A network architect is designing a new network for a rural hospital system. Given the following requirements:
Highly available
Consistent data transmission
Resilient to simultaneous failures
Which of the following topologies should the architect use?
A network administrator is configuring firewall rules to lock down the network from outside attacks. Which of the following should the administrator configure to create the most strict set of rules?
A network architect needs to design a new network to connect multiple private data centers. The network must:
Provide privacy for all traffic between locations
Use preexisting internet connections
Use intelligent steering of application traffic over the best path
Which of the following best meets these requirements?
A global company has depots in various locations. A proprietary application was deployed locally at each of the depots, but issues with getting the consolidated data instantly occurred. The Chief Information Officer decided to centralize the application and deploy it in the cloud. After the cloud deployment, users report the application is slow. Which of the following is most likely the issue?
A company hosts its applications on the cloud and is expanding its business to Europe. Thecompany must comply with General Data Protection Regulation (GDPR) to limit European customers' access to data. The network team configures the firewall rules but finds that some customers in the United States can access data hosted in Europe. Which of the following is the best option for the network team to configure?
A company is transitioning from on-premises to a hybrid environment. Due to regulatory standards, the company needs to achieve a high level of reliability and high availability for the connection between its data center and the cloud provider. Which of the following solutions best meets the requirements?
A company deployed new applications in the cloud and configured a site-to-site VPN to connect the internal data center with the cloud. The IT team wants the internal servers to connect to those applications without using public IP addresses. Which of the following is the best solution?
A cloud architect needs to change the network configuration at a company that uses GitOps to document and implement network changes. The Git repository uses main as the default branch, and the main branch is protected. Which of the following should the architect do after cloning the repository?
A company is replacing reserved public IP addresses with dynamic IP addresses. The network architect creates a list of assets with some dependencies to these reserved IPs:
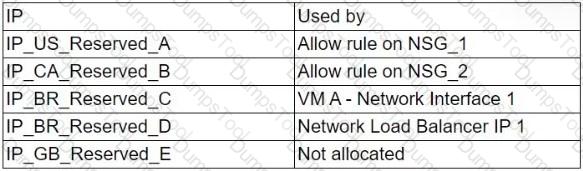
(Refer to image: Reserved IPs are in use by NSGs, VMs, load balancers, and one is unallocated.)
Which of the following issues may begin to affect cloud assets after the replacement is made?
A network engineer at an e-commerce organization must improve the following dashboard due to a performance issue on the website:
(Refer to the image: Website performance monitoring dashboard showing metrics like network usage, CPU usage, memory usage, and disk usage over time.)
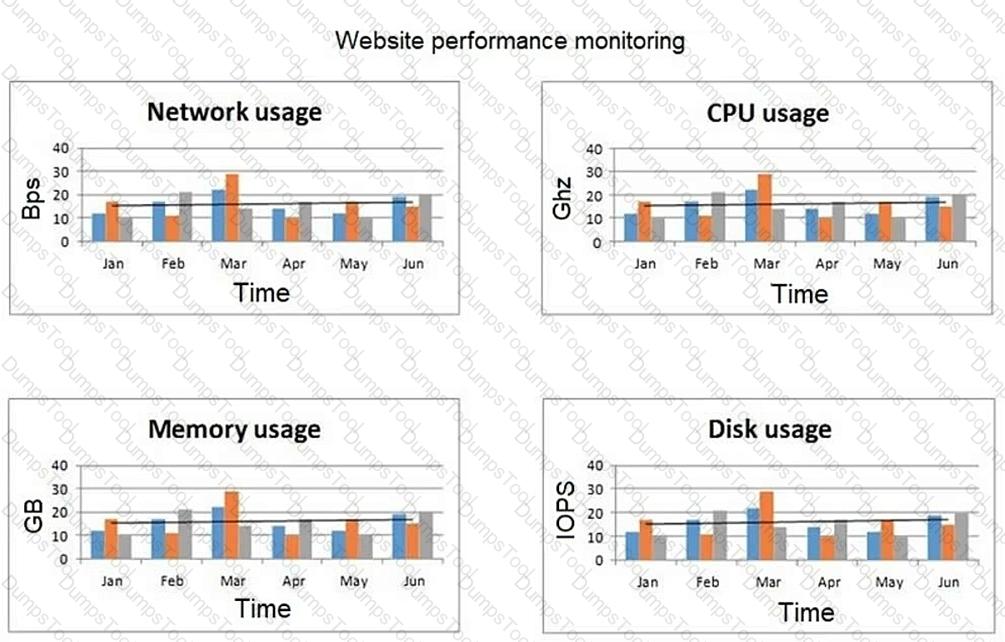
Which of the following is the most useful information to add to the dashboard for the operations team?
A network architect is choosing design options for a new SD-WAN installation that has the following requirements:
All network traffic from the cloud must pass through inspection devices in a dedicated data center.
Ensure redundancy.
Centralize egress traffic.
Which of the following network topologies best meets these requirements?
A network administrator must connect a remote building at a manufacturing plant to the main building via a wireless connection. Which of the following should the administrator choose to get the greatest possible range from the wireless connection? (Choose two.)
A company is expanding its network and needs to ensure improved stability and reliability. The proposed solution must fulfill the following requirements:
Detection and prevention of network loops
Automatic configuration of ports
Standard protocol (not proprietary)
Which of the following protocols is the most appropriate?
A call center company provides its services through a VoIP infrastructure. Recently, the call center set up an application to manage its documents on a cloud application. The application is causing recurring audio losses for VoIP callers. The network administrator needs to fix the issue with the least expensive solution. Which of the following is the best approach?
A cloud engineer is planning to build VMs in a public cloud environment for a cloud migration. A cloud security policy restricts access to the console for new VM builds. The engineer wants to replicate the settings for each of the VMs to ensure the network settings are preconfigured. Which of the following is the best deployment method?
An application is hosted on a three-node cluster in which each server has identical compute and network performance specifications. A fourth node is scheduled to be added to the cluster with three times the performance as any one of the preexisting nodes. The network architect wants to ensure that the new node gets the same approximate number of requests as all of the others combined. Which of the following load-balancing methodologies should the network architect recommend?
A network load balancer is not correctly validating a client TLS certificate. The network architect needs to validate the certificate installed on the load balancer before progressing. Which of the following commands should the architect use to confirm whether the private key and certificate match?
Server A (10.2.3.9) needs to access Server B (10.2.2.7) within the cloud environment since theyare segmented into different network sections. All external inbound traffic must be blocked to those servers. Which of the following need to be configured to appropriately secure the cloud network? (Choose two.)
A company hosts a cloud-based e-commerce application and only wants the application accessed from certain locations. The network team configures a cloud firewall with WAF enabled, but users can access the application globally. Which of the following should the network team do?
A network architect is working on a new network design to better support remote and on-campus workers. Traffic needs to be decrypted for inspection in the cloud but is not required to go through the company's data center. Which of the following technologies best meets these requirements?