An architect is designing a vSphere environment for a customer based on the following information:
Which two recommendations can the architect make so that the customer achieves the highest level of
application availability while taking into consideration operational resiliency? (Choose two.)
An architect is tasked with recommending a solution for a company that is running out of VLANs. Currently the company is running two separate data centers based on vSphere including an Enterprise Plus license. In the first data center, the problem was solved by using VMware NSX and overlay network. In the second data center, there is currently no VMware NSX implementation in place and no budget for additional licenses.
What should the architect recommend as a potential solution to provide support for additional VLANs?
An organization’s data scientists are executing a plan to use machine learning (ML). They must have access to graphical processing unit (GPU) capabilities to execute their computational models when needed. The
solutions architect needs to design a solution to ensure that GPUs can be shared by multiple virtual machines.
Which two solutions should the architect recommend to meet these requirements? (Choose two.)
An architect makes the design decision to install ESXi on embedded and resilient 8 GB SD cards.
What is the impact of this design decision?
An architect is considering placement of virtual machines within an existing VMware software-defined data center (SDDC).
During the discovery phase, the following information is documented:

Which two recommendations should the architect make for placement of the virtual machines to meet resource profile requirements? (Choose two.)
Refer to the exhibit.
During a requirements gathering workshop, the customer shares the following diagram regarding their availability service-level agreements (SLAs):
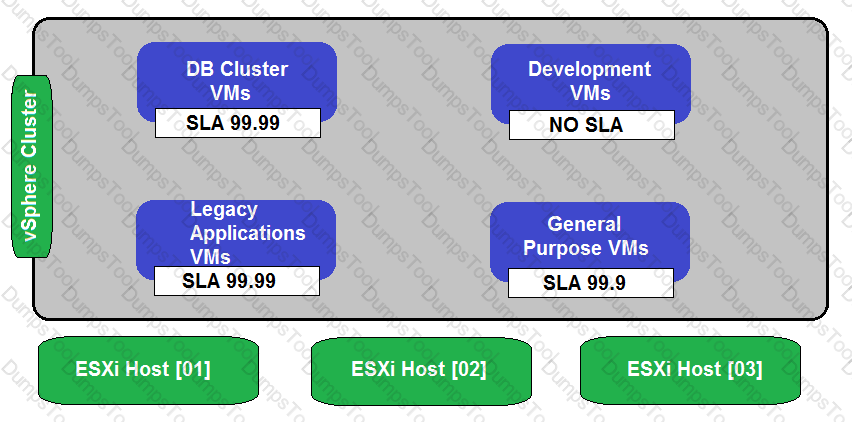
The customer wants database application level availability to always take precedence. What should the architect recommend to meet the customer’s requirement?
There is a request for approved virtual machine applications through a new vSphere platform’s integrated automation portal. The platform was built following all provided company security guidelines and has been assessed against Sarbanes-Oxley Act of 2002 (SOX) regulations.
The platform has the following characteristics:
There is a dedicated ESXi cluster for all line-of-business applications.
There is a dedicated ESXi cluster for virtual desktop infrastructure (VDI).
The application owner is requesting approval to install a new service that must be protected as per the Payment Card Industry (PCI) Data Security Standard.
Which additional non-functional requirement should the architect include in the design to support the new service?
In a meeting to discuss the minimum viable product (MVP) deployment of a new customer-facing application, the key stakeholder shares details of the application components and the application administrators share details of performance and integrity tests for the application.
The application will be made up of the following components:
-Steps to confirm the web server is operating correctly will take 15 minutes after the application server is online.
-Steps to confirm application server integrity will take 15 minutes after the database is online.
-The database server will be managed by a database administrator, with an agreed service-level agreement (SLA) to restore and validate database services within one hour.
The existing VMware infrastructure offers a recovery point objective (RPO) of 5 minutes and recovery time objective (RTO) of 15 minutes through a combination of backups and replication.
In the event of an outage impacting all three application components, how long will it take for the application to recover and complete all checks?
An architect is considering placement of virtual machines within an existing VMware software-defined data center (SDDC).
During the discovery phase, the following information is documented:
Cluster One
Cluster Two
Cluster Three
Virtual Machine Resource Profile 1
Virtual Machine Resource Profile 2
Which two recommendations should the architect make for placement of the virtual machines to meet resource profile requirements? (Choose two.)
The Chief Information Security Officer (CISO) for an organization is concerned about the security posture of the operating system images that are used for the provisioning of their Software-as-a-Service (SaaS) applications. The organization is in a growth period. The organization is opening a new data center to launch its next phase of new SaaS-based solutions.
The DevOps team currently creates encrypted virtual machine (VM) templates that are used for various operating systems and adds these to the vSphere inventory. The DevOps team already uses a published content library and has been granted a role with the ability to add and delete library items.
The following requirements have been noted:
Which three recommendations should the architect make to design a content library solution that will meet these requirements? (Choose three.)
An architect is designing a VMware solution for a customer to meet the following requirements:
Which design decision should the architect make to meet these requirements?
Application owners require support of a Microsoft Windows Server Failover Cluster (WSFC).
Their current environment consists of the following components:
The solution architect is tasked with coming up with a solution to meet this requirement while utilizing their existing investments.
Which two recommendations could the architect make? (Choose two.)
Which two of the listed requirements would be classified as manageability non-functional requirements? (Choose two.)
An architect has 50 ESXi hosts to deploy and DHCP servers are not allowed on any network. Which automated host deployment method should the architect use?
Which two of the listed requirements would be classified as performance non-functional requirements? (Choose two.)
An architect is designing a solution based on the following information:
Which recommendation for the configuration of vSphere High Availability (HA) should the architect include in the design?
An architect is designing a new vSphere platform to meet a list of requirements from the security team.
Which two requirements would be classified as non-functional requirements? (Choose two.)
An architect will be taking over control of a former Linux server fleet and repurposing the hardware into a new vSphere cluster. The current environment is already connected to the network but the hosts do not have any local disks. Since the fleet hardware is uniform, the architect can use a single ESXi image. All hosts within the cluster have the same CPU and memory capacity.
Which ESXi deployment method should the architect use?
An architect is designing a VMware software-defined data center (SDDC) solution based on the following customer requirements:
Which two assumptions could the architect make based on the information from the customer to help size the solution? (Choose two.)
Following a recent acquisition, an architect needs to merge IT assets into its current data center. The combined vSphere environment will need to run the newly acquired company’s virtual machines.
Network integration work has already been completed and the current environment has capacity to host all virtual machines. The Operations team needs to identify which virtual machines belong to the acquired company and report on their usage.
How should the architect merge the company’s assets and virtual machines?
An architect is tasked with designing a greenfield VMware software-defined data center (SDDC) solution that will be used to deliver a private cloud service for a customer.
During the initial meeting with the service owner and business sponsor, the customer has provided the following information to help inform the design:
Given the information from the customer, which two would be classified as assumptions within the design? (Choose two.)