An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.
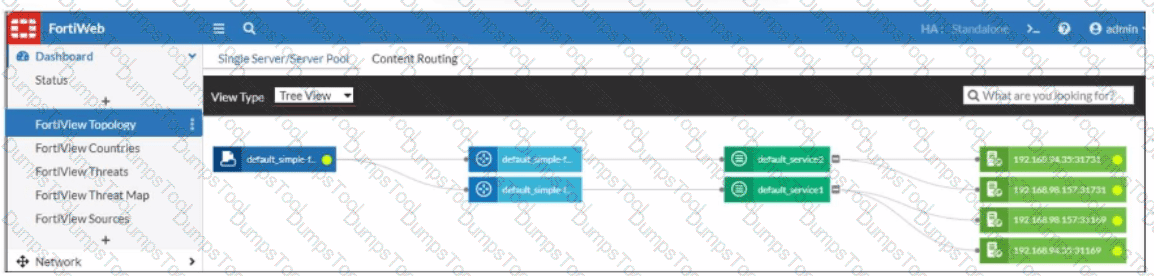
What can you conclude about the topology shown in FortiView?
An administrator is relying on an Azure Bicep linter to find possible issues in Bicep files.
Which problem can the administrator expect to find?
Refer to the exhibit.
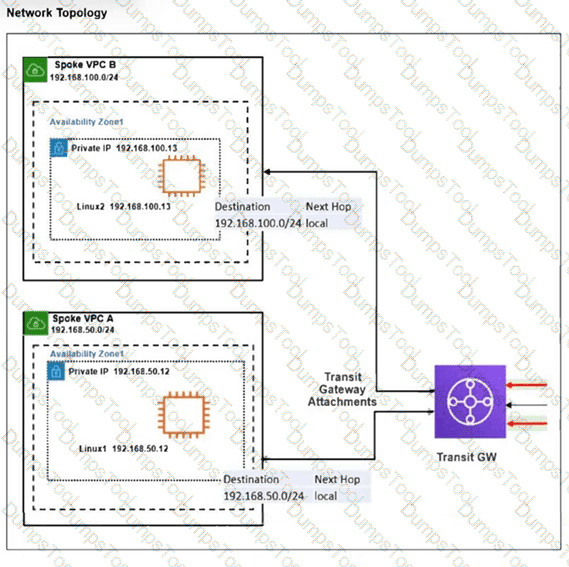
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments. Which two steps are required to route traffic from Linux instances to the TGW? (Choose two answers)
Exhibit.

In which type of FortiCNP insights can an administrator examine the findings triggered by this policy?
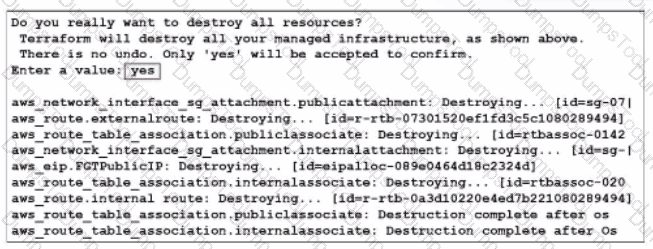
What would be the impact of confirming to delete all the resources in Terraform?
You have deployed a FortiGate HA cluster in Azure using a gateway load balancer for traffic inspection. However, traffic is not being routed correctly through the firewalls.
What can be the cause of the issue?
Refer to the exhibit.
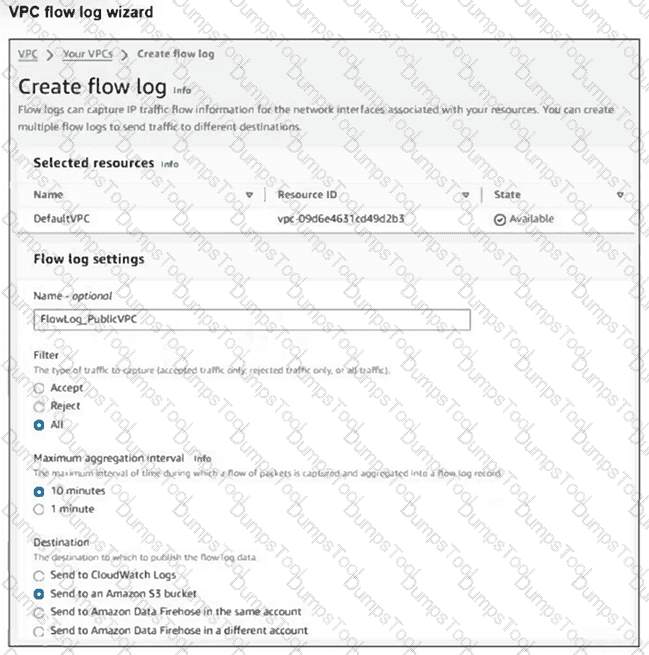
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)
Refer to the exhibit.
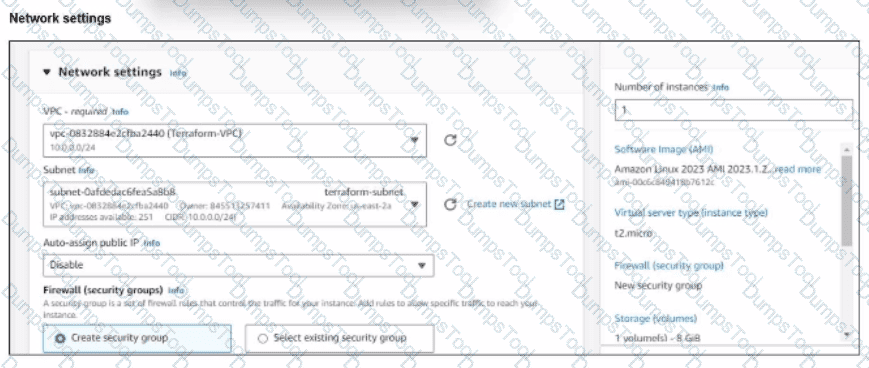
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit.
What next step must the administrator take to access this instance from the internet?
Refer to the exhibit.
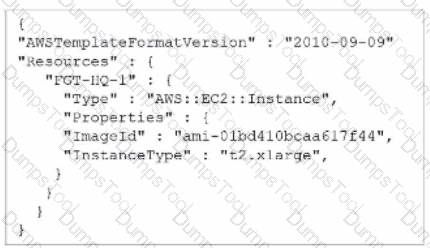
A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the Amazon Machine Image (AMI) ID to one that is valid in their location.
How can the administrator add the required comment in that section of the file?
Refer to the exhibit.
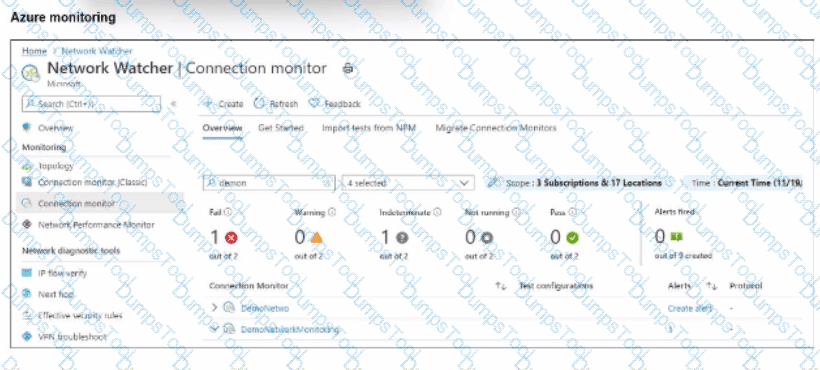
After analyzing the native monitoring tools available in Azure, an administrator decides to use the tool displayed in the exhibit.
Why would an administrator choose this tool?
A customer would like to use FortiGate fabric integration with FortiCNP. When adding a FortiGate VM to FortiCNP, which three mandatory configuration steps must you follow on FortiGate? (Choose three answers)