You need to meet the technical requirements for the San Diego office computers. Which Windows 10 deployment method should you use?
You deploy Windows 10 to a new computer named Computer1.
You sign in to Computer1 and create a user named User1.
You create a file named LayoutModification.xml in the C:\Users\Default\AppData\Local\Microsoft\Windows\Shell\folder. LayoutModification.xml contains the following markup.
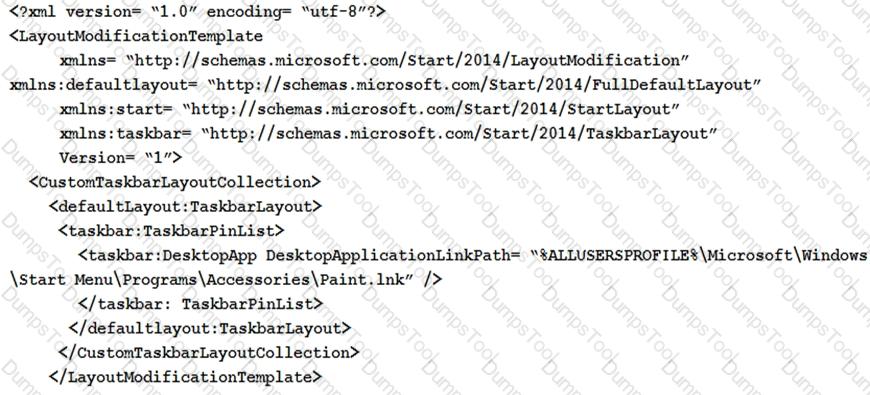
What is the effect of the configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
On Computer1, you need to configure the custom Visual Effects performance settings. Which user accounts can you use?
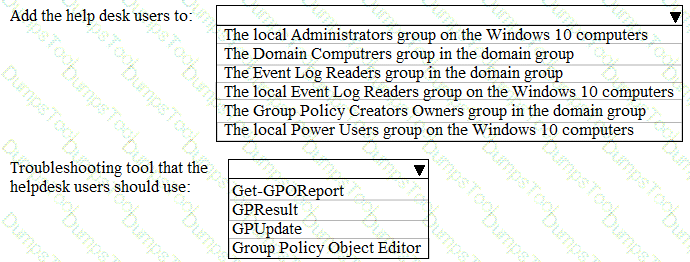
You need to meet the technical requirements for the helpdesk users.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
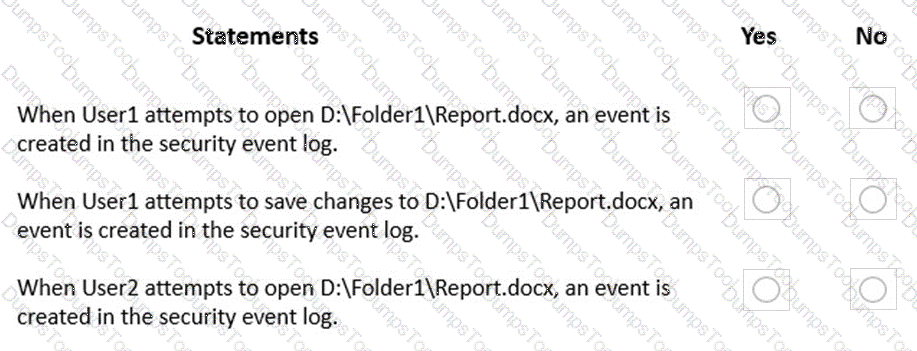
You need to meet the technical requirements for EFS on ComputerA.
What should you do?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to meet the quality update requirement for ComputerA.
For how long should you defer the updates?
You have a computer named Computer1 that runs Windows 10. Computer1 contains a registry key named Key1 that has the values shown in the exhibit. (Click the Exhibit tab.).
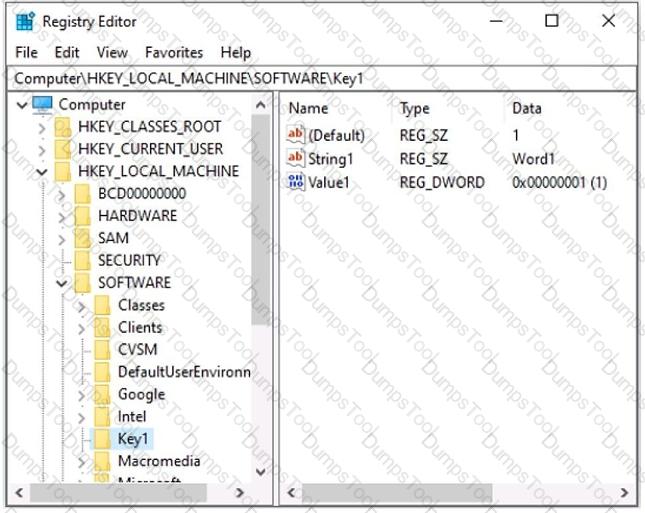
You have a Registration Entries (.reg) file named File1.reg that contains the following text.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Key1]
"String1"=-
@="2"
You need to identify the effect of importing File1.reg to Computer1.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
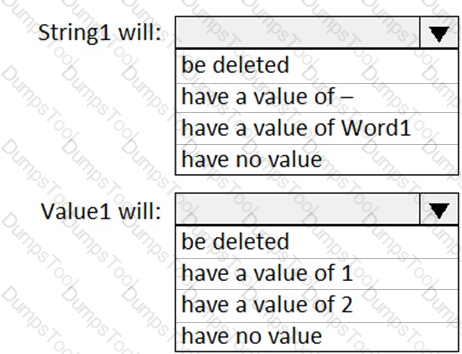
You need to meet the technical requirement for the IT department users.
What should you do first?
You need to recommend a solution to monitor update deployments.
What should you include in the recommendation?
You need to ensure that User10 can activate Computer10.
What should you do?
You need to reduce the amount of time it takes to restart Application1 when the application crashes.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
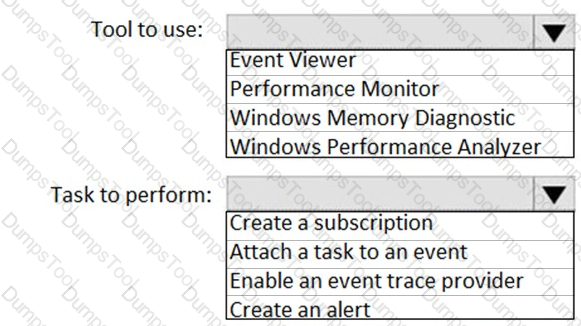
You need to implement a solution to configure the contractors’ computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
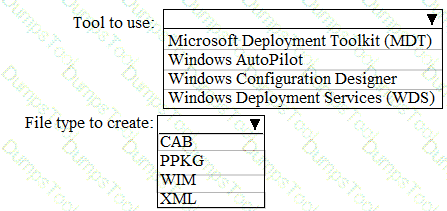
You need to recommend a solution to configure the employee VPN connections.
What should you include in the recommendation?
An employee reports that she must perform a BitLocker recovery on her laptop. The employee does not have her BitLocker recovery key but does have a Windows 10 desktop computer.
What should you instruct the employee to do from the desktop computer?
You need to take remote control of an employee’s computer to troubleshoot an issue.
What should you send to the employee to initiate a remote session?
Your company is not connected to the internet. The company purchases several new computers with Windows 10 Pro for its users.
None of the new computers are activated.
You need to activate the computers without connecting the network to the Internet.
What should you do?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com.
Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.
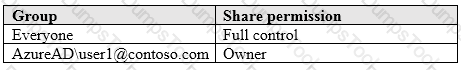
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com.
User2 attempts to access Share1 and receives the following error message: “The username or password is incorrect.”
You need to ensure that User2 can connect to Share1.
Solution: You create a local user account on Computer1 and instruct User2 to use the local account to connect to Share1.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a workgroup computer that runs Windows 10. The computer contains the local user accounts shown in the following table.
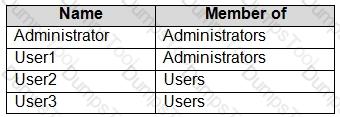
You need to configure the desktop background for User1 and User2 only.
Solution: You create two new local Group Policy Objects (GPOs) and apply one GPO to User1 and the other GPO to User2. You configure the Desktop Wallpaper setting in each GPO.
Does this meet the goal?
You have a computer named Computer1 that runs Windows 10.
Several users have signed in to Computer1 and have a profile.
You create a taskbar modification file named LayoutModification.xml.
You need to ensure that LayoutModification.xml will apply to all users who sign in to Computer1.
To which folder should you copy LayoutModification.xml?
You implement the planned changes for Computer1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You need to configure Delivery Optimization to meet the technical requirements.
Which download mode should you use?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
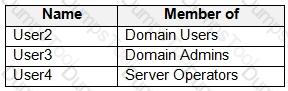
Your network contains an Active Directory domain named contoso.com. The domain contains the users shown in the following table.
You have a computer named Computer1 that runs Windows 10 and is in a workgroup.
A local standard user on Computer1 named User1 joins the computer to the domain and uses the credentials of User2 when prompted.
You need to ensure that you can rename Computer1 as Computer33.
Solution: You use the credentials of User1 on Computer1.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two computers named Computer1 and Computer2 that run Windows 10.
You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer.
You sign in to Computer1 by using admin@contoso.com.
You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2.
Solution: On Computer2, you create a Windows Defender Firewall rule that allows eventwr.exe.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
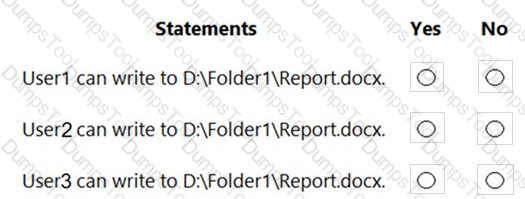
You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit privilege use.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a workgroup computer that runs Windows 10. The computer contains the local user accounts shown in the following table.
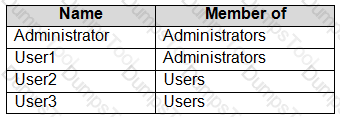
You need to configure the desktop background for User1 and User2 only.
Solution: From the local computer policy, you configure the Filter Options settings for the computer policy.
Does this meet the goal?
You have a file named Reg1.reg that contains the following content.
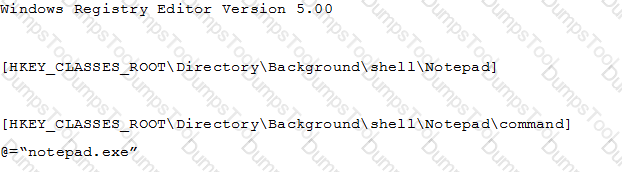
What is the effect of importing the file?
You have a computer that runs Windows 10.
You need to view the Windows Update diagnostic log.
What should you do first?
You have computers that run Windows 11 as shown in the following table.
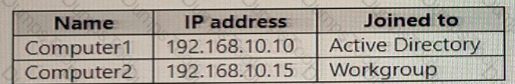
You ping 192.168.10.15 from Computed and discover that the request timed out. You need to ensure that you can successfully ping 192.168.10.15 from Computer1. Solution: On Computer1, you turn off Windows Defender Firewall-Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
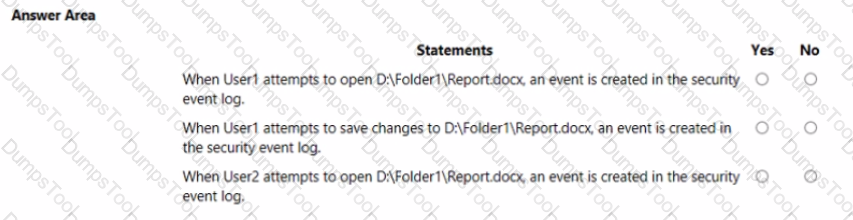
You have a computer named Computer1 that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit directory service access.
Does this meet the goal?