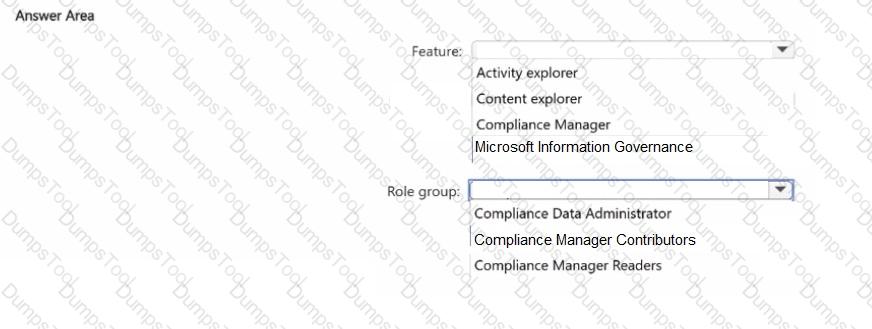
You have a Microsoft 365 E5 tenant that contains a trainable classifier named Classifier1.
You need to increase the accuracy of Classifier1. The solution must use the principle of least privilege.
Which feature should you use and to which role group should you be added? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
Users access their mailbox by using the following apps.
• Outlook for Microsoft 365
• Outlook on the web
• Outlook Mobile fiOS. Android)
You create a data loss prevention (DLP) policy named DLP1 that has the following settings:
• Location; Exchange email
• Status: On
• User notifications: On
• Notify users with a policy tip: Enabled
Which apps display a policy tip when content is matched by using DIP1 ?
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the device configurations shown in the following table.
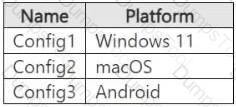
Each configuration uses either Google Chrome or Firefox as a default browser.
You need to implement Microsoft Purview and deploy the Microsoft Purview browser extension to the configurations.
To which configuration can each extension be deployed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You need to ensure that users can apply retention labels to individual documents in their Microsoft SharePoint libraries.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
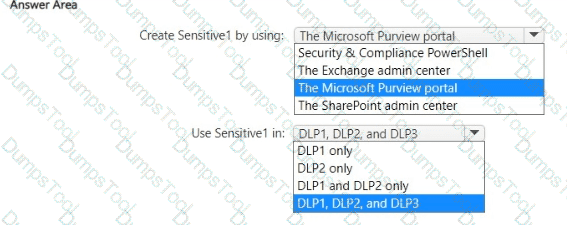
You have a Microsoft 365 E5 subscription that contains the data loss prevention (DLP) policies shown in the following table.
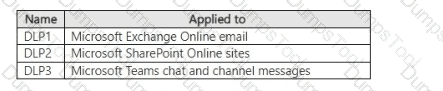
You have a custom employee information form named Template1 .docx.
You plan to create a sensitive info type named Sensitive! that will use the document fingerprint from Template1.docx.
What should you use to create Sensitive1, and in which DLP policies can you use Sensitive1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 36S ES subscription that contains the devices shown in the following table.
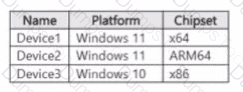
You publish Microsoft Purview Information Protection sensitivity labels.
You plan to deploy the information protection client to the devices. The solution must ensure that the labels can be applied to sensitive images and documents
On which devices can you install the information protection client, and what should users use to apply labels? To answer, select the appropriate options in the answer area.
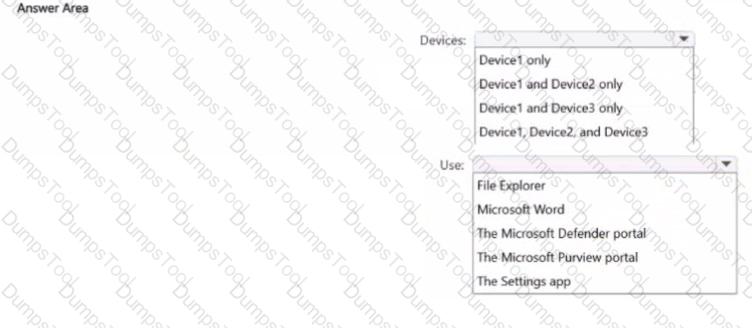
You have a Microsoft 365 E5 subscription.
You need to identify documents that contain patent application numbers containing the letters PA followed by eight digits, for example, PA 12345678. The solution must minimize administrative effort.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the adaptive scopes shown in the following table.
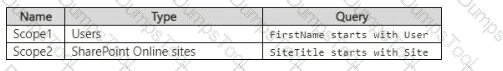
You create the retention policies shown in the following table.
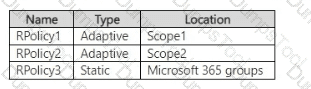
Which retention policies support a preservation lock?
Your company has a Microsoft 365 tenant.
The company performs annual employee assessments. The assessment results are recorded in a document named AssessmentTemplate.docx that is created by using a Microsoft Word template. Copies of the employee assessments are sent to employees and their managers.
The assessment copies are stored in mailboxes, Microsoft SharePoint Online sites, and OneDrive folders. A copy of each assessment is also stored in a SharePoint Online folder named Assessments.
You need to create a data loss prevention (DLP) policy that prevents the employee assessments from being emailed to external users. You will use a document fingerprint to identify the assessment documents. The solution must minimize effort.
What should you include in the solution?
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains the files shown in the following table.

In the Microsoft Purview portal, you create a content search named Conlent1 and configure the search conditions as shown in the following exhibit.

Which files will be returned by Content1?
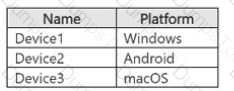
You have a Microsoft 36S subscription that contains the users shown in the following table.

You create the data loss prevention (DLP) policies shown in the following table.
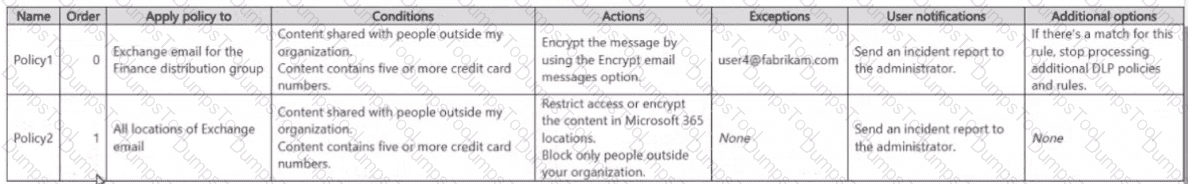
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that contains three users named U$er1, User2, and User3. The subscription contains the groups shown in the following table.
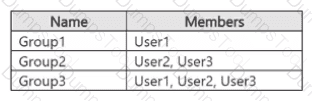
The subscription contains the devices shown in the following table.
All the devices are onboarded to Microsoft Purview.
You have the data loss prevention (DLP) policies shown in the following table.
You have a Microsoft 365 E5 subscription.
You need to prevent users from uploading data loss prevention (DLP)-protected documents to the following third-party websites:
● web1.contoso.com
● web2.contoso.com
The solution must minimize administrative effort.
To what should you set the Service domains setting for Endpoint DLP?
You have a Microsoft 365 £5 subscription.
You are implementing insider risk management.
You need to create an insider risk management notice template and format the message body of the notice template.
How should you configure the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 subscription.
You create a retention label named Label1 as shown in the following exhibit.
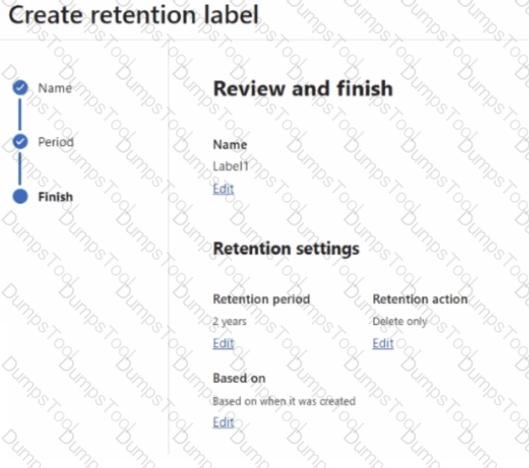
You publish Label! to SharePoint sites.
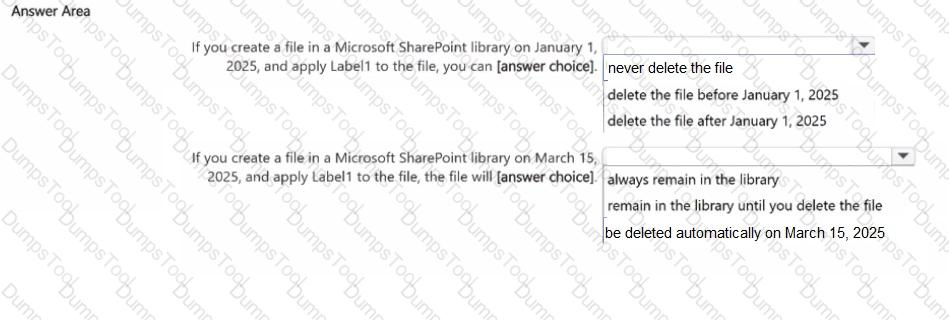
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From Microsoft Defender for Cloud Apps, you create an app discovery policy.
Does this meet the goal?
HOTSPOT
You have a Microsoft 365 E5 subscription. The subscription contains devices that are onboarded to Microsoft Purview and configured as shown in the following table.
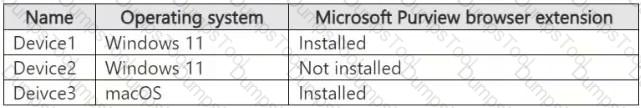
The subscription contains the users shown in the following table.

You need to review the activities.
What should you use for each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a retention policy named RP1 as shown in the following table.
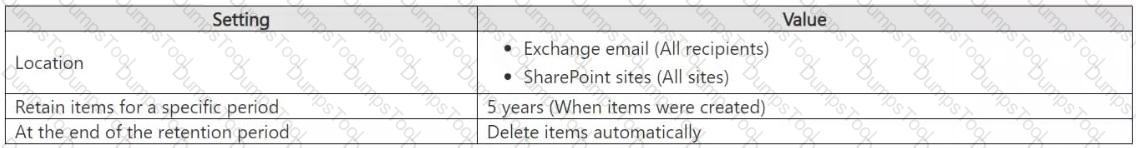
You place a preservation lock on RP1.
You need to modify RP1.
Which two modifications can you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 36S subscription that contains the sensitive information types (SITs) shown in the following exhibit.
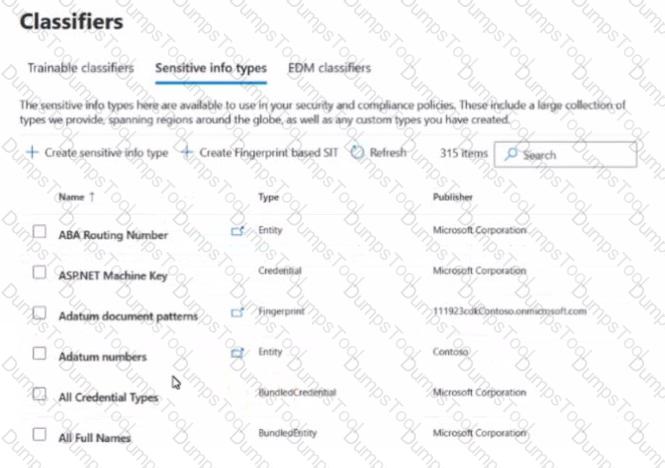
Use the drop-down menus To select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct flection is worth one point.
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.

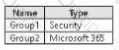
The subscription contains the groups shown in the following table.
You plan to create a priority user group named Priority1.
You need to identify the following:
. Which users and groups can be added to Priority1?
. Which users can be enabled to view alerts that involve the members of Priority1?
What should you identify? To answer, select the appropriate options in the answer area.

Your company has offices in multiple countries.
The company has a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management.
You plan to perform the following actions:
● In a new country, open an office named Office1.
● Create a new user named User1.
● Deploy insider risk management to Office1.
● Add User1 to the Insider Risk Management Admins role group.
You need to ensure that User1 can perform insider risk management tasks for only the users and the devices in Office1.
What should you create first?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview Audit (Premium) with the 10-Year Audit Log Retention add-on license.
The subscription contains the audit retention policies shown in the following table.
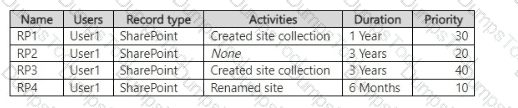
From the SharePoint Online admin center, User1 performs the actions shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
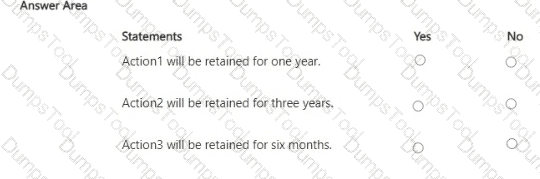
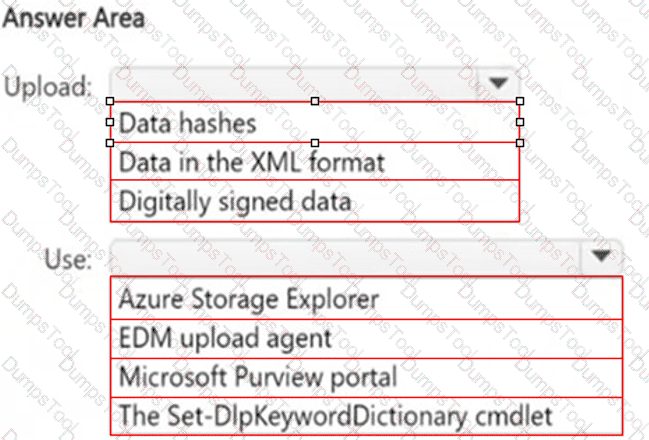
HOTSPOT
You plan to create a custom sensitive information type that will use Exact Data Match (EDM).
You need to identify what to upload to Microsoft 365, and which tool to use for the upload.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to ensure that encrypted email messages sent to an external recipient can be revoked or will expire within seven days.
What should you configure first?
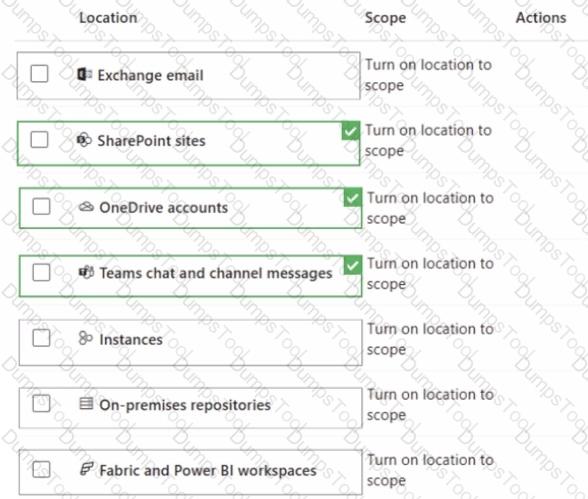
You have a Microsoft 365 tenant that uses Microsoft Teams.
You create a data loss prevention (DLP) policy to prevent Microsoft Teams users from sharing sensitive information. You need to identify which locations must be selected to meet the following requirements:
• Documents that contain sensitive information must not be shared inappropriately in Microsoft Teams.
• If a user attempts to share sensitive information during a Microsoft Teams chat session, the message must be deleted immediately.
Which three locations should you select? To answer, select the appropriate locations in the answer area
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site! and the data loss prevention (DLP) policies shown in the following table.
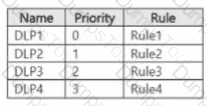
The DLP rules are configured as shown In the following table.
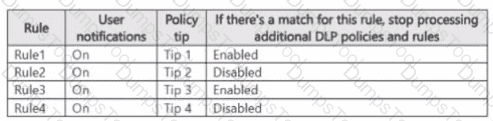
All the policies are assigned to Site1.
You need to ensure that if a user uploads a document to Site1 that matches all the rules, the user will be shown the Tip 2 policy tip. What should you do?
You have a Microsoft 365 tenant.
A new regulatory requirement states that all documents containing a patent ID be labeled, retained for 10 years, and then deleted. The policy used to apply the retention settings must never be disabled or deleted by anyone.
You need to implement the regulatory requirement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI websites.
What should you deploy to the devices?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-MailboxFolderPermission -Identity "User1" -User User1@contoso.com -AccessRights Owner command.
Does that meet the goal?
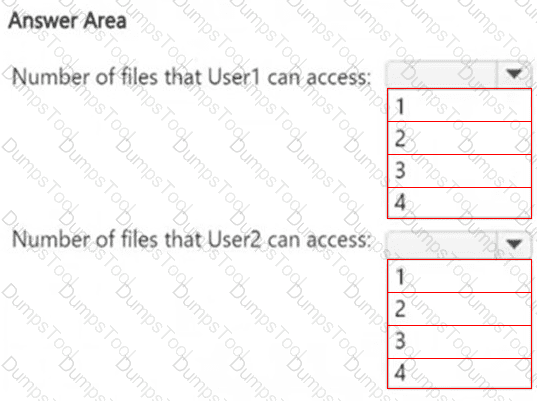
HOTSPOT
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?