Which solution should be used in a high-density wireless environment to increase bandwidth for each user?
Which method is used by an AP to join HA controllers and is configured in NVRAM?
Drag and drop the snippets onto the blanks within the code to construct a script that brings up the failover Ethernet port if the primary port goes down and also shuts down the failover port when the primary returns to service. Not all options are used.
Which method ensures the confidentiality of data exchanged over a REST API?
Which devices does Cisco DNA Center configure when deploying an IP-based access control policy?
An engineer is implementing a new SSID on a Cisco Catalyst 9800 Series WLC that must be broadcast on 6 GHz radios. Users will be required to use EAP-TLS to authenticate. Which wireless Layer 2 security method is required?
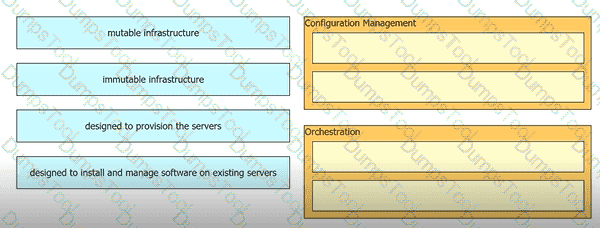
Drag and drop the characteristics from the left onto the orchestration tool classifications on the right.
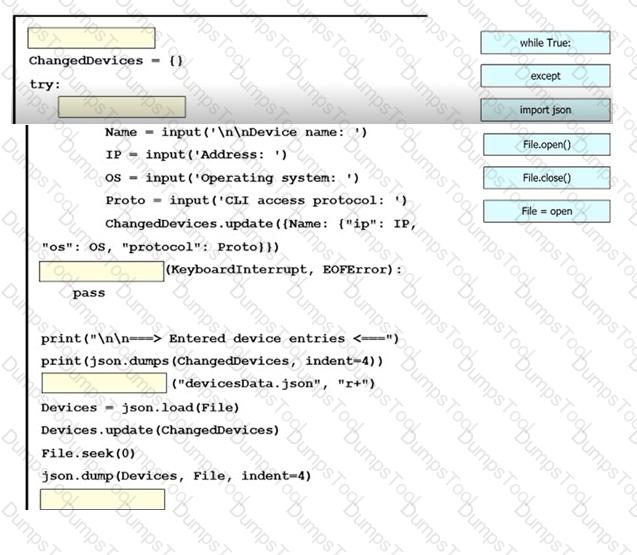
An engineer must create a script to append and modify device entries in a JSON-formatted file. The script must work as follows:
Until interrupted from the keyboard, the script reads in the hostname of a device, its management IP address, operating system type, and CLI remote access protocol.
After being interrupted, the script displays the entered entries and adds them to the JSON-formatted file, replacing existing entries whose hostname matches.
The contents of the JSON-formatted file are as follows

Drag and drop the statements onto the blanks within the code to complete the script. Not all options are used.

Refer to the exhibit. Which Python snippet stores the data structure of the device in JSON format?
When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
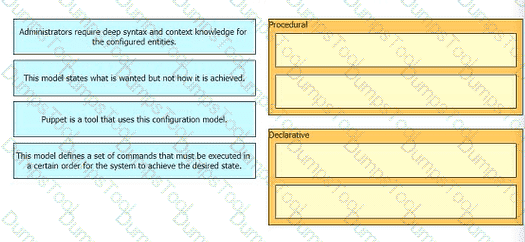
Drag anti drop the characteristics from the ten onto the configuration models on the right.
Which technology reduces the implementation of STP and leverages both unicast and multicast?
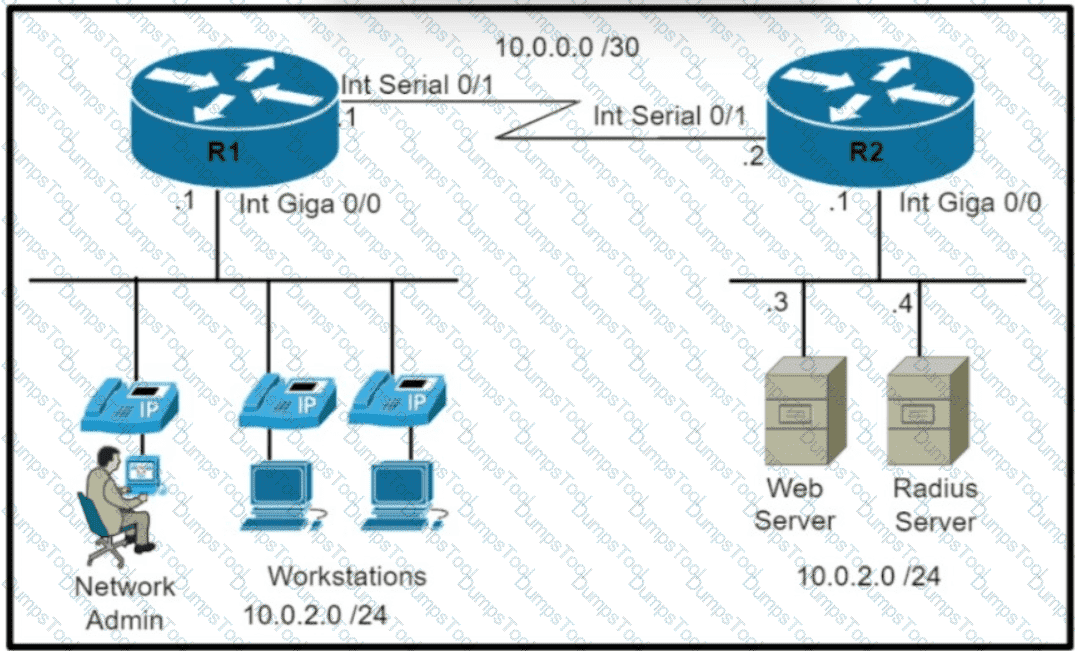
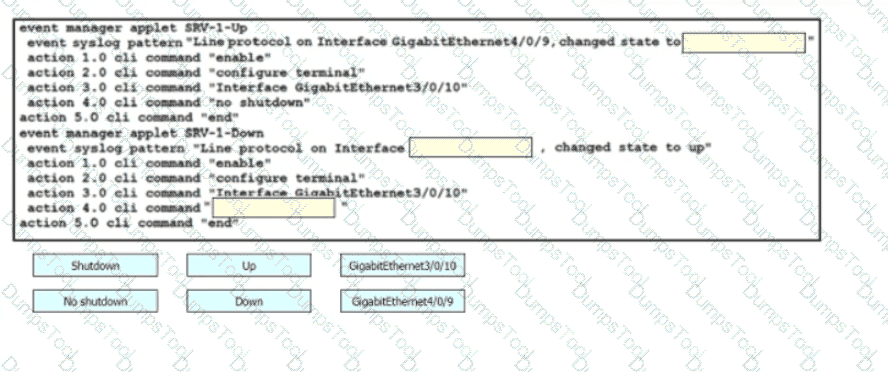
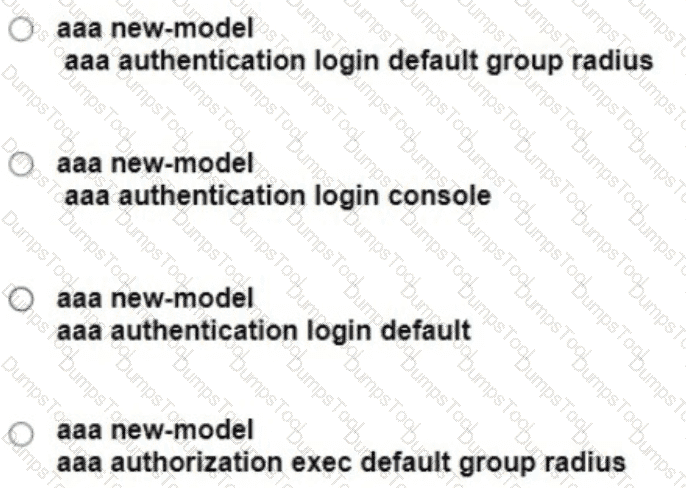
Refer to the exhibit Which command set is required on router R1 to allow the network administrator to authenticate via RADIUS'?
What does the LAP send when multiple WLCs respond to the CISCO_CAPWAP-CONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
Refer to the exhibit. A network engineer must configure NETCONF. After creating the configuration, the engineer gets output from the command show line, but not from show running-config. Which command completes the configuration?
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two.)