In an IPv4 address space, Class D addresses are used for multicast. Among Class D addresses, which of the following is the permanent group address range reserved for routing protocols?
On an OSPF network, there are multiple types of packets, each with a different function. Which of the following are the main functions of Hello packets?
On a WLAN, the HSB service sets up an HSB channel between two devices that back up each other, maintains the channel status, and backs up data. Which of the following can HSB back up in real time?
Four routers run ISIS and have established adjacencies. The area IDs and router levels are marked in the following figure. If route leaking is configured on R3, which of the following is the cost of the route from R4 to 10.0.2.2/32?
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
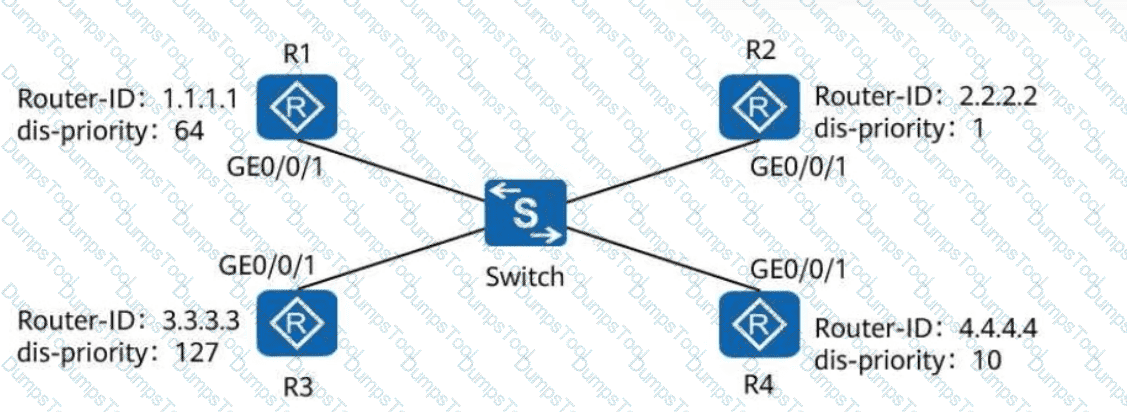
On a broadcast IS-IS network shown in the following figure, a DIS needs to be elected to create and update pseudonodes. Which of the following routers is elected as the DIS?
BFD can quickly detect faults in channels at multiple network layers, ensuring high reliability. To which of the following layers does BFD belong?
On an enterprise network, the directly connected interfaces of two OSPF routers are on different network segments and have different masks. To establish an OSPF neighbor relationship between the two interfaces, you can change their network types to which of the following?
Which of the following PIM protocol packets have unicast destination addresses.
Multicast applies to any point-to-multipoint data transmission. Which of the following types of application data can be forwarded in multicast mode?
VRRP defines three states. Only the device in which state can forward packets destined for a virtual IP address?
(Write in full and capitalize the first letter.)
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
On a network, each router has a local core routing table and protocol routing tables. A routing entry in the local core routing table has multiple key fields. Which of the following are included?
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
Hackers often obtain the login permissions of system administrators through various attacks.
Which of the following measures can be taken to enhance the security of administrator accounts?(Select all that apply)
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
On the OSPF network shown in the figure, an adjacency has been established between R1 and R2. An engineer configures the commands in the figure on R2. In this case, which of the following routing entries may exist in the routing table of R2?
On an OSPF network, routers learn routing information on the entire network by exchanging LSAs. Which of the following values is the LS Age in the LSA header when an LSA is deleted?
On an OSPF network, an IR in area 0 must be a BR, but an ASBR may not be an ABR.
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?
If the interval for two consecutive packets of a TCP session reaching the firewall is longer than the aging time of the session, the firewall deletes the session information from the session table to ensure network security.
An edge port is a new port role added to RSTP to overcome the disadvantages of STP. Which of the following statements is false about this port role?
The following figure shows acampus network. IS-IS is configured on all routers, and the network runs normally.
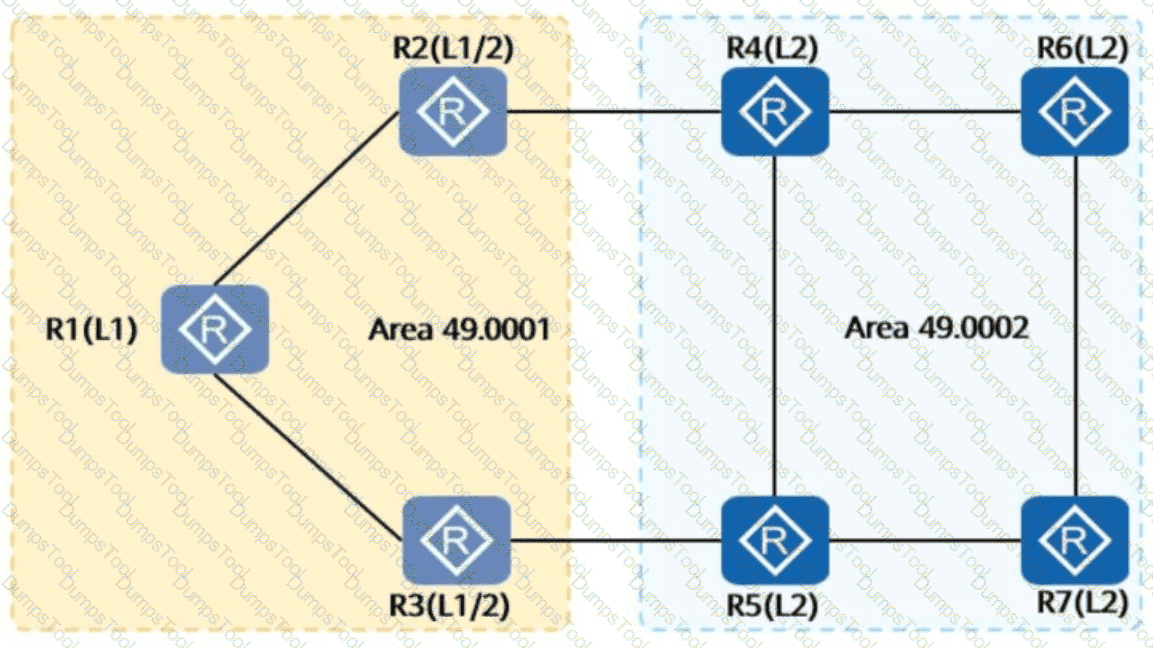
By default, which of the following routers havespecific routeson the entire network?
Which of the following methods is usually used by a network administrator to configure a newly purchased device for the first time?
An enterprise administrator views the following details about a BGP route during routine O&M:
yaml
CopyEdit
BGP local router ID: 10.1.1.1
Local AS number: 100
Paths: 2 available, 0 best, 0 select
BGP routing table entry information of 192.168.1.1/32:
From: 10.1.1.2 (10.1.1.2)
Route Duration: 00h01m31s
Relay IP Nexthop: 0.0.0.0
Relay IP Out-Interface: --
Original nexthop: 172.16.1.2
AS-path: 200, origin incomplete, MED 0, localpref 100, pref-val 0, internal, pre 255, invalid for IP unreachable
Not advertised to any peer yet
Which of the following statements are true about the BGP route?
OSPF supports area authentication and interface authentication. If both authentication modes are configured, Interface authentication takes preference over area authentication.
In special scenarios, when advertising routes to an IBGP peer, a BGP device needs to set the next hop to its IP address to prevent blackhole routes. Which of the following commands can be run in this case?
An IP prefix list is a common matching tool used in routing policies. Which of the following cannot be configured as matching conditions in an IP prefix list on a Huawei router?
A non-client is an IBGP peer that functions as neither an RR nor a client. A non-client must establish fully meshed connections with the RR and all the other non-clients.
The Next_Hop attribute in BGP records the next hop of a route. Similar to the next hop in an IGP, the Next_Hop attribute in BGP must be the IP address of a peer interface.
BGP can select routes based on the AS_Path attribute. Therefore, in some cases, a route-policy needs to be used to modify the AS_Path attribute for route selection. Which of the following parameters can be specified in the apply as-path command for a route-policy to modify this attribute?
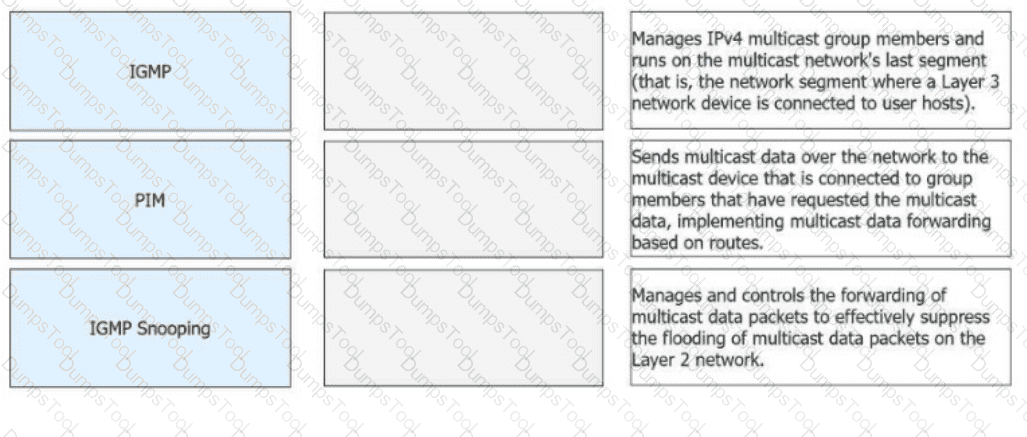
Match the following IPv4 multicast protocols with the corresponding functions.
As shown in the figure, SWA, SWB, and SWC run the Rapid Spanning Tree Protocol (RSTP). What are the roles of SWB's GE0/0/2 and SWC's GE0/0/1?
In IP multicast, RPF routes can be elected only from among unicast routes and multicast static routes.
Which of the following statements isfalseabout thesession table mechanismon firewalls?
BFD can associate with multiple protocols to quickly detect faults.
Which of the following functions are supported?(Select all that apply)
There are two types ofBGP peer relationships:EBGPandIBGP. When configuring EBGP, ensure that the peer IP address is routable and theUDPconnection can be correctly established.
When a BGP device sends an Open message to establish a peer connection, which of the following information is carried?
To prevent loops on anSTP network, after adesignated portis elected, it mustwait for a long timeand can forward packetsonly after the status of all ports on the entire network is determined. To solve this problem,RSTP uses the P/A mechanismto speed up thedownstream port's transition to the Forwarding state.
IP multicast effectively conserves network bandwidth and reduces network load. Therefore, it is widely used in network services, such as IPTV, real-time data transmission, and multimedia conferencing.
After IPsec is deployed on an enterprise network, services are interrupted. The administrator finds that no data flow triggers IKE negotiation.
Which of the following are possible causes?(Select all that apply)
Which of the following statements about the forwarding plane of a switch is false?
The filter-policy 2000 export command is run in an ISIS process. Which of the following statements about the functions of a filter policy is false?
RSTP provides different functions in different scenarios. Which of the following statements Is false?
An enterprise uses OSPF to implement network communication. To ensure data validity and security, all authentication modes supported by OSPF are enabled on routers. In this case, interface authentication is preferentially used by the routers.
Which of the following statements regarding the BGP error display of a router false?
The Origin attribute is used to define the origin of BGP path information. There are three types of Origin attributes. Which of the following lists the Origin attributes in descending order of priority?
On an IS-IS network, each device needs to be configured with anetwork entity title (NET), which consists of three parts, each containing different fields. Which of the following fields are contained in theArea Address part?
In the OSPF protocol, intra-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
SSHis a secure protocol that establishes tunnels for users on insecure networks.Which of the following statements is false about SSH login?
Which of the following configurations are not mandatory when an administrator configures VRRP?
By default, if no router ID is configured but multiple loopback interface addresses are configured, BGP selects the largest loopback interface address as the router ID.
On an IS-IS network, the length and components of aNETare the same as those of anNSAP. Which of the followingNETfields is used to uniquely identify a host or router in an area?
Typically, a protocol that occupies two ports during communication is called a multi-channel protocol. For such protocols, the ASPF function must be enabled on the firewall to ensure smooth setup of the data channel and reduce the risk of attacks. Which of the following protocols is not a multi-channel protocol?
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
The administrator of an enterprise configuresSNMPv3on a device for communicating with theNMS (Network Management System). After the configuration is complete, thedisplay trapbuffercommand output shows that there are traps in the trap buffer of theinformation center, but theNMS does not receive any of them. Which of the following may cause this problem?
See the following figure. RTA, RTB, RTC, and RTD are in the same AS and establish IBGP peer relationships through direct links. RTB an RTC are route reflectors (RRs), RTA and RTC are the RR clients of RTB, and RTB and RTD are the RR clients of RTC. If RTA advertises the route 10.1.1.0/24 to the BGP process, the Originator ID of the BGP route received by RTD is------------------.
IGMP has three versions. Different versions support different features. Which of the following features is supported by all versions?
A filter named si is configured on a device using the as-path-filter command and is applied to a specified BGP peer. The detailed configurations are as follows:
csharp
Copy
[SW1] ip as-path-filter si permit _65500$
[SW1] bgp 65100
[SW1-bgp] ipv4-family unicast
[SW1-bgp-af-ipv4] peer 10.1.1.2 as-path-filter si import
After the configuration is complete, which of the following statements is true about the way the local device processes the routes received from the peer?
On Huawei switches, which of the following planes provides network information and forwarding entries that are mandatory for data plane forwarding?
To inject IGP routes into BGP routes, you can only use the network command.
Which of the following attributes must be carried when BGP sends route update messages?
A company has a stack consisting of three switches that are running properly. The master switch restarts due to a fault. Given this, which of the following statements are true?
BGP is a distance-vector protocol that implements route reachability between ASs and selects optimal routes. Which of the following statements are true about this protocol?
On an IS-IS network, all routers generate LSPs. Which of the following types of information isnotcontained in the LSPs generated by pseudonodes?
By default, some security zones are created when Huawei firewalls are enabled. Which of the following security zones is created by users?
GRE is a VPN technology that can implement packet transmission over heterogeneous networks. Which of the following statements are true about GRE?
On aBGP network, aroute-policycan be used to modify route attributes. Which of the following statements isfalseaboutroute-policies?
An IP prefix list is configured on a router using the following command:
ip ip-prefix huawei index 10 permit 10.1.1.0 24 greater-equal 26
In this case, the value ofgreater-equal-valueis ____, and the value ofless-equal-valueis ____.
Which of the following statements regarding the summary automatic command and BGP route summarization is false?
BFD provides fast fault detection independent of media and routing protocols. To use this mechanism to detect link connectivity, devices at both ends must support this feature.
See the command output of a router below. Which of the following statements is true?
OSPF Process 1 with Router ID 10.0.2.2
Interface: 10.0.12.2 (GigabitEthernet 0/0/0)
Cost: 1 State: BDR Type: Broadcast MTU: 1500
Priority: 1
Designated Router: 10.0.12.1
Backup Designated Router: 10.0.12.2
Timers: Hello 10 , Dead 40 , Poll 120 , Retransmit 5 , Transmit Delay 1
On an IPv6 network, intermediate forwarding devices do not fragment IPv6 packets for the purpose of reducing their packet processing pressure. Packets are fragmented only on the source node.
In BGP, Keepalive messages are used to maintain BGP peer relationships. When a BGP router receives a Keepalive message from a peer, the BGP router sets the state of the peer to Established and periodically sends Keepalive messages to maintain the connection. By default, the device sends Keepalive messages every seconds.
A route-policy consists of one or more nodes. What is the maximum number of nodes in a route-policy?
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
To overcome the disadvantages ofSTP,RSTPchanges the format ofconfiguration BPDUs. Which of the following fields inSTP BPDUsis used to specify theport role?
See the network shown in the following figure.
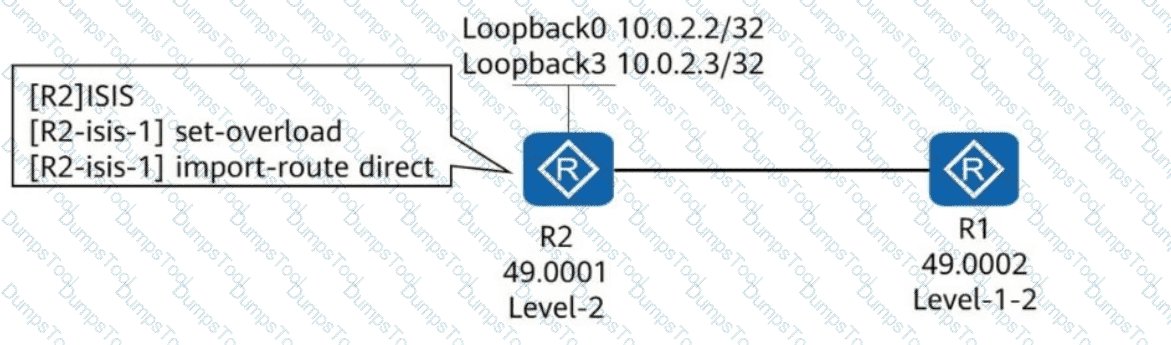
R1 and R2 run IS-IS and establish an adjacency. IS-IS is enabled on Loopback0 of R2 but disabled on Loopback3 of R2. The configurations shown in the figure are performed in the IS-IS process of R2. Which of the following statements are true?
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
OSPF networks are classified into broadcast, P2P, P2MP, and NBMA networks. Which of the following types of networks use the default Hello time (30s)?
Which of the following is the default dead time of an interface on an OSPF P2P or broadcast network?