A consultant has been hired by the V.P. of a large financial organization to assess the company's security posture. During the security testing, the consultant comes across child pornography on the V.P.'s computer. What is the consultant's obligation to the financial organization?
Which of the following is a primary service of the U.S. Computer Security Incident Response Team (CSIRT)?
Which of the following resources does NMAP need to be used as a basic vulnerability scanner covering several vectors like SMB, HTTP and FTP?
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
While performing data validation of web content, a security technician is required to restrict malicious input. Which of the following processes is an efficient way of restricting malicious input?
A security consultant is trying to bid on a large contract that involves penetration testing and reporting. The company accepting bids wants proof of work so the consultant prints out several audits that have been performed. Which of the following is likely to occur as a result?
A recently hired network security associate at a local bank was given the responsibility to perform daily scans of the internal network to look for unauthorized devices. The employee decides to write a script that will scan the network for unauthorized devices every morning at 5:00 am.
Which of the following programming languages would most likely be used?
Which of the following is an advantage of utilizing security testing methodologies to conduct a security audit?
The Open Web Application Security Project (OWASP) testing methodology addresses the need to secure web applications by providing which one of the following services?
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
Which of the following cryptography attack methods is usually performed without the use of a computer?
A network administrator received an administrative alert at 3:00 a.m. from the intrusion detection system. The alert was generated because a large number of packets were coming into the network over ports 20 and 21. During analysis, there were no signs of attack on the FTP servers. How should the administrator classify this situation?
Which type of scan measures a person's external features through a digital video camera?
A hacker is attempting to see which IP addresses are currently active on a network. Which NMAP switch would the hacker use?
A hacker is attempting to see which ports have been left open on a network. Which NMAP switch would the hacker use?
Which of the following does proper basic configuration of snort as a network intrusion detection system require?
Which command line switch would be used in NMAP to perform operating system detection?
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
When using Wireshark to acquire packet capture on a network, which device would enable the capture of all traffic on the wire?
On a Linux device, which of the following commands will start the Nessus client in the background so that the Nessus server can be configured?
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
A Certificate Authority (CA) generates a key pair that will be used for encryption and decryption of email. The integrity of the encrypted email is dependent on the security of which of the following?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
Which of the following tools would be the best choice for achieving compliance with PCI Requirement 11?
Which of the following ensures that updates to policies, procedures, and configurations are made in a controlled and documented fashion?
A hacker was able to sniff packets on a company's wireless network. The following information was discovered:
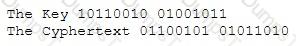
Using the Exlcusive OR, what was the original message?
During a penetration test, a tester finds that the web application being analyzed is vulnerable to Cross Site Scripting (XSS). Which of the following conditions must be met to exploit this vulnerability?
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
In order to show improvement of security over time, what must be developed?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
Passive reconnaissance involves collecting information through which of the following?
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
An NMAP scan of a server shows port 69 is open. What risk could this pose?
Which of the following is considered an acceptable option when managing a risk?
A network security administrator is worried about potential man-in-the-middle attacks when users access a corporate web site from their workstations. Which of the following is the best remediation against this type of attack?
Advanced encryption standard is an algorithm used for which of the following?
While testing the company's web applications, a tester attempts to insert the following test script into the search area on the company's web site:
Afterwards, when the tester presses the search button, a pop-up box appears on the screen with the text: "Testing Testing Testing". Which vulnerability has been detected in the web application?
Which of the following defines the role of a root Certificate Authority (CA) in a Public Key Infrastructure (PKI)?
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on his cell phone as an authorized employee badges in. Jimmy, while still on the phone, grabs the door as it begins to close.
What just happened?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
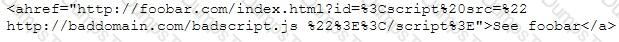
What is this attack?
Which of the following describes the characteristics of a Boot Sector Virus?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
Which of the following programs is usually targeted at Microsoft Office products?
Which of the following is an application that requires a host application for replication?
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
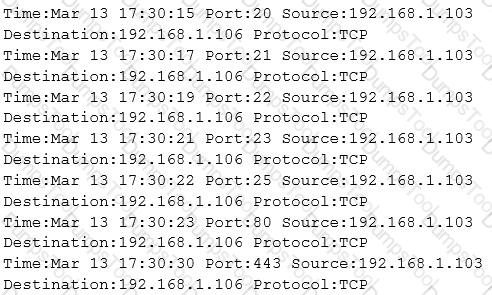
What type of activity has been logged?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
What is the correct PCAP filter to capture all TCP traffic going to or from host 192.168.0.125 on port 25?
When does the Payment Card Industry Data Security Standard (PCI-DSS) require organizations to perform external and internal penetration testing?