You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
As long as you are a member of the Vault Admins group you can grant any permission on any safe.
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
Which file must be edited on the Vault to configure it to send data to PTA?
Your organization has a requirement to allow users to “check out passwords” and connect to targets with the same account through the PSM.
What needs to be configured in the Master policy to ensure this will happen?
If PTA is integrated with a supported SIEM solution, which detection becomes available?
You have been asked to secure a set of shared accounts in CyberArk whose passwords will need to be used by end users. The account owner wants to be able to track who was using an account at any given moment.
Which security configuration should you recommend?
A newly created platform allows users to access a Linux endpoint. When users click to connect, nothing happens.
Which piece of the platform is missing?
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
According to CyberArk, which issues most commonly cause installed components to display as disconnected in the System Health Dashboard? (Choose two.)
What are the mandatory fields when onboarding from Pending Accounts? (Choose two.)
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
A Vault administrator have associated a logon account to one of their Unix root accounts in the vault. When attempting to verify the root account’s password the Central Policy Manager (CPM) will:
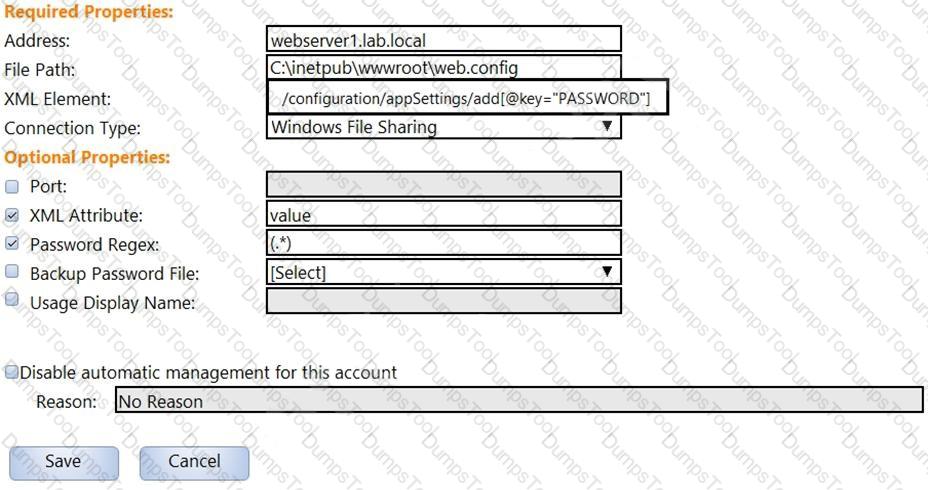
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
How much disk space do you need on a server to run a full replication with PAReplicate?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
Which combination of Safe member permissions will allow end users to log in to a remote machine transparently but NOT show or copy the password?
You created a new platform by duplicating the out-of-box Linux through the SSH platform.
Without any change, which Text Recorder Type(s) will the new platform support? (Choose two.)
For a safe with Object Level Access enabled you can turn off Object Level Access Control when it no longer needed on the safe.
Which Automatic Remediation is configurable for a PTA detection of a “Suspected Credential Theft”?
As long as you are a member of the Vault Admins group, you can grant any permission on any safe that you have access to.
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
You created a new safe and need to ensure the user group cannot see the password, but can connect through the PSM.
Which safe permissions must you grant to the group? (Choose two.)
A password compliance audit found:
1) One-time password access of 20 domain accounts that are members of Domain Admins group in Active Directory are not being enforced.
2) All the sessions of connecting to domain controllers are not being recorded by CyberArk PSM.
What should you do to address these findings?
Which dependent accounts does the CPM support out-of-the-box? (Choose three.)
Which of the following statements are NOT true when enabling PSM recording for a target Windows server? (Choose all that apply)
Which option in the Private Ark client is used to update users’ Vault group memberships?
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
To enable the Automatic response “Add to Pending” within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
In accordance with best practice, SSH access is denied for root accounts on UNIX/LINUX system. What is the BEST way to allow CPM to manage root accounts.
Which statement about the Master Policy best describes the differences between one-time password and exclusive access functionality?
All of your Unix root passwords are stored in the safe UnixRoot. Dual control is enabled for some of the accounts in that safe. The members of the AD group UnixAdmins need to be able to use the show, copy, and connect buttons on those passwords at any time without confirmation. The members of the AD group Operations Staff need to be able to use the show, copy and connect buttons on those passwords on an emergency basis, but only with the approval of a member of Operations Managers never need to be able to use the show, copy or connect buttons themselves.
Which safe permission do you need to grant Operations Staff? Check all that apply.
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account.
How should this be configured to allow for password management using least privilege?
A new HTML5 Gateway has been deployed in your organization.
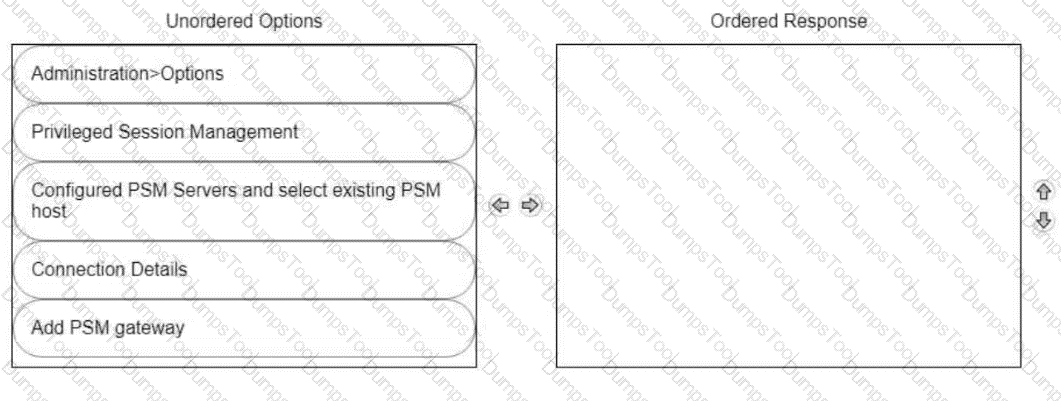
From the PVWA, arrange the steps to configure a PSM host to use the HTML5 Gateway in the correct sequence.
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
Which certificate type do you need to configure the vault for LDAP over SSL?
What are the minimum permissions to add multiple accounts from a file when using PVWA bulk-upload? (Choose three.)
You have been asked to create an account group and assign three accounts which belong to a cluster. When you try to create a new group, you receive an unauthorized error; however, you are able to edit other aspects of the account properties.
Which safe permission do you need to manage account groups?
Which authorizations are required in a recording safe to allow a group to view recordings?
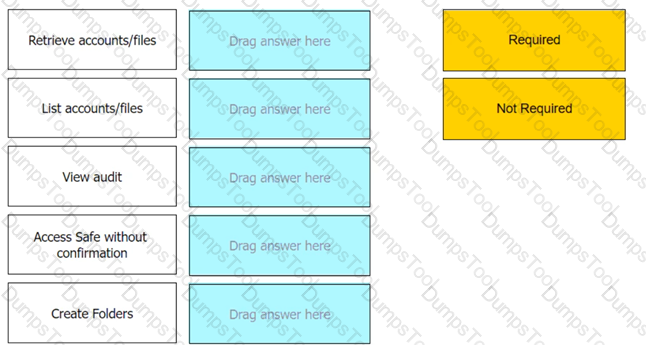
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
You receive this error:
“Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.”
Which root cause should you investigate?
When an account is unable to change its own password, how can you ensure that password reset with the reconcile account is performed each time instead of a change?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
You have been asked to turn off the time access restrictions for a safe.
Where is this setting found?
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
When onboarding multiple accounts from the Pending Accounts list, which associated setting must be the same across the selected accounts?