. 3 and 4
D. 4 only
Answer: B
When a client sends a DHCP Discover message:
It does not yet have an IP address, so it sends a Layer 2 broadcast (FF:FF:FF:FF:FF:FF).
DHCP uses UDP, not TCP.
Specifically, it uses UDP port 67 (server) and 68 (client).
Layer 2 destination is broadcast — it certainly does use a Layer 2 address.
MTCNA Course Material – DHCP Process:
“The client broadcasts a DHCP Discover message to FF:FF:FF:FF:FF:FF using UDP ports 67 and 68.”
René Meneses MTCNA Study Guide – DHCP Message Types:
“DHCP uses UDP. Discovery messages are Layer 2 broadcasts to locate a DHCP server.”
MikroTik Wiki – DHCP Protocol Behavior:
“The Discover message uses UDP and broadcast MAC addressing.”
Statements:
1: True (Layer 2 broadcast)
2: True (Uses UDP)
3: False (TCP not used)
4: False (Layer 2 destination address is broadcast)
────────────────────────────────────────────────────────────
Action=redirect can be used in NAT chain src-nat
true
false
The action=redirect is used only in the dstnat chain to redirect traffic to a local port (e.g., for transparent proxy or DNS capture). It is not valid in the srcnat chain.
A.✘Incorrect – RouterOS will not permit redirect in srcnat.
B.✔Correct – redirect is only supported in dstnat.
Extract from Official MTCNA Course Material – NAT Actions:
“Redirect is used in the dstnat chain to force traffic to a specific port on the local router.”
Extract from MikroTik Wiki – NAT Action Reference:
“Action=redirect is only meaningful in dstnat and is used to redirect traffic to router-local services.”
Extract from René Meneses Study Guide – NAT Table:
“Redirect cannot be used in srcnat. Only valid in dstnat for local service interception.”
===========

TESTED 24 Feb 2026
Copyright © 2014-2026 DumpsTool. All Rights Reserved
