If an asset owner wants to improve their organization’s ability to respond during a cyberattack, which of the following activities would be MOST appropriate to implement?
What type of malware disrupted an emergency shutdown capability in safety systems?
What programs are MOST effective if they are tailored to the audience, consistent with company policy, and communicated regularly?
What is a major reason for maintaining an asset inventory baseline in Configuration Management (SP Element 2)?
What does the expression SL-T (BPCS Zone) vector {2 2 0 1 3 1 3} represent?
What type of attack is characterized by encrypting an organization’s data and demanding payment for restoration?
Why is patch management more difficult for IACS than for business systems?
Available Choices (select all choices that are correct)
Which part of the ISA/IEC 62443 series describes a methodology to develop quantitative metrics?
What does Layer 1 of the ISO/OSI protocol stack provide?
Available Choices (select all choices that are correct)
What.are the two elements of the risk analysis category of an IACS?
Available Choices (select all choices that are correct)
Safety management staff are stakeholders of what security program development?
Available Choices (select all choices that are correct)
Which is a PRIMARY reason why network security is important in IACS environments?
Available Choices (select all choices that are correct)
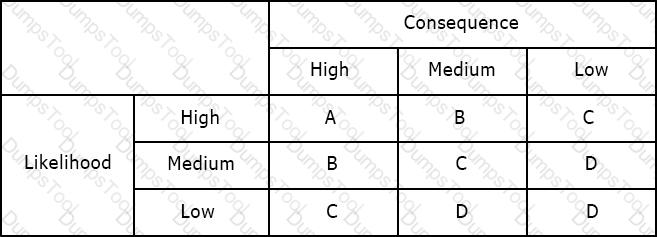
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
Which is an important difference between IT systems and IACS?
Available Choices (select all choices that are correct)
A manufacturing plant is developing a cybersecurity plan for its IACS that must evolve as new threats emerge and system changes occur. Which document should serve as the foundation for this evolving security approach?
A manufacturing plant has inconsistent cybersecurity processes that vary widely between shifts and teams. According to the maturity levels described in ISA/IEC 62443-2-1, how would this situation be classified?
Under User Access Control (SP Element 6), which of the following is included in USER 1 — Identification and Authentication?
Authorization (user accounts) must be granted based on which of the following?
Available Choices (select all choices that are correct)
If an asset owner wants to improve their organization's ability to respond during a cyberattack, which of the following activities would be MOST appropriate to implement?
As related to technical security requirements for IACS components, what does CCSC stand for?
According to the scheme for cybersecurity profiles, which of the following is true about ISA/IEC 62443 security requirements when creating a security profile?
Which U.S. Department is responsible for the Chemical Facility Anti-Terrorism Standards (CFATS)?
An industrial facility wants to ensure that only authorized communication reaches its PLCs while minimizing disruption to time-sensitive control processes. Which type of firewall would BEST suit this need?
How many element groups are in the "Addressing Risk" CSMS category?
Available Choices (select all choices that are correct)
Which of the following is an element of security policy, organization, and awareness?
Available Choices (select all choices that are correct)
What does the abbreviation CSMS round in ISA 62443-2-1 represent?
Available Choices (select all choices that are correct)
Which factor drives the selection of countermeasures?
Available Choices (select all choices that are correct)
In which layer is the physical address assigned?
Available Choices (select all choices that are correct)
Which of the following is a recommended default rule for IACS firewalls?
Available Choices (select all choices that are correct)
A company is developing an automation solution and wants to align its cybersecurity efforts with ISA/IEC 62443 standards. Which lifecycle phases should be integrated into their project plan to cover both security and automation solution security comprehensively?
What is recommended to use between the plant floor and the rest of the company networks?
In a defense-in-depth strategy, what is the purpose of role-based access control?
Available Choices (select all choices that are correct)
If an asset owner wants to demonstrate compliance with ISA/IEC 62443-2-1 requirements during an external audit, which type of evidence would be MOST appropriate?
What are the three main components of the ISASecure Integrated Threat Analysis (ITA) Program?
Available Choices (select all choices that are correct)
What is the purpose of ISO/IEC 15408 (Common Criteria)?
Available Choices (select all choices that are correct)
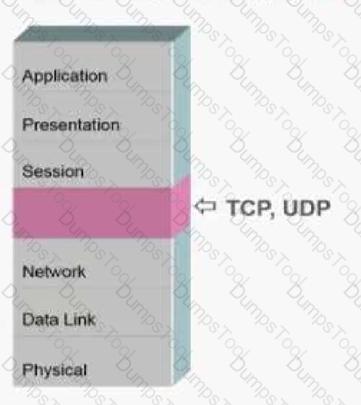
What is the name of the missing layer in the Open Systems Interconnection (OSI) model shown below?
Which Security Level (SL) would be MOST appropriate for a system that requires protection against attackers with high motivation and extended resources using sophisticated means?
A company discovers malware on a portable USB device used within their IACS environment. According to the document, which SP Element and controls would be MOST relevant to address this issue?
A manufacturing plant wants to improve its risk management by categorizing all equipment and tracking their status and relationships. Which framework should it implement?
What is the definition of "defense in depth" when referring to cybersecurity?
How many security levels are in the ISASecure certification program?
Available Choices (select all choices that are correct)
An industrial facility wants to ensure that only authorized systems reach its PLCs while minimizing disruption to time-sensitive control processes. Which type of firewall would BEST suit this need?
Which characteristic is MOST closely associated with the deployment of a demilitarized zone (DMZ)?
Available Choices (select all choices that are correct)
Which of the following is an example of a device used for intrusion detection?
At Layer 4 of the Open Systems Interconnection (OSI) model, what identifies the application that will handle a packet inside a host?
Available Choices (select all choices that are correct)
To which category of the ISA-62443 (IEC 62443) series does the document titled "Patch management in the IACS environment" belong?
The ISA/IEC 62443 Profiles Group will include parts starting with which number?