Refer to the exhibit, which shows one way communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.
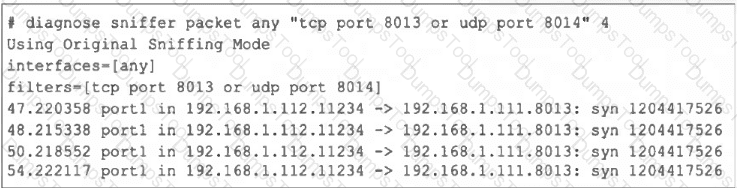
What three actions must you take to ensure successful communication? (Choose three.)
Refer to the exhibit, which shows a partial output from the get router info routing-table database command.
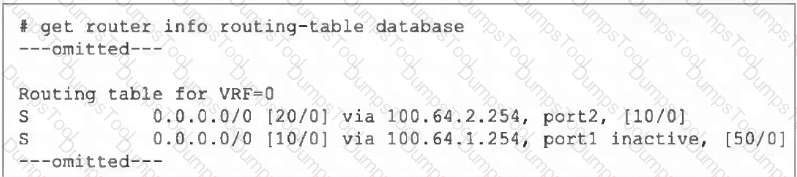
The administrator wants to configure a default static route for port3 and assign a distance of 50 and a priority of 0.
What will happen to the port1 and port2 default static routes after the port3 default static route is created?
Refer to the exhibit, which shows the partial output of FortiOS kernel slabs.
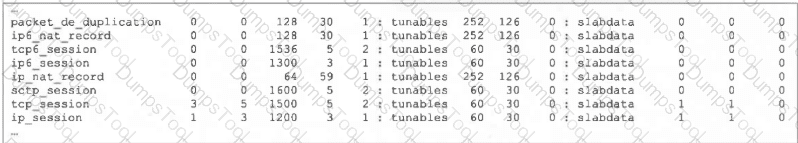
Which statement is true?
Exhibit.
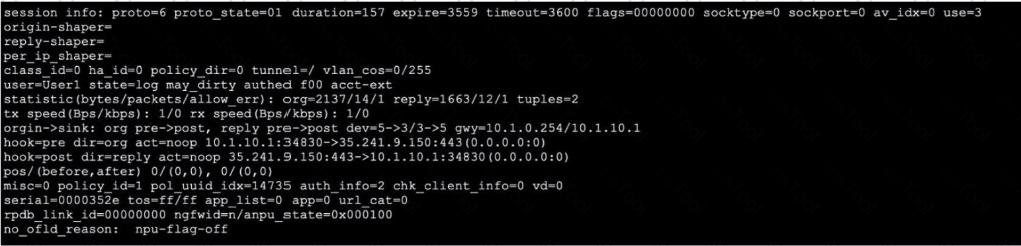
Refer to the exhibit, which shows the output of a session. Which two statements are true? (Choose Iwo.)
Exhibit.
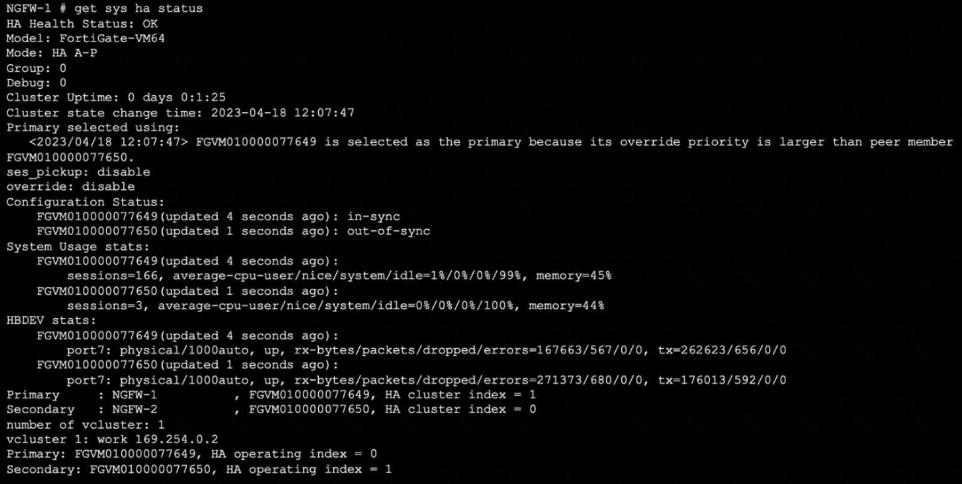
Refer to the exhibit, which shows the output of get system ha status.
NGFW-1 and NGFW-2 have been up for a week.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit, which contains the output of diagnose vpn tunnel list.
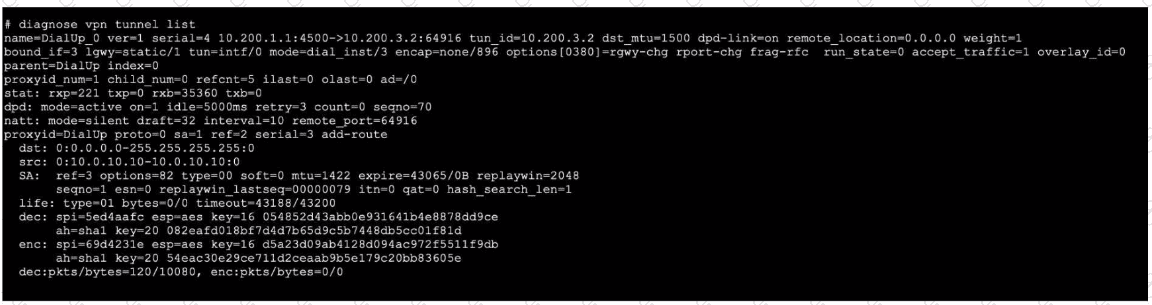
Which command will capture ESP traffic for the VPN named DialUp_0?
In the SAML negotiation process, which section does the Identity Provider (IdP) provide the SAML attributes utilized in the authentication process to the Service Provider (SP)?
Exhibit.

Refer to the exhibit, which shows two entries that were generated in the FSSO collector agent logs.
What three conclusions can you draw from these log entries? {Choose three.)
Refer to the exhibit, which shows the output of the command get router info bgp neighbors 100.64.2.254 advertised-routes.
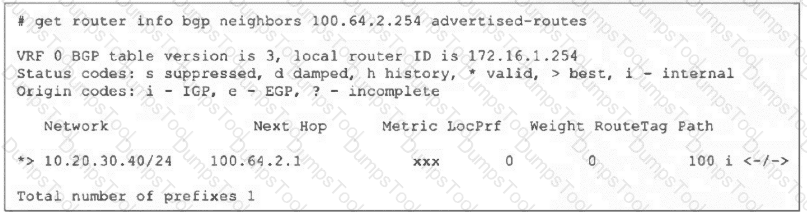
What can you conclude from the output?
Refer to the exhibit, which shows the output of diagnose sys session list.
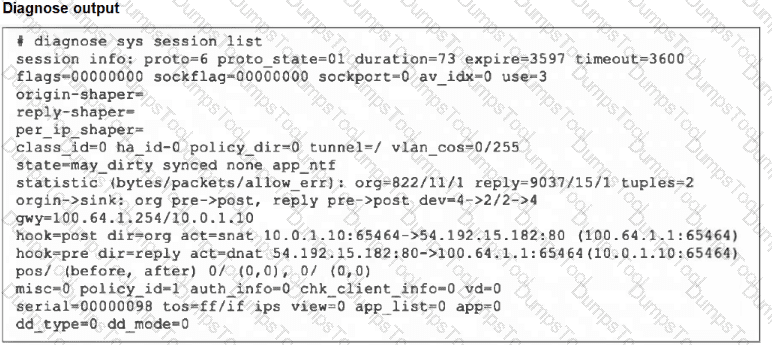
If the HA ID for the primary device is 0, what happens if the primary fails and the secondary becomes the primary?
Exhibit.
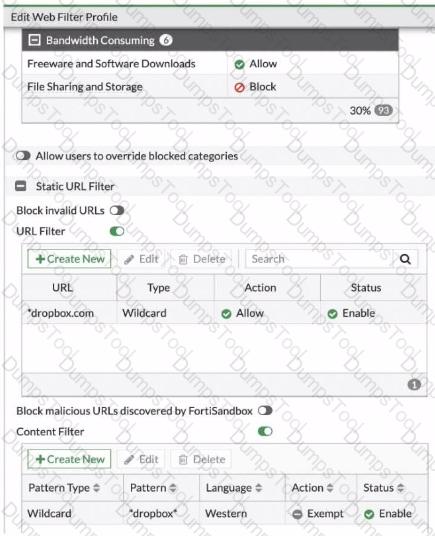
Refer to the exhibit, which shows a partial web fillet profile configuration.
Which action does FortiGate lake if a user attempts to access www. dropbox. com, which is categorized as File Sharing and Storage?
Refer to the exhibit, which shows a session entry.
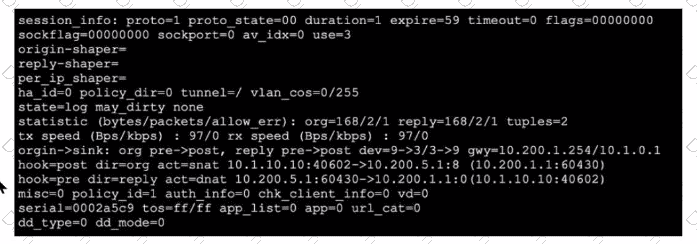
Which statement about this session is true?