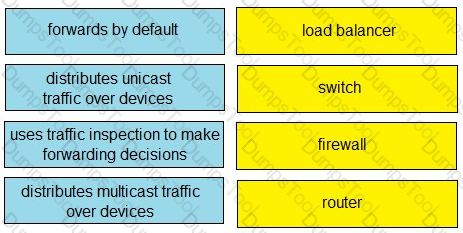
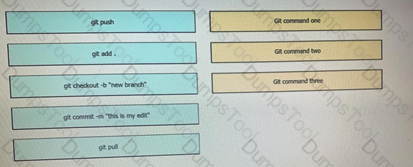
Drag and Drop the Bash commands from the left onto the correct actions on the right.
What is the outcome of executing this command?
git clone ssh://john@exmaple.com/path/to/my-project_git
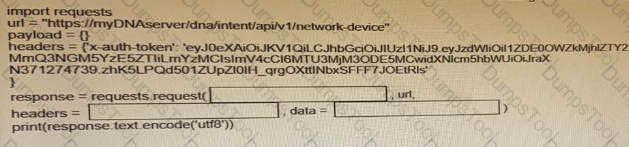
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
Fill in the blanks to complete the statement.
Cisco DNA provide the capability to send an HTTP _______________ request to the API endpoint https://DNA-c_API_ADDRESS/api/vi/network-device/ and receive the network __________ list in __________ format.
A 401 HTTP response code is returned when calling a REST API. What is the error state identified by this response code?
A REST API service requires authentication based on the username and password. The user “john” has the password “384279060” and the Base64 encoding of those credentials is “am9objowMTIzNDU2Nzg=”. Which method completes an authentication request?
Users cannot access a webserver and after the traffic is captured, the capture too* shows an ICMP packet that reports "communication administratively prohibited" What Is the cause of this webserver access Issue?
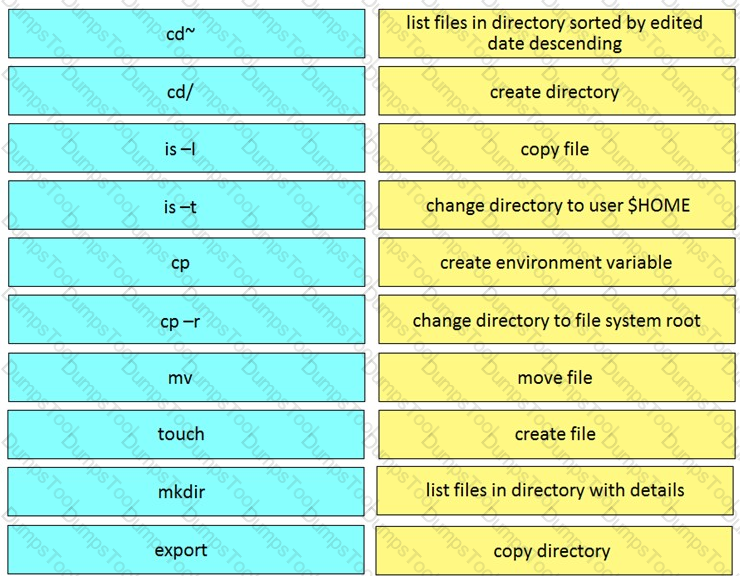
The project is migrated to a new codebase, the “old_project” directory must be deleted. The directory has multiple read-only files, and it must be deleted recursively without prompting for confirmation. Which bash command must be used?
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device mut be at fault?
Refer to the exhibit.
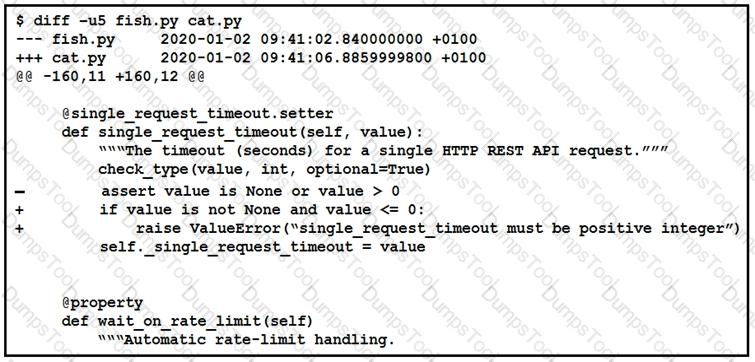
The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”

In python, which expression checks whether the script returns a success status code when the Requests library is used?
Refer to the exhibit.
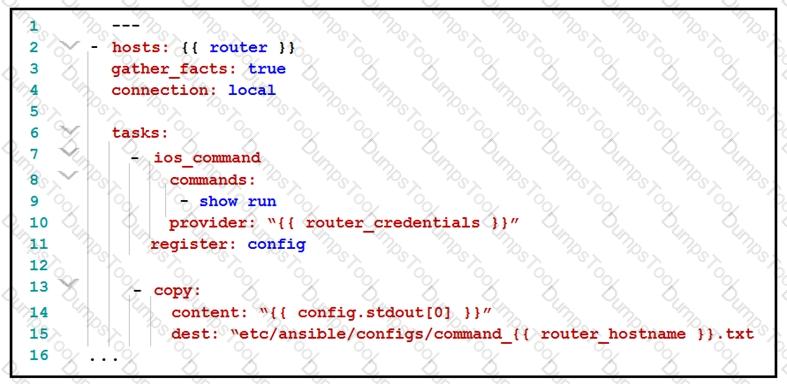
What is the effect of this Ansible playbook on an IOS router?
Before which process is code review performed when version control is used?
Refer to the exhibit.
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
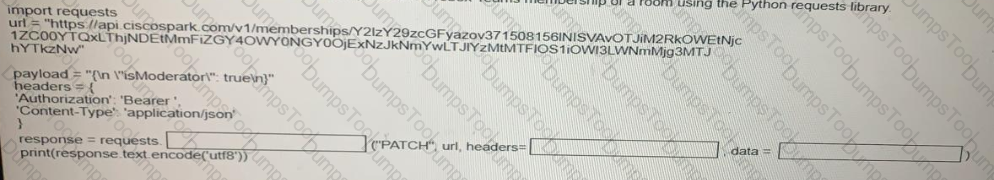
Fill in the blanks to complete the Python script to update the Webex Teams membership of a room using the Python requests library import requests
How is a branch called "my-bug-fix" started to develop a fix needed in a product?
Refer to the exhibit.
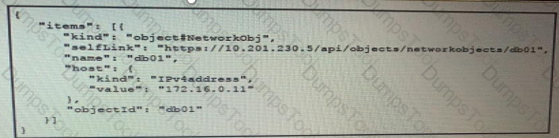
The JSON data in the exhibit has been parsed and stored in a variable, “data”. What returns the value “172.16.0.11” ?
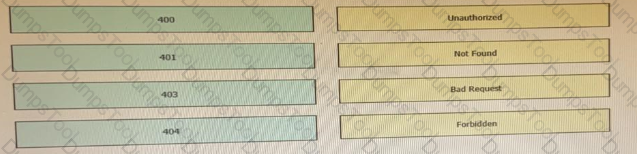
Drag and drop the HTTP status codes from the left onto the correct descriptions on the right.
Which action resolves a 401 error in response to an HTTP GET that is issued to retrieve statement using RESTCONF on a CSR 1000V?
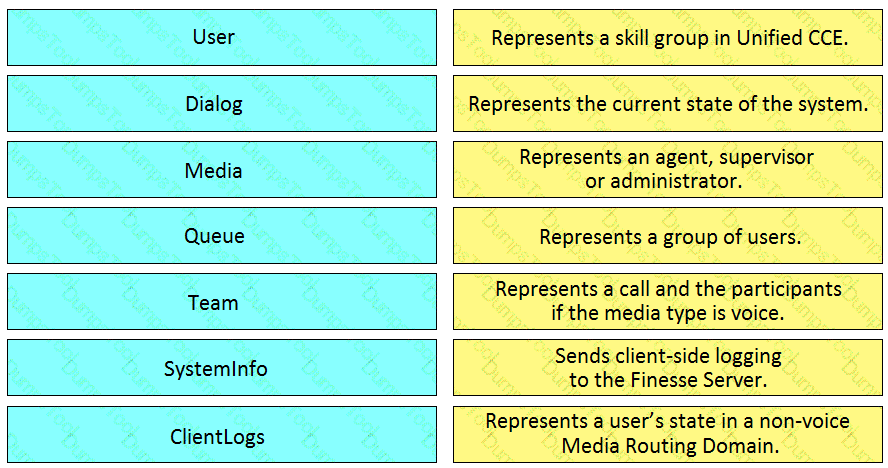
Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
Refer to the exhibit.
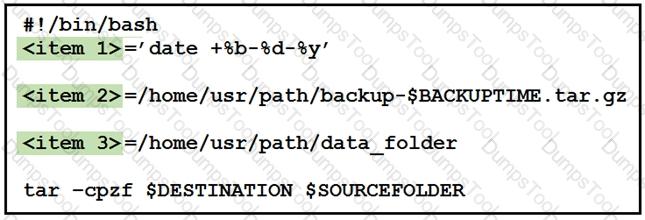
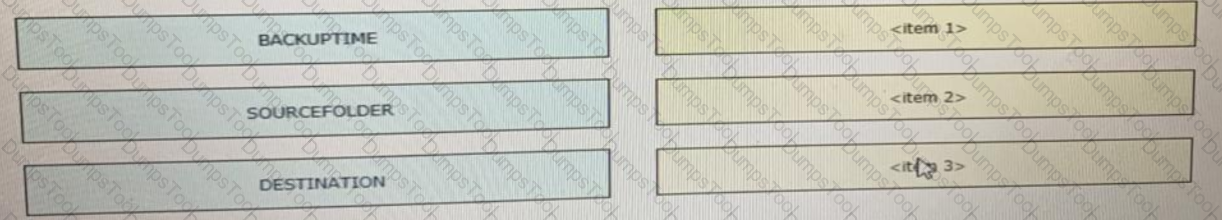
Drag and drop the variables from the left onto the item numbers on the right that match the missing assignments in the exhibit.
A developer needs to prepare the file README.md in the working tree for the next commit operation using Git. Which command needs to be used to accomplish this?
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
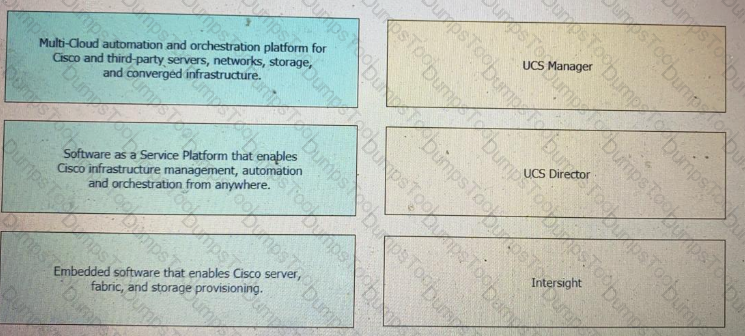
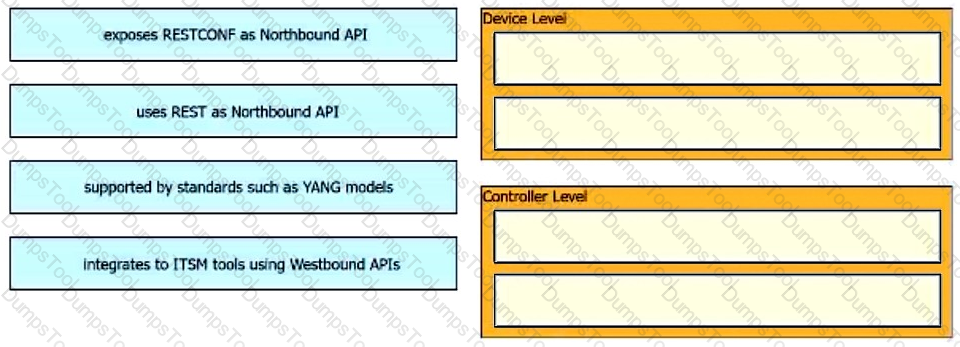
Drag and drop the capability on the left onto the Cisco compute management platform that supports the capability on the right.
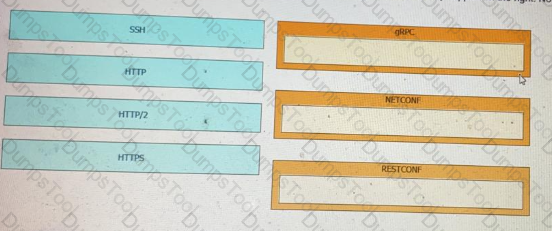
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
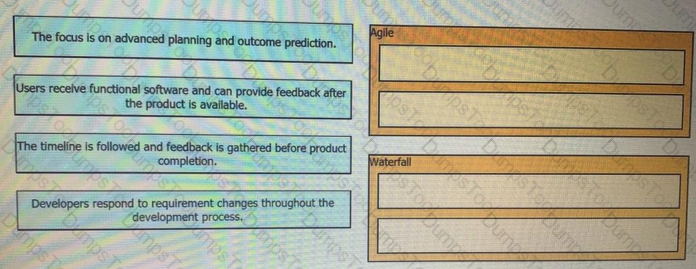
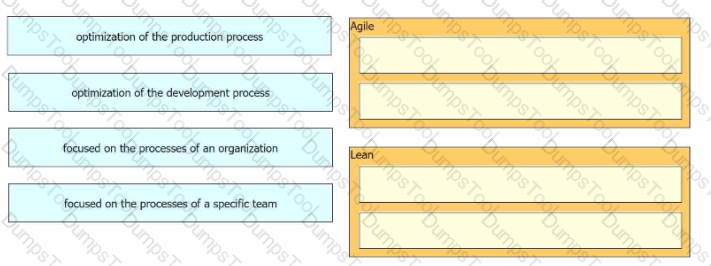
Drag and drop the characteristics from the left onto the corresponding software development methodologies on the right?
Refer to the exhibit.
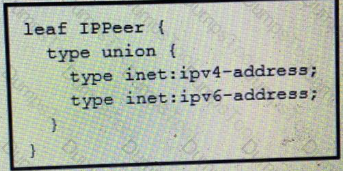
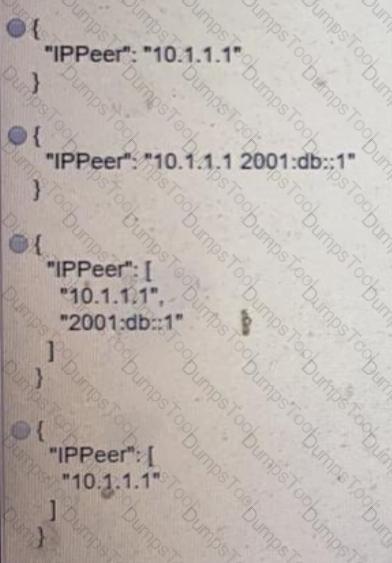
What is the value of the node defined by this YANG structure?
Which HTTP status Code means that the server cannot or will not process the request because of perceived client error?
Drag and Drop the GIT commands from the left onto the right that add modified local files to a remote repository. Not all options are used
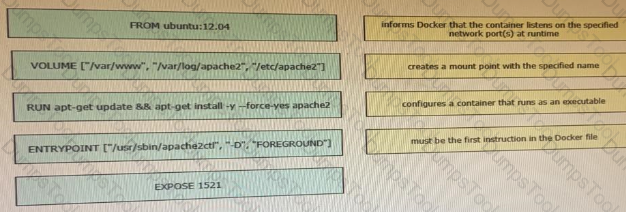
Drag and drop the Docker file instructions from the onto correct descriptions on the right. Not all options are used.
Refer to the exhibit.
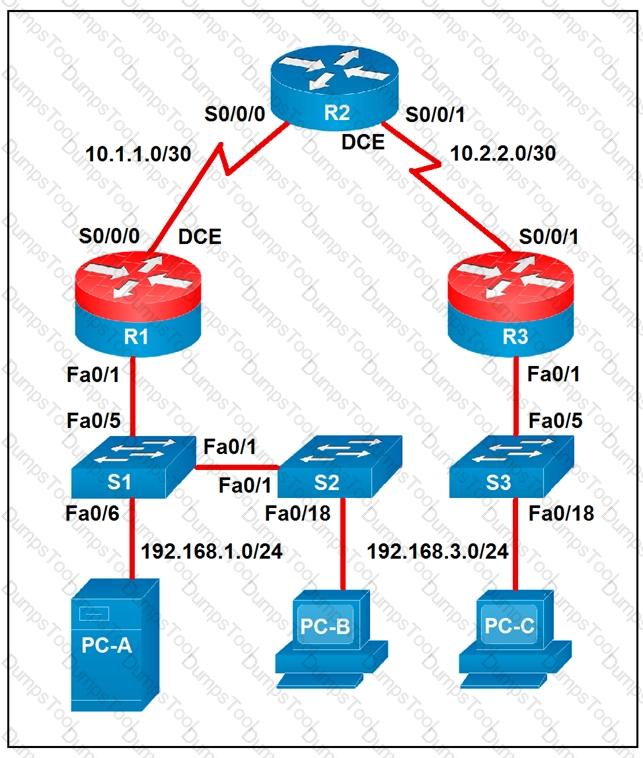
Which two statements about the network diagram are true? (Choose two.)
Which HTTP code group is issued when a request is received successfully, understood, and processed?
What are two functions of a routing table on a network device? (Choose two.)
Refer to the exhibit.
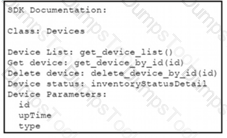
A Python script must delete all Cisco Catayst 9300 Series switches that have an uptime that is greater than 90 days The script must also query for the status of all the other devices Drag and drop the code from the bottom onto the bottom box the code is missing to complete the script Not at options are used

Refer to the exhibit.
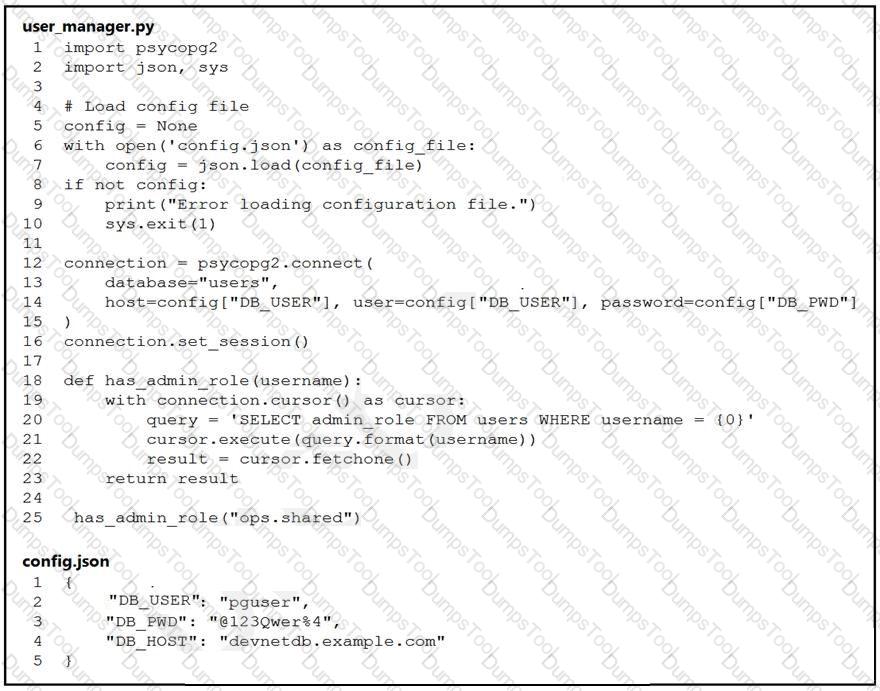
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
In which two ways is an application characterized when interacting with a webhook? (Choose two.)
How does a developer create and switch to a new branch called "my-bug-fix" to develop a product fix?
Which tool is used to block all traffic to the domain by using a single API call?
Refer to the exhibit.
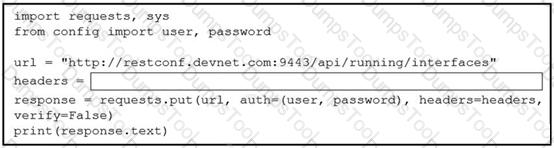
A network engineer wants to use an API to update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which line of code needs to be placed in the snippet where the code is missing?
Refer to the exhibit.
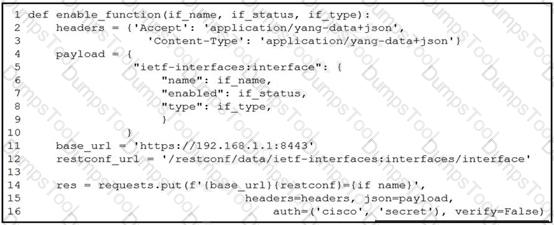
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
A developer is working on a feature for a new application. The changes in the existing branch named 'feat00304' must be integrated into a single commit with the current working primary branch named 'prodapp411926287'. Which git command must be used?
Refer to the exhibit.
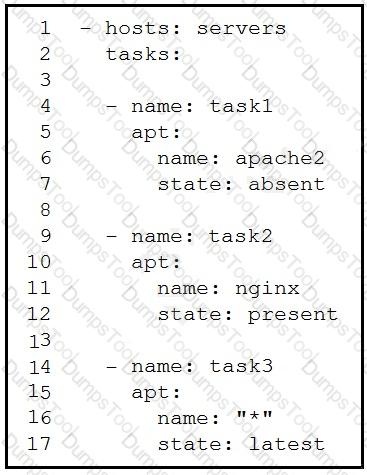
A developer must check packages on web load balancers that use nginx packages. The developer updates the servers as required in Ansible inventory and prepares an Ansible playbook to automate this workflow on related servers. Which process is being automated by the Ansible playbook?
Refer to the exhibit.

An engineer must configure a load balancer server. The engineer prepares a script to automate workflow by using Bash. The script install the nginx package, moves to the /optAtginx directory, and reads the sites M We (or further processing Based on the script workflow, which process is being automated within the loop by using the information mi sites txt?
Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components:
• MySQL database that stores data about customers
• HTML5 and JavaScript UI that runs on Apache
• REST API written in Python
What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.)
A company is adopting DevOps as part of an internal transformation, and is reviewing the success of the first deployments. Developers and engineers are working together to resolve any resulting issues. However, this new way of working has increased overhead, and the team is finding it difficult to complete releases in time.
Which area of the CALMS framework must the company target for improvement?
How does a synchronous API request differ from an asynchronous API request?
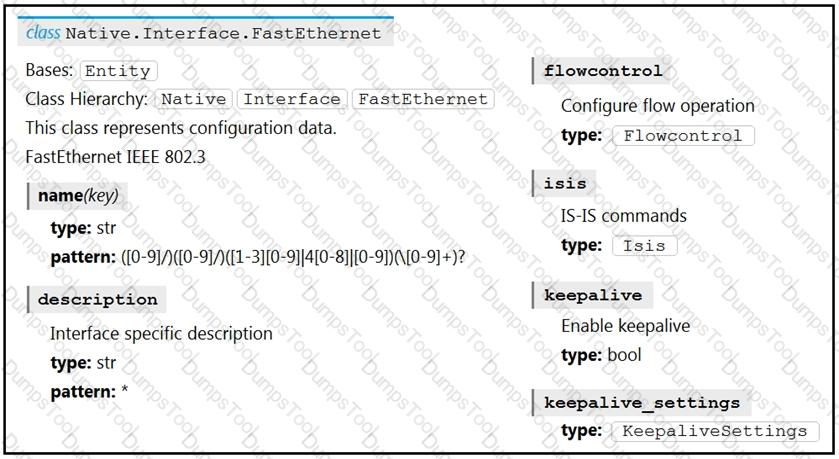
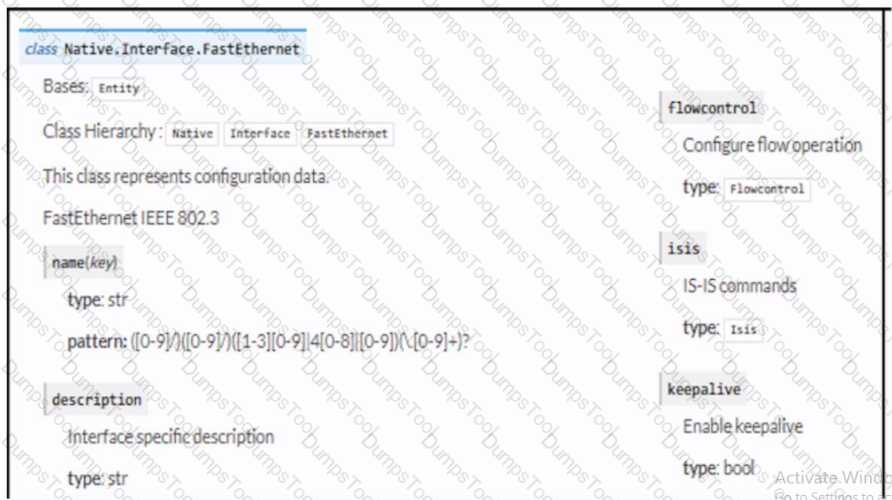
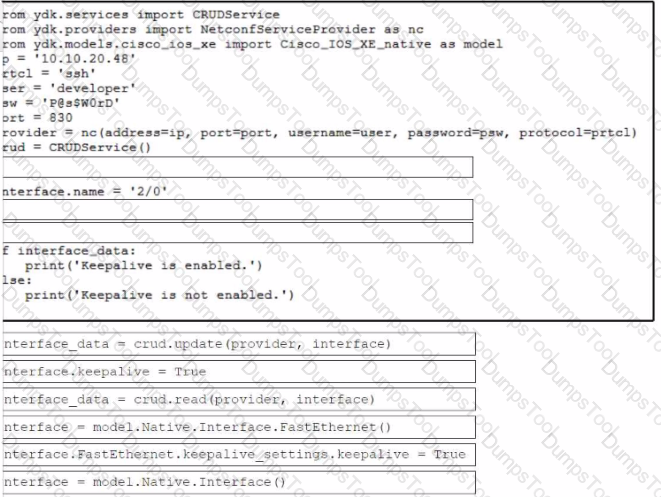
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?
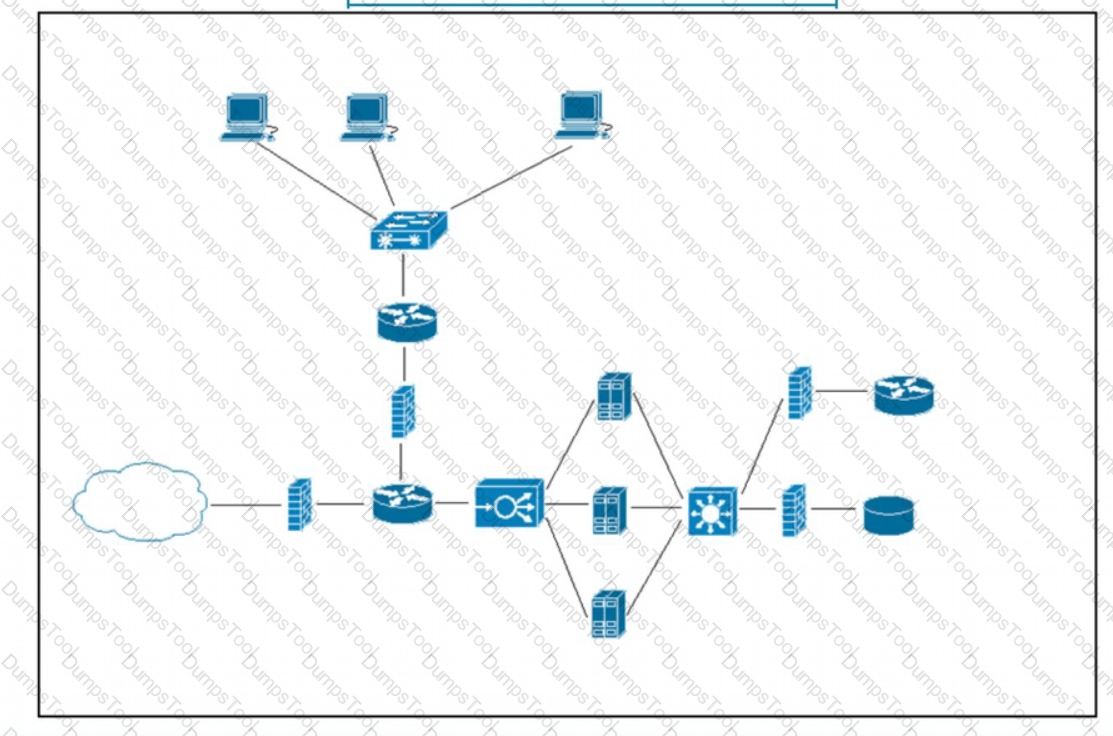
Refer to the exhibit. What does the load balancer enable in the network topology?
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
Refer to the exhibit.
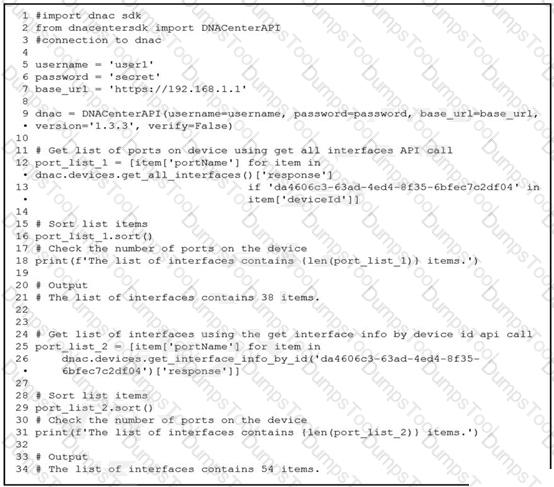
An engineer writes a Python script that uses two different API calls to query Cisco DNA Center for the number of interfaces on a device. The engineer notices that the two API calls produce different results. Why are fewer interfaces returned for the same device when the 'get_all_interfaces' API call is used?
Refer to the exhibit.

A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
Refer to the exhibit.
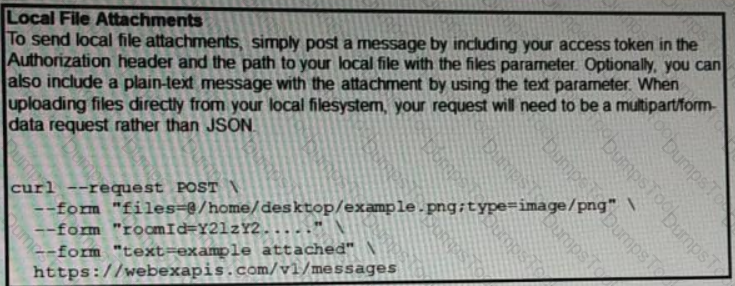
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
Refer to the exhibit.
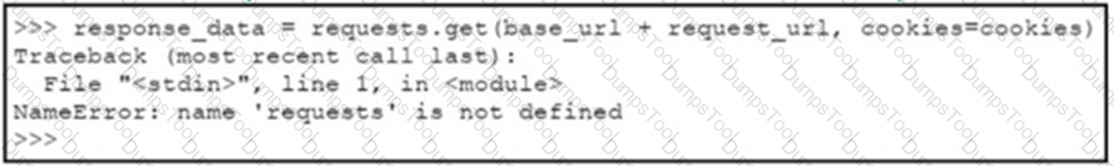
A Python code has been written to query a device. The executed code results in the error shown. Which action resolves the problem?
Refer to the exhibit.
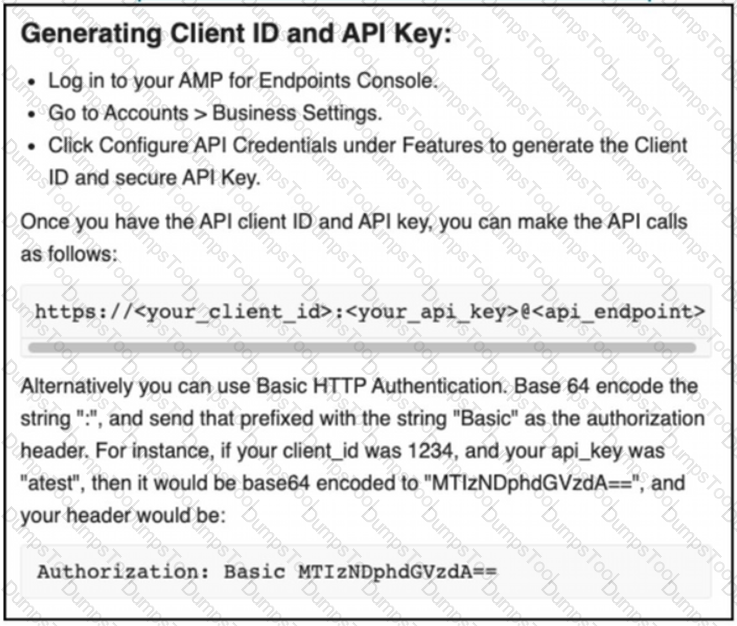
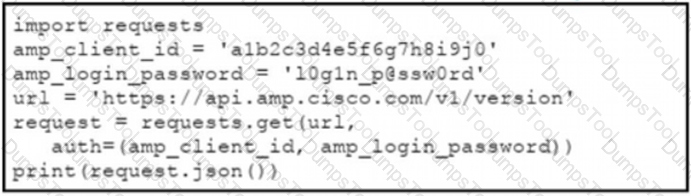
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
B)
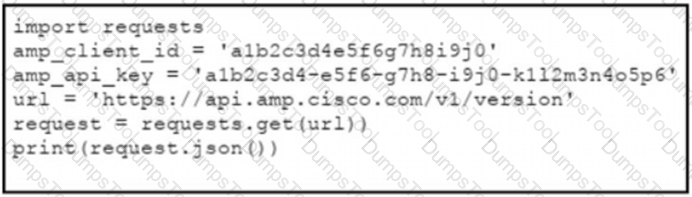
C)
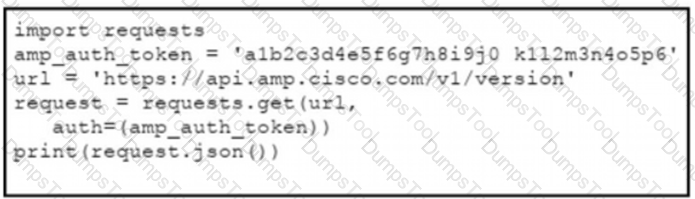
D)
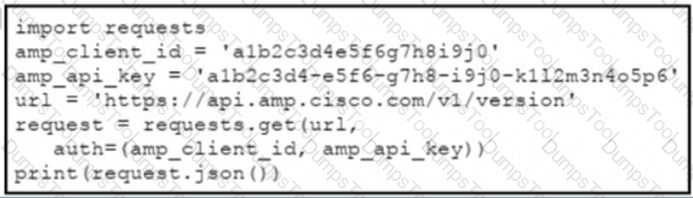
Refer to the exhibit.
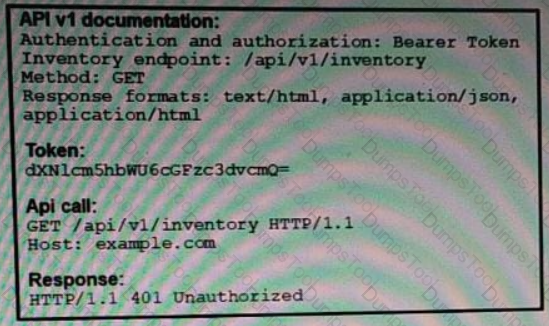
An API call is constructed to retrieve the inventory in XML format by using the API. The response to the call is 401 Unauthorized. Which two headers must be added to the API call? (Choose two.)
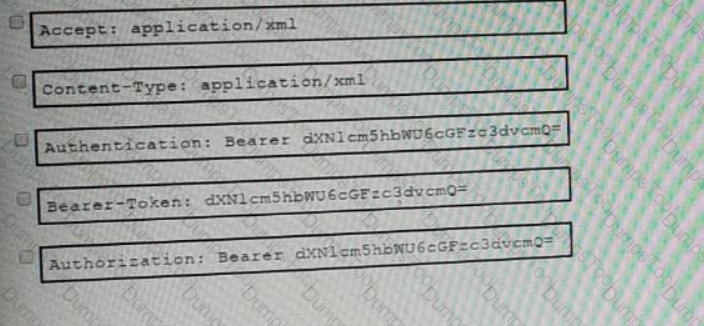
Refer to the exhibit.
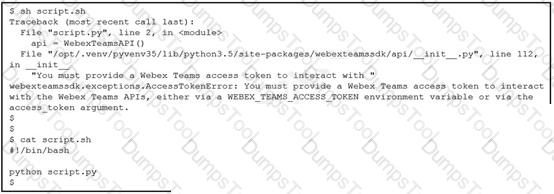
Which line must be included in the Bash script for the Python code to succeed?
A developer is creating a script to interact with a REST API service which requires basic authentication. The credentials are "devnet:391665405" and the Base64 encoding of the credentials is "GV2bmV0dXNlcjpDaXNj=". Which payload and header combination must be used for authentication?
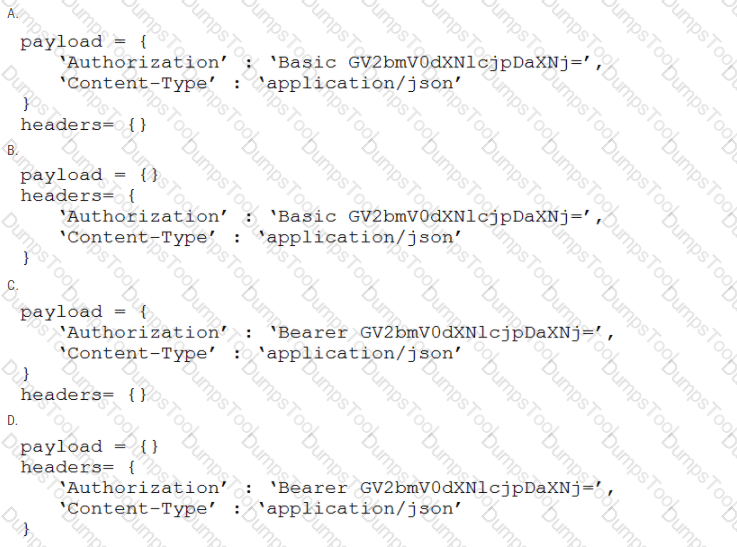
Refer to the exhibit.
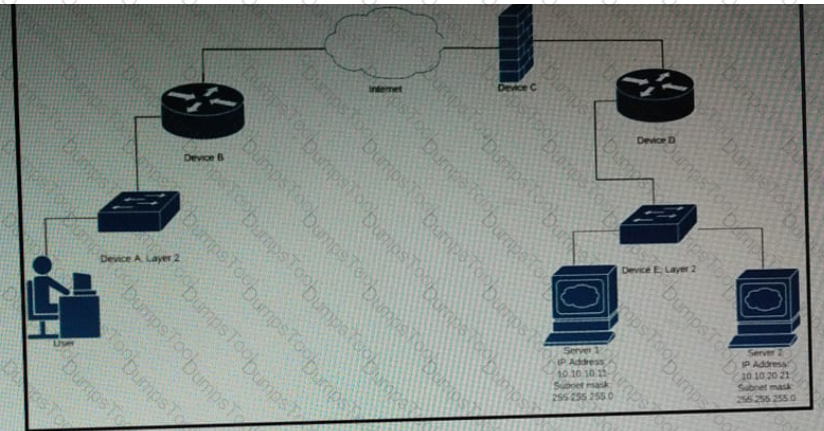
Which device limits traffic between server 1 and server 2?
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
Refer to the exhibit.
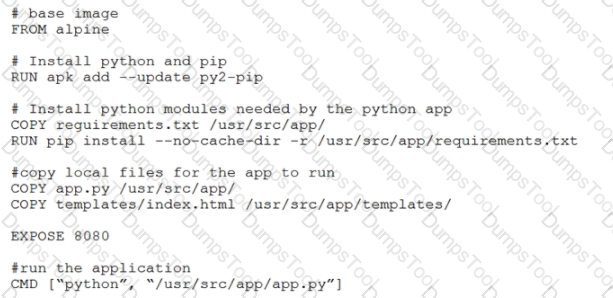
Which function does the EXPOSE line perform when building an image from this Dockerfile?
What is a benefit of a model-driven approach for infrastructure automation?
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request?
Which Cisco platform provides organization-wide automation, security, policy enforcement, any agility across wired and wireless networks?
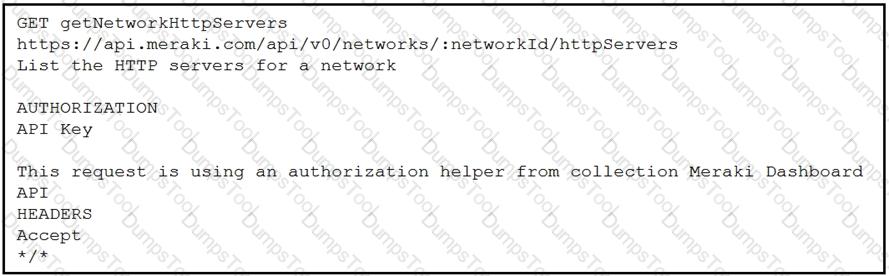
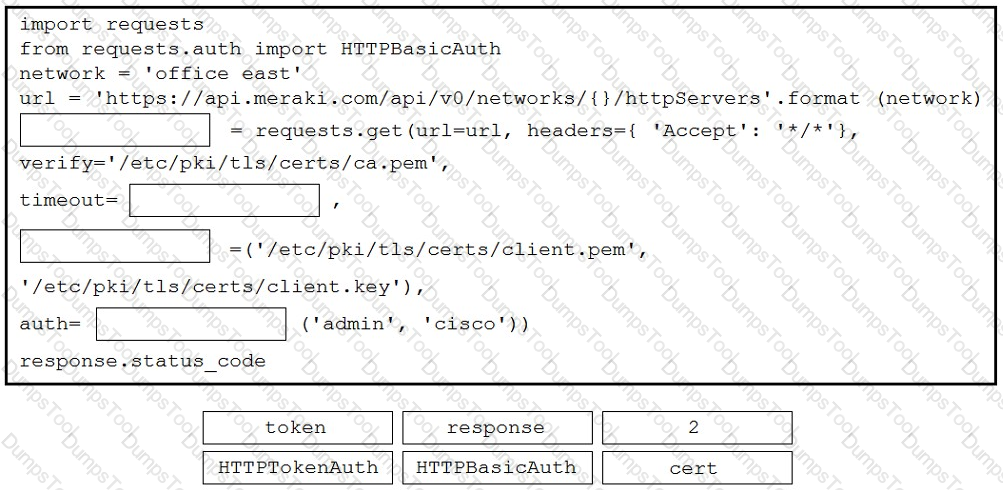
Refer to the exhibit. A developer is creating a Python script to obtain a list of HTTP servers on a network named office_east by using the Cisco Meraki API. The request has these requirements:
• Must time out if the response is not received within 2 seconds.
• Must utilize client certificates and SSL certificate verification.
• Must utilize basic authentication that uses a username of admin and a password of cisco.
• Must save the response to an object named response.
Drag and drop the code snippets from the bottom onto the blanks in the code to meet the requirements. Not all options are used.
Which advantage does the agile process offer compared to waterfall software development?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
A developer attempts to refactor and improve the application code. It is noticed that the code contains several pieces of key information that could be a security threat if this code is accessible by those who are not
authorized to this data. Which approach addresses the security concerns noticed by the developer?
What is a benefit of using model-driven programmability for infrastructure automation?
A customer's cloud services must:
Migrate services to another data center on demand.
Save the operational state of the machine on demand.
Support Windows and Linux GUIs.
Maximize hardware utilization.
Which type of deployment meets these requirements?
Refer to the exhibit.
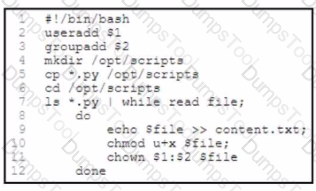
An engineer must add new users and set privileges for executing a few Python scripts. The engineer prepares a Bash script to automate this task. The script ds a user and a group from the command-line arguments, creates a directory, and copies the Python scripts to it. The script then changes to the directory and lists the scripts, used on the script workflow, which process is being automated within the loop by using the list of Python scripts?
Which HTTP response code is returned from a successful REST API call to create a new resource?
Refer to the exhibit.

What are two results of running the RESTCONF query? (Choose two.)
Which tool provides a testing environment to run tests on network devices and perform network automation scenarios?
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information?
Refer to the exhibit. An engineer runs a network that consists of Cisco Nexus devices. The network is distributed between data centers in different locations. The switches are configured using standalone connections and a single point of failure. Which process is being automated by the Ansible playbook?
What is a benefit of using a code review process in application development?
Refer to the exhibit.
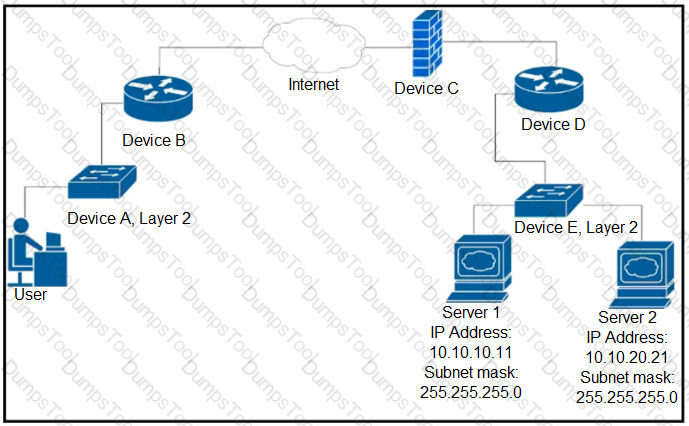
Up to which device does the communication server 1 and server 2 go?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
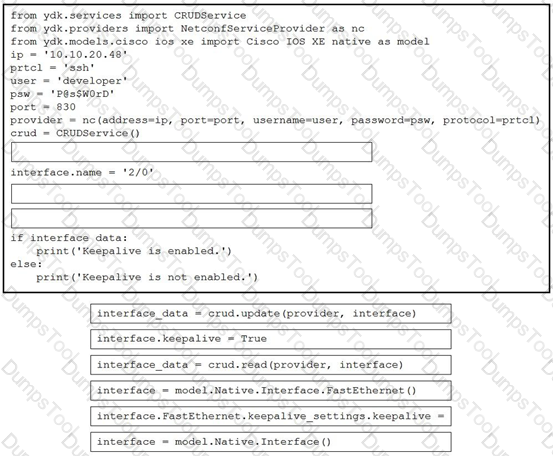
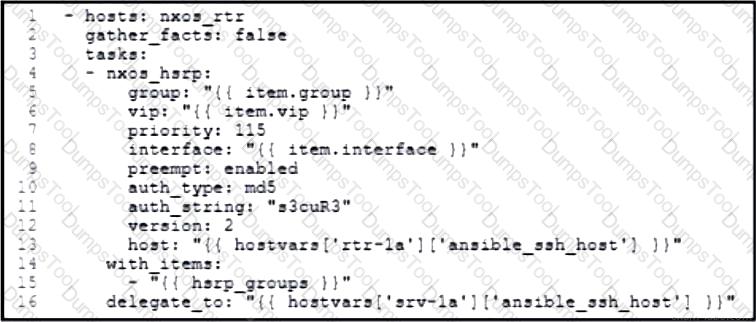
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
Developer is working on a new feature and made changes on a branch named ‘branch-413667549a-new’. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state?
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API?
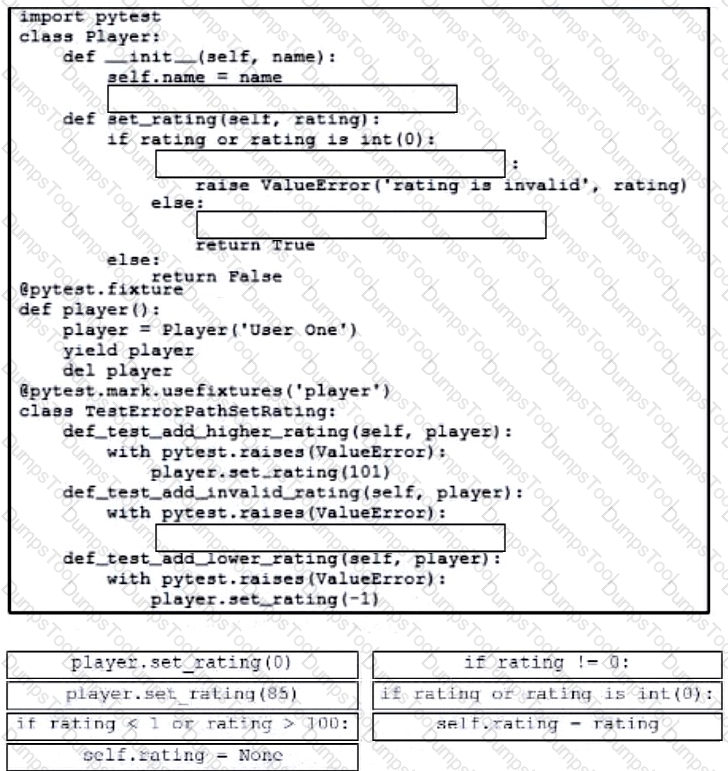
Drag and drop the code from the bottom onto the box where the code is missing to complete the error path scenario. Not all options are used.
Which command reverses the last commit without changing the index file or the working tree position?
Which protocol is used for clock synchronization between network devices?
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right.
A developer is attempting to retrieve all the messages from a Cisco Webex space. The server responds by sending the first 1,000 messages. The developer must make additional requests to retrieve the rest of the messages. Which API constraint is described in this scenario?
Refer to the exhibit.
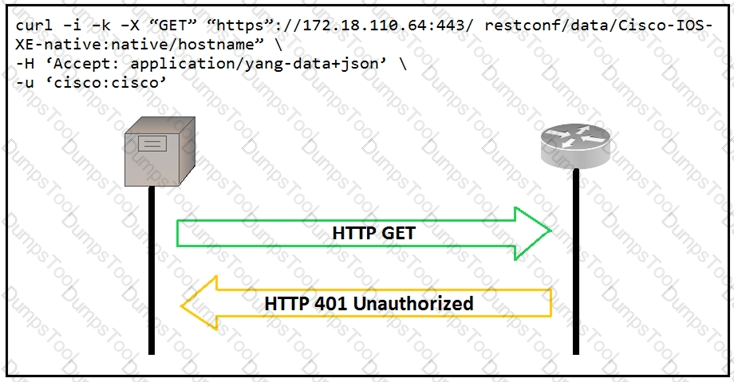
An administrator attempts to perform a GET operation by using the Cisco IOS XE RESTCONF API to return the hostname of a device. The sequence diagram in the exhibit illustrates the HTTP messages observed. Which change to the API request resolves the issue?
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.

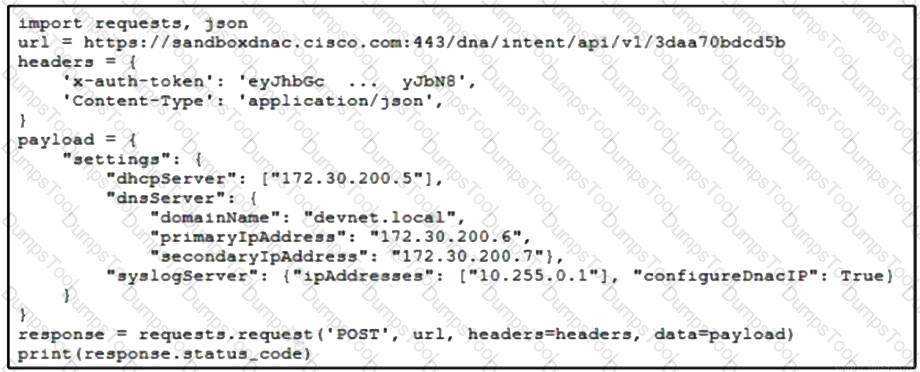
Refer to the exhibit. A developer writes a script to create a new network by using the Cisco DNA Center API. After running the script for the first time, the developer observes that HTTP code 404 is printed to the console. Which action resolves the problem?
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
Refer to the exhibit.
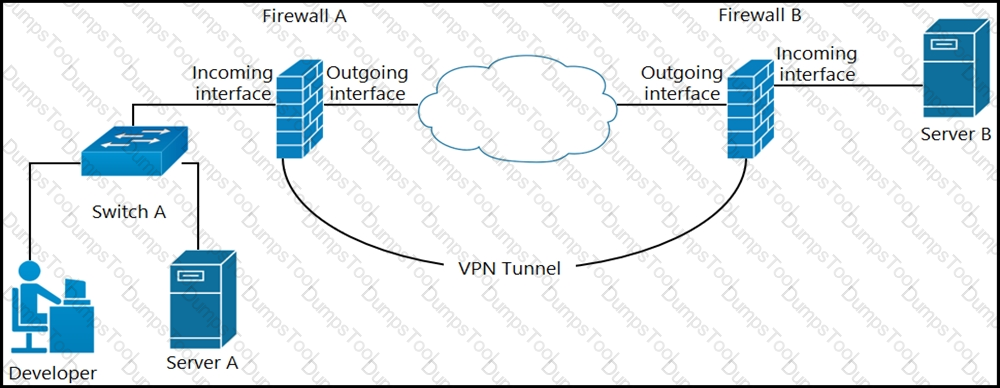
A developer can access the TLS REST API on server A, but cannot access the API on server B. The developer can ping server B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue?
A company deploys an application via containers in its local data center. As soon as the application goes into production, it starts to crash at specific hours of the day. After investigation, it is concluded that the crashes are due to too many users accessing the application simultaneously. The spikes must be addressed and allow for future growth without discarding the investment already made. Which deployment model must be used?
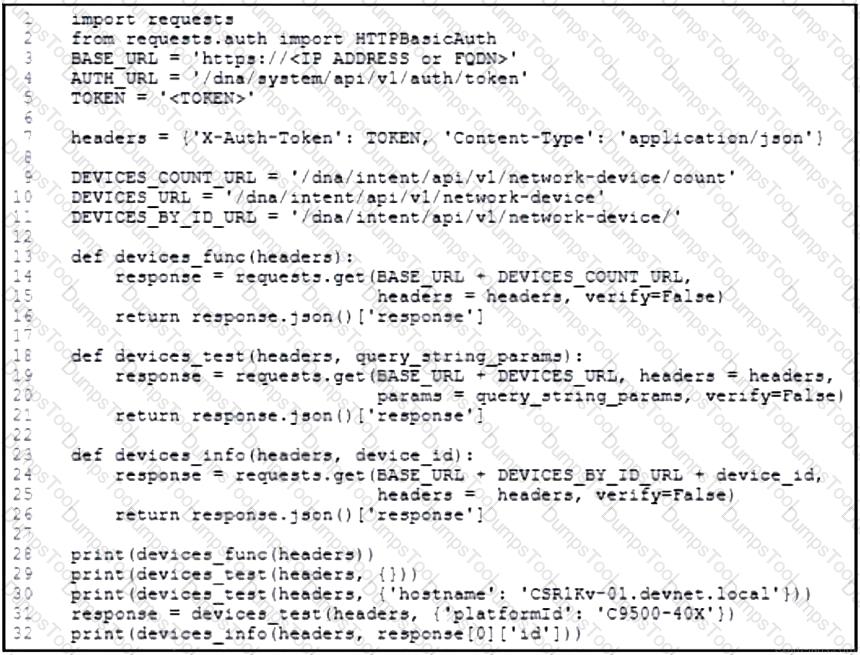
Refer to the exhibit. An engineer prepares a script to automate workflow by using Cisco DNA Center APIs to display:
total count of devices
list of the network devices
information of one device with a hostname filter
What is displayed in the final step after the Python script is executed?
Drag and drop the characteristics from the left onto the software development methodologies on the right.

Refer to the exhibit. A network engineer makes a RESTCONF API call to Cisco IOS XE to retrieve information. Which HTTP method and URL does the engineer use to make the ..call?
A)

B)

C)

D)

An engineer clones a repository that contains a Python script from GitLab to a laptop. After modifying the code, the engineer wants to validate the changes. Which command starts … CI/CD pipeline and runs the automated tests?

Refer to the exhibit. A developer creates a Python script by using the Cisco Meraki API. The solution must:
• Obtain a list of HTTP servers for a network named "netl".
• Print the response body if the HTTP status code is 200.
• Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
A)
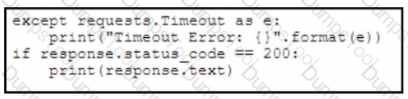
B)
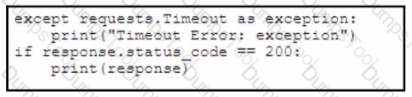
Drag and drop the code from the bottom onto the box where the code is missing to enable ports on a switch by using RESTCONF. Not all options are used.

Why would a developer compare a current version of code to a previous version?
Which standard supported by Cisco IOS XE and Cisco NX-OS is used for automating the configuration of multiple devices across a network?
Which RFC 1918 address space includes a subnet of 172.16.0.0 that uses a mask of 255.255.0.0?
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used.
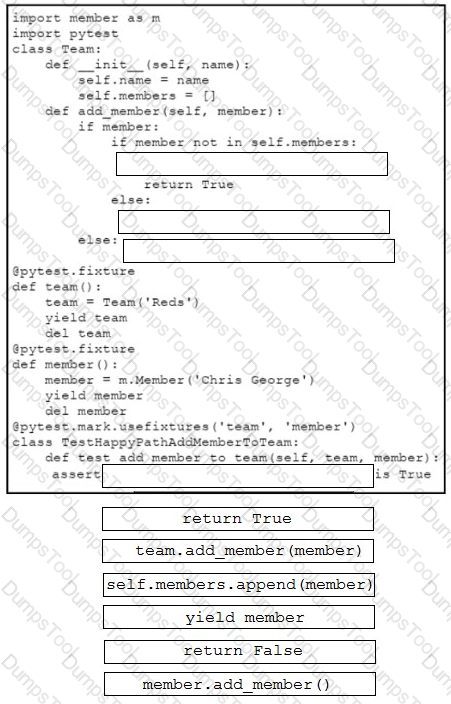
Drag and drop the functions from the left onto the networking devices on the right.