To what environment variable will you assign or append a value if you need to tell the dynamic linker to look in a build directory for some of a program's shared libraries?
LD_LOAD_PATH
LD_LIB_PATH
LD_LIBRARY_PATH
LD_SHARE_PATH
LD_RUN_PATH
The environment variable LD_LIBRARY_PATH is used to tell the dynamic linker to look in a specific directory for some of a program’s shared libraries. It is a colon-separated list of directories that are searched by the dynamic linker when looking for a shared library to load1. The directories are searched in the order they are mentioned in. For example, if we have a program that depends on a shared library libfoo.so that is located in /home/user/build/lib, we can run the program with:
LD_LIBRARY_PATH=/home/user/build/lib ./program
This will instruct the dynamic linker to search for libfoo.so in /home/user/build/lib before the default directories. The environment variable LD_LIBRARY_PATH can also be appended to an existing value with the += operator, for example:
LD_LIBRARY_PATH+=:/home/user/build/lib
This will add /home/user/build/lib to the end of the LD_LIBRARY_PATH list. The other options are not valid environment variables for the dynamic linker. LD_LOAD_PATH, LD_LIB_PATH, and LD_SHARE_PATH are not recognized by the dynamic linker. LD_RUN_PATH is a linker option that can be used to embed a library search path in the executable at link time, but it is not an environment variable that can be set or modified at run time2. References:
LPI Exam 101 Detailed Objectives, section 1.101.3
ld-linux(8) — Linux manual page
Setting the dynamic linker with an environment variable - narkive
Which of the following commands overwrites the bootloader located on /dev/sda without overwriting the partition table or any data following it?
dd if=/dev/zero of=/dev/sda bs=512
dd if=/dev/zero of=/dev/sda bs=512 count=1
dd if=/dev/zero of=/dev/sda bs=440 count=1
dd if=/dev/zero of=/dev/sda bs=440
The dd command is used to copy data from one device or file to another, with optional parameters to specify the block size (bs), the number of blocks to copy (count), and other options. The bootloader is typically located in the first 440 bytes of the disk, which is the Master Boot Record (MBR) area. The MBR also contains the partition table, which starts at byte 446 and occupies 64 bytes. Therefore, to overwrite the bootloader without affecting the partition table or any data following it, the command should copy 440 bytes from /dev/zero (a special device that provides null bytes) to /dev/sda (the disk device) and stop after one block. This is achieved by the command: dd if=/dev/zero of=/dev/sda bs=440 count=1 References:
LPI Exam 101 Detailed Objectives, section 1.101.3
dd man page
Master Boot Record
Which file should be edited to select the network locations from which Debian installation package files are loaded?
/etc/dpkg/dpkg.cfg
/etc/apt/apt.conf
/etc/apt/apt.conf.d
/etc/apt/sources.list
/etc/dpkg/dselect.cfg
The /etc/apt/sources.list file is the main configuration file for the Advanced Package Tool (apt), which is used to manage Debian installation package files. This file contains a list of repositories, or sources, from which apt can download and install packages. Each repository is specified by a line that has the following format:
type uri suite [component1] [component2] […]
Where:
type is the access method, such as http, ftp, file, etc.
uri is the Uniform Resource Identifier (URI) of the repository, such as http://deb.debian.org/debian
suite is the distribution code name or archive name, such as stable, testing, unstable, etc.
component is an optional section of the repository, such as main, contrib, non-free, etc.
For example, a typical sources.list file for Debian stable could look like this:
deb http://deb.debian.org/debian stable main contrib non-free deb-src http://deb.debian.org/debian stable main contrib non-free
deb http://deb.debian.org/debian-security/ stable/updates main contrib non-free deb-src http://deb.debian.org/debian-security/ stable/updates main contrib non-free
deb http://deb.debian.org/debian stable-updates main contrib non-free deb-src http://deb.debian.org/debian stable-updates main contrib non-free
The first two lines specify the main repository for Debian stable, with both binary (deb) and source (deb-src) packages. The next two lines specify the security updates repository for Debian stable, which contains important security fixes. The last two lines specify the stable-updates repository, which contains packages that have been updated after the release of Debian stable.
By editing the /etc/apt/sources.list file, one can select the network locations from which Debian installation package files are loaded. However, it is recommended to use a graphical or command-line tool, such as aptitude or synaptic, to manage the sources.list file, as they can handle the syntax and avoid errors.
Immediately after deleting 3 lines of text in vi and moving the cursor to a different line, which single character command will insert the deleted content below the current line?
i (lowercase)
P (uppercase)
p (lowercase)
U (uppercase)
u (lowercase)
The p command in vi inserts the content of the buffer below the current line. The buffer is where the deleted or yanked text is stored temporarily. The P command inserts the buffer above the current line. The i command enters the insert mode before the cursor position. The U command restores the current line to its original state. The u command undoes the last change made to the file. References:
[LPI Linux Essentials - 1.3 Basic Editing]
[LPI Linux Essentials - 1.4 I/O Redirection]
[LPI Linux Essentials - 1.5 Manage Simple Partitions and Filesystems]
Which of the following commands replaces each occurrence of 'bob' in the file letter with 'Bob' and writes the result to the file newletter?
sed '/bob/Bob' letter > newletter
sed s/bob/Bob/ letter < newletter
sed's/bob/Bob' letter > newletter
sed 's/bob/Bob/g' letter > newletter
sed 's/bob, Bob/' letter > newletter
The command that replaces each occurrence of ‘bob’ in the file letter with ‘Bob’ and writes the result to the file newletter is sed ‘s/bob/Bob/g’ letter > newletter. This command uses the following options and syntax:
s: Specifies the substitution operation.
/: Separates the pattern and the replacement strings.
bob: The pattern to be searched and replaced.
Bob: The replacement string.
g: The global flag that indicates all occurrences of the pattern in each line should be replaced, not just the first one.
letter: The name of the input file.
: Redirects the output to a file.
newletter: The name of the output file.
The output of this command will be a new file called newletter that contains the same text as letter, except that every ‘bob’ is replaced by ‘Bob’. For example, if the file letter contains the following text:
Dear bob, I hope this letter finds you well. I am writing to inform you that your subscription to our magazine has expired. If you wish to renew it, please send us a check for $50 by the end of this month. Otherwise, we will have to cancel your subscription and remove you from our mailing list. Thank you for your cooperation and support. Sincerely, Alice
The file newletter will contain the following text:
Dear Bob, I hope this letter finds you well. I am writing to inform you that your subscription to our magazine has expired. If you wish to renew it, please send us a check for $50 by the end of this month. Otherwise, we will have to cancel your subscription and remove you from our mailing list. Thank you for your cooperation and support. Sincerely, Alice
The other commands are incorrect for the following reasons:
A. sed ‘/bob/Bob’ letter > newletter: This command is missing the s option and the second / delimiter, and will produce an error message.
B. sed s/bob/Bob/ letter < newletter: This command is using the wrong redirection operator (< instead of >), and will try to read the input from newletter instead of letter, and write the output to the standard output instead of newletter.
C. sed’s/bob/Bob’ letter > newletter: This command is missing a space between sed and the first ', and will produce an error message.
E. sed ‘s/bob, Bob/’ letter > newletter: This command is using a comma (,) instead of a slash (/) as a delimiter, and will produce an error message.
Which of the following commands is used to change options and positional parameters for a running Bash?
history
set
bashconf
setsh
envsetup
The command that is used to change options and positional parameters for a running Bash is set. The set command allows the user to modify the behavior of the shell by enabling or disabling various options, such as -x (trace mode), -e (exit on error), -u (treat unset variables as errors), and others. The set command can also be used to assign values to the positional parameters, which are the arguments passed to the shell or a shell script. The positional parameters are denoted by $1, $2, $3, and so on, up to $9. The special parameter 0referstothenameoftheshellortheshellscript.Thespecialparameter# refers to the number of positional parameters. The special parameter $@ refers to all the positional parameters as a list.
To change the positional parameters, the set command can be used with the – option, followed by the new arguments. For example, the following command will set the positional parameters to “a”, “b”, and “c”:
set – a b c
After this command, $1 will be “a”, $2 will be “b”, 3willbe"c",# will be 3, and $@ will be “a b c”. The – option signals the end of options and prevents any argument that starts with a - from being interpreted as an option. Alternatively, the set command can be used with the - option, followed by the new arguments. However, this will also disable the -x and -v options, if they were previously enabled. For example, the following command will set the positional parameters to “-a”, “-b”, and “-c”, and turn off the trace and verbose modes:
set - -a -b -c
The set command can also be used without any option or argument, in which case it will display the names and values of all shell variables and functions.
The other commands are not valid or relevant for changing options and positional parameters for a running Bash. The history command displays the history list of commands entered by the user. The bashconf command does not exist. The setsh command does not exist. The envsetup command does not exist.
From a Bash shell, which of the following commands directly executes the instruction from the file /usr/local/bin/runme.sh without starting a subshell? (Please select TWO answers.)
source /usr/local/bin/runme.sh
. /usr/local/bin/runme.sh
/bin/bash /usr/local/bin/runme.sh
/usr/local/bin/runme.sh
run /usr/local/bin/runme.sh
The commands that directly execute the instruction from the file /usr/local/bin/runme.sh without starting a subshell are source /usr/local/bin/runme.sh and . /usr/local/bin/runme.sh. These commands use the source or dot builtins, which read and execute commands from the given file in the current shell environment. This means that any changes made by the file, such as setting variables, defining functions, or changing directories, will affect the current shell. This is different from running the file as a script, which will create a new shell process and execute the commands in a separate environment. The source or dot commands are useful for loading configuration files, such as ~/.bashrc or /etc/profile, or for running scripts that modify the current state of the shell.
The other commands are incorrect for the following reasons:
C. /bin/bash /usr/local/bin/runme.sh: This command will run the file as a script using the /bin/bash interpreter. This will create a new shell process and execute the commands in a separate environment. Any changes made by the file will not affect the current shell.
D. /usr/local/bin/runme.sh: This command will also run the file as a script, but using the interpreter specified by the shebang line (#!) at the beginning of the file. If the file does not have a shebang line, it will use the default shell interpreter, which may or may not be /bin/bash. This will also create a new shell process and execute the commands in a separate environment. Any changes made by the file will not affect the current shell.
E. run /usr/local/bin/runme.sh: This command is not valid, as there is no builtin or external command called run. This will produce an error message.
What is the default nice level when a process is started using the nice command?
-10
10
20
0
The default nice level when a process is started using the nice command is 10. This means that the process will have a lower priority than the normal processes, which have a nice level of 0. The nice command allows the user to adjust the priority of a process at the time of its execution. The syntax of the nice command is:
nice [-n {nice value increment}] [command]
The -n option specifies the nice value increment, which can be a positive or negative integer in the range of -20 to 19. The command is the name of the program or script to be executed. If the -n option is omitted, the default nice value increment is 10. For example, the following command will run the program ackermann with a nice value of 10:
nice ./ackermann
To verify the nice value of a running process, we can use the ps or top commands and look at the NI column. For example, the following command will show the nice value of the ackermann process:
ps -el | grep ackermann
In compliance with the FHS, in which of the directories are man pages found?
/usr/share/man
/opt/man
/usr/doc/
/var/pkg/man
/var/man
According to the Filesystem Hierarchy Standard (FHS), the directory /usr/share/man contains manual pages for user commands, system calls, library functions, and other documentation1. The other directories are either non-standard, deprecated, or used for different purposes. For example, /opt/man is used for manual pages for add-on application software packages1, /usr/doc/ is an old location for documentation files that is no longer used2, /var/pkg/man and /var/man are not defined by the FHS. References:
[LPI Linux Essentials - 1.6 Basic File Editing]
[LPI Linux Essentials - 1.7 Personalize and/or Localize Your Linux System]
[LPI Linux Essentials - 1.8 Basic Security and File Permissions]
What is the difference between the i and a command of the vi editor?
i (interactive) requires the user to explicitly switch between vi modes whereas a (automatic) switches modes automatically.
i (insert) inserts text before the current cursor position whereas a (append) inserts text after the cursor.
i (independent rows) starts every new line at the first character whereas a (aligned rows) keeps the indentation of the previous line.
i (interrupt) temporarily suspends editing of a file to the background whereas a (abort) terminates editing.
The i and a commands are two of the most commonly used commands in the vi editor to enter the insert mode. The insert mode allows the user to insert text into the file. The difference between the i and a commands is that the i command inserts text before the current cursor position, while the a command inserts text after the cursor position. For example, if the cursor is on the letter “e” in the word “editor”, then pressing i will allow the user to insert text before the “e”, while pressing a will allow the user to insert text after the “e”. The user can exit the insert mode by pressing the Esc key, which will return to the command mode. References:
Basic vi commands (cheat sheet)
VI Editor with Commands in Linux/Unix Tutorial
How to use Vi editor in Linux (with examples)
Which of the following are valid stream redirection operators within Bash? (Choose THREE correct answers.)
<
<<<
>
>>>
%>
The <, > and %> are valid stream redirection operators within Bash. The < operator redirects the standard input of a command from a file or another command. For example, sort < names.txt will sort the lines of the file names.txt and print them to the standard output. The > operator redirects the standard output of a command to a file or another command, overwriting the file if it exists. For example, echo "Hello World" > greeting.txt will write the string “Hello World” to the file greeting.txt. The %> operator redirects the standard error of a command to a file or another command, overwriting the file if it exists. For example, ls foo %> errors.log will list the contents of the directory foo and write any error messages to the file errors.log. The other options are either invalid or do not perform the desired task. The <<< operator is not a valid Bash operator, but it is used in some other shells like Zsh to redirect a string literal as the standard input of a command. The >>> operator is not a valid Bash operator, but it is used in some programming languages like Python to denote a bitwise right shift operation. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.4 Use streams, pipes and redirects
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
What is the purpose of the Bash built-in export command?
It allows disks to be mounted remotely.
It runs a command as a process in a subshell.
It makes the command history available to subshells.
It sets up environment variables for applications.
It shares NFS partitions for use by other systems on the network.
The export command is a Bash built-in command that exports environment variables and functions for use in other shell sessions1. Environment variables are named values that affect the behavior of applications and processes2. For example, the PATH variable stores a list of directories where executable programs are located, and the LANG variable sets the language and locale of the system2. By using the export command, you can make these variables available to any child process spawned by the current shell1. For example, if you want to set the EDITOR variable to vim for all subshells, you can run:
export EDITOR=vim
The export command can also be used to export functions, which are blocks of code that can be reused by invoking their name3. For example, if you want to create and export a function that prints “Hello world”, you can run:
hello () { echo “Hello world”; } export -f hello
Then, you can call the hello function in any subshell or script that inherits the environment from the current shell.
The other options are not related to the export command. Option A refers to the mount command, which attaches a filesystem to a directory4. Option B refers to the command substitution feature, which runs a command in a subshell and replaces it with its output5. Option C refers to the history command, which displays the command history of the current shell. Option E refers to the exportfs command, which maintains the table of exported NFS shares.
Which standardized TCP port is used by HTTPS services?
25
80
8080
443
636
Given the following routing table:
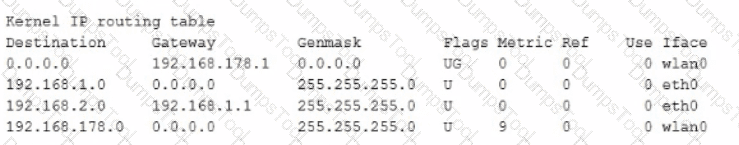
How would an outgoing packet to the destination 192 168 2 150 be handled?
It would be passed to the default router 192 168 178 1 onwIan0.
It would be directly transmitted on the device eth0
It would be passed to the default router 255 255 255 0 on eth0
It would be passed to the router 192 168.1.1 oneth0
It would be directly transmitted on the device wlan0.
Which character in the password field of /etc/passwd is used to indicate that the encrypted password is stored in /etc/shadow?
*
-
$
#
x
Which parameter is missing in the command
ip link set _dev eth0
to activate the previously inactive network interface eth0? (Specify the parameter only without any command, path or additional options)
Up
When redirecting the output of find to the xargs command, what option to find is useful if the filenames contain spaces?
–rep-space
-printnul
-nospace
–ignore-space
–print0
This option to the find command is useful if the filenames contain spaces when redirecting the output of find to the xargs command. The syntax of the option is:
find [where to start searching from] [expression determines what to find] -print0
The -print0 option tells the find command to print the full file name on the standard output, followed by a null character (ASCII code 0) instead of the newline character. This allows file names that contain spaces or other special characters to be correctly interpreted by the xargs command, which can use the -0 option to read items from the standard input that are terminated by a null character. The syntax of the xargs command with the -0 option is:
xargs -0 [command]
The -0 option tells the xargs command to expect the items from the standard input to be separated by a null character, and to execute the command using the items as arguments.
Therefore, the command find … -print0 | xargs -0 … will search for files and directories using the find command, print the results with a null character as the separator, pipe the output to the xargs command, which will read the items with a null character as the separator, and execute another command using the items as arguments. This will avoid any problems with filenames that contain spaces or other special characters.
The other options are incorrect for the following reasons:
A, -rep-space: This option does not exist in the find command. There is no option to replace spaces in the filenames with another character in the find command. The command will report an error and exit.
B, -printnul: This option does not exist in the find command. There is a similar option, -print0, which prints the filenames with a null character as the separator, but -printnul is not a valid option. The command will report an error and exit.
C, -nospace: This option does not exist in the find command. There is no option to ignore spaces in the filenames in the find command. The command will report an error and exit.
D, -ignore-space: This option does not exist in the find command. There is no option to ignore spaces in the filenames in the find command. The command will report an error and exit.
Which ol the following fields can be found in the /etc/group file? (Choose TWO correct answers.)
The home directory of the group
The list of users that belong to the group
The name of the group
The default group ACL
The description of the group
Which of the following vi commands deletes two lines, the current and the following line?
d2
2d
2dd
dd2
de12
The correct answer is C, 2dd. This command will delete two lines, the current and the following line, in vi editor. The syntax of the command is:
[number]dd
The number specifies how many lines to delete, starting from the current line. The dd command deletes the lines and puts them in a buffer, which can be pasted later with the p command. If no number is given, the command will delete only the current line.
The other commands are incorrect for the following reasons:
A, d2: This command will delete two characters, not two lines. The syntax of the command is:
d[motion]
The motion specifies how many characters to delete, starting from the current cursor position. The 2 motion means two characters to the right. The d command deletes the characters and puts them in a buffer, which can be pasted later with the p command.
B, 2d: This command is incomplete and will not work. The d command requires a motion argument to specify how many characters to delete. The 2 argument is only a number, not a motion. The command will wait for another keystroke to complete the motion.
D, dd2: This command will delete the current line and then move the cursor two lines down. The syntax of the command is:
dd[number]
The dd command deletes the current line and puts it in a buffer, which can be pasted later with the p command. The number specifies how many lines to move the cursor down, after deleting the current line. If no number is given, the command will move the cursor to the next line.
E, de12: This command will delete from the current cursor position to the end of the word, and then move the cursor to the 12th line. The syntax of the command is:
d[motion][number]
The d command deletes the characters specified by the motion and puts them in a buffer, which can be pasted later with the p command. The e motion means the end of the word. The number specifies the line number to move the cursor to, after deleting the characters.
What is true regarding the configuration of yum? (Choose two.)
Changes to the repository configuration become active after running yum confupdate
Changes to the yum configuration become active after restarting the yumd service
The configuration of package repositories can be divided into multiple files
Repository configurations can include variables such as $basearch or $releasever
In case /etc/yum.repos.d/ contains files, /etc/yum.conf is ignored
The configuration of yum can be divided into multiple files, and repository configurations can include variables such as $basearch or $releasever. The main configuration file for yum is /etc/yum.conf, which contains the global options for yum and can also define repositories in the [repository] sections. However, it is recommended to define individual repositories in separate files in the /etc/yum.repos.d/ directory, which can be easier to manage and maintain. Each file in this directory should have a .repo extension and contain one or more [repository] sections with the repository name, URL, and other options12. Repository configurations can use yum variables to dynamically set values for certain options, such as the baseurl or the enabled. Yum variables are enclosed in curly braces and start with a dollar sign, such as {$basearch} or {$releasever}. These variables are replaced by their actual values at runtime, based on the system architecture, the operating system version, or other factors. Some of the common yum variables are34:
$basearch: The base architecture of the system, such as x86_64, i386, or arm.
$releasever: The release version of the operating system, such as 7, 8, or 9.
$arch: The exact architecture of the system, such as x86_64, i686, or armv7hl.
$uuid: A unique identifier for the system, generated by the product-id plugin.
$YUM0-$YUM9: Custom variables that can be set by the user in the /etc/yum/vars/ directory or the /etc/yum.conf file.
The other options are false or irrelevant. There is no yum confupdate command or yumd service, and changes to the yum configuration become active immediately after saving the files. The /etc/yum.conf file is not ignored if the /etc/yum.repos.d/ directory contains files, but the repository options in the /etc/yum.conf file can be overridden by the options in the .repo files. References:
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute2
How to Use Yum Variables to Enhance your Yum Experience - Red Hat …3
Yum Variables - CentOS4
Which of the following commands installs all packages with a name ending with the string foo?
zypper get “*foo”
zypper update “foo?”
zypper force “foo*”
zypper install “*foo”
zypper add “.*foo”
The command that installs all packages with a name ending with the string foo is zypper install “*foo”. The zypper command is the command line interface of the ZYpp package manager for SUSE Linux. The install (in) subcommand is used to install packages with specified capabilities or RPM files with specified location. The argument “*foo” is a glob pattern that matches any package name that ends with foo. For example, zypper install “foo" will install packages like barfoo, bazfoo, and foo itself. The other commands are either invalid or do not perform the desired task. The zypper get, zypper update, zypper force, and zypper add subcommands do not exist. The “foo?” and "foo” arguments are also invalid glob patterns, as they do not match the end of the package name. The “.*foo” argument is a valid glob pattern, but it matches any package name that contains foo, not just the ones that end with foo. References:
Zypper package manager - SUSE Documentation1
zypper(8) [suse man page] - The UNIX and Linux Forums2
45 Zypper Commands to Manage ‘Suse’ Linux Package Management - Tecmint
Which of the following commands redirects the output of ls to standard error?
ls >-1
ls <
ls >&2
ls >>2
ls |error
This command redirects the output of ls to standard error, which is file descriptor 2 by default. The syntax of the command is:
ls >& file_descriptor
The ls command is a utility that lists the files and directories in the current working directory or a specified directory. The >& symbol is a redirection operator that redirects the standard output of a command to another file descriptor, which can be a file, a device, or another stream. The file_descriptor is the number of the file descriptor to which the output is redirected.
Therefore, the command ls >&2 will run the ls command and redirect its output to file descriptor 2, which is standard error. This means that the output of ls will not be displayed on the screen, but sent to the standard error stream, which can be used for error handling or logging purposes.
The other commands are incorrect for the following reasons:
A, ls >-1: This command will not redirect the output of ls to standard error, but it will cause an error. The > symbol is a redirection operator that redirects the standard output of a command to a file or device, overwriting any existing content. The -1 argument is not a valid file name or device name, and it will cause the shell to report an error and exit.
B, ls < D, ls >>2: This command will not redirect the output of ls to standard error, but it will append the output of ls to a file named 2. The >> symbol is a redirection operator that redirects the standard output of a command to a file or device, appending to any existing content. The 2 argument is the name of the file to which the output is appended. If the file does not exist, it will be created. The command will not display anything on the screen, but write the output of ls to the file 2. E, ls |error: This command will not redirect the output of ls to standard error, but it will pipe the output of ls to another command named error. The | symbol is a pipe operator that redirects the standard output of one command to the standard input of another command. The error argument is the name of the command that receives the output of ls as its input. However, there is no such command named error in the Linux system, and the shell will report an error and exit.
Typically, which top level system directory is used for files and data that change regularly while the system is running and are to be kept between reboots? (Specify only the top level directory)
/var
/var/,
Var
var/
The top-level system directory that is used for files and data that change regularly while the system is running and are to be kept between reboots is /var. The /var directory contains variable data that changes in size as the system runs. For instance, log files, mail directories, databases, and printing spools are stored in /var. These files and data are not temporary and need to be preserved across system reboots. The /var directory is one of the few directories that are recommended to be on a separate partition, according to the Filesystem Hierarchy Standard (FHS)1. This is because the /var directory can grow unpredictably and fill up the / partition, which can cause system instability or failure. By having /var on a separate partition, we can limit the amount of disk space that can be used by variable data and prevent users from affecting the / partition. The /var directory is also a common target for malicious attacks, so having it on a separate partition can improve the security and isolation of the system. References:
Filesystem Hierarchy Standard
You want to preview where the package file, apache-xml.i386.rpm, will install its files before installing it. What command do you issue?
rpm -qp apache-xml.i386.rpm
rpm -qv apache-xml.i386.rpm
rpm -ql apache-xml.i386.rpm
rpm -qpl apache-xml.i386.rpm
Which function key is used to start Safe Mode in Windows NT?
F10
F8
F6
Windows NT does not support Safe Mode
The function key that is used to start Safe Mode in Windows NT is none of the above, because Windows NT does not support Safe Mode. Safe Mode is a diagnostic mode of Windows that starts the system with minimal drivers and services, allowing the user to troubleshoot problems and restore the system to a normal state1. Safe Mode was introduced in Windows 95 and later versions, but not in Windows NT 4.0 and earlier2.
The other options are incorrect for the following reasons:
F10. This function key is used to access the Recovery Console in Windows XP, which is a command-line interface that allows the user to perform various administrative tasks, such as repairing the boot sector, restoring the registry, or copying files3. The Recovery Console is not the same as Safe Mode, and it is not available in Windows NT.
F8. This function key is used to access the Advanced Boot Options menu in Windows Vista and later versions, which allows the user to choose from various boot modes, including Safe Mode, Last Known Good Configuration, Debugging Mode, and others4. In Windows NT, pressing F8 during startup only displays a simple menu with three options: Normal, VGA mode, and Boot Logging5. None of these options are equivalent to Safe Mode.
F6. This function key is used to load additional drivers during the installation of Windows, such as SCSI or RAID drivers, from a floppy disk or a USB flash drive6. This function key has nothing to do with Safe Mode, and it is not relevant after the installation is completed.
Which of the following commands can be used to perform a full text search on all available packages on a Debian system?
apt
apt-cache
apt-get
apt-search
dpkg
The command apt-cache can be used to perform a full text search on all available packages on a Debian system. It searches the package names and the descriptions for an occurrence of the regular expression given as a keyword and prints out the package name and the short description1. The syntax is: apt-cache search keyword. For example, apt-cache search openssh will return a list of packages related to OpenSSH2. The other commands are not suitable for this task because:
apt is a high-level command-line tool that provides a user-friendly way to manage packages, but it does not have a search option3.
apt-get is a low-level command-line tool that handles the installation and removal of packages, but it does not have a search option4.
apt-search is not a valid command.
dpkg is a tool to install, build, remove and manage Debian packages, but it does not have a search option5. It can only list the installed packages with the option -l4. References:
How To Search For Available Packages From Command Line In Debian, Ubuntu Or Linux Mint [APT] - Linux Uprising Blog
apt(8) — apt — Debian buster — Debian Manpages
How to List Installed Packages on Debian | Linuxize
Debian / Ubuntu Linux search package names with apt-cache command
dpkg(1) — dpkg — Debian buster — Debian Manpages
An administrator has issued the following command:
grub-install --root-directory=/custom-grub /dev/sda
In which directory will new configuration files be found? (Provide the full directory path only without the filename)
/custom-grub/boot/grub/
/custom-grub/boot/grub
The command grub-install is used to install GRUB on a device or a partition. The option --root-directory specifies the directory where GRUB images are put. The default is /boot/grub. The argument /dev/sda specifies the device where GRUB is installed, usually the Master Boot Record (MBR) of the disk. Therefore, the command grub-install --root-directory=/custom-grub /dev/sda will install GRUB on the MBR of /dev/sda and put the GRUB images under the directory /custom-grub/boot/grub. This means that the new configuration files, such as grub.cfg, will be found in the directory /custom-grub/boot/grub. References:
GNU GRUB Manual 2.06: Installing GRUB using grub-install
Installing GRUB using grub-install - GNU GRUB Manual 0.97
Which of the following commands lists all currently installed packages when using RPM package management?
yum --query --all
yum --list --installed
rpm --query --all
rpm --list –installed
The command that lists all currently installed packages when using RPM package management is rpm --query --all. This command displays information about all the packages that are currently installed on the system, including their name, version, release, and architecture1. The output can be customized by using various query options and format specifiers2.
The other commands are either invalid or related to YUM, not RPM. yum --query --all is not a valid YUM command, as YUM does not have a --query option3. yum --list --installed is a valid YUM command, but it lists the packages from the YUM repositories, not the RPM database3. rpm --list --installed is not a valid RPM command, as RPM does not have a --list option2.
When using rpm --verify to check files created during the installation of RPM packages, which of the following information is taken into consideration? (Choose THREE correct answers.)
Timestamps
MD5 checksums
Inodes
File sizes
GnuPG signatures
When using rpm --verify to check files created during the installation of RPM packages, the following information is taken into consideration:
Timestamps. RPM compares the modification time of the installed files with the original time stored in the RPM database. If the file has been modified after installation, the timestamp will differ and RPM will report it with an M flag1.
MD5 checksums. RPM calculates the MD5 checksum of the installed files and compares it with the original checksum stored in the RPM database. If the file has been altered in any way, the checksum will differ and RPM will report it with an 5 flag1.
File sizes. RPM compares the size of the installed files with the original size stored in the RPM database. If the file has been truncated or appended, the size will differ and RPM will report it with an S flag1.
RPM does not take into consideration the following information:
Inodes. RPM does not check the inode number of the installed files, as it is not a reliable indicator of file identity. The inode number can change if the file is moved, copied, or restored from a backup2.
GnuPG signatures. RPM does not verify the GnuPG signatures of the installed files, as they are not part of the RPM package format. The GnuPG signatures are used to verify the authenticity and integrity of the RPM package files before installation, not after3.
To prevent users from being able to fill up the / partition, the ____________ directory should be on a separate partition if possible because it is world writeable.
/tmp
tmp
The /tmp directory should be on a separate partition if possible because it is world writable. This means that any user can create, modify, or delete files and directories in /tmp. This can pose a risk of filling up the / partition, which can cause system instability or failure. By having /tmp on a separate partition, we can limit the amount of disk space that can be used by temporary files and prevent users from affecting the / partition. The /tmp directory is also a common target for malicious attacks, so having it on a separate partition can improve the security and isolation of the system. The /tmp directory is one of the few directories that are world writable by default, according to the Filesystem Hierarchy Standard (FHS)1. The other directories that are usually world writable are /var/tmp and /var/lock, which are also used for temporary or lock files. However, these directories are not as frequently used or as large as /tmp, so they are less likely to fill up the / partition. The /tmp directory also has the sticky bit set, which means that only the owner of a file or directory can delete or rename it2. This prevents users from deleting or modifying other users’ files in /tmp. However, this does not prevent users from creating new files or directories in /tmp, which can still consume disk space and resources. Therefore, it is advisable to have /tmp on a separate partition if possible. References:
Filesystem Hierarchy Standard
Sticky bit - Wikipedia
Which of the following commands lists the dependencies of a given dpkg package?
apt-cache depends-onpackage
apt-cache dependencies package
apt-cache depends package
apt-cache requires package
The apt-cache command is used to query the APT cache for information about packages. The depends option shows a listing of each dependency a package has and all the possible other packages that can fulfill that dependency. For example, apt-cache depends ubuntu-restricted-extras will show the dependencies of the ubuntu-restricted-extras package. The other options are not valid for the apt-cache command. References:
How to Check Dependencies of a Package in Ubuntu/Debian-based Linux Distributions
Check DEB package dependencies on Ubuntu / Debian
Which of the following options is used in a GRUB Legacy configuration file to define the amount of time that the GRUB menu will be shown to the user?
hidemenu
splash
timeout
showmenu
The timeout option in a GRUB Legacy configuration file is used to define the amount of time (in seconds) that the GRUB menu will be shown to the user before booting the default entry. The timeout option is usually located in the /boot/grub/menu.lst file. For example, timeout 10 will display the GRUB menu for 10 seconds. To disable the timeout and wait for user input indefinitely, the value of timeout can be set to -1. To boot immediately without displaying the menu, the value of timeout can be set to 0. The other options are not valid for the GRUB Legacy configuration file. References:
GRUB Legacy - ArchWiki
How do I set the grub timeout and the grub default boot entry?
How to Remove the Timeout From GRUB Menu
Which of the following environment variables overrides or extends the list of directories holding shared libraries?
LD_LOAD_PATH
LD_LIB_PATH
LD_LIBRARY_PATH
LD_SHARE_PATH
LD_RUN_PATH
The environment variable that overrides or extends the list of directories holding shared libraries is LD_LIBRARY_PATH. This variable is used to specify a colon-separated list of directories where the dynamic linker should look for shared libraries when loading a program1. The directories in LD_LIBRARY_PATH are searched before the default directories, such as /lib and /usr/lib, or the directories specified in /etc/ld.so.conf or the executable’s rpath1. This variable can be useful for testing or debugging purposes, or for running programs that require a specific version of a library that is not installed in the system1.
The other options are incorrect for the following reasons:
LD_LOAD_PATH. This is not a standard environment variable for shared libraries. It may be confused with LD_PRELOAD, which is a variable that allows the user to specify one or more shared libraries that should be loaded before any other library, even the C library2. This variable can be used to override or modify the behavior of certain functions or symbols in the libraries2.
LD_LIB_PATH. This is not a standard environment variable for shared libraries. It may be confused with LIBPATH, which is a variable that is used on some Unix variants, such as AIX, to specify the search path for shared libraries3. On Linux, this variable has no effect4.
LD_SHARE_PATH. This is not a standard environment variable for shared libraries. It may be confused with LD_RUN_PATH, which is a variable that allows the user to specify a list of directories that should be embedded in the executable as the rpath5. The rpath is a attribute that tells the dynamic linker where to look for shared libraries at run time5. Unlike LD_LIBRARY_PATH, LD_RUN_PATH is only effective at link time, not at run time5.
LD_RUN_PATH. This is not an environment variable that overrides or extends the list of directories holding shared libraries, but rather one that sets the rpath of the executable at link time. See the explanation for LD_SHARE_PATH above.
Which of the following commands can be used to download the RPM package kernel without installing it?
yum download --no-install kernel
yumdownloader kernel
rpm --download --package kernel
rpmdownload kernel
The command that can be used to download the RPM package kernel without installing it is yumdownloader kernel. This command is part of the yum-utils package, which contains a suite of helper tools for yum package manager. To use this command, you need to install the yum-utils package first1. The downloaded package will be saved in the current directory. You need to use root privilege because yumdownloader will update package index files during downloading. Unlike yum command, yumdownloader will not download any dependent packages1.
The other commands are either invalid or do not have the desired functionality. yum download --no-install kernel is not a valid yum command, as yum does not have a --no-install option2. rpm --download --package kernel is not a valid rpm command, as rpm does not have a --download or a --package option3. rpmdownload kernel is not a standard Linux command. rpm has a native support to download a package from a URL and install it, but not to download a package without installing it4.
What can the Logical Volume Manager (LVM) be used for? (Choose THREE correct answers.)
To create RAID 9 arrays.
To dynamically change the size of logical volumes.
To encrypt logical volumes.
To create snapshots.
To dynamically create or delete logical volumes.
The Logical Volume Manager (LVM) is a tool that allows the creation and management of logical volumes on Linux systems. Logical volumes are partitions that can span multiple physical disks and can be resized or deleted without affecting the rest of the system. Some of the benefits of using LVM are:
To dynamically change the size of logical volumes. LVM allows the user to increase or decrease the size of a logical volume without having to repartition the disk or reboot the system. This can be useful for allocating more space to a volume that is running out of space, or freeing up space from a volume that is not needed anymore.
To create snapshots. LVM allows the user to create a snapshot of a logical volume, which is a copy of the volume at a certain point in time. Snapshots can be used for backup purposes, as they can be restored to the original volume if needed. Snapshots can also be used for testing purposes, as they can be mounted as read-only or read-write volumes without affecting the original volume.
To dynamically create or delete logical volumes. LVM allows the user to create or delete logical volumes on the fly, without having to repartition the disk or reboot the system. This can be useful for creating temporary volumes for specific purposes, or deleting volumes that are no longer needed.
LVM cannot be used for the following purposes:
To create RAID 9 arrays. RAID 9 is not a valid RAID level, and LVM does not support RAID functionality. RAID is a technique that uses multiple disks to provide redundancy, performance, or both. RAID can be implemented at the hardware level, by using a RAID controller, or at the software level, by using tools such as mdadm or dmraid. LVM can work on top of RAID devices, but it cannot create them.
To encrypt logical volumes. LVM does not provide encryption functionality. Encryption is a technique that protects data from unauthorized access by using a secret key to transform the data into an unreadable form. Encryption can be implemented at the disk level, by using tools such as dm-crypt or LUKS, or at the file system level, by using tools such as eCryptfs or EncFS. LVM can work on top of encrypted devices, but it cannot encrypt them.
Which of the following files, located in the user home directory, is used to store the Bash history?
.bash_history
.bash_histfile
.history
.bashrc_history
.history_bash
The .bash_history file, located in the user home directory, is used to store the Bash history. The Bash history is a list of commands that the user has entered in the Bash shell. The .bash_history file is created when the user first starts a Bash session, and is updated when the user exits the session or runs the history command with the -a or -w option. The user can view the contents of the .bash_history file with the cat command, or use the history command to see the numbered list of commands. The user can also edit, delete, or clear the .bash_history file with various commands and options. The location and name of the history file can be changed by setting the HISTFILE environment variable to a different value. References:
[LPI Exam 101 Detailed Objectives], Topic 103: GNU and Unix Commands, Objective 103.1: Work on the command line, Weight: 4, Key Knowledge Areas: Use of history and HISTFILE.
Where is bash’s history stored?, Topic: Bash maintains the list of commands internally in memory while it’s running.
QUESTIONNO: 26
Which Bash environment variable defines in which file the user history is stored when exiting a Bash process? (Specify ONLY the variable name.)
Answer: HISTFILE
The HISTFILE environment variable defines in which file the user history is stored when exiting a Bash process. The user history is a list of commands that the user has entered in the Bash shell. By default, the HISTFILE variable is set to ~/.bash_history, which means that the history is stored in a hidden file called .bash_history in the user’s home directory. The user can change the value of the HISTFILE variable to store the history in a different file or location. For example, the following command will set the HISTFILE variable to ~/my_history:
export HISTFILE=~/my_history
This will cause the history to be stored in a file called my_history in the user’s home directory. The user can also unset the HISTFILE variable to disable the history saving feature. For example, the following command will unset the HISTFILE variable:
unset HISTFILE
This will prevent the history from being written to any file when the Bash process exits. The user can view the value of the HISTFILE variable by using the echo command. For example, the following command will display the value of the HISTFILE variable:
echo $HISTFILE
The output will be something like:
/home/user/.bash_history
Which of the following signals is sent to a process when the key combination CTRL+C is pressed on the keyboard?
SIGTERM
SIGINT
SIGSTOP
SIGKILL
The SIGINT signal is sent to a process when the user presses the key combination CTRL+C on the keyboard. This signal is used to interrupt the process and cause it to terminate, unless the process catches or ignores the signal. The SIGTERM signal is the default signal sent by the kill command to request a process to terminate gracefully. The SIGSTOP signal is used to pause a process and make it stop executing until it receives a SIGCONT signal. The SIGKILL signal is used to force a process to terminate immediately and cannot be caught or ignored by the process. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.2 Process management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following commands can be used to determine how long the system has been running? (Choose TWO correct answers.)
uptime
up
top
uname -u
time –up
The uptime and top commands can be used to determine how long the system has been running. The uptime command displays the current time, the system load, the number of users logged in, and the time since the system was last booted. The top command displays information about the processes running on the system, as well as the system load, the number of users logged in, and the time since the system was last booted. The other options are either invalid or do not perform the desired task. The up command is not a valid Linux command. The uname -u command displays the user ID of the current user, not the system uptime. The time –up command is not a valid syntax for the time command, which measures the execution time of a command, not the system uptime. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.2 Process management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following statements is correct regarding the command foo 1> bar?
The stdout from the command foo is appended to the file bar.
The stdout from the command foo overwrites the file bar.
The command foo receives its stdin from the file bar.
The command foo receives its stdin from the stdout of the command bar.
The stderr from the command foo is saved to the file bar.
The command foo 1> bar redirects the standard output (stdout) from the command foo to the file bar, overwriting the existing contents of the file. The number 1 before the redirection operator > indicates the file descriptor of the stdout stream, which is 1 by default. The redirection operator > means that the output of the command is written to the file, replacing any previous data in the file. The file name after the redirection operator is the destination of the output. For example, if the command foo prints “Hello world” to the stdout, and the file bar contains “Goodbye world”, the command foo 1> bar will write “Hello world” to the file bar, erasing “Goodbye world”. The other options are not correct because:
A. The stdout from the command foo is appended to the file bar: This is not what 1> does, because it overwrites the file, not appends to it. To append the output to the file, the operator >> should be used instead of >.
C. The command foo receives its stdin from the file bar: This is not what 1> does, because it redirects the output, not the input. To redirect the input from the file, the operator < should be used instead of >.
D. The command foo receives its stdin from the stdout of the command bar: This is not what 1> does, because it redirects the output to a file, not to another command. To redirect the output to another command, the operator | (pipe) should be used instead of >.
E. The stderr from the command foo is saved to the file bar: This is not what 1> does, because it redirects the stdout, not the stderr. To redirect the stderr, the file descriptor 2 should be used instead of 1.
In a nested directory structure, which find command line option would be used to restrict the command to searching down a particular number of subdirectories?
-dirmax
-maxdepth
-maxlevels
-n
-s
The find command is used to search for files and directories that match certain criteria. The option -maxdepth can be used to restrict the command to searching down a particular number of subdirectories. The argument to -maxdepth is a positive integer that specifies the maximum depth of the directory tree to be searched. For example, -maxdepth 0 means only the current directory, -maxdepth 1 means the current directory and its direct subdirectories, and so on1. The option -maxdepth should be placed before any other expressions, as it affects the behavior of the whole command2. For example, to find all the files with the extension .txt in the current directory and its direct subdirectories, the command would be:
find . -maxdepth 1 -type f -name “*.txt”
The other options are not correct because:
A. -dirmax is not a valid find option.
C. -maxlevels is not a valid find option.
D. -depth is a valid find option, but it does not restrict the command to searching down a particular number of subdirectories. It only changes the order of the search, so that the files and directories are processed in depth-first order, meaning that the contents of a directory are processed before the directory itself1. References:
find(1) — Linux manual page
How to use find command to search for multiple extensions - Unix & Linux Stack Exchange
Which umask value ensures that new directories can be read, written and listed by their owning user, read and listed by their owning group and are not accessible at all for everyone else?
0750
0027
0036
7640
0029
The umask value is a four-digit octal number that determines the default permissions for new files and directories created by a user. The umask value specifies the permissions that are not granted to the user, group, and others. The permissions are represented by three bits for each category, where 1 means execute, 2 means write, and 4 means read. The sum of these values indicates the combination of permissions. For example, 7 means read, write, and execute; 6 means read and write; 5 means read and execute; 4 means read only; 3 means write and execute; 2 means write only; 1 means execute only; and 0 means no permission.
The umask value is subtracted from the maximum permissions for files and directories, which are 666 and 777, respectively. The maximum permissions are then converted to binary and bitwise ANDed with the bitwise complement of the umask value. The result is the default permissions for the new files and directories. For example, if the umask value is 0027, the default permissions for a new file are:
666 - 027 = 639 639 in octal = 110 011 001 in binary 027 in octal = 000 010 111 in binary Bitwise complement of 027 = 111 101 000 in binary 110 011 001 AND 111 101 000 = 110 001 000 in binary 110 001 000 in binary = 608 in octal 608 in octal = rw- — —
The default permissions for a new directory are:
777 - 027 = 750 750 in octal = 111 101 000 in binary 027 in octal = 000 010 111 in binary Bitwise complement of 027 = 111 101 000 in binary 111 101 000 AND 111 101 000 = 111 101 000 in binary 111 101 000 in binary = 750 in octal 750 in octal = rwx r-x —
Therefore, the umask value of 0027 ensures that new files can be read and written by their owning user, and are not accessible at all for everyone else. New directories can be read, written and listed by their owning user, read and listed by their owning group, and are not accessible at all for everyone else.
Which of the following environment variables can be defined in locale. conf? (Choose TWO correct answers )
LC_ALL
Lr_USERNAME
LCMJTF8
LC_GEOGRAPHY
LC_TIME
A faulty kernel module is causing issues with a network interface card. Which of the following actions ensures that this module is not loaded automatically when the system boots?
Using lsmod --remove --autoclean without specifying the name of a specific module
Using modinfo –k followed by the name of the offending module
Using modprobe –r followed by the name of the offending module
Adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf
Deleting the kernel module’s directory from the file system and recompiling the kernel, including its modules
The action that ensures that a faulty kernel module is not loaded automatically when the system boots is adding a blacklist line including the name of the offending module to the file /etc/modprobe.d/blacklist.conf. This file contains a list of kernel modules that are prevented from loading by the modprobe command, which is used to load and unload modules from the running kernel. By adding a line like blacklist
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute2
Linux Kernel Module Management 101 - Linux.com1
Chapter 2. Managing kernel modules - Red Hat Customer Portal2
Which of the following apt-get subcommands installs the newest versions of all currently installed packages?
auto-update
dist-upgrade
full-upgrade
install
update
The apt-get subcommand that installs the newest versions of all currently installed packages is dist-upgrade. The dist-upgrade subcommand performs the same function as the upgrade subcommand, which is to install the latest versions of the packages that are already installed on the system, but it also intelligently handles the dependencies and removes the obsolete packages if necessary. The dist-upgrade subcommand is useful when upgrading the entire system to a new release or distribution12.
The other options are either invalid or do not perform the desired task. The auto-update subcommand does not exist, and the update subcommand only updates the list of available packages from the repositories, but does not install any packages. The full-upgrade subcommand is an alias for the dist-upgrade subcommand, so it performs the same function, but it is not the standard name for the subcommand. The install subcommand installs new packages or specific versions of packages, but it does not upgrade all the currently installed packages. References:
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute2
APT-GET Command in Linux {Detailed Tutorial With Examples} - phoenixNAP3
How do I get help on apt-get’s install subcommand?
APT Cheat Sheet | Packagecloud Blog
What is true regarding UEFI firmware? (Choose two.)
It can read and interpret partition tables
It can use and read certain file systems
It stores its entire configuration on the /boot/ partition
It is stored in a special area within the GPT metadata
It is loaded from a fixed boot disk position
UEFI firmware is a software program that provides the interface between the hardware and the operating system on a computer. UEFI stands for Unified Extensible Firmware Interface and it is a replacement for the traditional BIOS (Basic Input/Output System). UEFI firmware has several advantages over BIOS, such as faster boot times, better security, larger disk support, and graphical user interface. Some of the features of UEFI firmware are12:
It can use and read certain file systems: UEFI firmware can access files on partitions formatted with FAT12, FAT16, or FAT32 file systems. This allows UEFI to load boot loaders, kernels, and configuration files from these partitions without relying on the legacy MBR (Master Boot Record) or boot sector code. UEFI firmware can also support other file systems, such as NTFS or ext4, with additional drivers.
It is loaded from a fixed boot disk position: UEFI firmware is stored in a ROM chip on the motherboard, but it also requires a special partition on the boot disk to store additional files and drivers. This partition is called the EFI System Partition (ESP) and it is usually the first partition on the disk. The ESP must have a specific GUID (Globally Unique Identifier) and must be formatted with a FAT file system. The UEFI firmware will look for the ESP on the boot disk and load the files from there.
The other options are false or irrelevant. UEFI firmware does not read and interpret partition tables, it relies on the operating system to do that. UEFI firmware does not store its entire configuration on the /boot/ partition, it stores some of its settings in the NVRAM (Non-Volatile Random Access Memory) on the motherboard and some of its files on the ESP. UEFI firmware is not stored in a special area within the GPT (GUID Partition Table) metadata, it is stored in a ROM chip and an ESP. GPT is a partitioning scheme that supports larger disks and more partitions than the legacy MBR scheme. References:
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute2
How to Boot and Install Linux on a UEFI PC With Secure Boot3
How to Access UEFI Settings From Linux - It’s FOSS4
UEFI firmware updates for linux-surface - GitHub5
Which file contains the date of the last change of a user's password?
/etc/gshadow
/etc/passwd
/etc/pwdlog
/var/log/shadow
/etc/shadow
Which of the following protocols is designed to access the video card output of a virtual machine?
KDE
X11
Xfce
SPICE
XDMCP
Which of the following is true regarding the command sendmail?
With any MTA, the sendmail command must be run periodically by the cron daemon.
When using systemd, sendmail is an alias to relayctl.
The sendmail command prints the MTA's queue history of which mails have been sent successfully.
It is only available when the sendmail MTA is installed.
All common MTAs, including Postfix and Exim, provide a sendmail command.
Which chown command will change the ownership to dave and the group to staff on a file named data.txt?
chown dave/staff data.txt
chown –u dave –g staff data.txt
chown --user dave --group staff data.txt
chown dave:staff data.txt
The chown command is used to change the owner and group of files and directories in Linux. The basic syntax of the chown command is:
chown [options] user[:group] file…
The user is the name or the numeric ID of the new owner of the file. The group is the name or the numeric ID of the new group of the file. The file is the name or the path of the file or directory to be changed. The user and group are separated by a colon (:), not a slash (/). The group is optional, and if it is omitted, the group will not be changed. The options are optional, and they can modify the behavior of the chown command, such as changing the ownership recursively, silently, or verbosely.
In this question, the user is dave and the group is staff. The file is data.txt. Therefore, the correct command to change the ownership to dave and the group to staff on data.txt is:
chown dave:staff data.txt
This command will change the owner of data.txt to dave and the group of data.txt to staff. You can verify the changes by using the ls -l command to view the owner and group of data.txt.
The other options are not correct because:
A. chown dave/staff data.txt: This command is not valid because it uses a slash (/) instead of a colon (:) to separate the user and group. The slash (/) is used to separate the directories in a path, not the user and group in the chown command. If you run this command, you will get an error message saying:
chown: invalid user: ‘dave/staff’
B. chown -u dave -g staff data.txt: This command is not valid because it uses the -u and -g options, which do not exist in the chown command. The -u and -g options are used in the chgrp command, which is used to change only the group of files and directories, not the owner. The chown command does not have the -u and -g options, and it uses the user[:group] argument to specify the new owner and group. If you run this command, you will get an error message saying:
chown: invalid option – ‘u’ Try ‘chown --help’ for more information.
C. chown --user dave --group staff data.txt: This command is not valid because it uses the --user and --group options, which do not exist in the chown command. The --user and --group options are used in the usermod command, which is used to modify the user account information, not the file ownership. The chown command does not have the --user and --group options, and it uses the user[:group] argument to specify the new owner and group. If you run this command, you will get an error message saying:
chown: unrecognized option ‘–user’ Try ‘chown --help’ for more information.
Which of the following commands will change the quota for a specific user?
edquota
repquota
quota -e
quota
The correct command to change the quota for a specific user is edquota. This command allows you to edit the quota limits for a user, a group, or a file set. You can specify the name of the user that you want to edit the quotas for after the command. For example, to change the disk quota for user ‘linuxconfig’, you can use the following command:
sudo edquota -u linuxconfig
This command will open an editor with the current quota information for the user ‘linuxconfig’. You can modify the soft and hard limits for the block and inode usage as per your requirements. You can also use the -p option to copy the quota settings from another user. For example, to copy the quota settings from user ‘ramesh’ to user ‘linuxconfig’, you can use the following command:
sudo edquota -p ramesh -u linuxconfig
The other commands are not suitable for changing the quota for a specific user. The repquota command displays a summary of the current quota usage and limits for the users or groups. The quota -e command turns off the disk quota for the current user. The quota command shows the disk quota and usage for the current user or for the users specified on the command line. For more information on how to use disk quota on Linux, you can refer to the following articles:
How to use disk quota on Linux with examples
5 Steps to Setup User and Group Disk Quota on UNIX / Linux
Which command is used to query information about the available packages on a Debian system?
apt-cache
apt-get
apt-search
dpkg
dpkg-search
The command apt-cache is used to query information about the available packages on a Debian system. This command can perform various operations on the package cache, such as searching for packages that match a given pattern, showing detailed information about a specific package, displaying the dependencies of a package, and more. The apt-cache command does not require root privileges and does not modify the system state12.
The other commands are either invalid or do not perform the same function as the correct answer. For example:
apt-get is used to install, update, upgrade, remove, or purge packages on a Debian system. It requires root privileges and modifies the system state13.
apt-search is not a valid command. The correct syntax to search for packages using the apt command is apt search1 .
dpkg is a low-level tool that can install, remove, configure, or query information about Debian packages. It operates on individual packages and does not handle dependencies. It requires root privileges to install or remove packages1 .
dpkg-search is not a valid command. The correct syntax to search for packages using the dpkg command is dpkg -l or dpkg-query -l1 .
The system is having trouble and the engineer wants to bypass the usual /sbin/init start up and run /bin/sh. What is the usual way to pass this change to the kernel from your boot loader?
Start in runlevel 1.
Pass init=/bin/sh on the kernel parameter line.
Pass /bin/sh on the kernel parameter line.
Pass start=/bin/sh on the kernel parameter line.
The usual way to pass this change to the kernel from the boot loader is to pass init=/bin/sh on the kernel parameter line12. The init kernel parameter is used to specify the program that is run as the first process after the kernel is loaded3. By default, this program is /sbin/init, which is responsible for starting and managing other processes and services4. However, by passing init=/bin/sh, the kernel will run /bin/sh instead, which is a shell program that allows the user to execute commands interactively or from a script5. This way, the user can bypass the usual initialization process and run /bin/sh as the root user, which can be useful for troubleshooting or recovery purposes12.
The other options in the question are not correct because:
A. Start in runlevel 1: This option would not bypass the /sbin/init program, but rather instruct it to start the system in single-user mode, which is a mode that allows only the root user to log in, and disables all network services and graphical interfaces. To start in runlevel 1, the user would need to pass single or 1 on the kernel parameter line, not init=/bin/sh.
C. Pass /bin/sh on the kernel parameter line: This option would not work, because the kernel would not recognize /bin/sh as a valid parameter and would ignore it. The kernel only accepts parameters that have a specific format, such as name=value or name.flag3. To specify the init program, the user would need to use the init= prefix, as in init=/bin/sh3.
D. Pass start=/bin/sh on the kernel parameter line: This option would also not work, because the kernel does not have a start parameter. The user would need to use the init parameter, as in init=/bin/sh3.
During a system boot cycle, what is the program that is run after the BIOS completes its tasks?
The bootloader
The inetd program
The init program
The kernel
The program that is run after the BIOS completes its tasks is the bootloader12. The bootloader is a small program that loads the operating system into memory and executes it. The bootloader can be located in the Master Boot Record (MBR) of the first hard disk or the boot sector of a partition for BIOS systems, or in an .efi file on the EFI System Partition for UEFI systems12. The bootloader can also display a menu to allow the user to choose from different operating systems or kernel versions to boot12.
The other options in the question are not correct because:
B. The inetd program: This is a program that listens for incoming network connections and launches the appropriate service for them. It is not involved in the boot process3.
C. The init program: This is a program that is executed by the kernel as the first user-space process. It is responsible for starting and managing other processes and services. It is not run by the BIOS.
D. The kernel: This is the core of the operating system that controls everything in the system. It is loaded and executed by the bootloader, not by the BIOS.
During a system boot cycle, what program is executed after the BIOS completes its tasks?
The bootloader
The inetd program
The init program
The kernel
The bootloader is a program that is executed by the BIOS after it completes its tasks of initializing the hardware and performing the POST (Power-On Self Test). The bootloader is responsible for loading the kernel and other necessary files into memory and passing control to the kernel. The bootloader can be either installed in the Master Boot Record (MBR) of the disk or in a separate partition. Some examples of bootloaders are GRUB, LILO, and SYSLINUX. References: LPI Linux Essentials - 1.101.1, LPI Linux Administrator - 102.1
Which of the following statements is correct when talking about /proc/?
All changes to files in /proc/ are stored in /etc/proc.d/ and restored on reboot.
All files within /proc/ are read-only and their contents cannot be changed.
All changes to files in /proc/ are immediately recognized by the kernel.
All files within /proc/ are only readable by the root user.
The /proc/ directory is a virtual filesystem that provides a view of the kernel’s data structures and parameters. It contains information about processes, hardware, memory, modules, and other aspects of the system. The files in /proc/ are not stored on disk, but are generated on the fly by the kernel when they are accessed. Therefore, any changes to files in /proc/ are immediately recognized by the kernel and affect its behavior. For example, writing a value to /proc/sys/kernel/hostname will change the system’s hostname without rebooting. The files in /proc/ are not all read-only; some of them can be modified by the root user or by processes with the appropriate permissions. The files in /proc/ are readable by any user, unless restricted by the kernel or by the mount options. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 102.3
Which of the following are init systems used within Linux systems? (Choose THREE correct answers.)
startd
systemd
Upstart
SysInit
SysV init
systemd, Upstart, and SysV init are all init systems used within Linux systems. An init system is the first process executed by the kernel at boot time, which has a process ID (PID) of 1, and is responsible for starting and managing all other processes on the system. Different init systems have different features, advantages, and disadvantages. Some of the most common init systems are:
systemd: A relatively new and modern init system that aims to provide a unified and efficient way of managing system and service states. It is compatible with SysV and LSB init scripts, and supports features such as parallel processing, socket activation, logging, job scheduling, and more. It is the default init system for many popular Linux distributions, such as Fedora, Debian, Ubuntu, Arch Linux, and others12.
Upstart: An event-based init system developed by Ubuntu as a replacement for SysV init. It starts and stops system tasks and processes based on events, such as hardware changes, network availability, filesystem mounting, etc. It is a hybrid init system that uses both SysV and systemd scripts, and supports features such as parallel processing, dependency tracking, logging, and more. It is the default init system for some older versions of Ubuntu, and some other Linux distributions, such as Linux Mint and Chrome OS12.
SysV init: A mature and traditional init system that follows the System V (SysV) design of Unix operating systems. It uses a series of runlevels to define the state of the system, and executes scripts in the /etc/rc.d or /etc/init.d directories according to the current runlevel. It is simple and stable, but lacks some features of modern init systems, such as parallel processing, event handling, dependency tracking, etc. It is still used by some Linux distributions, such as Slackware, Gentoo, and others12.
Which of the following commands reboots the system when using SysV init? (Choose TWO correct answers.)
shutdown -r now
shutdown -r "rebooting"
telinit 6
telinit 0
shutdown -k now "rebooting"
The shutdown command is used to bring the system down in a safe and controlled way. It can take various options and arguments, such as the time of shutdown, the message to broadcast to users, the halt or reboot mode, etc. The option -r instructs the shutdown command to reboot the system after shutting down. The argument now means to shut down immediately. Therefore, shutdown -r now will reboot the system without delay. The telinit command is used to change the run level of the system. It takes a single argument that specifies the new run level. The run level 6 is reserved for rebooting the system. Therefore, telinit 6 will also reboot the system. The other options are either incorrect or irrelevant. shutdown -r “rebooting” will also reboot the system, but with a delay of one minute and a message to the users. telinit 0 will halt the system, not reboot it. shutdown -k now “rebooting” will only send a warning message to the users, but not actually shut down or reboot the system. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 101.3
Which of the following information is stored within the BIOS? (Choose TWO correct answers.)
Boot device order
Linux kernel version
Timezone
Hardware configuration
The system's hostname
The BIOS (Basic Input/Output System) is a firmware that is stored in a ROM chip on the motherboard and is responsible for initializing the hardware and loading the bootloader. The BIOS has a setup utility that allows the user to configure various settings, such as the boot device order, the hardware configuration, the system date and time, the security options, etc. The BIOS does not store information about the Linux kernel version, the time zone, or the system’s hostname, as these are part of the operating system and are not relevant for the BIOS. References: LPI Linux Essentials - 1.101.1, LPI Linux Administrator - 102.1
You suspect that a new ethernet card might be conflicting with another device. Which file should you check within the /proc tree to learn which IRQs are being used by which kernel drivers?
proc/interrupts
The file that you should check within the /proc tree to learn which IRQs are being used by which kernel drivers is /proc/interrupts1 Comprehensive Explanation: The /proc/interrupts file is a virtual file that provides information about the number and type of interrupts per CPU per I/O device12. It displays the IRQ number, the number of that interrupt handled by each CPU core, the interrupt type, and a comma-delimited list of drivers that are registered to receive that interrupt12. For example, the following output shows the contents of /proc/interrupts on a system with two CPUs and several devices:
The first column shows the IRQ number, followed by one column for each CPU core showing the number of interrupts handled by that core. The last column shows the interrupt type and the driver name. Some interrupt types are:
IO-APIC-edge: An edge-triggered interrupt from the I/O Advanced Programmable Interrupt Controller (APIC), which is a hardware device that handles and distributes interrupts.
IO-APIC-fasteoi: A fast end-of-interrupt from the I/O APIC, which means that the interrupt is acknowledged early to allow nesting interrupts.
PCI-MSI-edge: A Message Signaled Interrupt (MSI) from the Peripheral Component Interconnect (PCI) bus, which is a hardware bus that connects devices to the system. MSI is a method of sending interrupts using special messages instead of dedicated lines.
NMI: A Non-Maskable Interrupt, which is a hardware interrupt that cannot be ignored by the CPU and usually indicates a critical error.
LOC: A Local timer interrupt, which is a periodic interrupt generated by a local APIC on each CPU core for scheduling purposes.
RES: A Rescheduling interrupt, which is a type of inter-processor interrupt (IPI) that is sent to a CPU core to force it to reschedule its current task.
To check if a new ethernet card might be conflicting with another device, you can look for the driver name of the ethernet card in the /proc/interrupts file and see if it shares the same IRQ number with another device. If so, you can try to change the IRQ assignment of the devices or use the smp_affinity file to control which CPU cores can handle the interrupt12.
Which run levels should never be declared as the default run level when using SysV init? (Choose TWO correct answers.)
0
1
3
5
6
Run levels are predefined modes of operation in the SysV init system that determine which processes and services are started or stopped. The default run level is the one that the system enters after booting. It is usually specified in the /etc/inittab file with a line like id:5:initdefault:. The run levels 0 and 6 should never be declared as the default run level because they are used to halt and reboot the system, respectively. If they are set as the default, the system will enter an endless loop of shutting down and restarting. The other run levels (1-5) have different meanings depending on the distribution, but they usually correspond to single-user mode, multi-user mode, network mode, graphical mode, etc. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 101.3
Which command will display messages from the kernel that were output during the normal boot sequence?
dmesg
The command dmesg will display messages from the kernel that were output during the normal boot sequence. The dmesg command reads the kernel ring buffer, which is a data structure that stores the most recent messages generated by the kernel. The dmesg command can also be used to display messages from the kernel that were output after the boot sequence, such as hardware events, driver messages, or system errors. The dmesg command has various options to filter, format, or save the output. For example, dmesg -T will display human-readable timestamps for each message, and dmesg -w will display the messages in real time as they occur. References:
1: How to view all boot messages in Linux after booting? - Super User
2: dmesg(1) - Linux manual page
3: Kernel ring buffer - Wikipedia
What is the first program that is usually started, at boot time, by the Linux kernel when using SysV init?
/lib/init.so
/sbin/init
/etc/rc.d/rcinit
/proc/sys/kernel/init
/boot/init
The first program that is usually started, at boot time, by the Linux kernel when using SysV init is /sbin/init. This program is responsible for reading the /etc/inittab file and executing the appropriate scripts and programs for each runlevel. The other options are not valid programs that are started by the kernel. /lib/init.so is a shared library that is used by some init programs, but not by SysV init. /etc/rc.d/rcinit is a script that is run by init, not by the kernel. /proc/sys/kernel/init is a kernel parameter that can be used to specify a different init program, but the default value is /sbin/init. /boot/init is not a standard location for an init program, and it is unlikely that the kernel would find it there. References:
1: SysVinit - ArchWiki
2: Linux: How to write a System V init script to start, stop, and restart my own application or service - nixCraft
3: sysvinit - Gentoo wiki
The message "Hard Disk Error" is displayed on the screen during Stage 1 of the GRUB boot process. What does this indicate?
The kernel was unable to execute /bin/init
The next Stage cannot be read from the hard disk because GRUB was unable to determine the size and geometry of the disk
One or more of the filesystems on the hard disk has errors and a filesystem check should be run
The BIOS was unable to read the necessary data from the Master Boot Record to begin the boot process
The GRUB boot process consists of three stages1:
Stage 1: This stage is located in the Master Boot Record (MBR) of the first hard disk or the boot sector of a partition. Its main function is to load either Stage 1.5 or Stage 22.
Stage 1.5: This stage is located in the first 30 KB of hard disk immediately following the MBR or in the boot sector of a partition. It contains the code to access the file system that contains the GRUB configuration file. Its main function is to load Stage 22.
Stage 2: This stage is located in an ordinary file system, usually in the /boot/grub directory. It contains the code to display the GRUB menu and to load the kernel and initrd images. It can also load additional modules to support other file systems or features2.
The message “Hard Disk Error” is displayed on the screen during Stage 1 of the GRUB boot process. This indicates that the next Stage (either Stage 1.5 or Stage 2) cannot be read from the hard disk because GRUB was unable to determine the size and geometry of the disk3. This could occur because the BIOS translated geometry has been changed by the user or the disk is moved to another machine or controller after installation, or GRUB was not installed using itself (if it was, the Stage 2 version of this error would have been seen during that process and it would not have completed the install)3.
The other options in the question are not correct because:
A. The kernel was unable to execute /bin/init: This error would occur in Stage 2, after the kernel and initrd images are loaded, not in Stage 14.
C. One or more of the filesystems on the hard disk has errors and a filesystem check should be run: This error would also occur in Stage 2, when GRUB tries to access the file system that contains the GRUB configuration file, not in Stage 15.
D. The BIOS was unable to read the necessary data from the Master Boot Record to begin the boot process: This error would prevent GRUB from starting at all, not in Stage 16.
Which of the following commands will write a message to the terminals of all logged in users?
bcast
mesg
wall
yell
The wall command is a command-line utility that displays messages to all logged-in users on the terminal12. The wall command takes the following basic syntax:
$ wall OPTION { file | message }
The OPTION can be one of the following:
-n or --nobanner: Suppress the banner (the header line with the hostname, date, and time) from the output. This option can only be used by the root user.
-v or --version: Display version information and exit.
-h or --help: Display help message and exit.
The file or message argument is the source of the message to be displayed. If a file is specified, the wall command will read the message from the file. If a message is specified, the wall command will read the message from the standard input. The message can be terminated by pressing Ctrl+D.
The other commands in the options are not valid or do not have the same functionality as the wall command:
bcast: There is no such command in Linux.
mesg: This command is used to control write access to the terminal. It does not send messages to other users.
print: This command is used to print files or data to a printer. It does not send messages to other users.
yell: There is no such command in Linux.
What of the following statements are true regarding /dev/ when using udev? (Choose TWO correct answers.)
Entries for all possible devices get created on boot even if those devices are not connected.
Additional rules for udev can be created by adding them to /etc/udev/rules.d/.
When using udev, it is not possible to create block orcharacter devices in /dev/ using mknod.
The /dev/ directory is a filesystem of type tmpfs and is mounted by udev during system startup.
The content of /dev/ is stored in /etc/udev/dev and is restored during system startup.
udev is a device manager that dynamically creates and removes device nodes in the /dev/ directory. It also handles device events, such as adding, removing, or changing the attributes of devices. udev uses rules to match devices and assign properties, permissions, names, symlinks, and other actions. The rules are stored in files under /lib/udev/rules.d/ and /etc/udev/rules.d/. The latter directory can be used to create additional or override existing rules. The /dev/ directory is not a regular directory on the root filesystem, but a virtual filesystem of type tmpfs that is mounted by udev during system startup. tmpfs is a filesystem that resides in memory and can grow and shrink dynamically. The content of /dev/ is not stored in /etc/udev/dev, but is created by udev based on the rules and the available devices. udev does not prevent the creation of block or character devices in /dev/ using mknod, but it may overwrite or remove them if they conflict with the rules or the device events. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 102.4
You are having some trouble with a disk partition and you need to do maintenance on this partition but your users home directories are on it and several are logged in. Which command would disconnect the users and allow you to safely execute maintenance tasks?
telinit 1
shutdown -r now
killall -9 inetd
/bin/netstop --maint
/etc/rc.d/init.d/network stop
The command that would disconnect the users and allow you to safely execute maintenance tasks on a disk partition is telinit 112. The telinit command is used to change the runlevel of the system, which is a mode of operation that defines what processes and services are running3. The runlevel 1, also known as single-user mode, is a mode that allows only the root user to log in, and disables all network services and graphical interfaces4. This mode is useful for performing system maintenance and recovery tasks, such as repairing a disk partition5.
The other options in the question are not correct because:
B. shutdown -r now: This command would reboot the system immediately, without disconnecting the users gracefully or allowing you to do any maintenance tasks.
C. killall -9 inetd: This command would kill the inetd process, which is a daemon that manages network services. This would not disconnect the users who are already logged in, and it would not stop other processes that might interfere with the maintenance tasks.
D. /bin/netstop --maint: There is no such command in Linux.
E. /etc/rc.d/init.d/network stop: This command would stop the network service, which would disconnect the users who are logged in remotely, but not the ones who are logged in locally. It would also not stop other processes that might interfere with the maintenance tasks.
Which file in /proc describes the IRQs that are used by various kernel drivers? (Specify the file name only without any path.)
interrupts
What is the process ID number of the init process on a SysV init based system?
-1
0
1
It is different with each reboot.
It is set to the current run level.
The process ID number of the init process on a SysV init based system is 1. The init process is the first process that runs on the system, and it is responsible for initializing the user-space environment and spawning all other processes. The init process is always the first process that runs on the system, and it has the process ID (PID) of 1. The PID is a unique identifier for each process on the system, and it is assigned by the kernel. The PID of the init process is always 1, regardless of the reboot or the run level. You can verify the PID of the init process by using the ps command, which shows information about the processes on the system. For example, to show the PID, the user, the command, and the arguments of the init process, use the following command:
ps -p 1 -o pid,user,cmd
The output of the command will show something like:
PID USER CMD 1 root /sbin/init
This shows that the init process has the PID of 1, the user of root, and the command of /sbin/init.
After running the command umount /mnt, the following error message is displayed:
umount: /mnt: device is busy.
What is a common reason for this message?
The kernel has not finished flushing disk writes to themounted device.
A user has a file open in the /mnt directory.
Another file system still contains a symlink to a file inside /mnt.
The files in /mnt have been scanned and added to the locate database.
The kernel thinks that a process is about to open a file in /mnt for reading.
One of the common reasons for the error message “device is busy” when trying to unmount a file system is that a user or a process has a file open in the mounted directory. This prevents the kernel from releasing the file system resources and detaching the device. To find out which user or process is holding the file system, one can use the lsof or fuser commands12. For example, lsof /mnt or fuser -m /mnt will list the processes that have open files in /mnt. To force the unmounting of a busy file system, one can use the -l option of the umount command, which will perform a lazy unmount. This means that the file system will be detached as soon as it is not busy anymore3. References: 1: How to solve “device is busy” problem in Linux 2: How to Find Out Which Process Is Using a File in Linux 3: umount(8) - Linux man page
Which of the following commands instructs SysVinit to reload its configuration file?
reinit
initreload
telinit 7
telinit q
init reinit
SysVinit is a program for Linux and Unix-based systems that initializes the system and spawns all other processes. It runs as a daemon and has PID 1. The boot loader starts the kernel and the kernel starts SysVinit. A Linux or Unix based system can be started up into various runlevels, which are modes of operation that define what services and processes are running. The /etc/inittab file is the configuration file for SysVinit, which defines the default runlevel, the available runlevels, and the actions to be taken when entering or leaving a runlevel.
The telinit command is used to change the current runlevel of the system or to send a signal to SysVinit. The telinit command takes a single argument, which can be either a runlevel number (0-6) or a special character. The syntax of the telinit command is:
telinit [runlevel|character]
The runlevel argument instructs SysVinit to switch to the specified runlevel. For example, to switch to runlevel 3, which is the multi-user mode with networking, use the following command:
telinit 3
The character argument instructs SysVinit to perform a special action. For example, to reboot the system, use the following command:
telinit 6
The q character argument instructs SysVinit to reload its configuration file, /etc/inittab, without changing the current runlevel. This is useful when the /etc/inittab file has been modified and the changes need to be applied. For example, to reload the /etc/inittab file, use the following command:
telinit q
The other options are not correct because:
A. reinit: This command does not exist in the Linux system. There is no such command as reinit in the Linux documentation or the man pages.
B. initreload: This command does not exist in the Linux system. There is no such command as initreload in the Linux documentation or the man pages.
C. telinit 7: This command is not valid because 7 is not a valid runlevel number. The valid runlevel numbers are 0-6, where 0 means halt, 1 means single-user mode, 2 means multi-user mode without networking, 3 means multi-user mode with networking, 4 means user-defined, 5 means graphical mode, and 6 means reboot. If you run this command, you will get an error message saying:
telinit: invalid runlevel: 7
E. init reinit: This command is not valid because reinit is not a valid argument for the init command. The init command is a synonym for the telinit command, and it takes the same arguments as the telinit command. The valid arguments for the init command are either a runlevel number (0-6) or a special character. If you run this command, you will get an error message saying:
init: invalid runlevel: reinit
Which of the following commands updates the already installed RPM package rpmname?
rpm --update rpmname
rpm –U rpmname
rpm –q rpmname
rpm --force rpmname
rpm –u rpmname
The rpm command is used to install, upgrade, query, verify and remove RPM packages on Linux systems. The -U option is used to upgrade an existing package to a newer version, or install a package if it does not exist in the RPM database. The -U option is equivalent to -e (erase) followed by -i (install). The other options are not valid for upgrading a package. The -q option is for querying a package, the -e option is for erasing a package, the --force option is for overriding conflicts, and the -u option is not a valid option for the rpm command. References: Using RPM Command to Install, Upgrade and Remove Packages, Linux package management with YUM and RPM
When piping the output of find to the xargs command, what option to find is useful if the filenames have spaces in them?
–rep-space
–print0
–nospace
–ignore-space
Pressing the Ctrl-C combination on the keyboard while a command is executing in the foreground sends the SIGINT(2) signal code. The SIGINT(2) signal means interrupt and is usually sent when the user presses Ctrl-C on the keyboard. The signal causes the process to terminate, unless it is caught or ignored by the process. The SIGHUP(1) signal means hang up and is usually sent when the terminal or network connection is disconnected. The SIGQUIT(3) signal means quit and is usually sent when the user presses Ctrl-\ on the keyboard. The SIGKILL(9) signal means kill and is used to force the process to terminate immediately, without any chance to catch the signal or perform any cleanup. The SIGTERM(15) signal means terminate and is the default signal sent by the kill command. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, Signal List
Which of the following describes the correct order in which the components of the system boot process are started?
BIOS, kernel, bootloader, init system
BIOS, bootloader,kernel, init system
Bootloader, BIOS, kernel, init system
BIOS, bootloader, init system, kernel
Bootloader, BIOS, init system, kernel
The system boot process is the sequence of steps that the system follows when it is powered on or restarted. The system boot process can be divided into four main components: BIOS, bootloader, kernel, and init system. The order in which these components are started is:
BIOS: BIOS stands for Basic Input/Output System, and it is the first component that runs when the system is powered on. BIOS is a firmware program that is stored in a ROM chip on the motherboard, and it performs some basic tasks, such as:
initializing the hardware components and peripherals
performing the power-on self-test (POST) to check the system integrity
selecting a boot device from the boot order list
loading and executing the bootloader program from the boot device
Bootloader: Bootloader is a small program that is responsible for loading and executing the kernel. Bootloader is usually stored in the first sector of the boot device, which can be a hard disk, a USB drive, or a CD-ROM. Bootloader can also display a menu that allows the user to choose from different kernel images or operating systems. Some common bootloaders for Linux systems are GRUB, LILO, and SYSLINUX.
Kernel: Kernel is the core of the operating system, and it manages the system resources, controls the hardware devices, and provides basic services to other programs. Kernel is a large binary file that is compressed and stored in the boot device, usually in the /boot directory. Kernel is loaded into memory and executed by the bootloader, and it performs some tasks, such as:
decompressing itself and relocating to a higher memory address
detecting and initializing the hardware devices and drivers
mounting the root filesystem and creating a temporary filesystem in RAM
starting the init system, which is the first user-space program
Init system: Init system is the program that initializes the user-space environment and spawns all other processes. Init system is always the first process that runs on the system, and it has the process ID (PID) of 1. Init system can also perform some tasks, such as:
reading the configuration files and scripts that define the system services and runlevels
starting and stopping the system services and daemons
managing the system logins and terminals
running a graphical user interface or a command-line interface
Some common init systems for Linux systems are SysVinit, systemd, and Upstart.
Which of the following command lines creates or, in case it already exists, overwrites a file called data with the output of ls?
ls 3> data
ls >& data
ls > data
ls >> data
The command line that will create or, in case it already exists, overwrite a file called data with the output of ls is ls > data. The > character is a redirection operator that redirects the standard output (STDOUT) of a command to a file. If the file does not exist, it will be created. If the file already exists, it will be overwritten. The 3> character is not a valid redirection operator. The >& character is a redirection operator that redirects both standard output (STDOUT) and standard error (STDERR) of a command to a file. The >> character is a redirection operator that appends the standard output (STDOUT) of a command to a file, without overwriting the existing file contents. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, Redirection
Which of the following commands prints a list of available package updates when using RPM-based package management?
dpkg list
yum list
dpkg check-update
yum check-update
yum list-update
The command yum check-update prints a list of available package updates when using RPM-based package management. This command queries all enabled repositories and shows the packages that have updates available, along with the new version number. This command does not actually update any packages, but only lists them. To update the packages, the command yum update can be used. The other commands are either invalid or belong to a different package management system. dpkg is a low-level tool for Debian-based package management, and yum list shows all available packages in the repositories, not just the ones that have updates. References:
Linux Package Management with Yum, RPM, Apt, Dpkg, Aptitude and Zypper - Part 9
rpm - RPM package management tool | Linux Docs
RPM Command in Linux | Linuxize
How can the list of files that would be installed by the RPM package file apache-xml.rpm be previewed?
rpm –qp apache-xml.rpm
rpm –qv apache-xml.rpm
rpm –ql apache-xml.rpm
rpm –qpl apache-xml.rpm
The command rpm -qpl apache-ql.rpm is used to preview the list of files that would be installed by the RPM package file apache-xml.rpm. This command queries the package file without installing it and lists the contents of the package. Here’s what each part of the command means:
rpm is the command-line tool used for managing RPM packages on Linux systems.
-qpl are options for the rpm command.
q stands for query mode
l stands for list the contents of the package.
p specifies that the package being queried is not installed, but is a file located on the system.
apache-xml.rpm is the name of the RPM package file you want to query.
So, when you run this command, it will display a list of all the files that are included in the apache-xml.rpm package file, without installing it. This can be useful for checking what files are included in the package before installing it or comparing it with another version of the package.
The other commands are either invalid or do not perform the same function as the correct answer. For example:
rpm -qp apache-xml.rpm will only display the name and version of the package, not the list of files.
rpm -qv apache-xml.rpm will display the verbose information about the package, such as the description, license, and changelog, but not the list of files.
rpm -ql apache-xml.rpm will list the files that are installed on the system by the apache-xml.rpm package, but only if the package is already installed. If the package is not installed, it will return an error.
Which of the following commands is used to change metadata and options for ext3 filesystems?
mod3fs
tune3fs
mod2fs
tune2fs
dump2fs
The tune2fs command is used to change metadata and options for ext2, ext3, and ext4 filesystems. The tune2fs command can adjust various parameters such as the maximum mount count, the check interval, the reserved blocks percentage, the volume label, and the UUID. The tune2fs command can also enable or disable some filesystem features, such as the journal, the dir_index, the acl, and the user_xattr. The tune2fs command requires the device name or the UUID of the filesystem as an argument, and one or more options to specify the changes to be made. For example, to change the volume label of an ext3 filesystem on /dev/sda1 to “data”, use the following command:
tune2fs -L data /dev/sda1
The other options are not valid commands or options. The mod3fs and mod2fs commands do not exist on a standard Linux system. The tune3fs command is a synonym for tune2fs, but it is not commonly used. The dump2fs command is used to display the superblock and blocks group information for ext2, ext3, and ext4 filesystems, but it does not change any parameters or options. References:
tune2fs - adjust tunable filesystem parameters on ext2/ext3/ext4 …
Chapter 5. The Ext3 File System - Red Hat Customer Portal
Chapter 37. Getting started with an ext3 file system - Red Hat Customer …
Which option to the tee command will cause the output to be concatenated on the end of the output file instead of overwriting the existing file contents?
–a
–c
--no-clobber
--continue
The -a option to the tee command will cause the output to be appended to the end of the output file instead of overwriting the existing file contents. The tee command reads from standard input (STDIN) and writes to standard output (STDOUT) and one or more files simultaneously. For example, ls | tee file.txt will display the output of the ls command and also write it to file.txt. If file.txt already exists, it will be overwritten unless the -a option is used. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, tee command
In Bash, inserting 1>&2 after a command redirects
standard error to standard input.
standard input to standard error.
standard output to standard error.
standard error to standard output.
standard output to standard input.
In Bash, inserting 1>&2 after a command redirects standard output to standard error. This means that the output of the command that normally goes to the standard output stream (file descriptor 1) will be sent to the standard error stream (file descriptor 2) instead. This can be useful if we want to capture or discard both the normal output and the error output of a command. For example, if we want to run a command and send both its output and error to /dev/null (a special device that discards any data written to it), we can use:
command > /dev/null 1>&2
This will redirect the standard output of command to /dev/null, and then redirect the standard error of command to the same place as the standard output, which is /dev/null. The other options are not correct because:
A. standard error to standard input: This is not possible, because standard input is a read-only stream, and we cannot redirect output to it.
B. standard input to standard error: This is not what 1>&2 does, because 1 refers to standard output, not standard input. To redirect standard input to standard error, we would need to use 0>&2, where 0 refers to standard input.
D. standard error to standard output: This is not what 1>&2 does, because it would require the opposite order of file descriptors: 2>&1. This would redirect standard error to standard output, not the other way around.
E. standard output to standard input: This is not possible, for the same reason as option A. References:
Bash redirections cheat sheet
How to redirect stderr to a file - Linuxize
You are trying to make a hard link to an ordinary file but ln returns an error. Which of the following could cause this?
The source file is hidden.
The source file is read-only.
The source file is a shell script.
You do not own the source file.
The source and the target are on different filesystems.
A hard link is a directory entry that refers to the same inode as another file. An inode is a data structure that stores the metadata and the location of the data blocks of a file. A hard link allows multiple names to refer to the same file content, as long as they are on the same filesystem. However, if the source and the target of the hard link are on different filesystems, the ln command will return an error, because the inode numbers are not consistent across different filesystems. Therefore, the ln command cannot create a hard link that crosses filesystem boundaries. The other options are either incorrect or not applicable. The source file being hidden, read-only, a shell script, or not owned by the user does not prevent the creation of a hard link, as long as the user has the permission to write to the target directory and the source and the target are on the same filesystem. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.3 Perform basic file management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following explanations are valid reasons to run a command in the background of your shell?
The command does not need to execute immediately.
The command has to run immediately but the user needs to log out.
The system is being shut down and the command needs to restart execution immediately after the reboot.
The command can run at a lower priority than normal commands run on the command line.
Running a command in the background of your shell means that the command will execute asynchronously, without blocking the shell prompt or waiting for user input. This can be useful for commands that take a long time to complete, or that do not require user interaction. One of the valid reasons to run a command in the background is when the command has to run immediately but the user needs to log out. For example, if the user wants to start a backup process that will take several hours, but also wants to close the terminal session and log out from the system, they can run the backup command in the background by appending an ampersand (&) to the command line. This way, the backup command will continue to run even after the user logs out, and the user can check the status or output of the command later. The other options are either incorrect or not applicable. Running a command in the background does not affect the execution priority of the command, which is determined by the nice value and the scheduler. Running a command in the background does not delay the execution of the command, which will start as soon as possible. Running a command in the background does not guarantee that the command will survive a system shutdown or reboot, unless the command is configured to do so with a service manager or a startup script. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.1 Work on the command line
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following partition types is used for Linux swap spaces when partitioning hard disk drives?
82
83
8e
fd
7
Linux swap spaces are designated as type 82 on MBR (Master Boot Record) partition tables, which are used to store information about the partitions on a hard disk drive. This type code identifies the partition as a Linux swap area, which can be used by the Linux kernel to supplement the system RAM by holding idle memory pages. The mkswap command can be used to initialize a partition of type 82 as a swap partition. Other type codes are used for different purposes, such as 83 for Linux native partitions, 8e for Linux LVM partitions, fd for Linux RAID partitions, and 7 for NTFS partitions. References:
How to create swap partition in Linux
Choosing partition types for swap and root and choosing device for bootloader installation
Creating and Using a Swap Partition
Swap

TESTED 04 Mar 2026
Copyright © 2014-2026 DumpsTool. All Rights Reserved
