You have a Microsoft 365 E5 Subscription named cont0S0.C0rn.
You create a user named User'.
You Need to ensure that User1 can change Status of Microsoft Defender for Identity health alerts. The solution must use principle of the least principle.
What should you do?
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit.
What should you do to meet the security requirements?
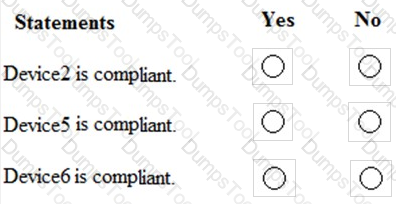
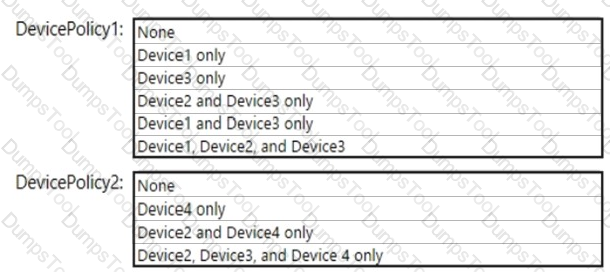
You are evaluating which devices are compliant in Intune.
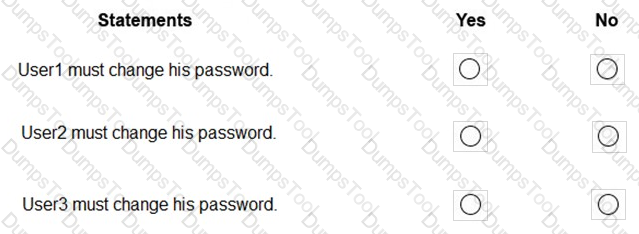
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
NO: 7
You need to resolve the issue that targets the automated email messages to the IT team.
Which tool should you run first?
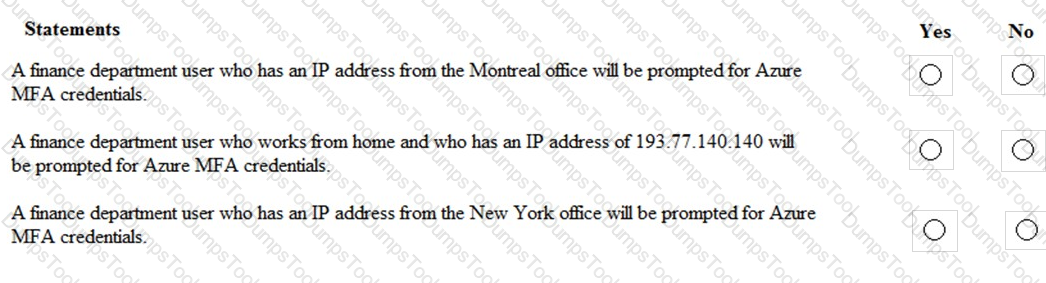
You are evaluating which finance department users will be prompted for Azure MFA credentials.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
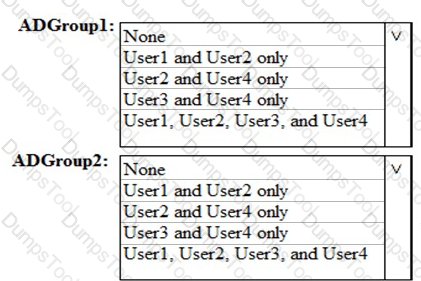
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
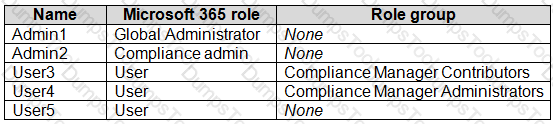
You create an assessment named Assessment1 as shown in the following exhibit.
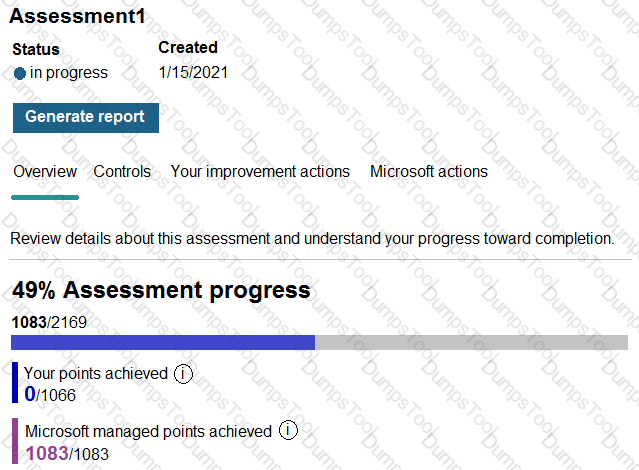
Which users can update the title of Assessment1, and which users can add User5 to the Compliance Manager Readers role group? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
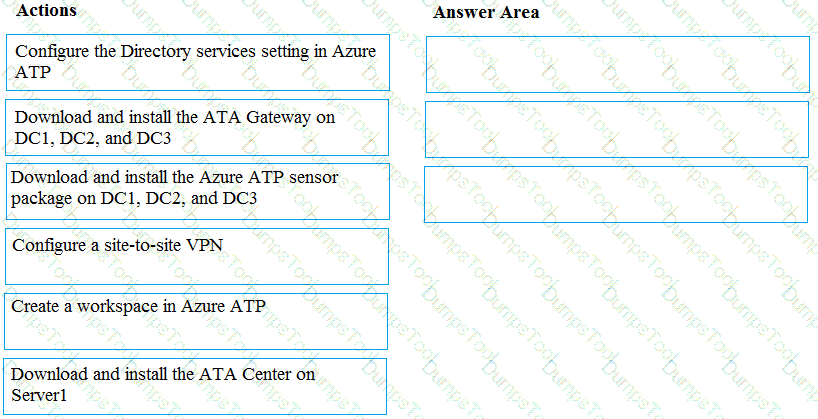
You install Azure ATP sensors on domain controllers.
You add a member to the Domain Admins group. You view the timeline in Azure ATP and discover that information regarding the membership change is missing.
You need to meet the security requirements for Azure ATP reporting.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
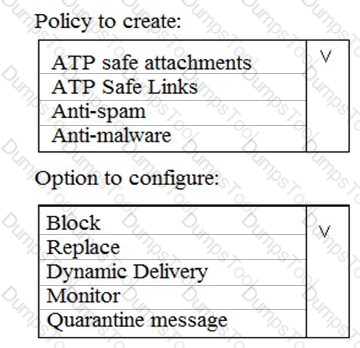
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Which users are members of ADGroup1 and ADGroup2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.
You discover that all the users in the subscription can access Compliance Manager reports.
The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend modifying the licenses assigned to User5.
Does this meet the goal?
Which policies apply to which devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
Users and device objects are added and removed daily. Users in the sales department frequently change their device.
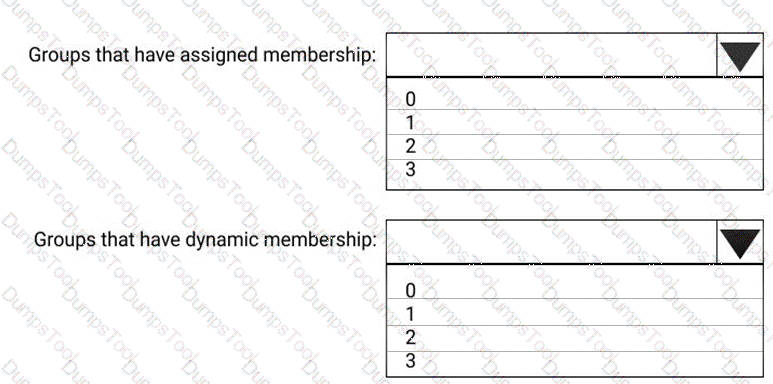
You need to create three following groups:

The solution must minimize administrative effort.
What is the minimum number of groups you should create for each type of membership? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 165 ES subscription that contains users named User 1 and User2?
You have the audit log retention requirements shown in the following table.
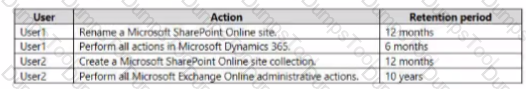
You need to create audit retention policies to meet the requirements. The solution must minimize cost and the number of policies.
What is the minimum number of audit retention policies that you should create?
You have a Microsoft 365 subscription and a Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) subscription.
You have devices enrolled in Microsoft Endpoint Manager as shown in the following table:
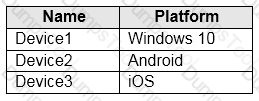
You integrate Microsoft Defender ATP and Endpoint Manager.
You plan to evaluate the Microsoft Defender ATP risk level for the devices.
You need to identify which devices can be evaluated.
Which devices should you identify?
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@LODSe00019@onmicrosoft.com
Microsoft 365 Password: #HSP.ug?$p6un
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support only:
Lab instance: 11122308


You need to protect against phishing attacks. The solution must meet the following requirements:
The solution must apply to the current SMTP domain names and any domain names added later.
To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft 365 subscription.
You have a Microsoft SharePoint Online site named Site1.
The files in Site1 are protected by using Microsoft Azure Information Protection.
From the Security & Compliance admin center, you create a label that designates personal data.
You need to auto-apply the new label to all the content in Site1.
What should you do first?
You need to ensure that administrators can publish a label that adds a footer to email messages and documents.
To complete this task, sign in to the Microsoft Office 365 portal.
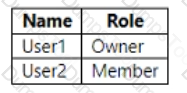
You have a Microsoft SharePoint Online site named Site1 that has the users shown in the following table.
You create the retention labels shown in the following table.
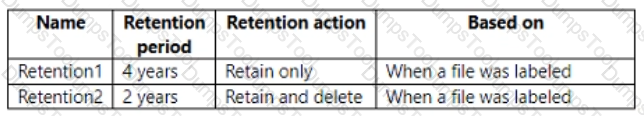
You publish the retention labels to Site1.
On March 1. 2021, you assign the retention labels to the files shown in the following table.
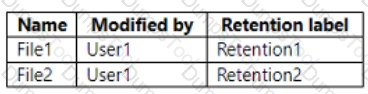
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains the users shown in the following table.
You create and enforce an Azure Active Directory (Azure AD) Identity Protection sign-in risk policy that has the following settings:
The users attempt to sign in. The risk level for each user is shown in the following table.
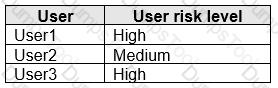
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a user named User1.
User1 needs to be able to create Data Subject Requests (DSRs) in the Microsoft 365 compliance center.
To which role or role group should you add User1?
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@LODSe244001@onmicrosoft.com
Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support only:
Lab instance: 11032396
You need to ensure that SharepointAdmins@contoso.com receives an alert when a user establishes a sync relationship to a document library from a computer that is a member of an Active Directory (AD) domain.
To complete this task, sign in to the Microsoft Office 365 admin center.
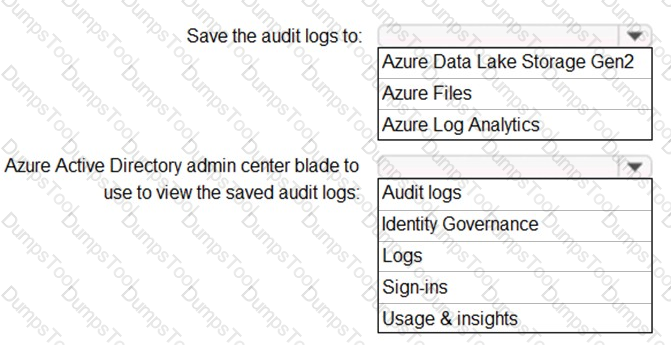
You have a Microsoft 365 tenant.
You need to retain Azure Active Directory (Azure AD) audit logs for two years. Administrators must be able to query the audit log information by using the Azure Active Directory admin center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that unmanaged mobile devices are quarantined when the devices attempt to connect to Exchange Online.
To complete this task, sign in to the Microsoft 365 portal.
You configure several Advanced Threat Protection (ATP) policies in a Microsoft 365 subscription.
You need to allow a user named User1 to view ATP reports in the Threat management dashboard.
Which role provides User1with the required role permissions?
Several users in your Microsoft 365 subscription report that they received an email message without the attachment. You need to review the attachments that were removed from the messages. Which two tools can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
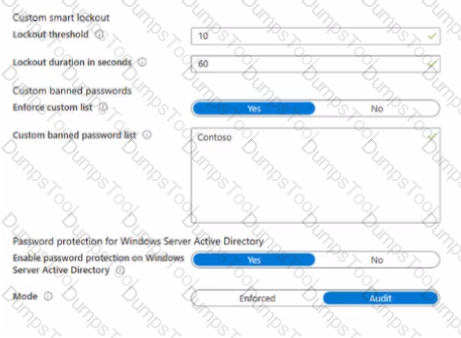
You company has a Microsoft 36S E5 subscription and a hybrid Azure active Directory named contoso.com.
Contoso.com includes the following users:
You configure Password protection for Contoso.com as shown in the following exhibit.
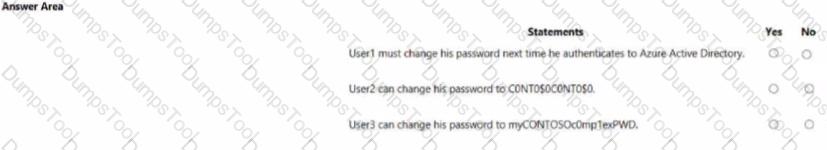
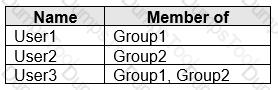
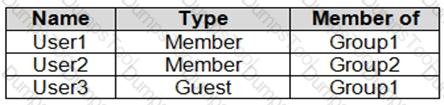
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
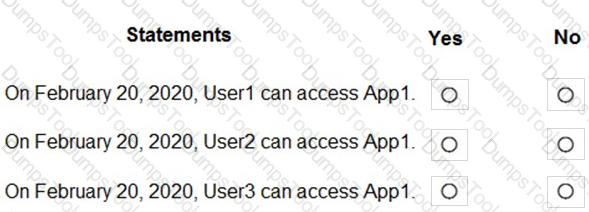
You assign an enterprise application named App1 to Group1 and User2.
You configure an Azure AD access review of App1. The review has the following settings:
On February 15, 2020, you review the access review report and see the entries shown in the following table:

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the groups in the following table
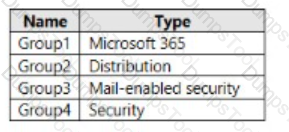
You plan to implement privileged access in Microsoft 365,
Which groups can you specify as the default approval group?
You have a Microsoft 365 Enterprise E5 subscription.
You use Windows Defender Advanced Threat Protection (Windows Defender ATP).
You need to integrate Microsoft Office 365 Threat Intelligence and Windows Defender ATP.
Where should you configure the integration?
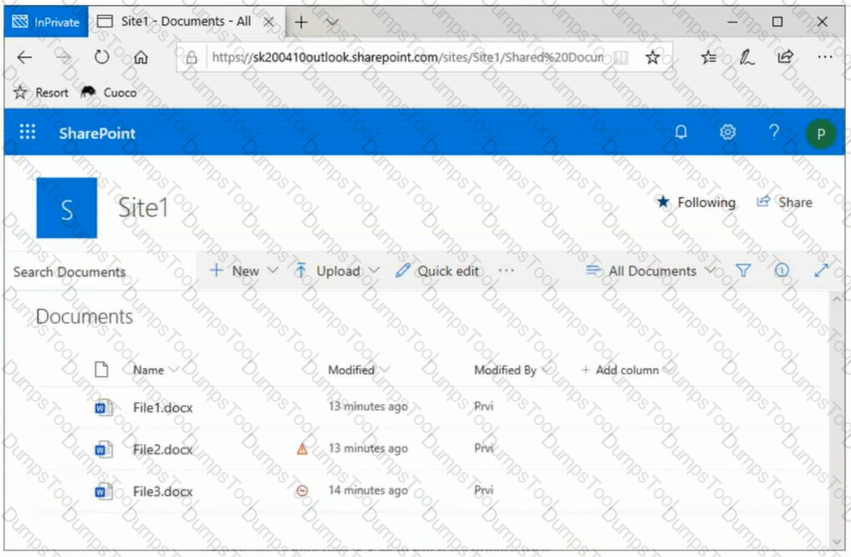
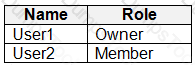
You have a Microsoft 365 E5 tenant that contains two users named User1 and User2 and a Microsoft SharePoint Online site named Site1 as shown in
For Site1, the users are assigned the roles shown in the following table.
You publish a retention label named Retention1 to Site1.
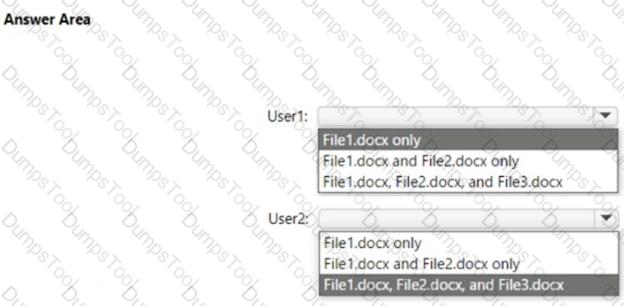
To which files can the users apply Retention1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft Office 365 Attack simulator to model a spear-phishing attack that targets the Research group members.
The email address that you intend to spoof belongs to the Executive group members.
What should you do first?
Your network contains an on-premises Active Directory domain. The domain contains the servers shown in the following table.
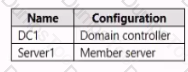
You plan to implement Microsoft Defender for Identity for the domain. You install a Microsoft Defender for Identity standalone sensor on Server 1. You need to monitor the domain by using Microsoft Defender for Identity. What should you do?
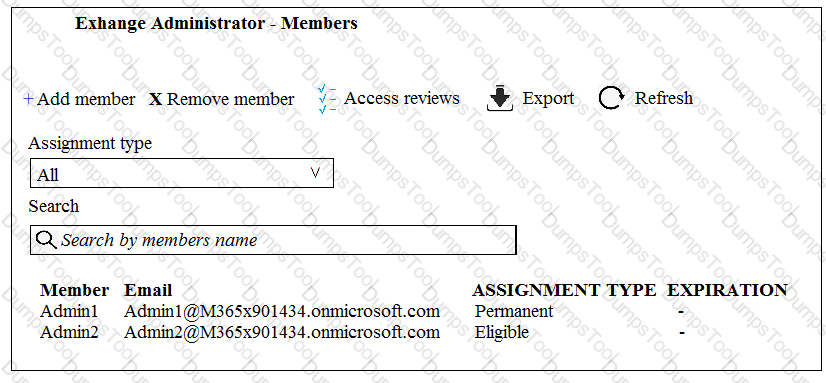
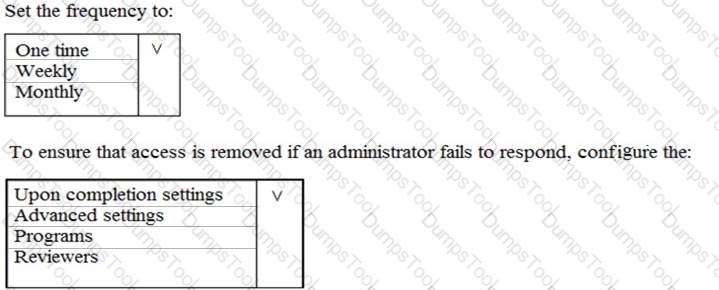
You plan to configure an access review to meet the security requirements for the workload administrators. You create an access review policy and specify the scope and a group.
Which other settings should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to protect the sign-ins of Admin1 and Admin2.
What should you include in the recommendation?
You need to enable and configure Microsoft Defender for Endpoint to meet the security requirements. What should you do?
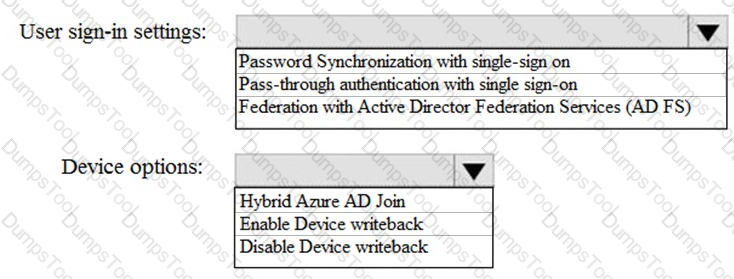
How should you configure Azure AD Connect? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement Windows Defender ATP to meet the security requirements. What should you do?
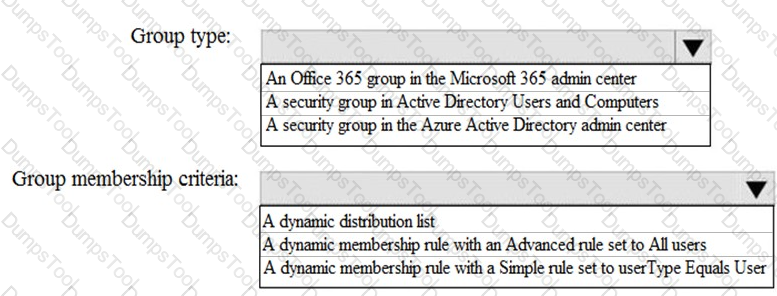
How should you configure Group3? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.