Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
Refer to the exhibit.
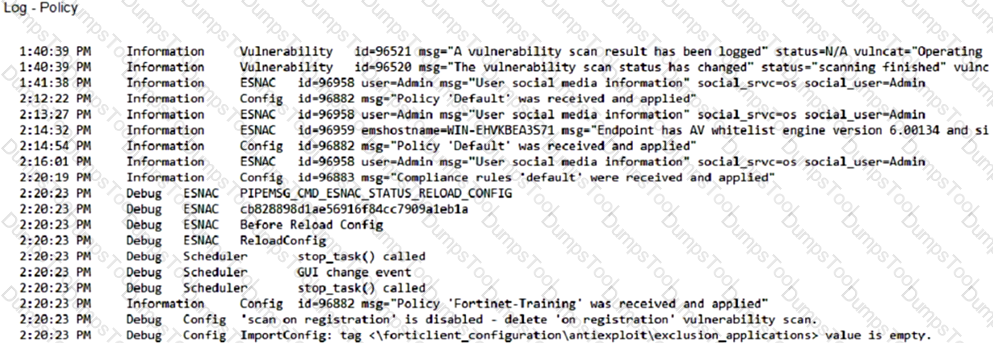
Based on the FortiClient logs shown in the exhibit which endpoint profile policy is currently applied to the FortiClient endpoint from the EMS server?
Refer to the exhibit.
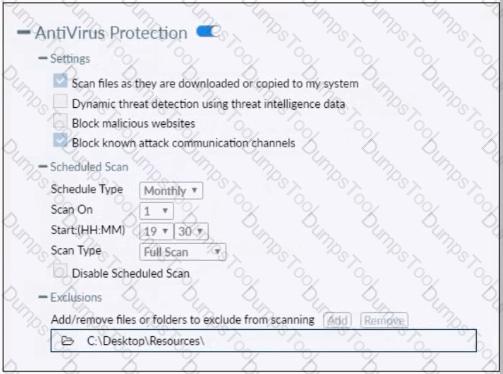
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
Which three types of antivirus scans are available on FortiClient? (Choose three )
Refer to the exhibit.
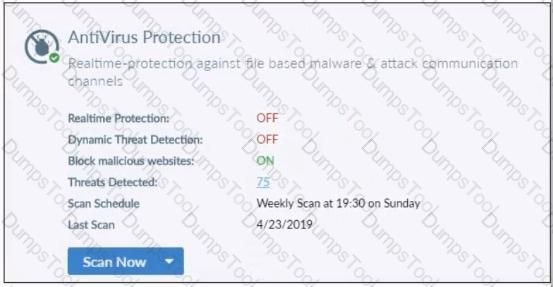
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
An administrator installs FortiClient EMS in the enterprise.
Which component is responsible for enforcing protection and checking security posture?
An administrator configures ZTNA configuration on the FortiGate for remote users. Which statement is true about the firewall policy?
Refer to the exhibit.
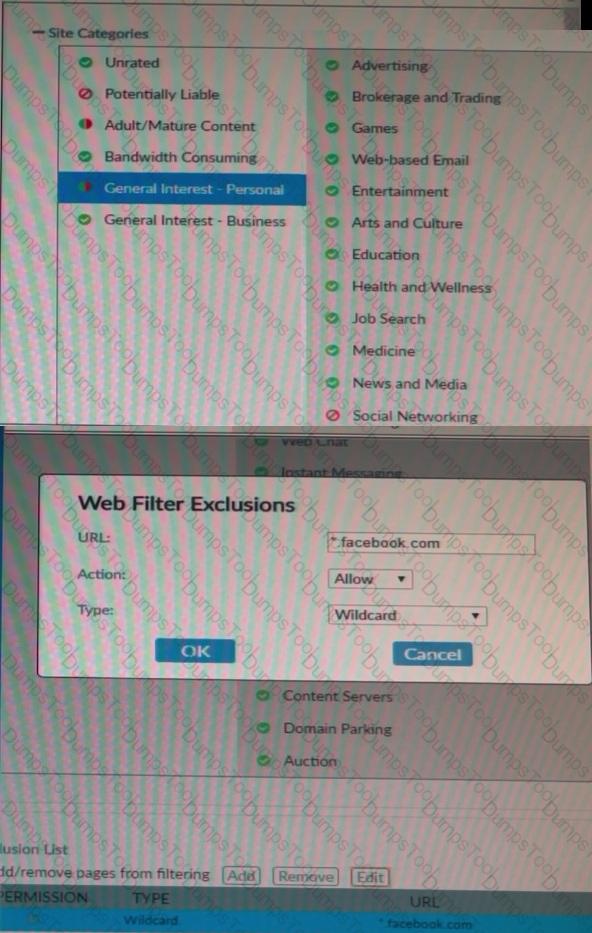
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www.facebook.com ?