Which three FortiOS tools can you use to troubleshoot RADIUS authentication issues? (Choose three.)
Refer to the exhibits.
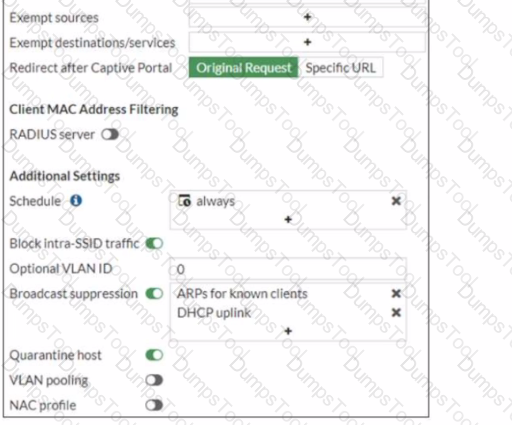
Firewall Policy
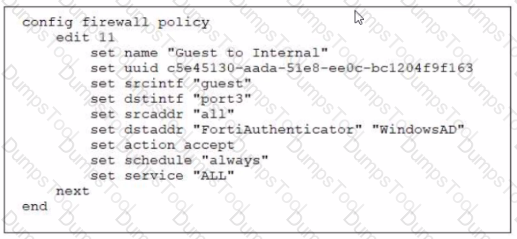
Examine the firewall policy configuration and SSID settings
An administrator has configured a guest wireless network on FortiGate using the external captive portal The administrator has verified that the external captive portal URL is correct However wireless users are not able to see the captive portal login page
Given the configuration shown in the exhibit and the SSID settings which configuration change should the administrator make to fix the problem?
Exhibit.
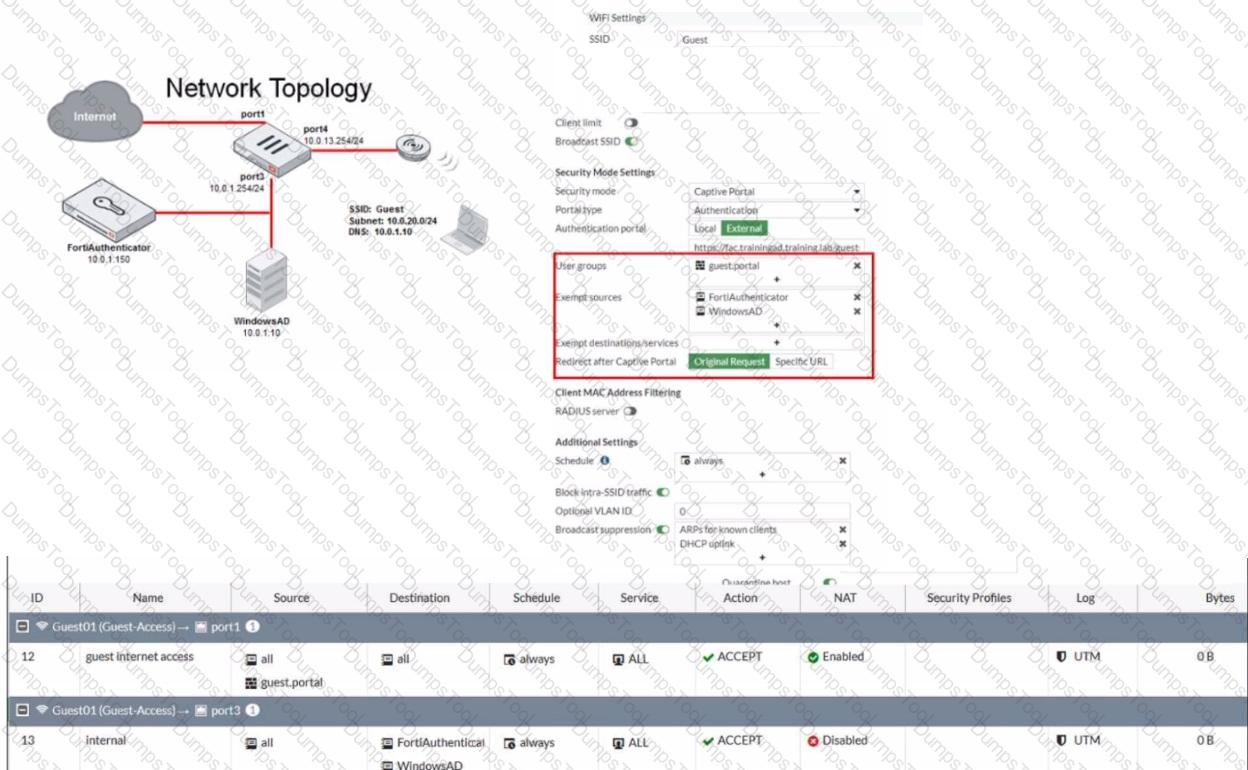
Refer to the exhibit showing a network topology and SSID settings.
FortiGate is configured to use an external captive portal However wireless users are not able to see the captive portal login page
Which configuration change should the administrator make to fix the problem?
An administrator has configured an SSID in bridge mode for corporate employees All APs are online and provisioned using default AP profiles Employees are unable to locate the SSID to conned
Which two configurations can the administrator verify? (Choose two)
Which CLI command should an administrator use on FortiGate to view the RSSO authentication process in real time?
An administrator is testing the connectivity for a new VLAN The devices in the VLAN are connected to a FortiSwitch device that is managed by FortiGate Quarantine is disabled on FortiGate
While testing the administrator noticed that devices can ping FortiGate and FortiGate can ping the devices The administrator also noticed that inter-VLAN communication works However intra-VLAN communication does not work
Which scenario is likely to cause this issue?
Which two statements about MAC address quarantine by redirect mode are true? (Choose two)
Refer to the exhibits
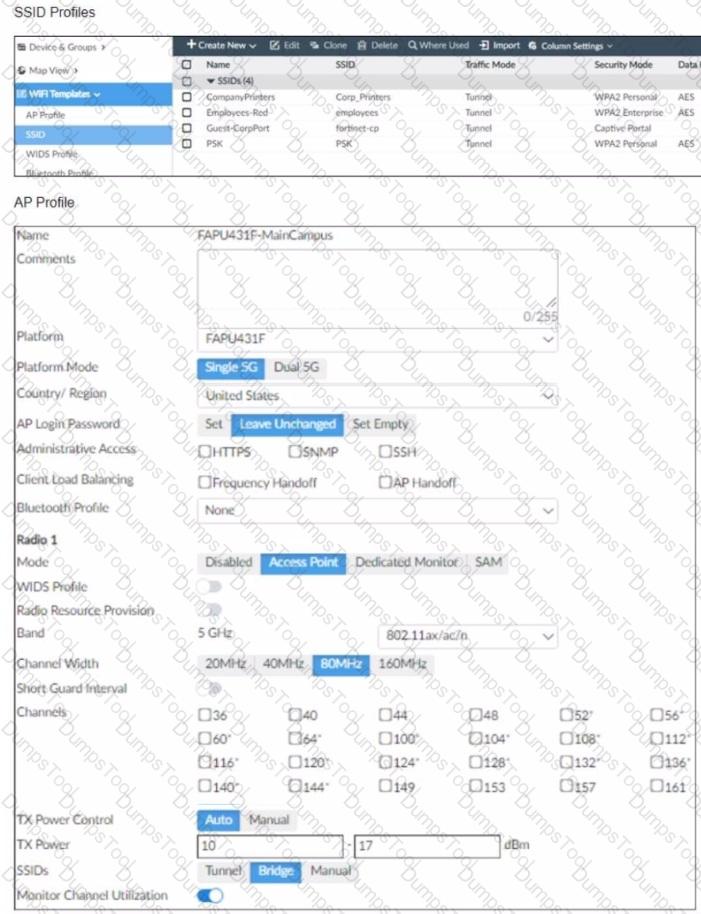
The exhibits show the wireless network (VAP) SSID profiles defined on FortiManager and an AP profile assigned to a group of APs that are supported by FortiGate
None of the APs are broadcasting the SSlDs defined by the AP profile
Which changes do you need to make to enable the SSIDs to broadcast?
Refer to the exhibit.
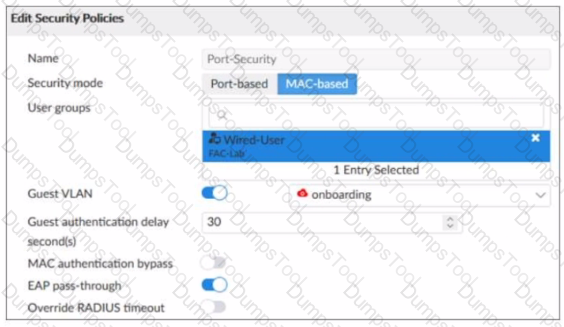
Examine the FortiSwitch security policy shown in the exhibit
If the security profile shown in the exhibit is assigned to all ports on a FortiSwitch device for 802 1X authentication which statement about the switch is correct?
Refer to the exhibit
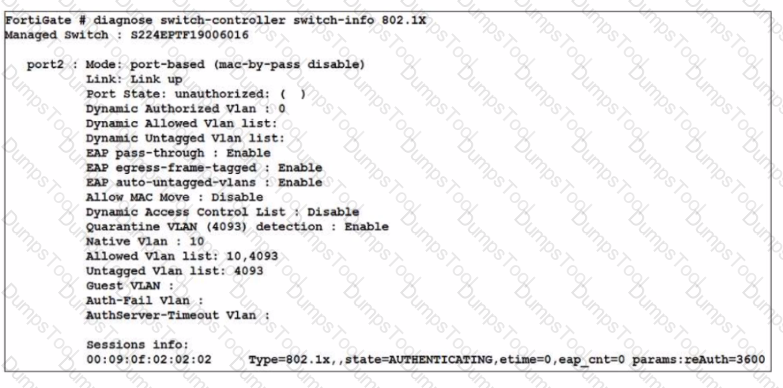
A device connected to port2 on FortiSwitch cannot access the network The port is assigned a security policy to enforce 802 1X authentication While troubleshooting the issue, the administrator obtains the debug output shown in the exhibit
Which two scenarios are likely to cause this issue? (Choose two.)
Refer to the exhibits.
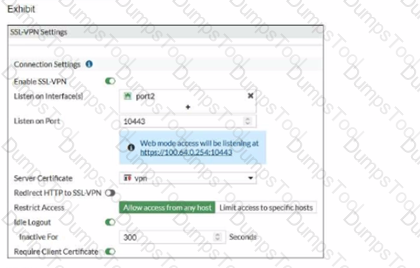
Examine the debug output and the SSL VPN configuration shown in the exhibits.
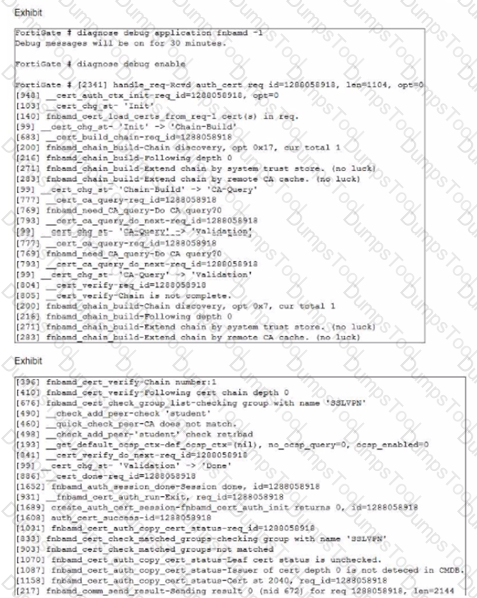
An administrator has configured SSL VPN on FortiGate. To improve security, the administrator enabled Required Client Certificate on the SSL VPN configuration page. However, a user is unable to successfully authenticate to SSL VPN.
Which configuration change should the administrator make to fix the problem?
Refer to the exhibit.
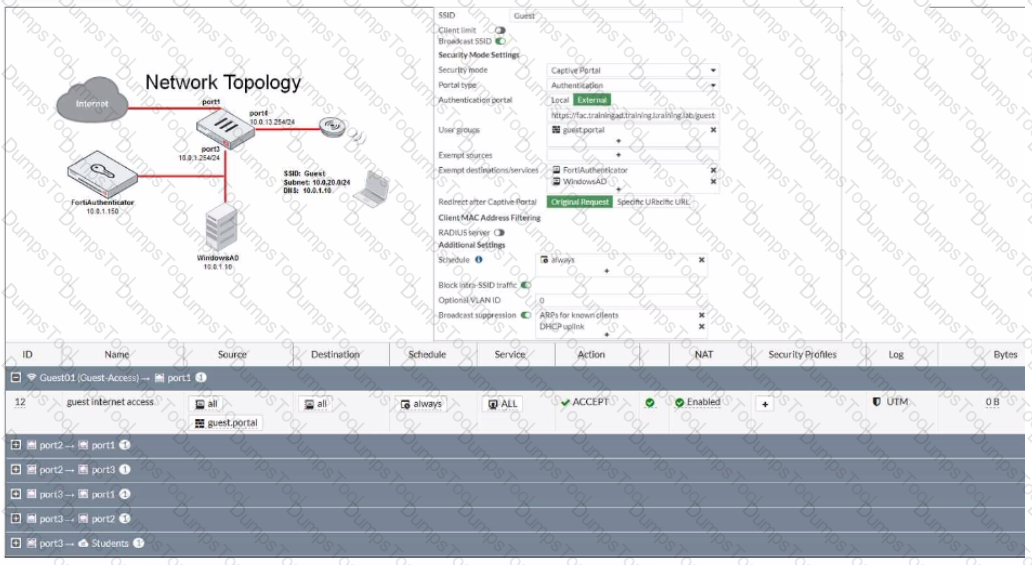
The exhibit shows a network topology and SSID settings. FortiGate is configured to use an external captive portal.
However, wireless users are not able to see the captive portal login page.
Which configuration change should the administrator make to fix the problem?