A customer wants to buy a new laptop with a 2.5Gbps processor. Which of the following best describes the device the salesperson should suggest?
Multiple users need to access the same data simultaneously. Which of the following is the best place to store the data?
Which of the following internet service types is most susceptible to weather disruptions?
Which of the following would MOST likely prevent malware sent as compromised file via email from infecting a person’s computer?
A company is concerned with ensuring its databases are highly available. Which of the following can be used to
increase database availability?
Which of the following is a wireless communication that requires devices to be within 6in of each other to
transfer information?
A database administrator has created a primary table and must ensure the date column in the table only accepts date values. Which of the following does the administrator need to set?
Which of the following data types would be best for storing data representing a phone number?
Salespeople roam around a retail store conducting transactions. Which of the following computing devices would be most ideal for point-of-sale transactions?
Which of the following commands would most likely be used to add data to an existing database table?
Which of the following wireless communication technologies requires devices to be within 6in (15.24cm) from each other?
A programmer creates an object to retrieve customer names from a database. Which of the following best describes the object that is retrieving the names?
Which of the following WiFi security options would create the MOST need for a VPN connection on the client
device?
A network administrator requires that a non-magnetic drive be used to store critical data for a project. The project is expected to last a few years. Which of the following would the administrator most likely choose for the project?
A user wants to use a laptop outside the house and still remain connected to the Internet. Which of the
following would be the BEST choice to accomplish this task?
Which of the following database concepts would MOST likely use a CSV file?
A network technician is installing an RJ11 connector inside a home tor new internet service. Which ot the following network connection types is the technician most likely using?
Which of the following programming languages would most likely include tables and the select command?
Which of the following interfaces is best for viewing database performance information?
Which of the following filesystems is compatible with the greatest number of operating systems?
A user connects a wireless router to a home network and notices another wireless access point uses the same name. Which of the following should the user change?
Which of the following internal computing components is typically tasked with handling complex mathematical calculations required for realistic in-game physics?
A user is attempting to print a document to a wireless printer and receives an error stating the operation could not be completed. Which of the following should the user do to correct this issue?
During a meeting, managers spoke of several instances in which confidential information appeared on inappropriate websites. The company also discovered its firewall did not filter out certain traffic to prevent such issues. Which of the following most likely exposed the confidential information?
Which of the following types of encryptions would BEST protect a laptop computer in the event of theft?
After creating a database, which of the following would a developer most likely use to put data in the database?
A technician is investigating the who, what, when, where, and why of an issue. Which of the following steps of the troubleshooting methodology is the technician currently at?
Concerned with vulnerabilities on a home network, an administrator replaces the wireless router with a recently
released new device. After configuring the new device utilizing the old SSID and key, some light switches are
no longer communicating. Which of the following is the MOST likely cause?
Which of the following software solutions ensures that programs running simultaneously on a workstation do not utilize the same physical memory?
A programmer needs to store output in a place that can be accessed as quickly as possible. The data does not need to remain persistent. Which of the following is the BEST option for storing the data?
Which of the following is an example of utilizing a personalized code for continuous personal access to a software product?
Which of the following software license models allows a developer to modify the original code and release its own version of the application?
Which of the following should a technician do to fix stability issues on a workstation?
A technician has been asked to assign an IP address to a new desktop computer. Which of the following is a valid IP address the technician should assign?
Which of the following storage types is MOST vulnerable to magnetic damage?
Malware infections are being caused by websites. Which of the following settings will help prevent infections caused by Internet browsing?
A programmer needs to specify how to store a test score entered using a web form. Which of the following would be best to use?
Which of the following business continuity concepts is the best example of fault tolerance?
Which of the following backup types is most likely to allow restoration of a fully bootable computer on new hardware?
Which of the following is a characteristic of both a database and a flat file?
A company wants to build an application that is available to employees without a client component because some employees do not connect to the corporate network in order to work. Which of the following network types would best deliver this application to all employees?
A building has two legacy APs. A new AP was recently installed within 30ft (9m) of the legacy APs. Multiple users have been reporting intermittent internet connectivity since the new AP was installed. Which of the following explains what is happening?
A user installs a wireless router and opens a browser to modify the settings. Which of the following installation types does this describe?
Which of the following is considered a traditional input and output device?
A technician is concerned that sensitive data transmitted over the Internet can be intercepted and viewed during
a MITM attack. Which of the following should the technician enable to reduce the risk?
A programmer is generating results by iterating rows that provide values needed for one calculation. Which of the following functions best accomplishes this task?
In an effort to reduce costs, a company decides not to renew its contract for a secure shredding service. Which of the following risks should the management team most likely be concerned with if employees fail to properly dispose of documents according to security protocols?
Which of the following storage types presents the most likely security risk?
A flatbed scanner that is connected to a laptop is used to convert photographic prints to digital images for reproduction on a color printer. Which of the following is considered the input device for this process?
Given the following pseudocode:
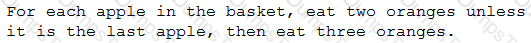
If there are seven apples in the basket, which of the following would be the number of oranges a person eats?
A programmer chooses a database for a new application that needs to store information, including dates, times, names, and amounts. Which of the following database features is this an example of?
A customer is looking for a device that uses tap to pay when making purchases. Which of the following technologies should the customer use?
Which of the following describes the ability to recover access to a specific account if a credential is forgotten?
Which of the following should privacy expectations on a company intranet be limited to?
Given the following pseudocode:
If the Breakfast program ran on Sunday, which of the following would be the output?
Which of the following is most appropriate to list on a social media site about an employer?
Which of the following availability concerns is mitigated by having a business continuity site?
A company allows employees to use their own devices for work. Which of the following is the best security method for such devices?
An accounting firm needs to allow users to update records simultaneously without errors. Which of the following best meets the firm's needs?
An IT manager wants to prevent end users from booting alternative operating systems on workstations. Which of the following security-related best practices would be used to accomplish this?
A systems administrator wants to return results for a time range within a database. Which of the following
commands should the administrator use?
Employees of a large technology company are provided access to the internet as a work resource. Which of the following most likely represents the level of privacy employees should expect when utilizing this resource?
Which of the following is the least expensive way for users at a large company to load a 2GB spreadsheet quickly?
A product advertising kiosk at a mall is set up using a thin client without a hard drive and is running a web application managed and updated through an internet connection. Which of the following application delivery methods is most likely being used for the kiosk?
A technician has successfully verified full system functionality after implementing the solution to a problem.
Which of the following is the NEXT troubleshooting step the technician should do?
On which of the following distinct numbers of digits is the hexadecimal numbering system based?
Which of the following is MOST likely used to represent international text data?
A programmer is tasked with providing a human-readable rough draft of output. Which of the following techniques would be used?
A user wants to prevent web history logging. Which of the following features will allow the user to achieve this goal?
A user is trying to set up a new wireless access point. Which of the following should the user do first?
Which of the following best practices can be used to mitigate password reuse?
A new device has been installed on a wired network and can be accessed via the LAN but cannot be accessed remotely.
Which of the following is the most likely cause?
Which of the following operating systems do not require extensions on files to execute a program? (Select
TWO).
A small company wants to set up a server that is accessible from the company network as well as the Internet.
Which of the following is MOST important to determine before allowing employees to access the server
remotely?
A technician is installing an MFD. After installation, all functions work except faxing. Which of the following interfaces is required to enable faxing functionality?
A global variable called “age” will be created in a program and incremented through the use of a function.
Which of the following data types should be defined with the age variable?
A small company has authorized an allowance for employees to purchase their own work computers. The administrator has noticed a sizable increase in network traffic following the arrival of the new computers. Which of the following is the most likely reason?