Which feature in Splunk allows Event Breaking, Timestamp extractions, and any advanced configurations
found in props.conf to be validated all through the UI?
Which option accurately describes the purpose of the HTTP Event Collector (HEC)?
Which Splunk component performs indexing and responds to search requests from the search head?
In a customer managed Splunk Enterprise environment, what is the endpoint URI used to collect data?
What hardware attribute would need to be changed to increase the number of simultaneous searches (ad-hoc and scheduled) on a single search head?
This file has been manually created on a universal forwarder
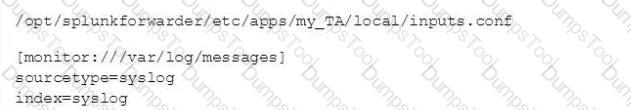
A new Splunk admin comes in and connects the universal forwarders to a deployment server and deploys the same app with a new
Which file is now monitored?
Which of the following are supported configuration methods to add inputs on a forwarder? (select all that apply)
In which scenario would a Splunk Administrator want to enable data integrity check when creating an index?
Which Splunk configuration file is used to enable data integrity checking?
When running a real-time search, search results are pulled from which Splunk component?
Which default Splunk role could be assigned to provide users with the following capabilities?
Create saved searches
Edit shared objects and alerts
Not allowed to create custom roles
In addition to single, non-clustered Splunk instances, what else can the deployment server push apps to?
The following stanzas in inputs. conf are currently being used by a deployment client:
[udp: //145.175.118.177:1001
Connection_host = dns
sourcetype = syslog
Which of the following statements is true of data that is received via this input?
Which of the following statements describe deployment management? (select all that apply)
When using license pools, volume allocations apply to which Splunk components?
A log file contains 193 days worth of timestamped events. Which monitor stanza would be used to collect data 45 days old and newer from that log file?
An organization wants to collect Windows performance data from a set of clients, however, installing Splunk
software on these clients is not allowed. What option is available to collect this data in Splunk Enterprise?
What event-processing pipelines are used to process data for indexing? (select all that apply)
What are the required stanza attributes when configuring the transforms. conf to manipulate or remove events?
Which feature of Splunk’s role configuration can be used to aggregate multiple roles intended for groups of
users?
In case of a conflict between a whitelist and a blacklist input setting, which one is used?
Which Splunk forwarder type allows parsing of data before forwarding to an indexer?
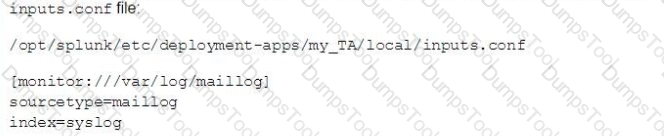
What are the values forhostandindexfor[stanza1]used by Splunk during index time, given the following configuration files?
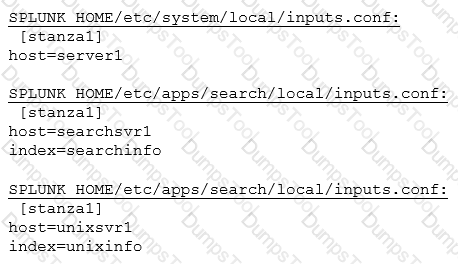
What is the correct curl to send multiple events through HTTP Event Collector?
Which Splunk indexer operating system platform is supported when sending logs from a Windows universal forwarder?
Which Splunk component(s) would break a stream of syslog inputs into individual events? (select all that apply)
Where can scripts for scripted inputs reside on the host file system? (select all that apply)
Which of the following must be done to define user permissions when integrating Splunk with LDAP?
A configuration file in a deployed app needs to be directly edited. Which steps would ensure a successful deployment to clients?
What is required when adding a native user to Splunk? (select all that apply)
What options are available when creating custom roles? (select all that apply)
Which of the following Splunk components require a separate installation package?
When configuring monitor inputs with whitelists or blacklists, what is the supported method of filtering the lists?
Which of the following are available input methods when adding a file input in Splunk Web? (Choose all that
apply.)
All search-time field extractions should be specified on which Splunk component?
Which of the following configuration files are used with a universal forwarder? (Choose all that apply.)
Which file will be matched for the following monitor stanza in inputs. conf?
[monitor: ///var/log/*/bar/*. txt]
Which configuration file would be used to forward the Splunk internal logs from a search head to the indexer?
Which of the following are reasons to create separate indexes? (Choose all that apply.)
Which of the following statements accurately describes using SSL to secure the feed from a forwarder?