A security incident has been created after noticing unusual behavior from a Windows domain controller. The server administrator has discovered that a user logged in to the server with elevated permissions, but the user’s account does not follow the standard corporate naming scheme. There are also several other accounts in the administrators group that do not follow this naming scheme. Which of the following is the possible cause for this behavior and the BEST remediation step?
When performing reverse engineering, which of the following file types would be MOST easily decompiled Into source code?
A company has a large number of users who need to access corporate resources or networks from various locations. Many users have VPN access to the network, as well as wireless internet access from BYOD approved systems tablets and smartphones. The users can also access corporate resources from an internal-facing web portal now ever all of these services require a separate set of credentials. Which of the following should the cybersecurity analyst recommend to aggregate and audit on logins while allowing the corporate directory services credentials to be shared across all of the services?
The development team recently moved a new application into production for the accounting department. After this occurred, the Chief Information Officer (CIO) was contacted by the head of accounting because the application is missing a key piece of functionality that is needed to complete the corporation’s quarterly tax returns. Which of the following types of testing would help prevent this from reoccurring?
After analyzing and correlating activity from multiple sensors, the security analyst has determined a group from a high-risk country is responsible for a sophisticated breach of the company network and continuous administration of targeted attacks for the past three months. Until now, the attacks went unnoticed. This is an example of:
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)
Which of the following represent the reasoning behind careful selection of the timelines and time-of-day boundaries for an authorized penetration test? (Select TWO).
A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded. Which of the following should the security analyst recommend to add additional security to this device?
A security professional is analyzing the results of a network utilization report. The report includes the following information:
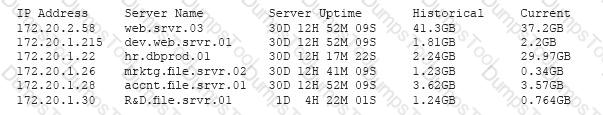
Which of the following servers needs further investigation?
A security analyst has just completed a vulnerability scan of servers that support a business critical application that is managed by an outside vendor. The results of the scan indicate the devices are missing critical patches. Which of the following factors can inhibit remediation of these vulnerabilities? (Choose two.)
A security analyst at a large financial institution is evaluating the security posture of a smaller financial company. The analyst is performing the evaluation as part of a due diligence process prior to a potential acquisition. With which of the following threats should the security analyst be MOST concerned? (Choose two.)
Which of the following is the MOST secure method to perform dynamic analysis of malware that can sense when it is in a virtual environment?
A company installed a wireless network more than a year ago, standardizing on the same model APs in a single subnet. Recently, several users have reported timeouts and connection issues with Internet browsing. The security administrator has gathered some information about the network to try to recreate the issues with the assistance of a user. The administrator is able to ping every device on the network and confirms that the network is very slow.
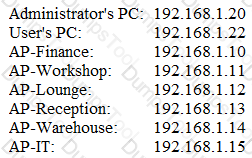
Output:
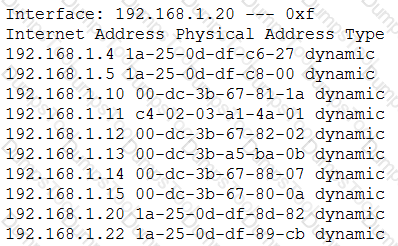
Given the above results, which of the following should the administrator investigate FIRST?
A cybersecurity analyst is investigating an incident report concerning a specific user workstation. The workstation is exhibiting high CPU and memory usage, even when first started, and network bandwidth usage is extremely high. The user reports that applications crash frequently, despite the fact that no significant changes in work habits have occurred. An antivirus scan reports no known threats. Which of the following is the MOST likely reason for this?
Joe, a user, is unable to launch an application on his laptop, which he typically uses on a daily basis. Joe informs a security analyst of the issue. After an online database comparison, the security analyst checks the SIEM and notices alerts indicating certain .txt and .dll files are blocked. Which of the following tools would generate these logs?
A project lead is reviewing the statement of work for an upcoming project that is focused on identifying potential weaknesses in the organization’s internal and external network infrastructure. As part of the project, a team of external contractors will attempt to employ various attacks against the organization. The statement of work specifically addresses the utilization of an automated tool to probe network resources in an attempt to develop logical diagrams indication weaknesses in the infrastructure.
The scope of activity as described in the statement of work is an example of:
After completing a vulnerability scan, the following output was noted:
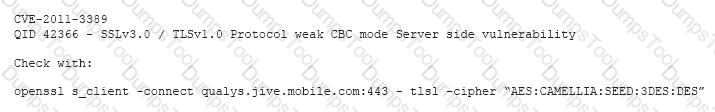
Which of the following vulnerabilities has been identified?
A security analyst is performing a forensic analysis on a machine that was the subject of some historic SIEM alerts. The analyst noticed some network connections utilizing SSL on non-common ports, copies of svchost.exe and cmd.exe in %TEMP% folder, and RDP files that had connected to external IPs. Which of the following threats has the security analyst uncovered?
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack. Which of the following would be the BEST action for the cybersecurity analyst to perform?
A cybersecurity analyst is conducting a security test to ensure that information regarding the web server is protected from disclosure. The cybersecurity analyst requested an HTML file from the web server, and the response came back as follows:
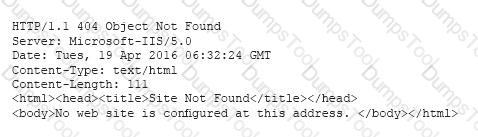
Which of the following actions should be taken to remediate this security issue?
A cybersecurity analyst has several SIEM event logs to review for possible APT activity. The analyst was given several items that include lists of indicators for both IP addresses and domains. Which of the following actions is the BEST approach for the analyst to perform?
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Select two.)
When network administrators observe an increased amount of web traffic without an increased number of financial transactions, the company is MOST likely experiencing which of the following attacks?
A security administrator determines several months after the first instance that a local privileged user has been routinely logging into a server interactively as “root” and browsing the Internet. The administrator determines this by performing an annual review of the security logs on that server. For which of the following security architecture areas should the administrator recommend review and modification? (Select TWO).
File integrity monitoring states the following files have been changed without a written request or approved change. The following change has been made:
chmod 777 –Rv /usr
Which of the following may be occurring?
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
After scanning the main company’s website with the OWASP ZAP tool, a cybersecurity analyst is reviewing the following warning:
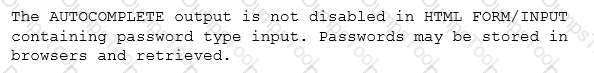
The analyst reviews a snippet of the offending code:
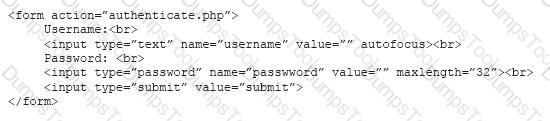
Which of the following is the BEST course of action based on the above warning and code snippet?
A database administrator contacts a security administrator to request firewall changes for a connection to a new internal application.
The security administrator notices that the new application uses a port typically monopolized by a virus.
The security administrator denies the request and suggests a new port or service be used to complete the application’s task.
Which of the following is the security administrator practicing in this example?
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis. The last completed scan of the network returned 5,682 possible vulnerabilities. The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues. Which of the following is the BEST way to proceed?
Which of the following principles describes how a security analyst should communicate during an incident?
Following a data compromise, a cybersecurity analyst noticed the following executed query:
SELECT * from Users WHERE name = rick OR 1=1
Which of the following attacks occurred, and which of the following technical security controls would BEST reduce the risk of future impact from this attack? (Select TWO).
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
A business-critical application is unable to support the requirements in the current password policy because it does not allow the use of special characters. Management does not want to accept the risk of a possible security incident due to weak password standards. Which of the following is an appropriate means to limit the risks related to the application?
An organization is experiencing degradation of critical services and availability of critical external resources. Which of the following can be used to investigate the issue?
An analyst is troubleshooting a PC that is experiencing high processor and memory consumption. Investigation reveals the following processes are running on the system:
Which of the following tools should the analyst utilize to determine the rogue process?
A security analyst is concerned that employees may attempt to exfiltrate data prior to tendering their resignations. Unfortunately, the company cannot afford to purchase a data loss prevention (DLP) system. Which of the following recommendations should the security analyst make to provide defense-in-depth against data loss? (Select THREE).
A security analyst begins to notice the CPU utilization from a sinkhole has begun to spike. Which of the following describes what may be occurring?
A threat intelligence analyst who works for a financial services firm received this report:
“There has been an effective waterhole campaign residing at www.bankfinancecompsoftware.com. This domain is delivering ransomware. This ransomware variant has been called “LockMaster” by researchers due to its ability to overwrite the MBR, but this term is not a malware signature. Please execute a defensive operation regarding this attack vector.”
The analyst ran a query and has assessed that this traffic has been seen on the network. Which of the following actions should the analyst do NEXT? (Select TWO).
A security analyst is assisting with a computer crime investigation and has been asked to secure a PC and deliver it to the forensic lab. Which of the following items would be MOST helpful to secure the PC? (Choose three.)
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After investigating the platform vulnerability, it was determined that the web services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
A cybersecurity professional wants to determine if a web server is running on a remote host with the IP address 192.168.1.100. Which of the following can be used to perform this task?
Considering confidentiality and integrity, which of the following make servers more secure than desktops? (Select THREE).
A cybersecurity analyst was asked to discover the hardware address of 30 networked assets. From a command line, which of the following tools would be used to provide ARP scanning and reflects the MOST efficient method for accomplishing the task?
The primary difference in concern between remediating identified vulnerabilities found in general-purpose IT network servers and that of SCADA systems is that:
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The security analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reactions, server functionality does not seem to be affected, and no malware was found after a scan.
Which of the following actions should the analyst take?
A company has decided to process credit card transactions directly. Which of the following would meet the requirements for scanning this type of data?
During a web application vulnerability scan, it was discovered that the application would display inappropriate data after certain key phrases were entered into a webform connected to a SQL database server. Which of the following should be used to reduce the likelihood of this type of attack returning sensitive data?
Which of the following has the GREATEST impact to the data retention policies of an organization?
A cybersecurity analyst is reviewing log data and sees the output below:
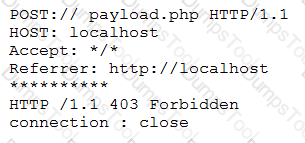
Which of the following technologies MOST likely generated this log?
An organization wants to harden its web servers. As part of this goal, leadership has directed that vulnerability scans be performed, and the security team should remediate the servers according to industry best practices. The team has already chosen a vulnerability scanner and performed the necessary scans, and now the team needs to prioritize the fixes. Which of the following would help to prioritize the vulnerabilities for remediation in accordance with industry best practices?
A systems administrator is trying to secure a critical system. The administrator has placed the system behind a firewall, enabled strong authentication, and required all administrators of this system to attend mandatory training.
Which of the following BEST describes the control being implemented?
A nuclear facility manager determined the need to monitor utilization of water within the facility. A startup company just announced a state-of-the-art solution to address the need for integrating the business and ICS network. The solution requires a very small agent to be installed on the ICS equipment. Which of the following is the MOST important security control for the manager to invest in to protect the facility?
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
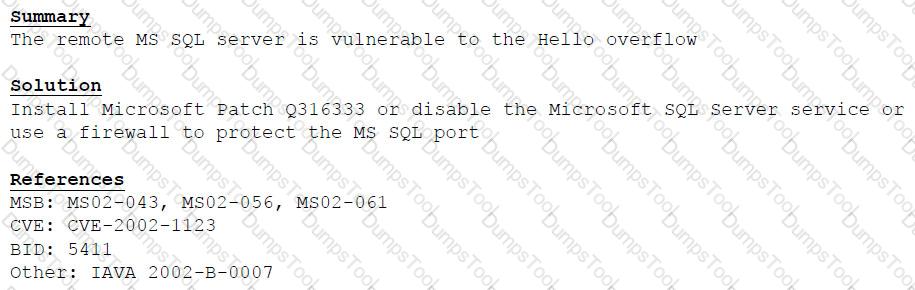
Based on the above information, which of the following should the system administrator do? (Select TWO).
Which of the following is a vulnerability that is specific to hypervisors?
A security analyst Is reviewing the most recent company scan results. Multiple Linux systems do not return any results. A comparison of the previous report, however, shows these same systems had several open vulnerabilities. Which of the following steps should the security analyst take NEXT?
A systems administrator at a company notices an unknown, randomly named process running on a database server that contains several terabytes of personal and account data for customers Reviewing the server, the administrator notices the process was installed and began running two days ago Database logs stored off the server Indicate unusual queries were run but not against tables containing personal and account data. Network logs show encrypted network traffic at minimal levels lo an external IP address that began shortly after the process started and ended at midnight yesterday wnen the threat intelligence feed automatically blocked the IP address. Which of the following is the BEST course of action'
A user received an invalid password response when trying to change the password. Which of the following policies could explain why the password is invalid?
An analyst is reviewing the following log from the company web server:
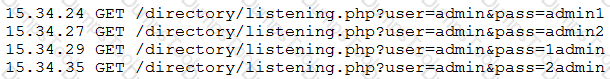
Which of the following is this an example of?
A security analyst received an email with the following key:
Xj3XJ3LLc
A second security analyst received an email with following key:
3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company’s financial segment for maintenance. This is an example of:
A security analyst is performing a routine check on the SIEM logs related to the commands used by operators and detects several suspicious entries from different users. Which of the following would require immediate attention?