You are reviewing your company’s disaster recovery plan.
Which two daily data backup actions should the plan include?(Choose 2.)
You need to transfer configuration files to a router across an unsecured network.
Which protocol should you use to encrypt the files in transit?
You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a successful login to a privileged account. What is the most appropriate next step?
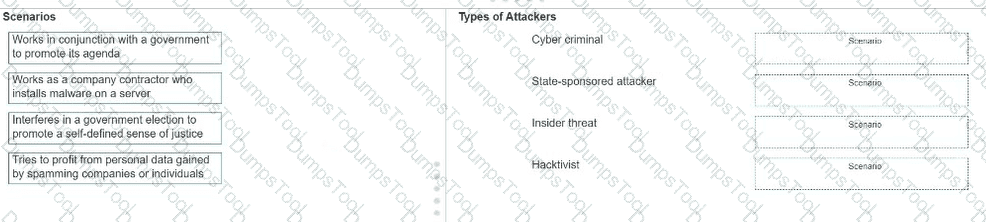
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.
For each statement, selectTrueif it is a common motivation to commit cyber attacks orFalseif it is not.
Note: You will receive partial credit for each correct selection.

Your supervisor tells you that you will participate in a CVSS assessment.
What will you be doing?
Which network security technology passively monitors network traffic and compares the captured packet stream with known malicious signatures?