A software module to be used in a mission critical application incorporates an algorithm for secure transmission of data.
Which review type is most appropriate to ensure high quality and technical correctness of the algorithm?
During which review process activity are the exit criteria for an inspection defined?
Which of the following statements BEST describes the shift-left approach in software testing?
Which of the following options cover the test types performed during typical system testing phase:
I. Usability
II Requirements based scenarios
III Testing parts of the code in isolation
IV Correct order of parameters in API calls
Which of the following statements about test estimation approaches is CORRECT?
The following sentences refer to the 'Standard for Software Test Documentation' specification (IEEE 829).
Which sentence is correct?
Which ONE of the following options CORRECTLY describes one of the seven principles of the testing process?
Which of the following options should NOT be used for writing acceptance criteria?
Which of the following should be included in a test status report?
I. Estimation details
II. Total number of open and closed defects
III Actual effort spent
IV. Defect reports
V. Number of executed, failed, blocked tests
Which of the following tasks is MOST LIKELY to be performed by the tester?
Which of the following does MOT describe a reason why testing is necessary?
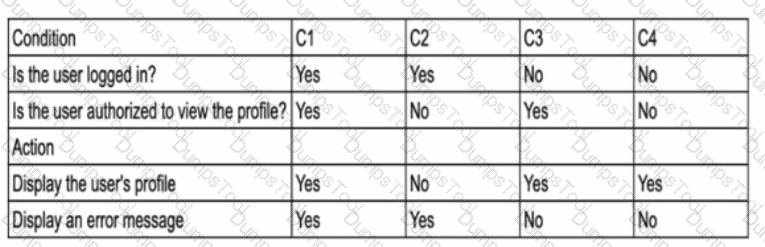
A tester created a decision table(DT) given below. While reviewing the DT some of the actions for the given conditions were found to be incorrect. The user is trying to view the profile, which of the given conditions has CORRECT action(s) listed?
A company wants to reward each of its salespeople with an annual bonus that represents the sum of all the bonuses accumulated for every single sale made by that salesperson. The bonus for a single sale can take on the following four values: 3%, 5%, 7% and 10% (the percentage refers to the amount of the single sale). These values are determined on the basis of the type of customer (classified as "Basic" or "Premium") to which such sale was made, and on the amount of such sale classified into the following three groups G1, G2 and G3:
• [G1]: less than 300 euros
• [G2]: between 300 and 2000 euros
• [G3]: greater than 2000 euros
Which of the following is the minimum number of test cases needed to cover the full decision table associated with this scenario?
Which of the following statements about the typical activities of a formal review process is TRUE?
Which of the following is NOT a typical debugging activity when a failure is triggered by dynamic testing?
Given the following user story for the development of an online shoe store:
"As a customer, I want to be able to filter shoes by color so that I see, for example, only red shoes in the selection."
Which of the following positive test cases BEST fits to the user story?
Which ONE of the following activities TYPICALLY belongs to the planning phase of the review process?
Which of the following exemplifies how a software bug can cause harm to a company?
In which of the following test documents would you expect to find test exit criteria described9
You are working on creating test cases for a user story -
As a customer, I want to be able to book an ISTQB exam for a particular date, so that I can find choose my time slot and pay the correct amount, including discounts, if any.
The acceptance criteria for this :
1. The dates shown should be from the current date to 2 years in future
2. Initially there should be 10 timeslots available for each day, 1 hour each, starting at 8 AM GMT
3. Maximum 5 persons should be able to select a time slot after which that time slot should become unavailable
4. First timeslot should have a 10% discount
Which of the following is the BEST example of a test case for this user story?
For the following pseudo-code determine number of tests required for 100% statement coverage
IF Gender = Boy
If Age > 3 AND Age < 5
Shoe Size = 1
ELSE IF Age >=5 AND Age < 7
Shoe Size = 2
ENDIF
ELSE
IF Age > 3 AND Age < 5
Shoe Size = 0
ELSE IF Age >=5 AND Age < 7
Shoe Size = 1
ENDIF
ENDIF
Which of the following statements are true?
1. Early and frequent feedback helps to avoid requirements misunderstanding.
2. Early feedback allows teams to do more with less.
3. Early feedback allows the team to focus on the most Important features.
4. Early and frequent feedback clarifies customer feedback by applying static testing techniques
Select the correct answer:
Which of the following statements about testing in the context of an agile (iterative-incremental) development model is correct?
Which one of the following statements relating to the benefits of static testing is NOT correct?
A mid-size software product development company has analyzed data related to defects detected in its product and found out that detects fixed in earlier builds are getting re-opened after a few months.
The company management now seeks your advice in order to reverse this trend and prevent re-opening of defects fixed earlier.
What would be your FIRST recommendation to the company?
Which of the following is a typical potential risk of using test automation tools?
For a given set of test-cases, which of the following is a benefit of running these tests with a test automation tool?
Which ONE of the following options MOST ACCURATELY describes statement testing?
Which ONE of the following options BEST describes the third test quadrant (Q3)?
In which of the following cases you would NOT execute maintenance testing?
Which of the following statements is LEAST likely to be describing component testing?
You work as a test manager for a supplier of PC games which can be purchased and downloaded via an online store. A tester from your team recorded the following failure caused by a defect:
Issue ID: DEF00223167
Title: Saving after shopping in online shop fails
Date: 2023-04-18
Tester: Sabine Meier
Description: "Saving the game immediately after purchasing it in the online store fails. As a result, the purchase is paid for, but the goods are not delivered."
Attached data: "log.txt", "screen1.bmp", "screen2.bmp"
During the review of the defect report, you notice that at least one important piece of information is missing for defining how to deal with the defect. Which one?
Which statement best describes the key difference between a mindset for test activities and a mindset for development activities?
Which of the following can be considered a VALID exit criterion?
I Estimates of defect density or reliability measures.
II. The completion and publication of an exhaustive Test Report.
III. Accuracy measures, such as code, functionality or risk coverage.
IV Residual risks such as lack of code coverage in certain areas.
Which of the following best describes the way in which statement coverage is measured?
A test manager decided to skip static testing since he believes bugs can be found easily by doing dynamic testing. Was this decision right or wrong?
In Agile teams, testers closely collaborate with all other team members. This close collaboration could be problematic and result in testing-related organizational risks.
Which TWO of the following organization risks could be encountered?
I.Testers lose motivation and fail at their core tasks.
ii.Close interaction with developers causes a loss of the appropriate tester mindset.
iii.Testers are not able to keep pace with incoming changes in time-constrained iterations.
iv.Testers, once they have acquired technical development or business skills, leave the testing team.
The following state transition diagram describes the functionality involved in a system using fingerprint and password authentication to log onto a system.
How many distinct states of the system are visible in the above diagram?
Which of the following project scenario gives the BEST example where maintenance testing should be triggered?
Testing Quadrants, as a model, is effective in aligning stakeholders within Agile teams.
Which of the following examples demonstrates this?
Which of the following statements is true in regards to how the context of a project affects the testing process?
The following requirement is given “Set X to be the sum of Y and Z”.
All the following four implementations have bugs.
Which one of the following bugs can be caught by Static Analysis?
A financial institution is to implement a system that calculates the interest rates paid on investment accounts based on the sum invested.
You are responsible for testing the system and decide to use equivalence partitioning and boundary value analysis to design test cases. The requirements describe the following expectations:
Investment range| Interest rate
R500 to RIO 00010%
RIO 001 to R50 00011%
R50 001 to RlOOOOO12%
RIOOOOl to R500 000| 13%
What is the minimum number of test cases required to cover all valid equivalence partitions for calculating the interest?
Which ONE of the following statements would you expect to be the MOST DIRECT advantage of the whole-team approach?
Which ONE of the following options is a PRODUCT risk and NOT a PROJECT risk?
A number of characteristics are given for impact of SDLC on the testing effort.
i. Finishing of requirements review leading to test analysis
ii. Both - static and dynamic testing performed at unit testing level
iii. Frequent regression testing may need to be performed
iv Extensive product documentation
v. More use of exploratory testing
Which of the following statements is MOST correct?
The following state diagram is given as basis for state transition testing and contains only valid transitions:
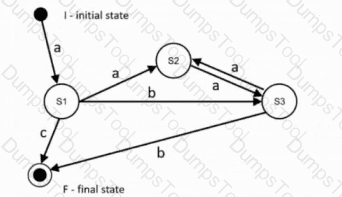
Explanation of the state diagram: States are depicted as nodes. The initial state is I, the final state is F. A state transition is depicted as a directed arrow with the initiating event as a label, e. g. from I to S1 with event a, and is also written as a triple (I,a,S1). Note: A test case is a sequence of events that initiates the corresponding sequence of state transitions.
The state diagram contains the following 7 state transitions:
(I, a, S1)
(S1, a, S2), (S1, b, S3), (S1, c, F)
(S2, a, S3)
(S3, a, S2), (S3, b, F)
What is the minimum number of test cases to achieve 100% coverage of all valid state transitions in the diagram?
Consider an estimation session in which a six-member Agile team (Memb1..... Memb6) uses the planning poker technique to estimate a user story (in story points). The team members will use a set of cards with the following values: 1,2, 3,5, 8,13,21. Below is the outcome of the first round of estimation for this session:
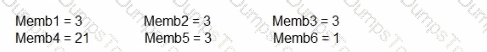
Which of the following answers BEST describes how the estimation session should proceed?
Which of the following is a CORRECT statement about how a tester should communicate about defects, test results, and other test information?
Which ONE of the following elements is TYPICALLY NOT part of a test progress report?
Pariksha labs is a mature software testing company. They are TMMi level 5 certified. Their testing processes are well defined. Which ONE of the following statements is likely to be CORRECT about them?
During component testing of a program if 100% decision coverage is achieved, which of the following coverage criteria is also guaranteed to be 100%?
You are a tester working on a critical project. Based on the risk analysis you execution? Priority 1 is the highest and Priority 3 is the lowest priority.
Calculate the measurement error SD for the following estimates done using three point estimation technique-Most optimistic effort (a) -120 person days Most likely effort (m) -180 person days Most pessimistic effort (b) - 240 person days
You need to test the login page of a web site. The page contains fields for user name and password. Which test design techniques are most appropriate for this case?
A new web app aims at offering a rich user experience. As a functional tester, you have run some functional tests to verify that, before releasing the app, such app works correctly on several mobile devices, all of which are listed as supported devices within the requirements specification. These tests were performed on stable and isolated test environments where you were the only user interacting with the application. All tests passed, but in some of those tests you observed the following issue: on some mobile devices only, the response time for two web pages containing images was extremely slow.
Based only on the given information, which of the following recommendation would you follow?
Which of the following statements about how different types of test tools support testers is true?
Which of the following issues cannot be identified by static analysis tools?
Consider the following statements (I to V) about software testing:
I. Can be applied to non-executable work products.
II. Can be used to measure performance efficiency.
III. Can lead to the detection of defects.
IV. Can find defects directly.
V. Can identify unexpected behaviors caused by potential defects.
Which ONE of the following options is the list that characterizes static tests the BEST?
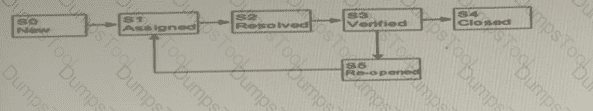
Which sequence of state transition stated in the answer choices is correct in accordance with the following figure depicting me life-cycle of a defect?
Which of the following answers describes a reason for adopting experience-based testing techniques?
A class grade application for instructors assigns letter grades based on students' numerical grades.
The letter grades for different numerical grades should be:
Above 89, up to 100 - A
Above 79, up to 89 • B
Above 69, up to 79 • C
Above 59, up to 69 - D
Below 60- F
Which of the following sets of test inputs would achieve the relatively highest equivalence partition coverage?
Which of the following statements about decision tables are TRUE?
I. Generally, decision tables are generated for low risk test items.
II. Test cases derived from decision tables can be used for component tests.
III. Several test cases can be selected for each column of the decision table.
IV. The conditions in the decision table represent negative tests generally.
You are testing a room upgrade system for a hotel. The system accepts three differed types of room (increasing order of luxury): Platinum. Silver and Gold Luxury. ONLY a Preferred Guest Card holder s eligible for an upgrade.
Below you can find the decision table defining the upgrade eligibility:
What is the expected result for each of the following test cases?
Customer A: Preference Guest Card holder, holding a Silver room
Customer B: Non Preferred Guest Card holder, holding a Platinum room
A state transition diagram describes a control system’s behavior in different operational modes. The initial state is “NORMAL MODE”.
Which ONE of the following test cases covers an INVALID sequence?
Which of the following BEST matches the attributes with a level of testing?
I. Stubs and drivers are often used
II The lest environment should correspond to the production environment
III Finding defects is not the main focus
IV Testing can be based on use cases
V Testing is normally performed by testers
VI Testing for functional and non-functional characteristics
Which of the following statements about impact of DevOps on testing is CORRECT?
Which ONE of the following options identifies the perspectives through which a collective authorship process generates a shared vision of user stories?
Which of the following statements about reviews are TRUE?
I. In walkthroughs the review meeting is typically led by the author.
II Inspection is characterized by an open-ended review meeting
III Preparation before the review meeting is part of informal reviews
IV Management rarely participates in technical review meetings
Which of the following statements best describes how configuration management supports testing?
Which of the following BEST distinguishes the terms "validation" and "verification"?
Use Scenario 1 “Happy Tomatoes” (from the previous question).
Using the Boundary Value Analysis (BVA) technique (in its two-point variant), identify the set of input values that provides the HIGHEST coverage.
Which of the following is a factor that contributes to a successful review?
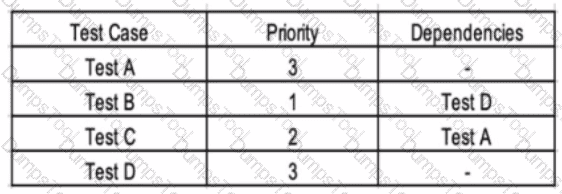
For each of the test cases to be executed, the following table specifies the priority order and dependencies on other test cases
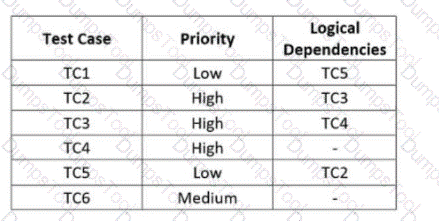
Which of the following test execution schedules is compatible with the logical dependencies and allows executing the test cases in priority order?
Which of the following BEST describes a test summary report for executive-level employees
A test score indicator for students produces a performance score based on a combination of the number of consecutive hours studied (below 4 hours, 4 to 8 hours. 9 to 12 hours or above 12 hours) and the average intensity of focus on the material during the study time (low, medium or high).
Given the following test cases:
hours intensity score
T1 3 low55
T2 14 high 95
T3 9 low75
What is the minimum number of additional test cases that are needed to ensure full coverage of all valid INPUT equivalence partitions?
What does the "absence-of-defects fallacy" refer to in software development?
Which of the following statements is true?
Select exactly one option (1 out of 4)!
Which ONE of the following options explains a benefit of independent testing the BEST?
Consider the following user story about the authentication functionality of an e-commerce website:
"As a logged-in user, I want to change my current password with a new one, so that I can make my account safer".
The following are some of the acceptance criteria defined for the user story:
[a] After the logged-in user has successfully changed his password, an email confirming the change must be sent to him
[b] To successfully change the password, the logged-in user must enter the current password, enter a new valid password, and finally confirm by pressing the 'Change Password' button
[c] To be valid, the new password entered by the logged-in user is not only required to meet the criteria related to the length and type of characters, but must also be different form the last 5 passwords of that user
[d] A dedicated error message must be presented to the logged-in user when he enters a wrong current password
[e] A dedicated error message must be presented to the logged-in user when he enters the correct current password, but enters an invalid password
Based only on the given information, which of the following ATDD tests is most likely to be written first?
The statement: "Test activities should start in the early stages of the lifecycle, adhering to the testing principle of early testing” is relevant to which of the recognized software development models?
Which of the following statements best describes the value of maintaining traceability in software testing?
You are performing the role of tester on an Agile project. Which of the following tasks would be your responsibility?
i. Understanding, implementing, and updating the test strategy.
II. Ensuring the proper use of testing tools.
Hi. Coaching other team members in the relevant aspects of testing.
iv. Actively collaborating with developers and business stakeholders to clarify requirements, especially in terms of testability, consistency, and completeness.
v. Participating proactively in team retrospective meeting, suggesting and implementing improvements.
Select the correct answer:
Which of the statements on confirmation testing and regression testing is correct?
Which of the following statements is an example of testing contributing to higher quality?
Which of the following statements best describes the difference between product risk and project risk in software testing?
Which of the following statements best describes the objective of branch testing?
Which of the following is a good testing practice which is applicable INDEPENDENT of the software development lifecycle followed?
Which ONE of the following statements does NOT describe how testing contributes to higher quality?