An engineer must implement a CPU ACL that blocks web management traffic to the controller, but they also must allow guests to reach a Web Authentication Redirect page. To which IP address is guest client HTTPS traffic allowed for this to work?
A WLAN is being configured for guest access using the portal on the Cisco CMX. Which Layer 3 security setting must be selected?
Refer to the exhibit. A network administrator must automate notifications for Security Advisories Data reports on the Cisco Catalyst Center v2.3.7 using the Report notification feature. Preferring a programmable approach over UI/CLI, the administrator decides to create a webhook via the Cisco DNA Center API to send real-time HTTP notifications to an external application. The webhook URL https://example.com/webhook uses HTTPS with a self-signed certificate, which requires a specific configuration in the payload to ensure the webhook functions correctly. Which code snippet must be placed onto the box in the code to complete the Python script that configures the webhook to use the self-signed certificate to extract the Security Advisories Data report?

A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
An engineer is implementing profiling for BYOD devices using Cisco ISE. When using a distributed model, which persona must the engineer configure with the profiling service?
Refer to the exhibit.
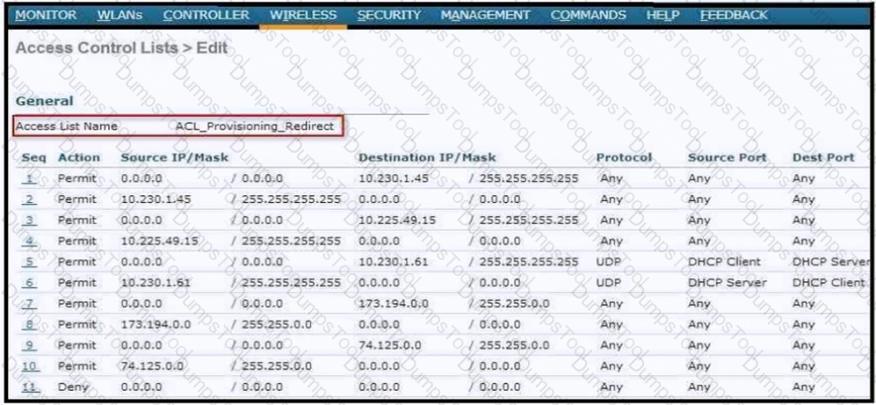
An ACL is configured to restrict access for BYOD clients. The ACL must redirect devices to the guest portal. To which two devices on the local network must the ACL allow access other than the DHCP server? (Choose two.)
Refer to the exhibit.
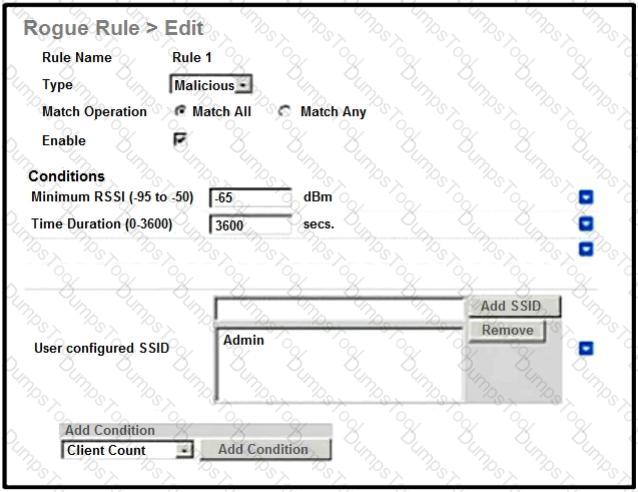
An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
A company has a Cisco wireless network with Cisco ISE. The company wants to allow employees to use their personal mobile devices on the wireless network. The company wants to allow access to the network only if the devices meet certain criteria. To meet the requirement, the company asked a network engineer to create a native supplicant profile. Which two fields must be configured when the profile is created? (Choose two.)
A wireless network has two RF groups where Cisco WLCs are joined. APs are associated with different controllers using the round-robin approach. Rogue containment must be deployed v\ all controllers, but the network must not be affected by any RRM neighbor packets sent by friendly APs. Which AP authentication protection type must be enabled?
An IT department receives a report of a stolen laptop and has information on the MAC address of the laptop. Which two settings must be set on the wireless infrastructure to determine its location? (Choose two.)
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
A network administrator of a school district must implement a DNS-based ACL to block students from accessing certain teacher URLs where test papers are hosted. The infrastructure contains a Cisco Catalyst 9800 WLC with 25 9136 APs. The administrator configured the URL Filter List called urllist_flex_pre, applied the URL Filter List to the default Flex Profile, and defined Preauth called urllist_local_preauth and Postauth called urllist_local_postaut URL Filter List. Which configuration must the administrator apply to implement the ACL on the default policy profile?
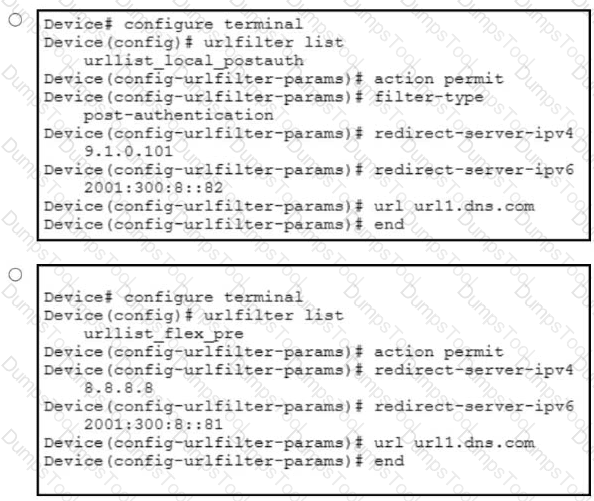
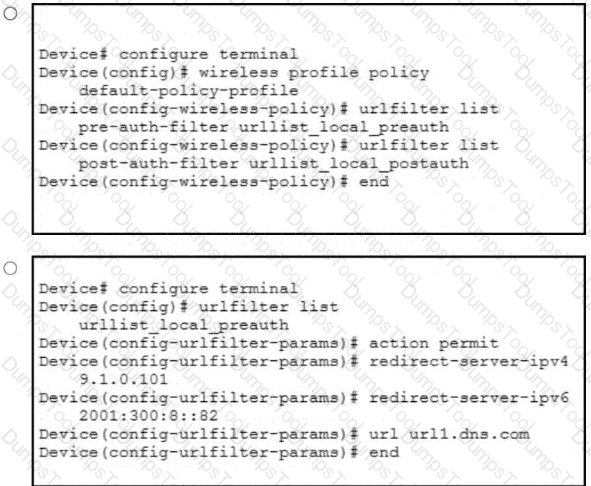
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
An engineer is troubleshooting a Cisco CMX high-availability deployment and notices that the primary and backup Cisco CMX servers are both considered primary. Which command must the engineer run on the backup server?
Which two restrictions are in place with regards to configuring mDNS? (Choose two.)
An engineer is responsible for a wireless network for an enterprise. The enterprise has distributed offices around the globe, and all APs are configured in FlexConnect mode. The network must be configured to support 802.11r and CCKM. What needs to be implemented to accomplish this goal?
WPA2 Enterprise with 802.1X is being used for clients to authenticate to a wireless network through a Cisco ISE server. For security reasons, the network engineer wants to ensure that only PEAP authentication is used. The engineer sent instructions to clients on how to configure the supplicants, but the ISE logs still show users authenticating using EAP-FAST. Which action ensures that access to the network is restricted for these users unless the correct authentication mechanism is configured?
An engineer is configuring an autonomous AP to allow 802.1X authentication for users. The policy on the RADIUS server only allows for EAP-TLS authentication. Which authentication method must the engineer select under the Client Authentication Settings for the SSID on the AP?
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?

A wireless engineer deployed all remote sites as FlexConnect. The client VLAN assignment on these sites is configured manually mapped by WLAN and using local switching. Dynamic VLAN assignment is provided by the newly deployed Cisco ISE. Which IETF attribute must be configured on the AAA server to send that VLAN ID?
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
A Cisco CMX 3375 appliance on the 10.6.1 version code counts duplicate client entries, which creates wrong location analytics. The issue is primarily from iOS clients with the private MAC address feature enabled. Enabling this feature requires an upgrade of the Cisco CMX 3375 appliance in a high availability pair to version 10.6.3. SCP transfers the Cisco CMX image, but the upgrade script run fails. Which configuration change resolves this issue?
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
What is configured to use more than one port on the OEAP to extend the wired network?
After receiving an alert about a rogue AP, a network engineer logs into Cisco Prime Infrastructure and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines that the rogue device is actually inside the campus. The engineer determines that the rogue is a security threat and decides to stop if from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
An engineer is adding APs to an existing VolMLAN to allow for location based services. Which option will the primary change be to the network?
An engineer must configure Cisco OEAPs for three executives. As soon as the NAT address is configured on the management interface, it is noticed that the WLC is not responding for APs that are trying to associate to the internal IP management address. Which command should be used to reconcile this?
Refer to the exhibit.
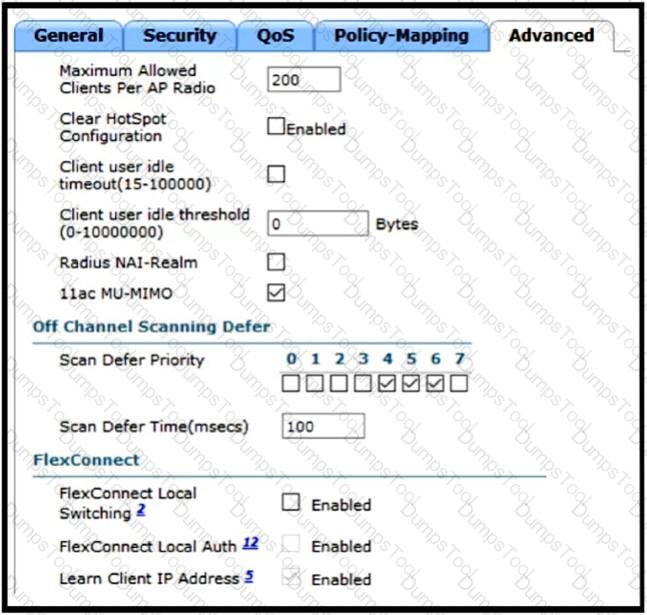
A customer has implemented Cisco FlexConnect deployments with different WLANs around the globe and is opening a new branch in a different location. The engineer’s task is to execute all the wireless configuration and to suggest how to configure the switch ports for new APs. Which configuration must the switching team use on the switch port?
An IT administrator is managing a wireless network in which most devices are Apple iOS. A QoS issue must be addressed on the WLANs. Which configuration must be performed?
An administrator receives reports of many interferers in the wireless network and wants to get the location of these interferers from the maps in Cisco Prime Infrastructure.
When looking at the floor plans/maps, the administrator does not see any interferers, but can see all wireless clients located successfully.
Which two statements define the cause of the issue? (Choose two.)
A company is concerned about unauthorized APs on their wired and wireless networks. The company implements a Cisco Catalyst Center (formerly DNA Center) solution. Which feature must be enabled?
An engineer is adding APs to an existing VolMLAN to allow for location based services. Which option will the primary change be to the network?
A network administrator managing a Cisco Catalyst 9800-80 WLC must place all iOS connected devices to the guest SSID on VLAN 101. The rest of the clients must connect on VLAN 102 distribute load across subnets. To achieve this configuration, the administrator configures a local policy on the WLC. Which two configurations are required? (Choose two.)
A customer has a distributed wireless deployment model where the WLCs are located in the data centers. Because the file servers are located in the data center, the traffic from the corporate WLAN “Corp-401266017” must go through the controllers, where the guest WLAN “Guest-19283746” traffic must use the local Internet line installed in each office. Which configuration will accomplish this task?
An engineer has many different WLANs on a WLC but does not want to broadcast them to every AP in the building. Which group must be configured on the WLC to allow different WLANs on the different APs without creating new interfaces?
An engineer must control administrative access to the WLC using their Active Directory without being concerned about RBAC after the admin user is authenticated. Which two features does the engineer configure to accomplish this task? (Choose two.)
Refer to the exhibit.
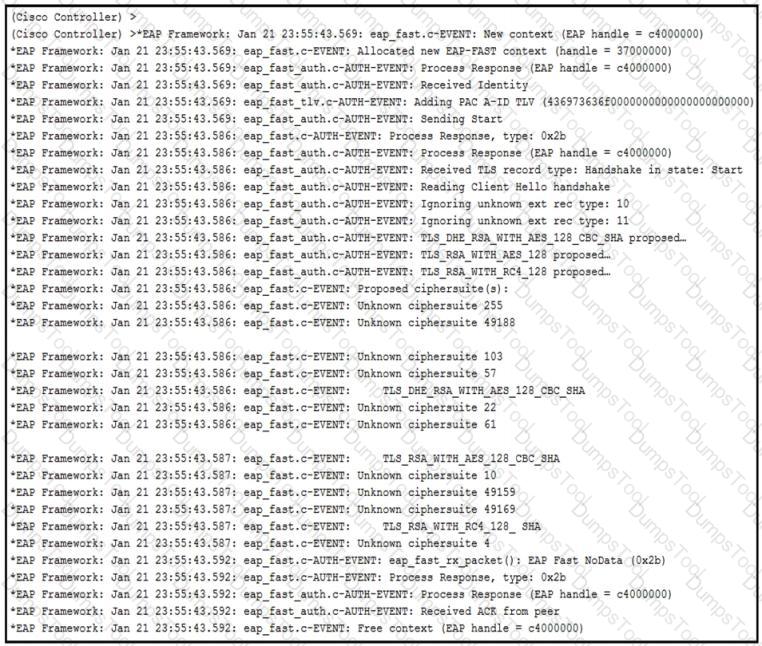
An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
An engineer is planning an image upgrade of the WLC, and hundreds of APs are spread across remote sites with limited WAN bandwidth. The engineer must minimize the WAN utilization for this upgrade. Which approach must be used for the AP image upgrade?
A network administrator just completed the basic implementation of Cisco CMX and tries to implement location tracking. The administrator is having trouble establishing connectivity between one of the WLCs through NMSP. What must be configured to establish this connectivity? (Choose two.)
An engineer needs read/write access to rename access points and add them to the correct AP groups on a wireless controller. Using Cisco ISE TACACS, which custom attributes is the minimum required?
Refer to the exhibit.
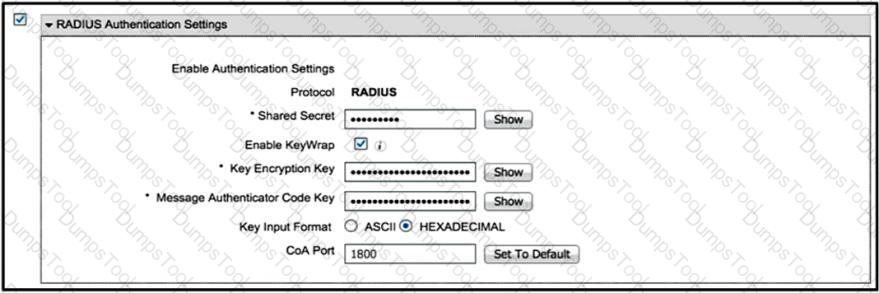
The security team has implemented ISE as an AAA solution for the wireless network. The wireless engineer notices that though clients are able to authenticate successfully, the ISE policies that are designed to place them on different interfaces are not working. Which configuration must be applied in the RADIUS Authentication Settings section from the ISE Network Device page?
An engineer is configuring wireless guests using Cisco CWA. When a device connects, it must be redirected to the WebAuth, but this was failing. What must be configured for the device to be redirected correctly?
A company is deploying wireless PCs on forklifts within its new 10,000-square-foot(3048-square-rneter) facility.
The clients are configured for PEAP-MS-CHAPv2 with WPA TKIP. Users report that applications frequently drop when the clients roam between access points on the floor. A professional site survey was completed.
Which configuration change is recommended to improve the speed of client roaming?
An engineer set up identity-based networking with ISE and configured AAA override on the WLAN. Which two attributes must be used to change the client behavior from the default settings? (Choose two.)
The IT manager is asking the wireless team to get a report for all guest user associations during the past two weeks. In which two formats can Cisco Prime save this report? (Choose two.)
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
The marketing department creates a promotion video for the branch store. Only interested hosts must receive the video over wireless multicast. What allows this feature?
Refer to the exhibit.
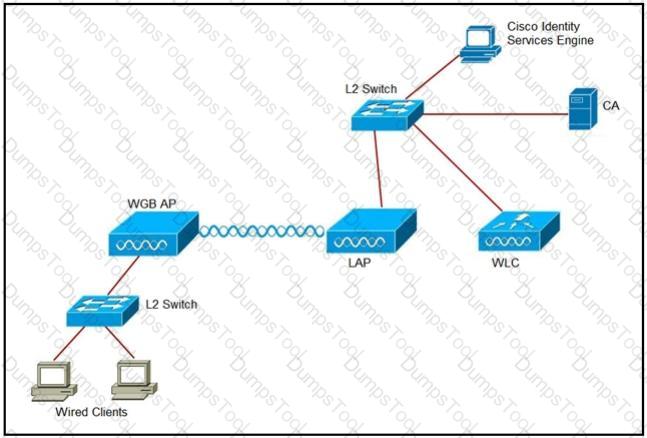
An engineer must connect a fork lift via a WGB to a wireless network and must authenticate the WGB certificate against the RADIUS server. Which three steps are required for this configuration? (Choose three.)
What is the default NMSP echo interval between Cisco MSE and a Wireless LAN Controller?
A network engineer needs to configure multicast in the network. The implementation will use multiple multicast groups and PIM routers. Which address provides automatic discovery of the best RP for each multicast group?
An engineer just added a new MSE to Cisco Prime Infrastructure and wants to synchronize the MSE with the Cisco 5520 WLC, located behind a firewall in a DMZ. It is noticed that NMSP messages are failing between the two devices. Which traffic must be allowed on the firewall to ensure that the MSE and WLC are able to communicate using NMSP?
What is the Cisco recommended configuration for a Cisco switch port connected to an AP in local mode for optimal voice over WLAN performance with an 8821 wireless phone?
A company is concerned about unauthorized APs on their wired and wireless networks. The company implements a Cisco Catalyst Center (formerly DNA Center) solution. Which feature must be enabled?
An engineer must implement intrusion protection on the WLAN. The AP coverage is adequate and on-channel attacks are the primary concern. The building is historic, which makes adding APs difficult. Which AP mode and submode must be implemented?
A FlexConnect remote office deployment is using five 2702i APs indoors and two 1532i APs outdoors. When a code upgrade is performed and FlexConnect Smart AP Image Upgrade is leveraged, but no FlexConnect Master AP has been configured, how many image transfers between the WLC and APs will occur?
Which two steps are needed to complete integration of the MSE to Cisco Prime Infrastructure to track the location of clients/rogues on maps? (Choose two.)
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A controller shows that an AP in your environment is detecting interference, but the AP health score in Cisco DNA Center is unaffected. What are two reasons that Cisco DNA Center is ignoring the interference? (Choose two.)
A network engineer created a new wireless network that will be used for guest access. The corporate network must utilize all rates. The guest network must use only lower rates instead of 802.11n data rates. To what must the WMM policy of the WLAN be set to accomplish this task?
A hospital wants to offer indoor directions to patient rooms utilizing its existing wireless infrastructure. The wireless network has been using location services specifications. Which two components must be installed to support this requirement? (Choose two.)
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
A customer wants the APs in the CEO’s office to have different usernames and passwords for administrative support than the other APs deployed throughout the facility. Which feature must be enabled on the WLC and APs to achieve this goal?
An engineer has implemented 802.1x authentication on the wireless network utilizing the internal database of a RADIUS server. Some clients reported that they are unable to connect. After troubleshooting, it is found that PEAP authentication is failing. A debug showed the server is sending an Access- Reject message. Which action must be taken to resolve authentication?
A company has a single WLAN configured for 802.1x authentication with the QoS set to Silver. This WLAN supports all corporate and BYOD access. A decision has been made to allow users to install Cisco Jabber on their personal mobile devices. Users report poor voice quality when using Jabber. QoS is being applied only as best effort. What must be configured to ensure that the WLAN remains on the Silver class and to ensure Platinum class for Jabber?
A company is collecting the requirements for an on-premises event. During the event, a wireless client connected to a dedicated WLAN will run a video application that will need on average 391595179 bits per second to function properly. What is the QoS marking that needs to be applied to that WLAN?
An engineer has implemented advanced location services for a retail wireless deployment. The marketing department wants to collect user demographic information in exchange for guest WLAN access and to have a customized portal per location hosted by the provider. Which social connector must be tied into Cisco CMX to provide this service?
Refer to the exhibit.
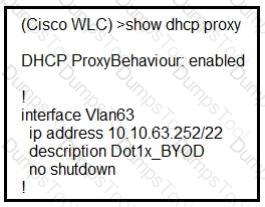
A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
A Cisco 8540 WLC manages Cisco Aironet 4800 Series Aps and sends AoA data to a Cisco CMX 3375 Appliance for Hyperlocation. The load from the WLC is distributed to another virtual CMX server using CMX grouping. The virtual CMX server shows location RSSI data and not Hyperlocation. No AoA metrics are shown on the metrics page of the CMX virtual appliance under System > Metrics > Location Metrics. How must the network administrator resolve this issue?
You enter the command or a Cisco Catalyst 3850 Series Switch that runs Cisco ISO XE. What does the command do?
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco
ISE?
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
A company wants to utilize the wireless network to push videos to wireless clients. An engineer has been hired to configure a Cisco WLC to notify users when it cannot provide a video stream while using the Multicast Direct Feature. Which settings must be enabled for this functionality?