Which two log format types are supported by the JATP appliance? (Choose two.)
You are asked to detect domain generation algorithms
Which two steps will accomplish this goal on an SRX Series firewall? (Choose two.)
Exhibit
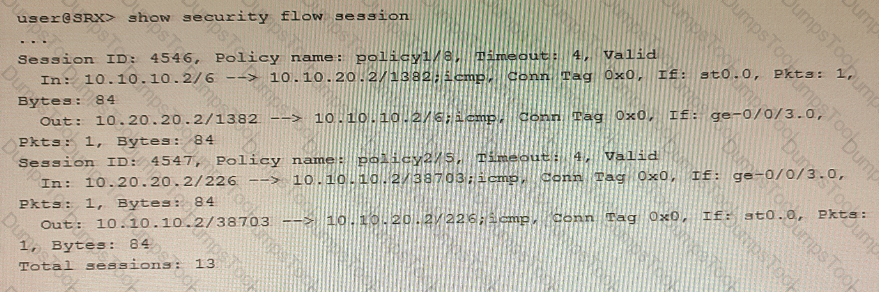
You are validating bidirectional traffic flows through your IPsec tunnel. The 4546 session represents traffic being sourced from the remote end of the IPsec tunnel. The 4547 session represents traffic that is sourced from the local network destined to the remote network.
Which statement is correct regarding the output shown in the exhibit?
you must create a secure fabric in your company’s network
In this Scenario, Which three statements are correct? (Choose Three)
You configured a chassis cluster for high availability on an SRX Series device and enrolled this HA cluster with the Juniper ATP Cloud. Which two statements are correct in this scenario? (Choose two.)
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
Exhibit
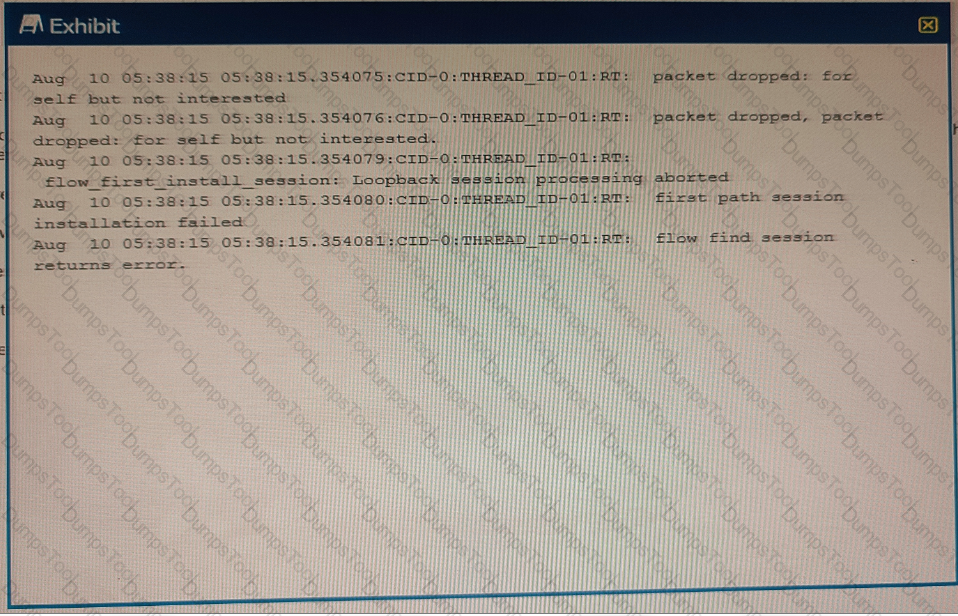
You are asked to establish an IBGP peering between the SRX Series device and the router, but the session is not being established. In the security flow trace on the SRX device, packet drops are observed as shown in the exhibit.
What is the correct action to solve the problem on the SRX device?
Exhibit
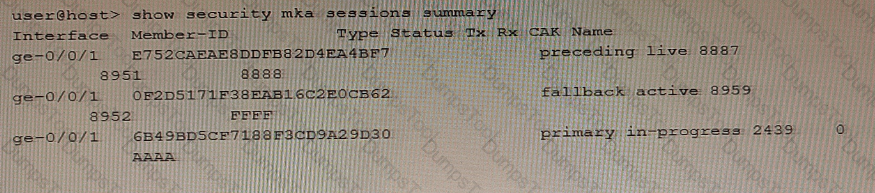
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
You issue the command shown in the exhibit.
Which policy will be active for the identified traffic?
Which method does an SRX Series device in transparent mode use to learn about unknown devices in a network?
Exhibit
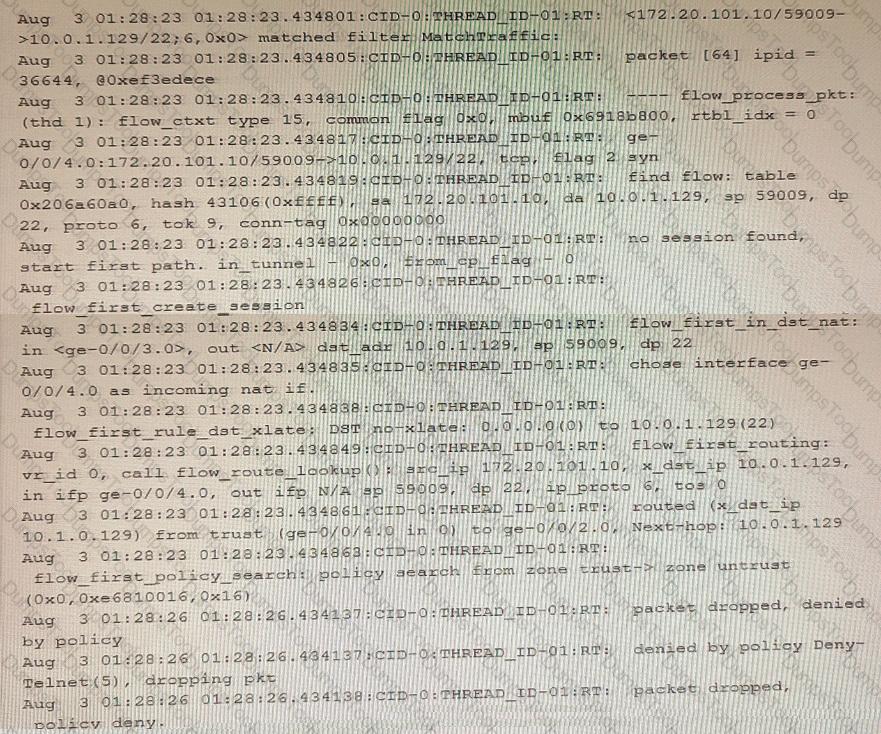
Which two statements are correct about the output shown in the exhibit? (Choose two.)
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request? (Choose three.)
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
Exhibit
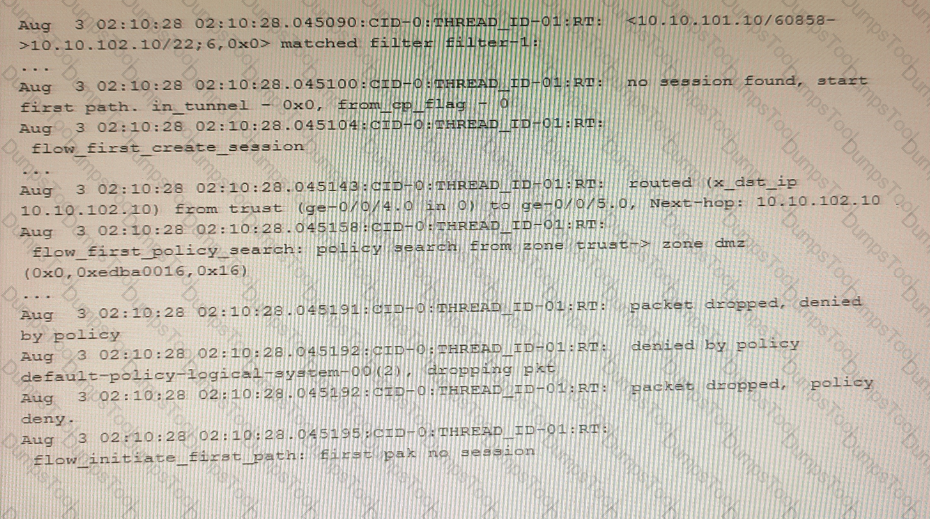
Which two statements are correct about the output shown in the exhibit? (Choose two.)
Exhibit.
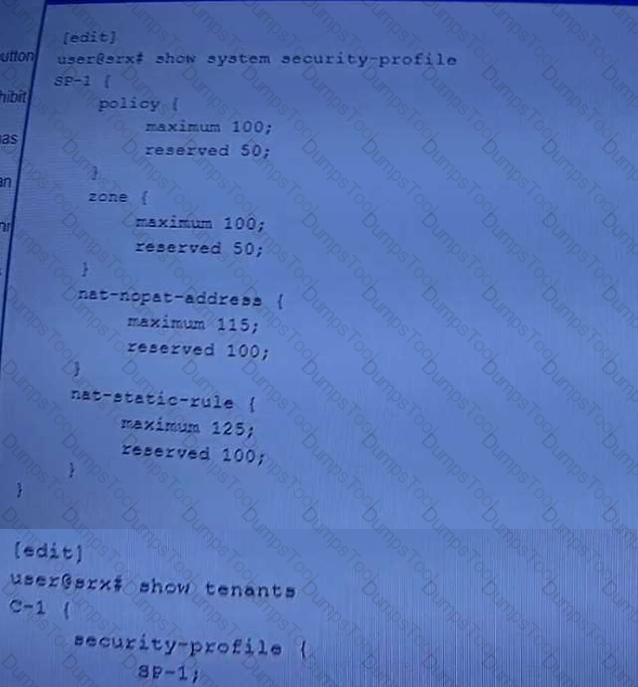
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit
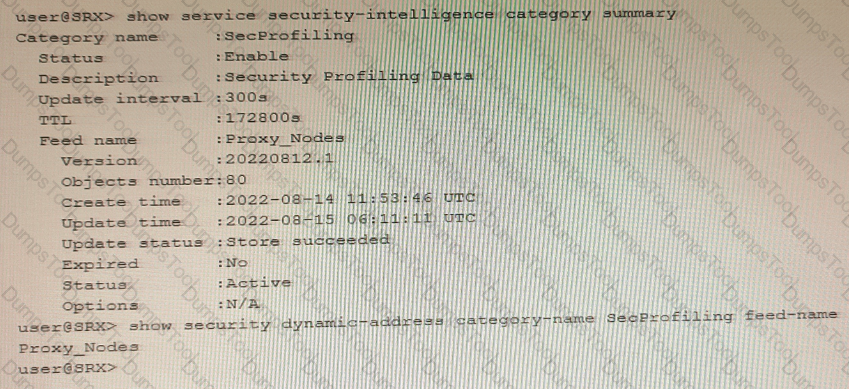
You have recently configured Adaptive Threat Profiling and notice 20 IP address entries in the monitoring section of the Juniper ATP Cloud portal that do not match the number of entries locally on the SRX Series device, as shown in the exhibit.
What is the correct action to solve this problem on the SRX device?
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
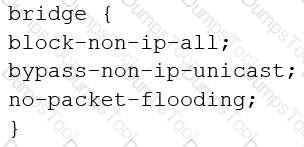
B)
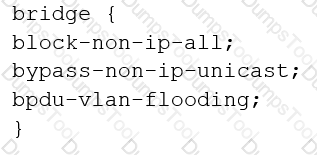
C)
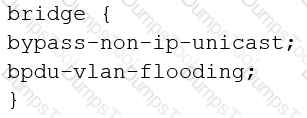
D)
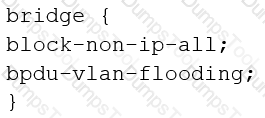
According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
A company wants to par??on their physical SRX series firewall into multiple logical units and assign
each unit (tenant) to a department within the organization. You are the primary administrator of firewall
and a colleague is the administrator for one of the departments.
Which two statements are correct about your colleague? (Choose two)
You must setup a Ddos solution for your ISP. The solution must be agile and not block legitimate traffic.
Which two products will accomplish this task? (Choose two.)
Exhibit
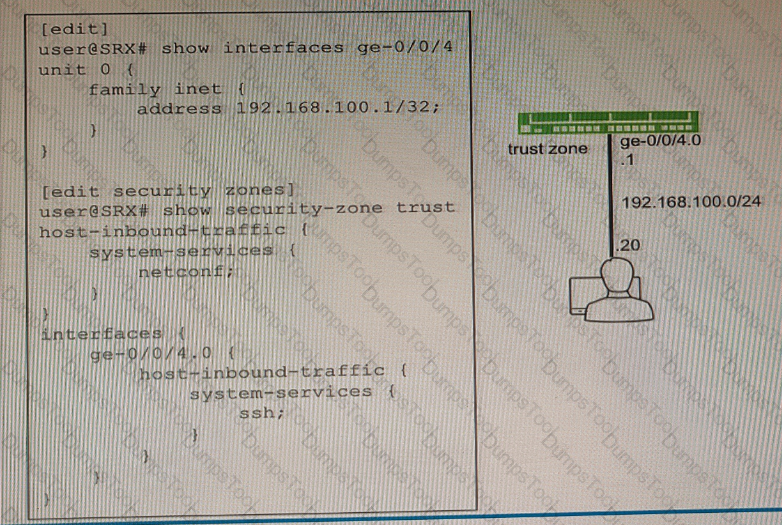
You are not able to ping the default gateway of 192.168 100 1 (or your network that is located on your SRX Series firewall.
Referring to the exhibit, which two commands would correct the configuration of your SRX Series device? (Choose two.)
A)

B)
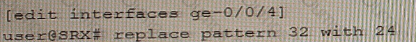
C)

D)

You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
You want to enable inter-tenant communica?on with tenant system.
In this Scenario, Which two solutions will accomplish this task?
You are asked to configure a security policy on the SRX Series device. After committing the policy, you receive the “Policy is out of sync between RE and PFE
Which command would be used to solve the problem?
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?