What is an enhancement that Cisco IOS XE Software has over Cisco IOS Software?
Refer to the exhibit:
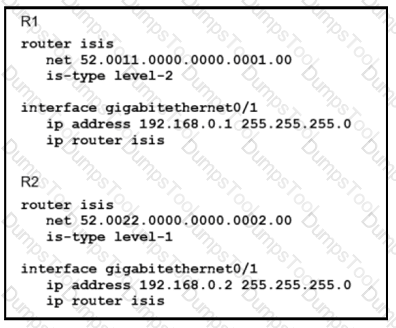
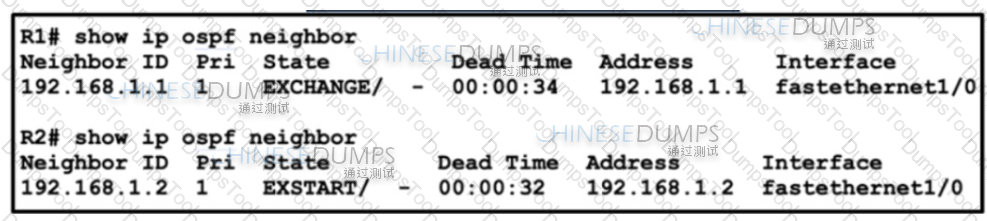
Which statement about the status of the neighbor relationship between R1 and R2 is true?
After a possible security breach, the network administrator of an ISP must verify the times that several different users logged into the network. Which command must the administrator enter to display the login time of each user that activated a session?
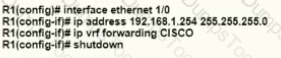
A network engineer is deploying VRF on ASBR router R1. The interface must have connectivity over an MPLS VPN inter-AS Option AB network. Which configuration must the engineer apply on the router to accomplish this task?
A)

B)
C)

D)

Which role does the Adjacency-SID sub-TLV extension perform in the IS-IS routing protocol?
Refer to the exhibit:

Which information is provided for traceback analysis when this configuration is applied?
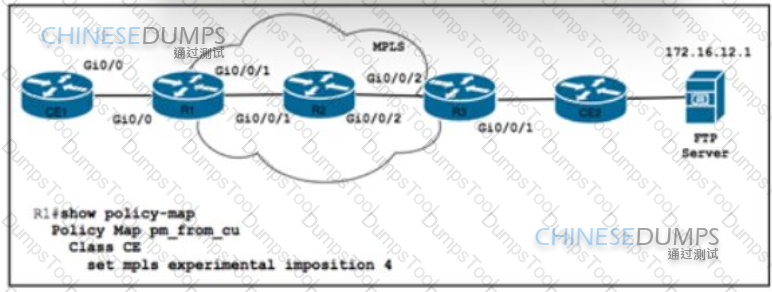
Refer to the exhibit. Router R1 is configured with class map CE with match Ip precedence critical to align with customer contract SLAs. The customer is sending all traffic from CE1 toward the FTP server with IP precedence 5 A network engineer must allow 10% of interface capacity on router R3 Which two actions must the engineer take to accomplish the task? (Choose two )
Which task must be performed first to Implement BFD in an IS-IS environment?
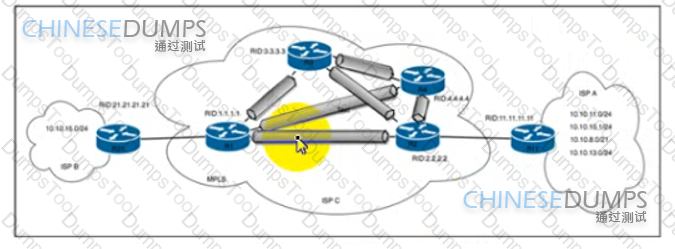
Refer to the exhibit An engineer at ISP C is configuring a new interconnection with ISPs A and B using the BGP protocol After the initial configuration the engineer noticed high memory usage and an abnormally large LIB table on router R2 Which two actions must the engineer take on R2 to minimize memory usage? (Choose two.)
A network engineer is implementing NetFlow to observe traffic patterns on the network. The engineer is planning to review the patterns to help plan future strategies for monitoring and preventing congestion as the network grows. If the captures must include BGP next-hop flows, which configuration must the engineer apply to the router?
Refer the exhibit.
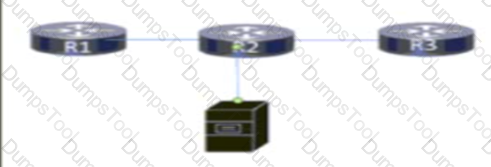
Users on a network connected to router R3 report slow speeds when they connect to the server connected to R2. After analyzing traffic on the network, a network engineer identified congestion on the link between R2 and R3 as the cause. Which QoS service must the engineer implement to drop traffic on the link when it exceeds a configured threshold?
Refer to the exhibit.
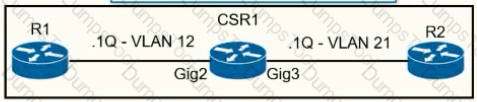
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
A)

B)
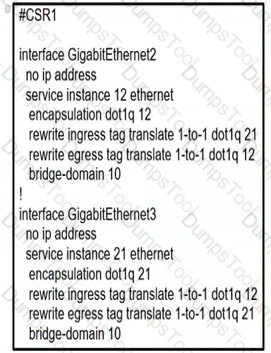
C)

D)

Refer to me exhibit.
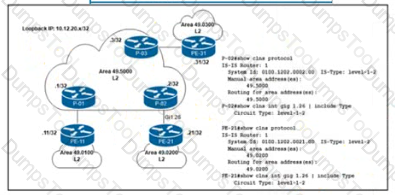
Refer to the exhibit. A network engineer notices PE-21 convergence degradation due to the growing LSDB size of Level 2 areas in the network. The engineer decides to migrate router PE-21 from an inter-area design to an intra-area implementation. Inter-area routing must be accomplished via an ATT-bit set by the Level 1/Level 2 router. Which configuration must the engineer implement on PE-21 to complete the migration?
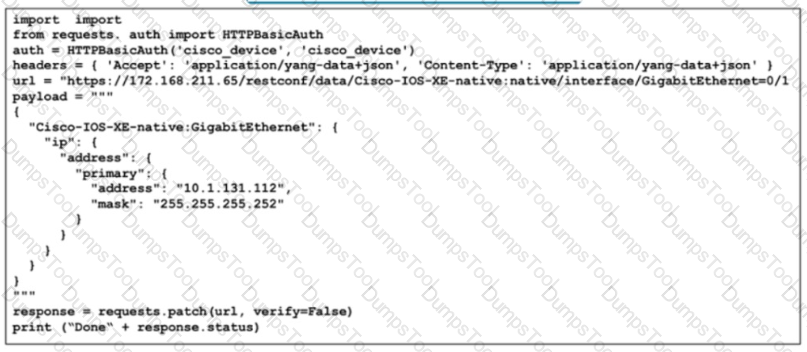
Refer for the exhibit. To optimize network operations, the senior architect created this Python 3.9 script for network automation tasks and to leverage Ansible 4.0 playbooks. Devices In the network support only RFC 2617-based authentication What does the script do?

Refer to the exhibit. A network engineer must configure XR-PE1 for uninterruptible failover from active RP to the standby RP Neither peer devices CGW1 nor the network of ASN 64512 support restart extensions Which configuration must the engineer apply to XR PEI to complete tasks?
A)

B)

C)

D)

A network engineer must enable the helper router to terminate the OSPF graceful restart process if it detects any changes in the LSA. Which command enables this feature?
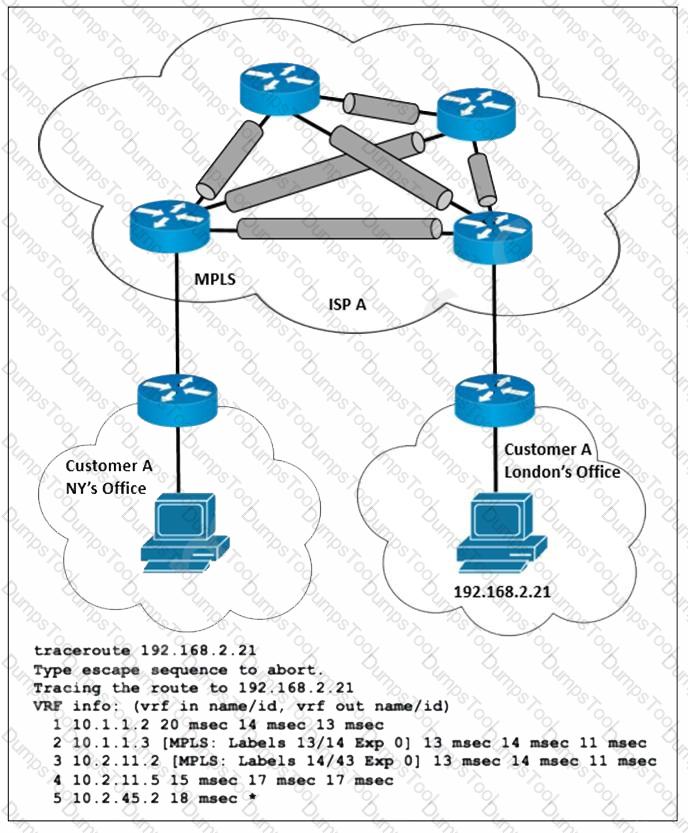
Refer to the exhibit. ISP A provides MPLS L3VPN service to customer A with BGP as the external routing protocol. Customer A has just opened a new branch office in London and requested the service provider to implement lossless service between its two offices. The LDP is enabled over the MPLS backbone and label exchange is working normally. Which action must the ISP engineering team take to enable the service?
Refer to the exhibit. A company recently deployed a new network using OSPF in the core to share routes. The network administrator selected OSPF as the routing protocol because of its ability to maintain a route database. When the new network was started up, all routers booted normally, but the link between routers R1 and R2 failed to come up. The two routers are located in the same rack at the data center. Which task should an engineer perform to correct the problem?
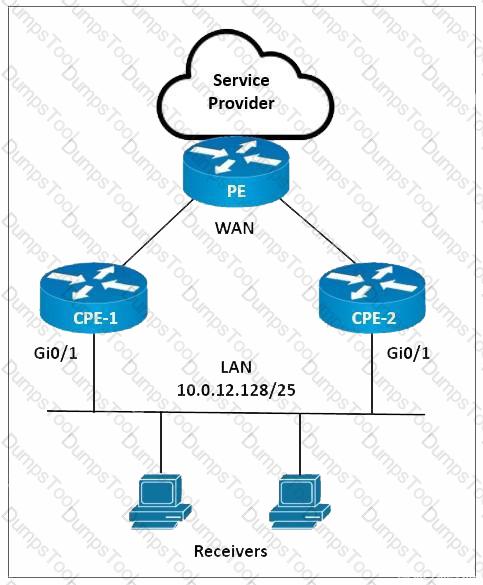
Refer to the exhibit. A network engineer is implementing multicast services on CPE-1 and CPE-2. CPE-1 must be configured as the preferred IGMP querier for the LAN segment. PIM-SM must be implemented on the LAN interfaces with an IGMP version that supports (*, G) joins only. Which configurations must the engineer implement on CPE-1 and CPE-2?
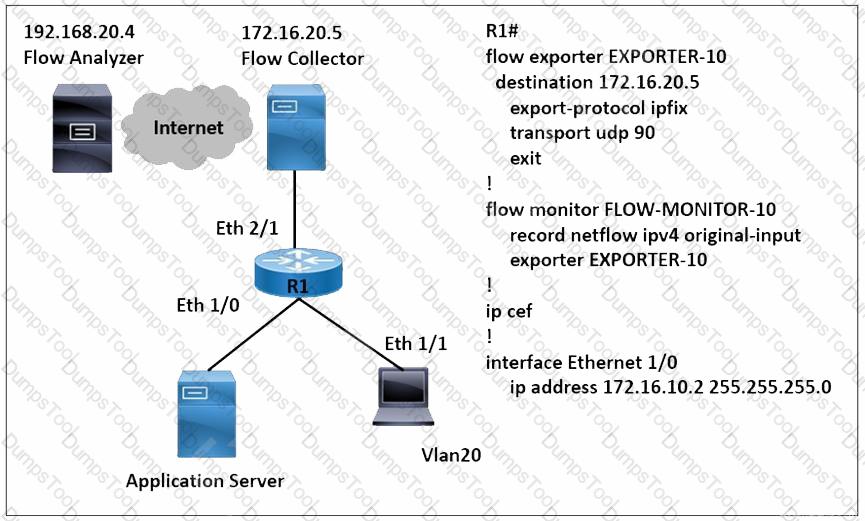
Refer to the exhibit. A network engineer wants to monitor traffic from the application server and send the output to the external monitoring device at 172.16.20.5. Application server traffic should pass through the R1 Eth2/1 interface for further analysis after it is monitored. Which configuration must be applied on the R1 router?
Refer to the exhibit. An organization s network recently experienced several significant outages due to device failures. The network administrator just moved the network devices to a new central data center, and packets are switched using labels. The administrator Is now implementing NSF on the network to reduce potential risk factors in the event of another outage. Which task must the administrator perform on each router as part of the process?
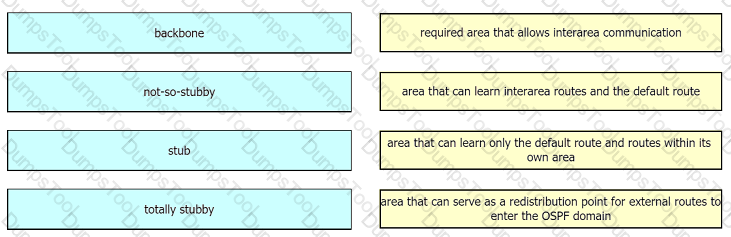
Drag and drop the OSPF area types from the left onto the correct statements on the right
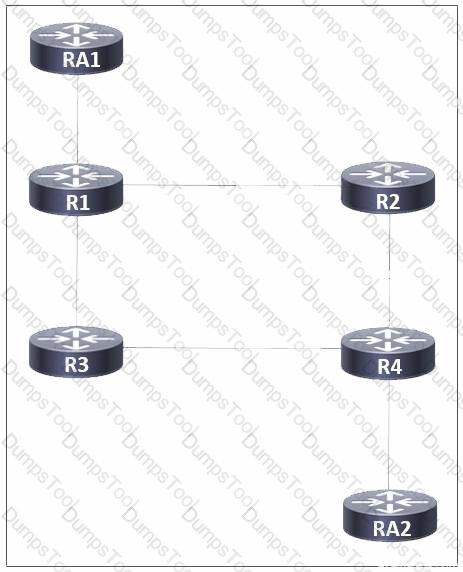
Refer to the exhibit. A network administrator implemented MPLS routing between routers R1, R2, R3, and R4. AToM is configured between R1 and R4 to allow Layer 2 traffic from hosts on RA1 and RA2. A targeted MPLS session is established between R1 and R4. Which additional action must the administrator take on all routers so that LDP synchronization occurs between connected LDP sessions?
Refer to the exhibit.
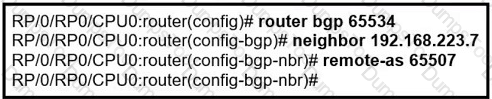
An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
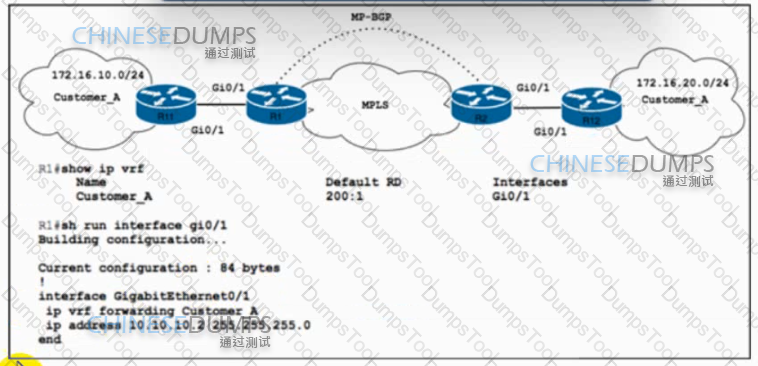
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A 172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?
An engineer Is implementing NSR with OSPF on a large campus that requires high availability. Which task must an engineer perform to complete the process with minimal disruption to traffic?
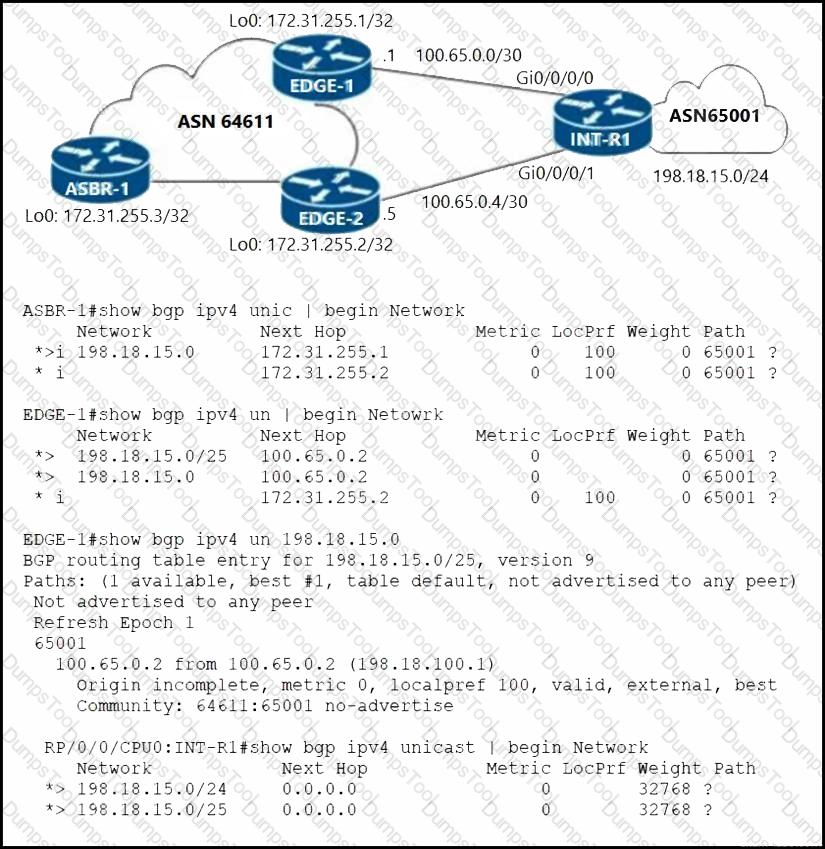
Refer to the exhibit. The network engineer who manages ASN 65001 is troubleshooting suboptimal routing to the 198.18.15.0/24 prefix. According to the network requirements:
Routing to IP destinations in the 198.18.15.0/25 block must be preferred via the EDGE-1 PE.
Routing to IP destinations in the 198.18.15.128/25 block must be preferred via the EDGE-2 PE.
More specific prefixes of the 198.18.15.0/24 block must not be advertised beyond the boundaries of ASN 64611.
Routing to 198.18.15.0/24 must be redundant in case one of the uplinks on INT-R1 fails.
Which configuration must the network engineer implement on INT-R1 to correct the suboptimal routing and fix the issue?
Refer to the exhibit:
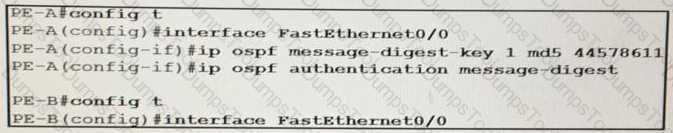
An engineer wants to authenticate the OSPF neighbor between PEA and PE-B using MD5.
Which command on PE-B successfully completes the configuration?
A)

B)

C)

D)

Refer to the exhibit.
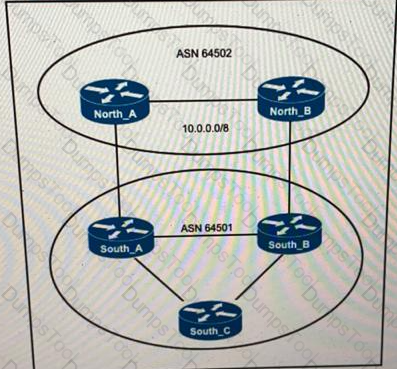
ASN 64501 currently reaches the networks under the 10.0.0.0/8 prefix via the North_B router, which is a slow backup link. The administrator of ASN 64502 wants traffic from ASN 64501 to 10.0.0.0/8 to travel via the primary link North_A. Which change to the network configuration accomplishes this task?
Refer to the exhibits:
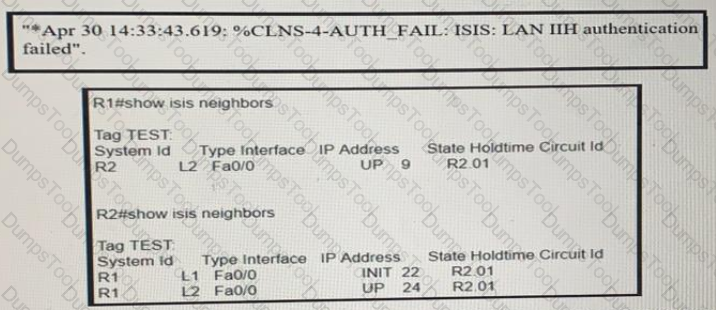
R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2 R1 message periodically Based on this output, which statement is true?
Refer to the exhibit.
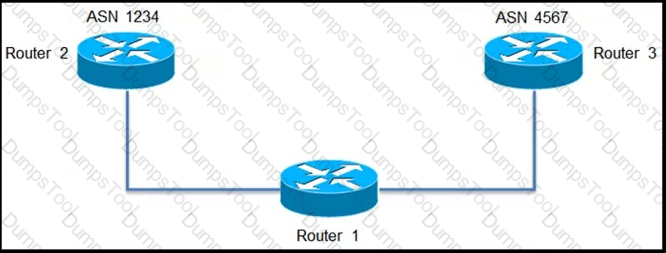
An engineer is configuring path selection on router R1 for two ASNs as shown. Which additional task must the engineer perform on Router 1 so that all outbound traffic utilizes the link between R1 and R3 to reach ASN 4567?
Refer to the exhibit.

An engineer ran this show telemetry command to view subscription SUB11 on RouterX. The engineer then decided that RouterY should provide the same output lor sensor group SGroup13 as RouterX. The engineer cannot access RouterX to copy its configuration No access lists on the router block user access Which configuration must the engineer apply on RouterY to provide the same output from the show telemetry command?
A)

B)

C)

D)

A customer site is being connected to a Frame Relay network via a T1 link. The customer has a contract for 512 kbps service with a Tc value of 125 ms. Under peak line conditions, customer traffic can reach four times the contracted speed. Which QoS configuration must the service provider implement to limit the customer to the contracted values?


Refer to the exhibit. An engineer started to configure a router for OSPF. Which configuration must the engineer perform on the router without changing any interface configuration so that the router establishes an OSPF neighbor relationship with its peer?
Refer to the exhibit:
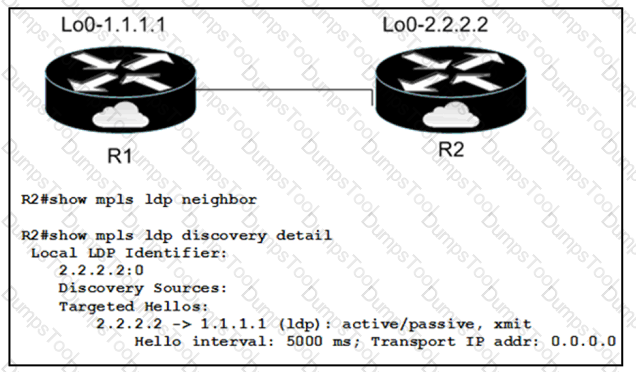
When implementing an LDP protocol, an engineer experienced an issue between two directly connected routers and noticed that no LDP neighbor exists for 1.1.1.1.
Which factor should be the reason for this situation?
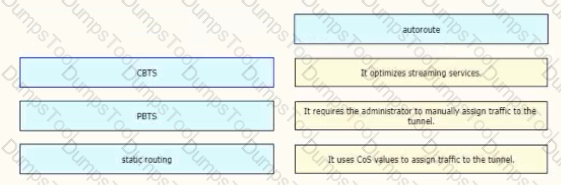
Drag and drop the methods of Cisco MPLS TE tunnel traffic assignment from the left onto their characteristics on the right.
Refer to the exhibit.
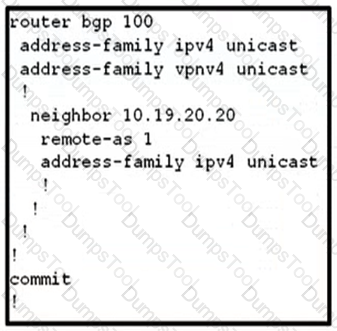
An engineer is trying to implement BGP configuration on a router Which configuration error prevents the ASBR from establishing a BGP neighborship to a directly connected BGP speaker?
An engineer working for a private telecommunication company with an employe id:3948:613 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
A)

B)

C)

D)

Refer to the exhibit.
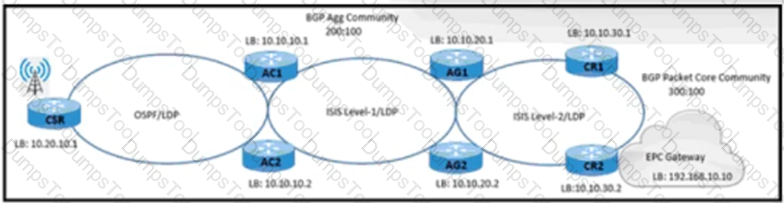
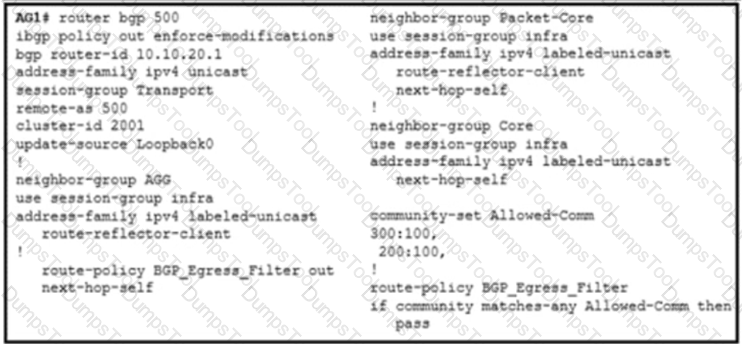
A NOC engineer is configuring label-based forwarding from CSR to the EPC gateway. Cell-site operation and maintenance for IPv4 traffic between 10.20.10.1 and 192.168.10.10 is already up. CR1 and CR2 are configured as route reflectors for AG1 and AG2. Which action completes the configuration?
Refer to Exhibit.
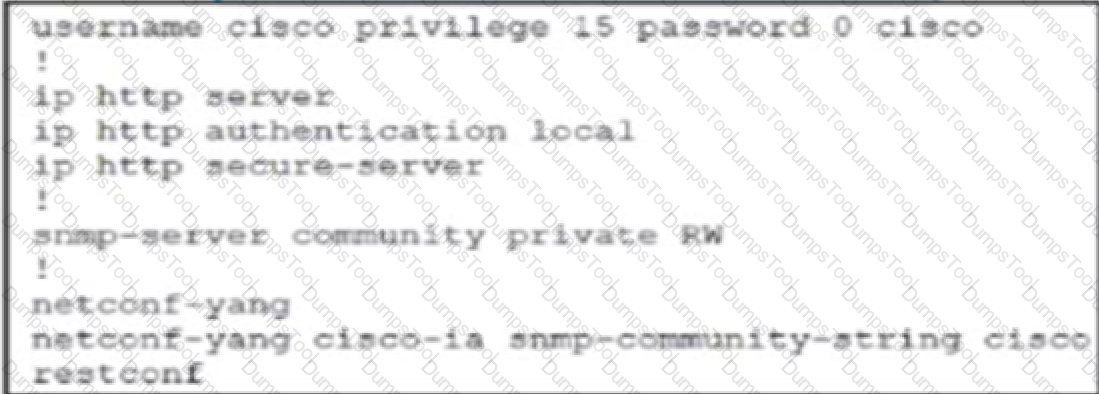
A network engineer is trying to retrieve SNMP MIBs with RESTCONF on the Cisco switch but fails. End-to-end routing is in place. Which configuration must the engineer implement on the switch to complete?
An engineer is trying to implement BGP in a multihomed architecture. What must the engineer configure to influence inbound path selection?
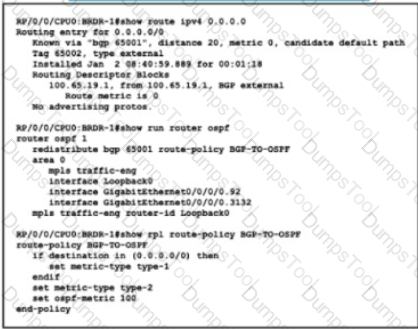
Refer to the exhibit. Router BRDR-1 is configured to receive the 0.0.0.0/0 and 172.17.1.0/24 network via BGP and advertise then into OSPF area 0. An engineer has noticed that the OSPF domain is receiving only the 172.17.1.0/24 route and default router 0.0.0.0/0 is still missing. Which configuration must an engineer apply to resolve this problem?

Which regular expression query modifier function indicates the start of a string?
A network architect plans to implement MPLS OAM to provide additional troubleshooting functionality for the NOC team. After analyzing the configuration on the MPLS P/PE nodes, the architect decides to revise the CoPP policies. Which two actions ensure that the new solution is secure? (Choose two.)
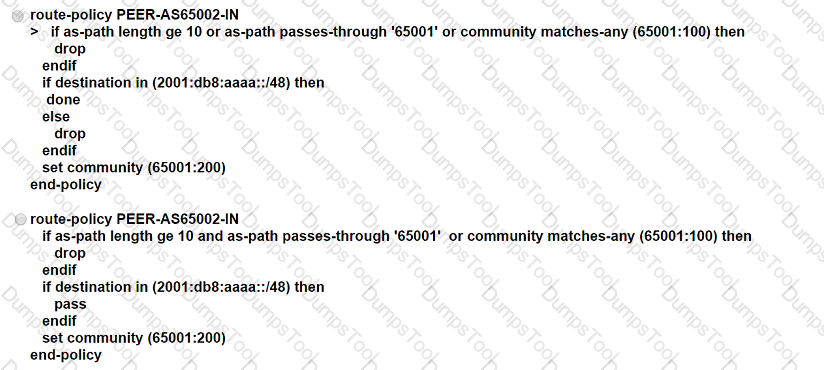
ASN 65001 is peering with ASN 65002 to exchange IPv6 BGP routes. All routes that originate in ASN 65001 have a standard community value of 65001:100, and ASN 65002 is allowed to advertise only 2001 :db8:aaaa::/48. An engineer needs to update the ASN 65001 route-filtering configuration to meet these conditions:
* Looped routes into ASN 65001 and routes that have traversed 10 or more ASNs must be denied.
* Routes accepted into ASN 65001 must be assigned a community value of 65001:200.
Which configuration must the engineer apply to the ASN 65001 border router?
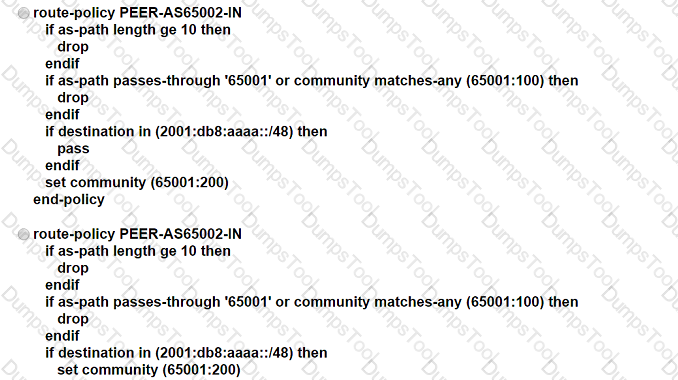
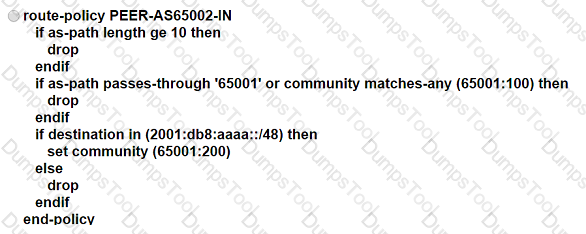
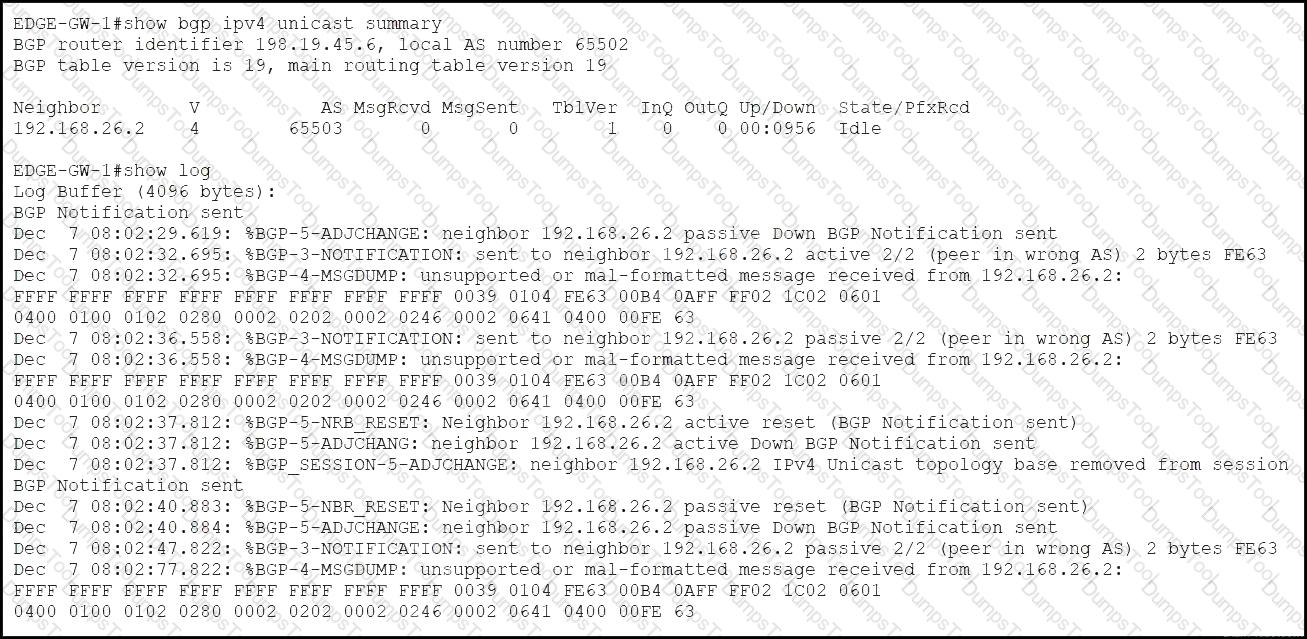
Refer to the exhibit. A network support engineer for ASN 65502 receives a technical support ticket from a customer in ASN 65503 who reports that an eBGP session is down. The engineer determines that the peering failed after a recent change to the device at 192.168.26.2. EDGE-GW-1 must establish an eBGP session with the peering router 192.168.26.2. Which configuration establishes this session?
Refer to the exhibit.
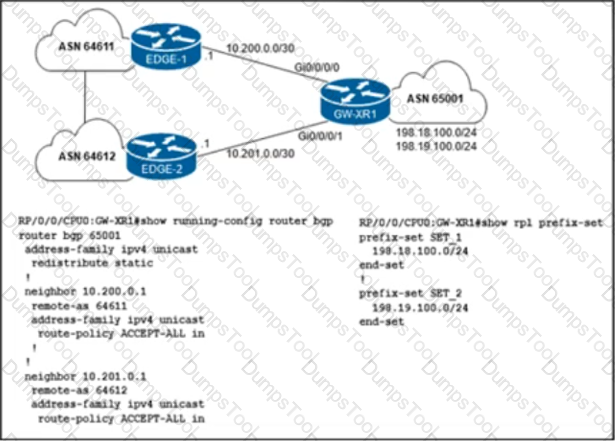
The network engineer who manages ASN 65001 must configure a BGP routing policy on GW-XR1 with these requirements:
• Advertise locally-originated routes and /24 prefixes assigned within the 198.18.0.0/15 range. All other prefixes must be dropped.
• Reachability to 198.18.100.0/24 must be preferred via the EDGE-1 connection.
• Reachability to 198.19.100.0/24 must be preferred via the EDGE-2 connection.
Which configuration must the network engineer implement on GW-XR1?
An engineer a cisco MPLS tunnel to improve the streaming experience for the clients of a video -on-demand server. Which action must the engineer perform to configure extended discovery to support the MPLS LDP session between the headend and tailend routers?

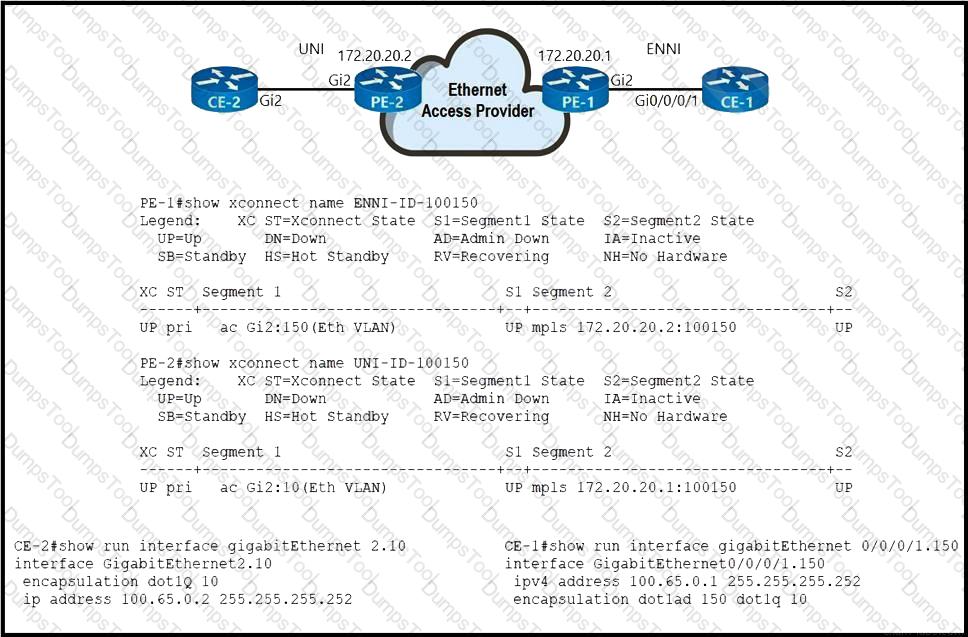
Refer to the exhibit. An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
Which is the benefit of implementing model-driven telemetry in a service provider environment?
Refer to the exhibit.
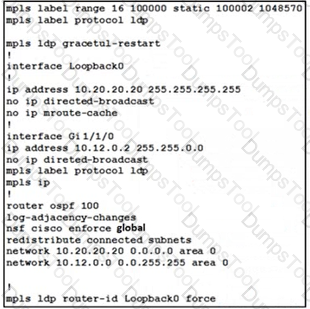
A network administrator implemented MPLS LDP changes on PE-A LSR device. The engineer must ensure there are no LDP peer are fully operational. Which LDP feature must the engineer apply to the existing configuration to eliminate the problem?
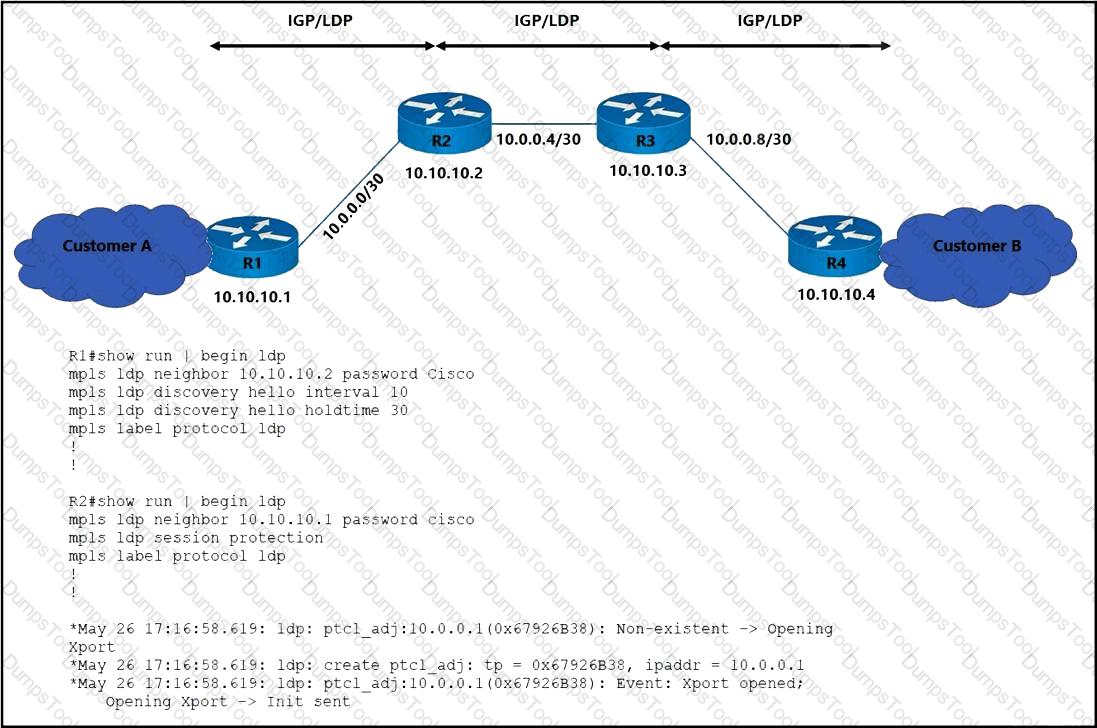
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service provider core network with these requirements:
R1 must establish LDP peering with the loopback IP address as its Router-ID.
Session protection must be enabled on R2.
How must the team update the network configuration to successfully enable LDP peering between R1 and R2?
A regional MPLS VPN provider operates m two regions and wants to provide MPLS L 3VPN service for a customer with two sites in these separate locations. The VPN provider approaches another organization to provide backbone carrier services so that the provider can connect to these two locations.
Which statement about this scenario is true?
Refer to the exhibit.

An engineer has started to configure a router for secure remote access as shown. All users who require network access need to be authenticated by the SSH Protocol.Which two actions must the engineer implement to complete the SSH configuration? (Choose two.)
Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
Which programmable API allows the service provider to plan and optimize the automation of network operations and achieve closed-loop operations?
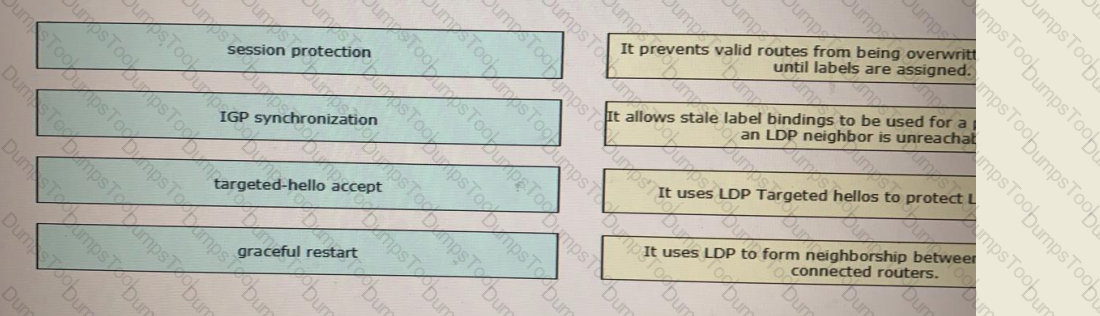
Drag and drop the LDP features from the left onto their usages on the right.

Drag and drop the functionalities from the left onto the target fields on the right.
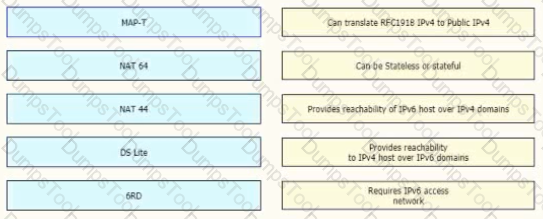
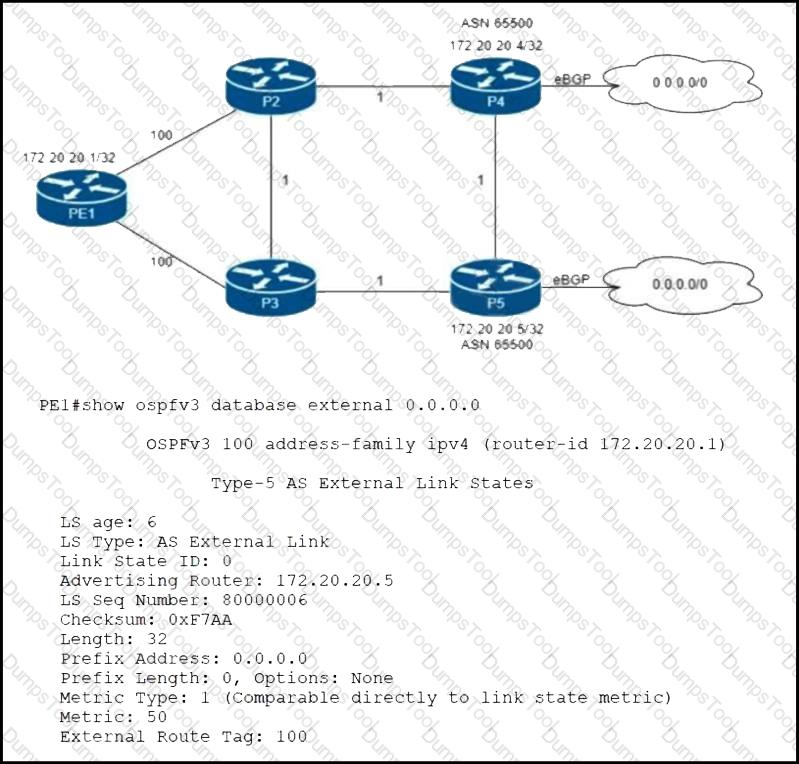
Refer to the exhibit. Routers P4 and P5 receive the 0.0.0.0/0 route from the ISP via eBGP peering. P4 is the primary Internet gateway router, and P5 is its backup. P5 is already advertising a default route into the OSPF domain. Which configuration must be applied to P4 so that it advertises a default route into OSPF and becomes the primary Internet gateway for the network?
Refer to the exhibit.

AN engineer is configuring segment routing on an ISP to simplify traffic engineering and management across network domains. What should the engineer do to complete the implementation of segment routing?
Egress PE NAT is being used via a single centralized router to provide Internet access to L3VPN customers.
Which description of the NAT operation is true?
FRR is configured on a network. What occurs when the headend router on the path is alerted to a link failure over IGP?
Refer to the exhibit:
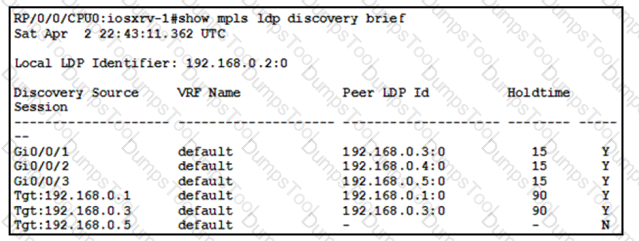
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
Drag and drop the functions from the path computation element protocol roles on the right.
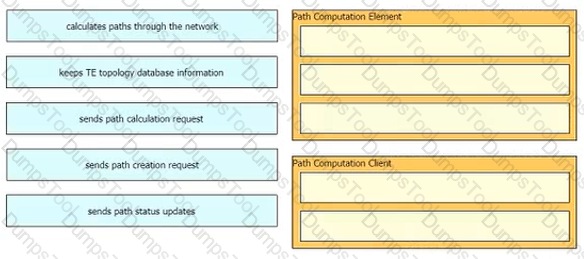
Drag and drop the LDP features from the left onto the correct usages on the right.
The service provider is serving hosts with two different multicast streams from source X and source Y. Source X is multicast group 224.0.0.0/8, and source Y is multicast group 226.0.0.0/8. Multicast source X should send its stream through bidirectional RP address 10.20.1.1, and multicast source Y should send its stream through RP address 10.20.2.1. Which configuration meets these requirements?
Which two tasks must an engineer perform when implementing LDP NSF on the network? (Choose two.)
Which two tasks must you perform when you implement LDP NSF on your network? (Choose two.)
Refer to the exhibit.
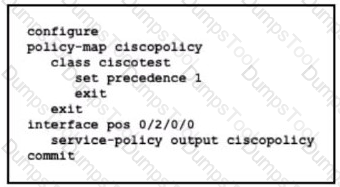
An engineer needs to implement this QoS policy on customer's network due to ongoing slow network issues. What will be the effect on the network when the engineer implements this configuration?
Refer to the exhibit.

An engineer is configuring multitiopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to complete the task?
A)

B)

C)

D)

Refer to the exhibit.
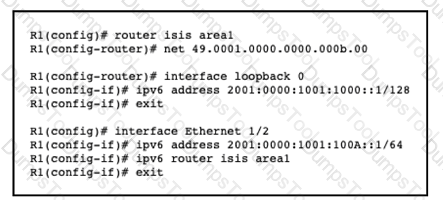
A network engineer with an employee id: 3812:12:993 has started to configure router R1 for IS-IS as shown. Which additional configuration must be applied to configure the IS-IS instance to advertise only network prefixes associated to passive interfaces?

Refer to the exhibit:
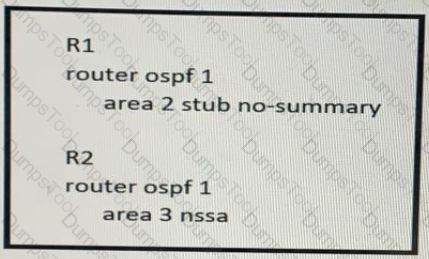
In which way does router R1 operate differently than router R2?
A router is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization to a neighbor to establish an LDP session? (Choose three)
Refer to the exhibit.

Router 1 and router 2 are running OSPF Area 0. The router logs on both routers show that the LDP link has flapped. Which configuration must the engineer apply to the two routers to implement session protection on the link?

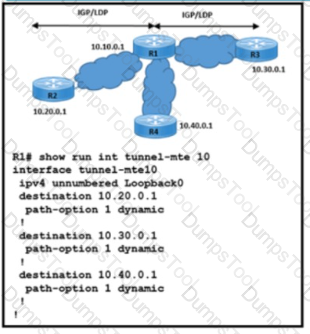
Refer to the exhibit. An engineer must Implement a traceroute operation to verity the R1 point-to-multipoint LSP connections. The traceroute operation must return all labels and hop-by-hop IP addresses for destinations 10.20.0.1. 10.30.0.1, and 10.40.0.1. and the maximum number of hops is 4. Which command must be executed to meet the requirements?
Refer to the exhibit:
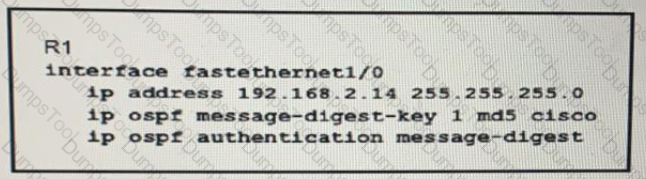
Which condition must be met by the OSPF peer of router R1 before the two devices can establish communication?
Refer to me exhibit.
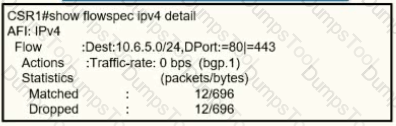
A network operator recently configured BGP FlowSpec for me internal IT network What will be inferred from the configuration deployed on me network?
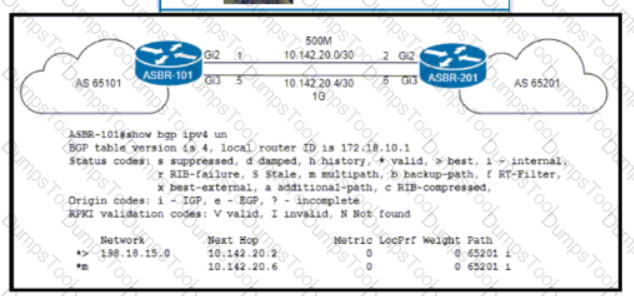
Refer to the exhibit an engineer working for a private telecommunication company with an employee Id: 4065:96:080 upgrades the WAN link between routers ASBR-101 and ASBR-201 to 1Gb by Installing a new physical connection between the Gi3 Interfaces. Which BGP attribute must the engineer configure on ASBR-201 so that the existing WAN link on Gi2 Is maintained as a backup?
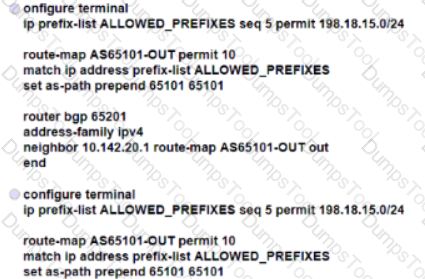
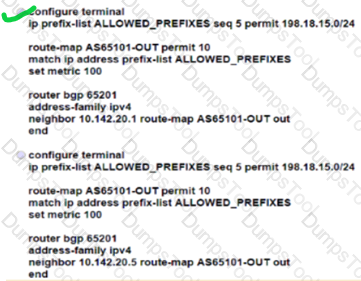
The NOC team must update the BGP forwarding configuration on the network with these requirements:
BGP peers must establish a neighborship with NSF capability and restart the session for the capability to be exchanged after 120 seconds.
BGP peers must delete routes after 360 seconds of inactivity.
Which action meets these requirements?
Refer to the exhibit.
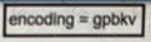
An engineer applied a gRPC dial-in configuration on customer's router to provide connection multiplexing and two-way streaming. What does this configuration accomplish in a gRPC?
Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
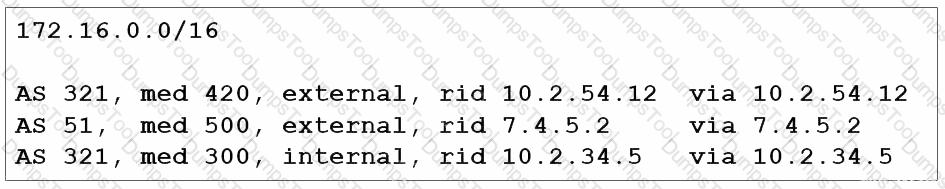
Refer to the exhibit. Tier 2 ISP A on AS 653 is connected to two Tier 1 ISPs on AS 321 and AS 51 respectively. The network architect at ISP A is planning traffic flow inside the network to provide predictable network services. Cisco Express Forwarding is disabled on the edge router. How should the architect implement BGP to direct all traffic via the Tier 1 ISP with next-hop 7.4.5.2?
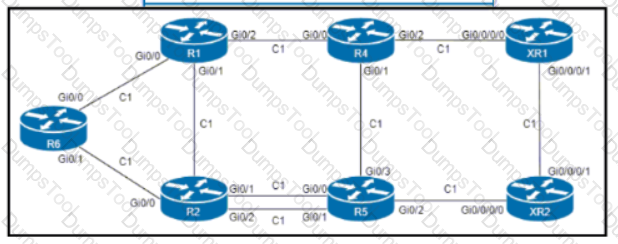
Refer to the exhibit. An engineer configured R6 as the headend LSR of an RSVP-TE LSP to router XR2, with the dynamic path signaled as R6-R2-R5-XR2. and set the OSPF cost of all links to 1. MPLS autotunnel backup Is enabled on all routers to protect the LSP. Which two NNHOP backup tunnels should the engineer use to complete the implementation? (Choose two.)
Refer to the exhibit:
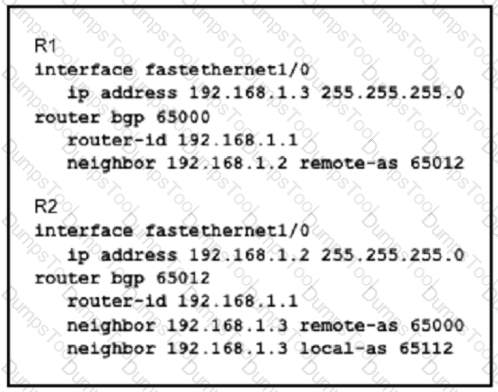
Assume all other configurations are correct and the network is otherwise operating normally. Which conclusion can you draw about the neighbor relationship between routers R1 and R2?
Refer to the exhibit:
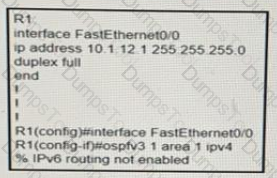
A network engineer is implementing an OSPF configuration Based on the output, which statement is true?
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
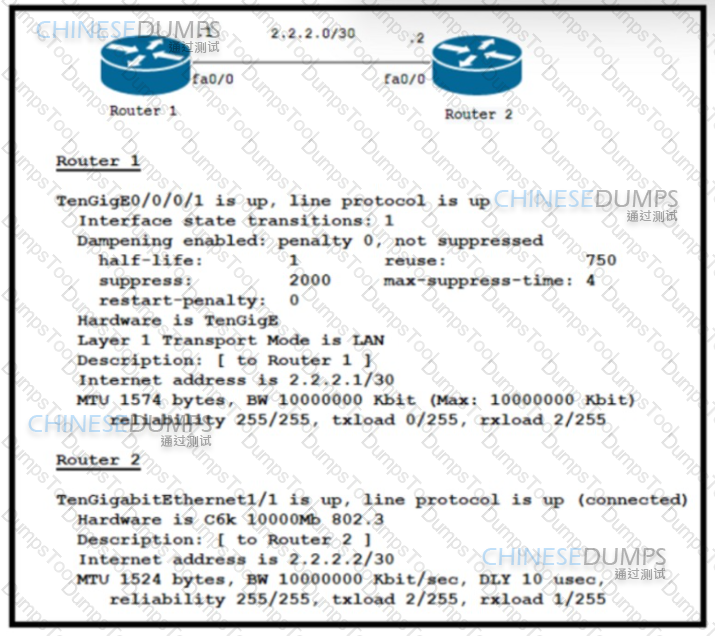
Refer to the exhibit. Router 1 and Router 2 were installed in the data center. Router 1 is the core router in the network, but it fails to establish an OSPF peering with Router 2. and customer traffic is unable to pass. Router 1 also reports an increase in CPU and memory usage. However, the CPU for R2 is stable. Which action resolves this issue?
Refer to the exhibit.
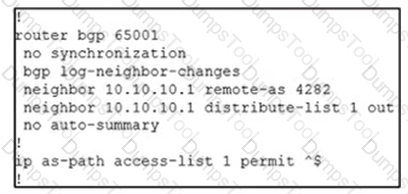
An engineer is reviewing the BGP configuration. Which routes must be advertised to 10.10.10.1
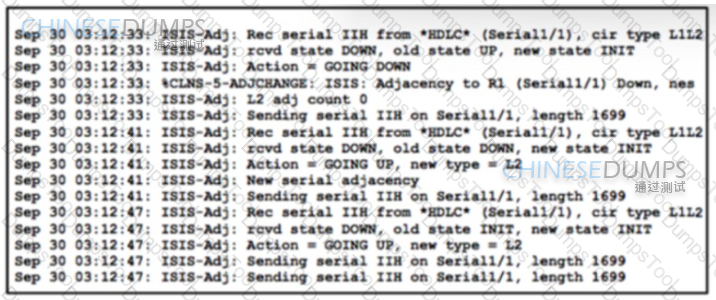
Refer to the exhibit Routers R1 and R2 are connected via a señal link and use the IS-IS routing protocol for route exchange After a configuration change on R2. IS-IS connectivity is interrupted A network engineer confirmed that the interfaces are in the UP state and connectivity exists between the two routers. Which two actions must the engineer perform to resolve the problem? (Choose two.)
An engineer must implement QoS to prioritize traffic that requires better service throughout the network. The engineer started by configuring a class map to identify the high-priority traffic. Which additional tasks must the engineer perform to implement the new QoS policy?
What causes multicast traffic to permanently stay on the shared tree and not switch to the source tree?
Refer to the exhibit.
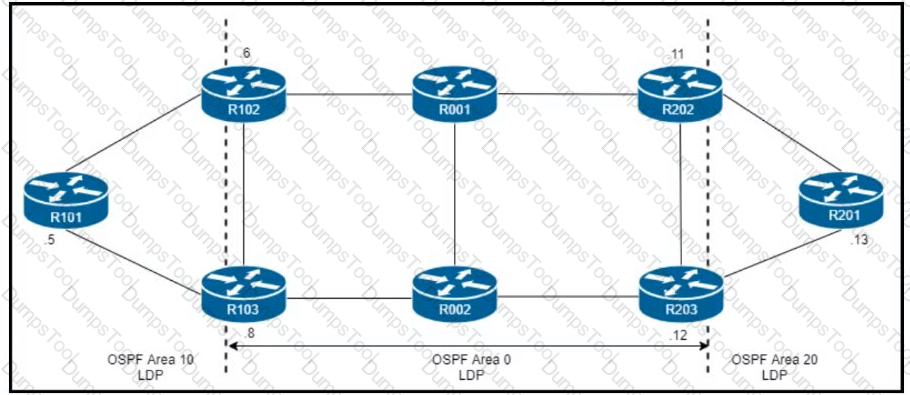
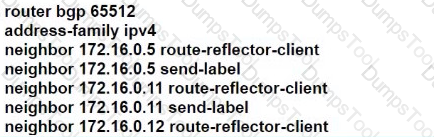
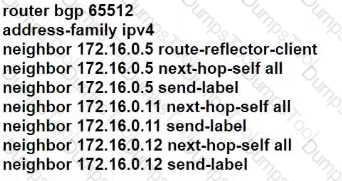
R101 is peering with R102 and R103, and R201 is peering with R202 and R203 using iBGP Labeled Unicast address families. The OSPF area 0 border routers are in a full iBGP Labeled Unicast mesh, and VPNv4 routes are exchanged directly between PE routers R101 and R201 through iBGP Which address family-level configuration must be applied on ABR R102 on ABR R102 to support a Unified MPLS routing architecture with partitioned IGP domains?
A)
B)
C)
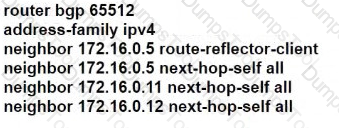
D)
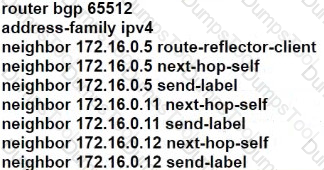
Refer to the exhibit.

To protect in-band management access to CPE-R7, an engineer wants to allow only SSH management and provisioning traffic from management network 192.168.0.0/16. Which infrastructure ACL change must be applied to router PE-R9 to complete this task?
A)

B)

C)

D)

Refer to the exhibit.
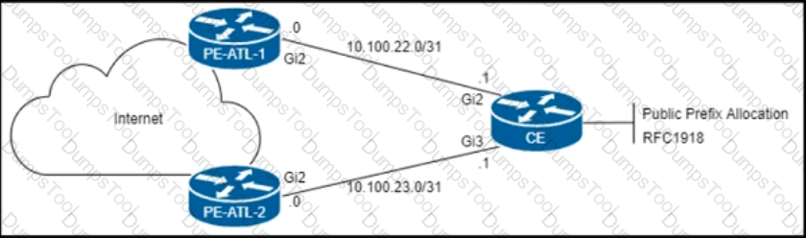
The CE router is peering with both PE routers and advertising a public prefix to the internet. Routing to and from this prefix will be asymmetric under certain network conditions, but packets must not be discarded. Which configuration must an engineer apply to the two PE routers so that they validate reverse packet forwarding for packets entering their Gi2 interfaces and drop traffic from the RFC1918 space?
Refer to the exhibit.
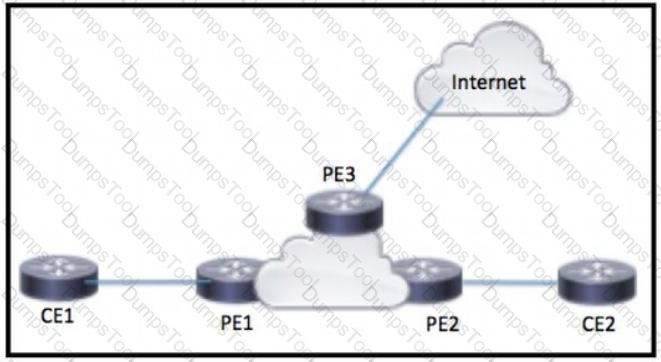
CE1 and CE2 require connectivity to the internet through the ISP connected to PE3 What should an engineer configure to complete this task?
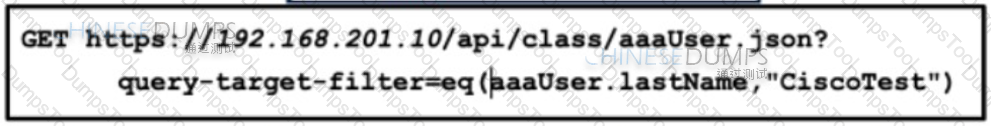
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
A network engineer is configuring RIP as the routing protocol between multiple PEs and CEs. The engineer must avoid advertising the same routes back to their sources. Which action should be performed on the routers to accomplish this task?
Refer to the exhibit:
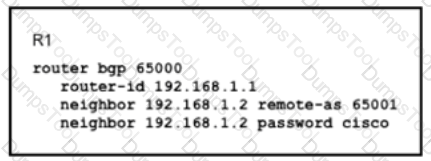
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27
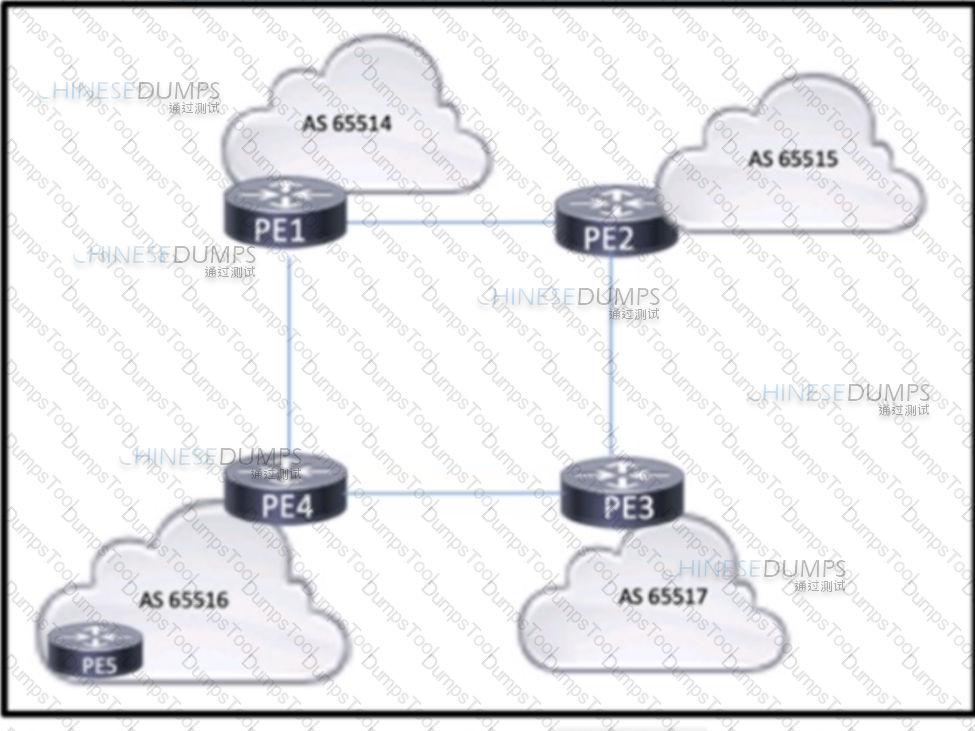
Refer to the exhibit. Four midsize service providers provide access to different customers that use Layer 3 VPN services to enable communication across geographic regions. The service providers are connected as shown in the exhibit, and the PEs have established eBGP relationships. PE4 has an IBGP relationship with PE5. The routes that PE4 learns from PE5 must reach the other PE routers, but they are absent from the routing tables on the other PES. Which action should the engineers take to correct the problem?
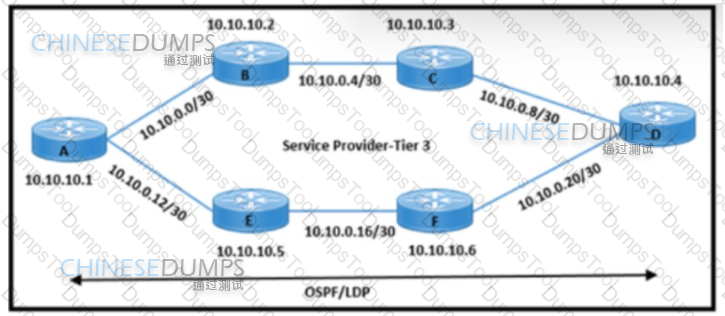
Refer to the exhibit. An engineering team must update the network configuration so that data traffic from router A to router D continues in case of a network outage between routers B and C. During a recent outage on the B-C link, the IGP traffic path was switched to the alternate path via routers E and F. but label forwarding did not occur on the new path. Which action ensures that traffic on the end-to-end path continues?
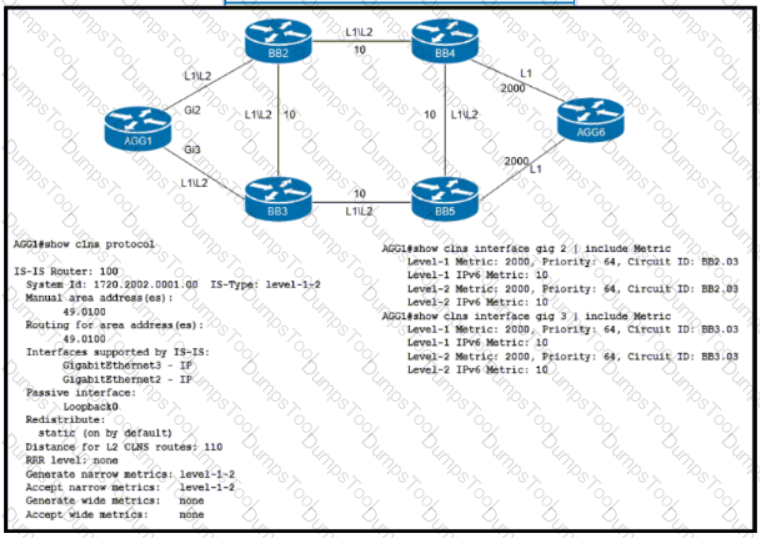
Refer to the exhibit. An engineer is configuring IS-IS on ISP network. Which IS-IS configuration must an engineer implement on router AGG1 so that it establishes connectivity to router AGG6 via the BB3 core router?
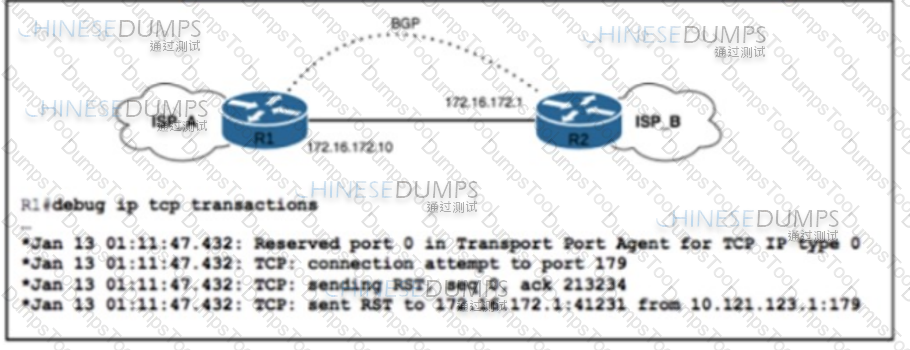
Refer to the exhibit. ISP_A and ISP_B use AS numbers 38321 and 16213 respectively. After a network engineer reloaded router R1, the BGP session with R2 failed to establish. The engineer confirmed BGP next-hop availability with a connectivity test between the router loopback addresses 10.121.123.2 and 10.121.123.1, as well as between interfaces Gi1/1 and Gi1/2. EBGP multihop has been configured on both routers. Which action must the engineer take to resolve the issue?
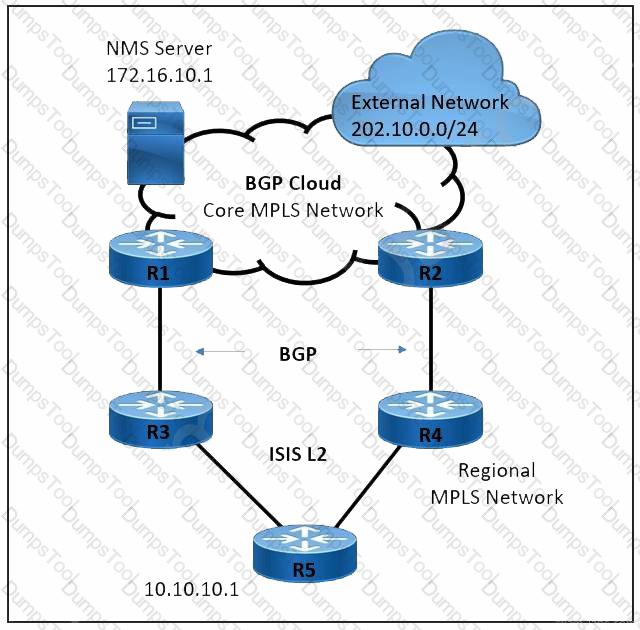
Refer to the exhibit. A large service provider is migrating device management from Layer 2 VLAN-based to Layer 3 IP-based solution. An engineer must configure the ISIS solution with these requirements:
Network management server IP 172.16.10.1 must be advertised from the core MPLS network to the regional domain.
The external network 202.10.0.0/24 must not establish ISIS peering with the R5 router.
The regional network must prevent sending unnecessary hello packets and flooding the routing tables of the R5 router.
Which two ISIS parameters must be implemented to meet these requirements? (Choose two.)
A network operator working for a private outsourcing company with an employee id: 4261:72:778 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
Refer to the exhibit:

This output is included at the end of an output that was provided by a device using NETCONF.
What does the code show?
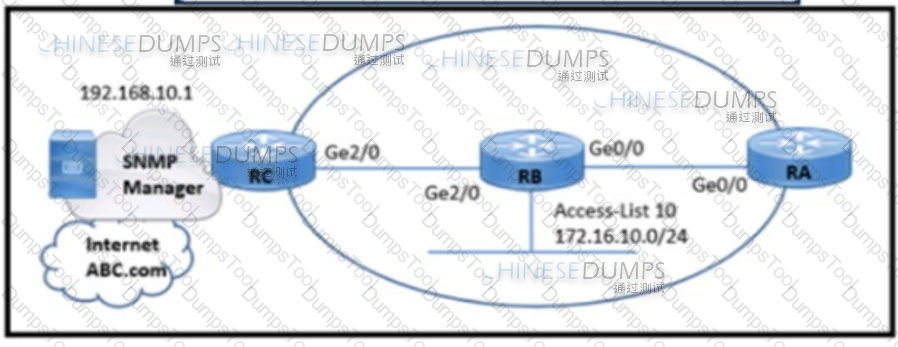
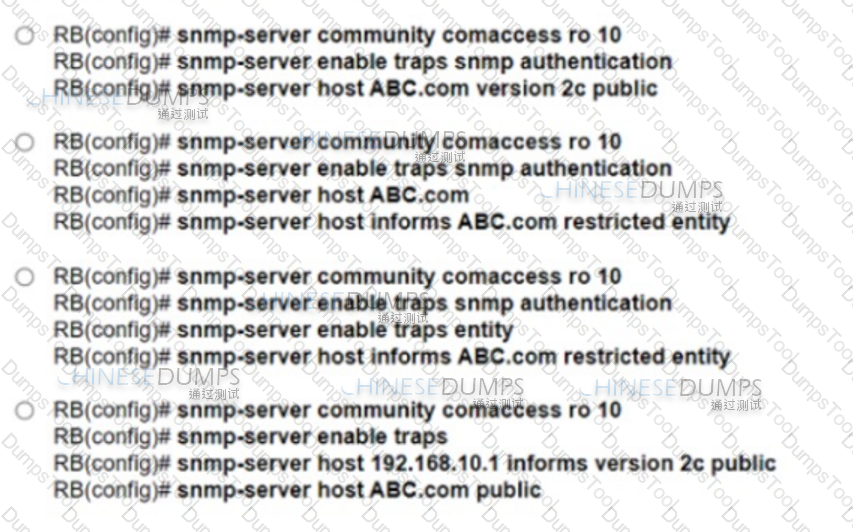
Refer to the exhibit. A network engineer is configuring an SNMP community on router RB with these requirements:
Which configuration meets these requirements?