A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
After a new Log Server is added to the environment and the SIC trust has been established with the SMS what will the gateways do?
The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
If an administrator wants to restrict access to a network resource only allowing certain users to access it, and only when they are on a specific network what is the best way to accomplish this?
When a SAM rule is required on Security Gateway to quickly block suspicious connections which are not restricted by the Security Policy, what actions does the administrator need to take?
Which SmartConsole tab shows logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
When URL Filtering is set, what identifying data gets sent to the Check Point Online Web Service?
Which of the following commands is used to monitor cluster members in CLI?
John is the administrator of a R80 Security Management server managing r R77.30 Check Point Security Gateway. John is currently updating the network objects and amending the rules using SmartConsole. To make John’s changes available to other administrators, and to save the database before installing a policy, what must John do?
Gaia includes Check Point Upgrade Service Engine (CPUSE), which can directly receive updates for what components?
Fill in the blank RADIUS Accounting gets_____data from requests generated by the accounting client
Which of the following methods can be used to update the trusted log server regarding the policy and configuration changes performed on the Security Management Server?
In the Check Point Security Management Architecture, which component(s) can store logs?
Which of the following statements about Site-to-Site VPN Domain-based is NOT true?
Route-based— The Security Gateways will have a Virtual Tunnel Interface (VTI) for each VPN Tunnel with a peer VPN Gateway. The Routing Table can have routes to forward traffic to these VTls. Any traffic routed through a VTI is automatically identified as VPN Traffic and is passed through the VPN Tunnel associated with the VTI.
Both major kinds of NAT support Hide and Static NAT. However, one offers more flexibility. Which statement is true?
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
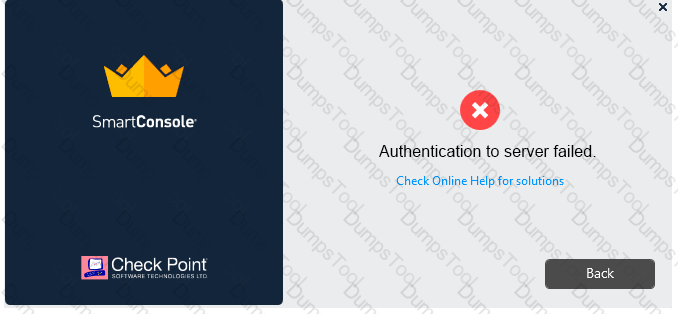
What is the most likely reason?
Fill in the blank: Once a certificate is revoked from the Security Gateway by the Security Management Server, the certificate information is _____.
What are valid authentication methods for mutual authenticating the VPN gateways?
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
Which of the following is NOT a valid configuration screen of an Access Role Object?
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
Fill in the blank: It is Best Practice to have a _____ rule at the end of each policy layer.
Is it possible to have more than one administrator connected to a Security Management Server at once?
Which information is included in the “Extended Log” tracking option, but is not included in the “Log” tracking option?
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
Why is a Central License the preferred and recommended method of licensing?
What are the software components used by Autonomous Threat Prevention Profiles in R8I.20 and higher?
A network administrator has informed you that they have identified a malicious host on the network, and instructed you to block it. Corporate policy dictates that firewall policy changes cannot be made at this time. What tool can you use to block this traffic?
Fill in the blank: By default, the SIC certificates issued by R80 Management Server are based on the ____________ algorithm.
Fill in the blank: A(n)_____rule is created by an administrator and configured to allow or block traffic based on specified criteria.
Which of the following is NOT an option to calculate the traffic direction?
What key is used to save the current CPView page in a filename format cpview_“cpview process ID”. cap”number of captures”?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
True or False: More than one administrator can log into the Security Management Server with SmartConsole with write permission at the same time.
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ___________.
Choose what BEST describes the reason why querying logs now are very fast.
You had setup the VPN Community NPN-Stores' with 3 gateways. There are some issues with one remote gateway(l .1.1.1) and an your local gateway. What will be the best log filter to see only the IKE Phase 2 agreed networks for both gateways.
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits even if the Track option is set to “None”?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
When configuring Spoof Tracking, which tracking actions can an administrator select to be done when spoofed packets are detected?
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
The SmartEvent R80 Web application for real-time event monitoring is called:
Which of the following is considered a "Subscription Blade", requiring renewal every 1-3 years?
Which part of SmartConsole allows administrators to add, edit delete, and clone objects?
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
When comparing Stateful Inspection and Packet Filtering, what is a benefit that Stateful Inspection offers over Packer Filtering?
When defining group-based access in an LDAP environment with Identity Awareness, what is the BEST object type to represent an LDAP group in a Security Policy?
In HTTPS Inspection policy, what actions are available in the "Actions" column of a rule?
The ______ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
Fill in the blanks: A Security Policy is created in_____, stored in the_____ and Distributed to the various
Which two Identity Awareness commands are used to support identity sharing?
Which application is used for the central management and deployment of licenses and packages?
Which of the following is NOT a method used by Identity Awareness for acquiring identity?
Which type of Check Point license ties the package license to the IP address of the Security Management Server?
The Network Operations Center administrator needs access to Check Point Security devices mostly for troubleshooting purposes. You do not want to give her access to the expert mode, but she still should be able to run tcpdump. How can you achieve this requirement?
What licensing feature automatically verifies current licenses and activates new licenses added to the License and Contracts repository?
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
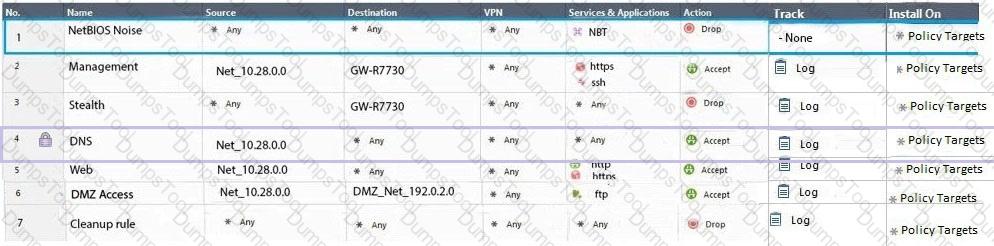
What is the possible explanation for this?
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
Which of the following log queries would show only dropped packets with source address of 192.168.1.1 and destination address of 172.26.1.1?
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
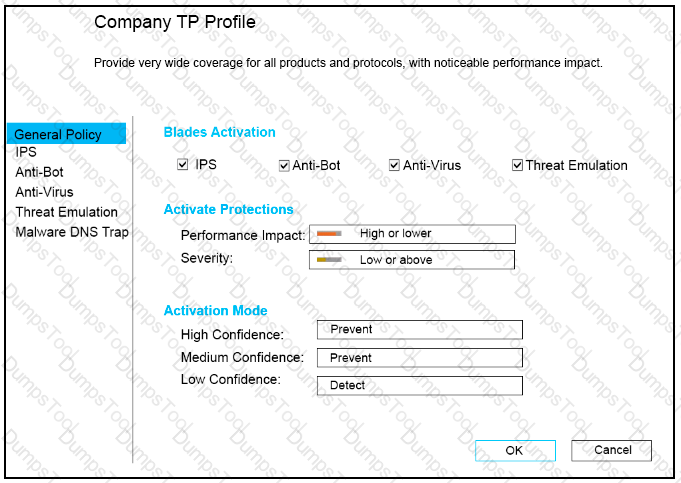
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Fill in the blank: With the User Directory Software Blade, you can create user definitions on a(n) ___________ Server.
Which Identity Source(s) should be selected in Identity Awareness for when there is a requirement for a higher level of security for sensitive servers?
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server?
Which product correlates logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
An administrator can use section titles to more easily navigate between large rule bases. Which of these statements is FALSE?
In a Distributed deployment, the Security Gateway and the Security Management software are installed on what platforms?
Identity Awareness allows easy configuration for network access and auditing based on what three items?
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
Which Check Point supported authentication scheme typically requires a user to possess a token?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Please choose correct command syntax to add an “emailserver1” host with IP address 10.50.23.90 using GAiA management CLI?
Which one of the following is the preferred licensing model? Select the BEST answer