Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
Which action would be applicable after enabling anomalous compute provisioning?
What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
If you are required to run in an air-gapped environment, which product should you install?
A manager informs the SOC that one or more RDS instances have been compromised and the SOC needs to make sure production RDS instances are NOT publicly accessible.
Which action should the SOC take to follow security best practices?
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
Given this information:
The Console is located at https://prisma-console.mydomain.local The username is: cluster
The password is: password123
The image to scan is: myimage:latest
Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
The security team wants to target a CNAF policy for specific running Containers. How should the administrator scope the policy to target the Containers?
Which ban for DoS protection will enforce a rate limit for users who are unable to post five (5) “. tar.gz" files within five (5) seconds?
A security team notices a number of anomalies under Monitor > Events. The incident response team works with the developers to determine that these anomalies are false positives.
What will be the effect if the security team chooses to Relearn on this image?
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
Which component of a Kubernetes setup can approve, modify, or reject administrative requests?
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
Which ROL query is used to detect certain high-risk activities executed by a root user in AWS?
What is the default namespace created by Defender DaemonSet during deployment?
A customer has a requirement to scan serverless functions for vulnerabilities.
What is the correct option to configure scanning?
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
Which three actions are available for the container image scanning compliance rule? (Choose three.)
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
Which two fields are required to configure SSO in Prisma Cloud? (Choose two.)
Which of the following is not a supported external integration for receiving Prisma Cloud Code Security notifications?
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)

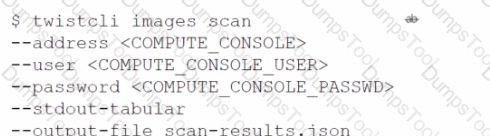
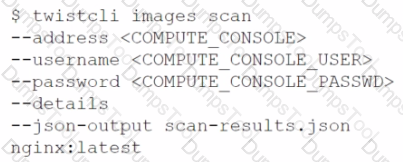
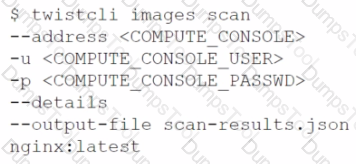
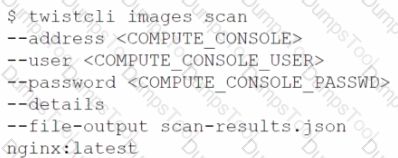
Which command correctly outputs scan results to stdout in tabular format and writes scan results to a JSON file while still sending the results to Console?
A)
B)
C)
D)
One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet:
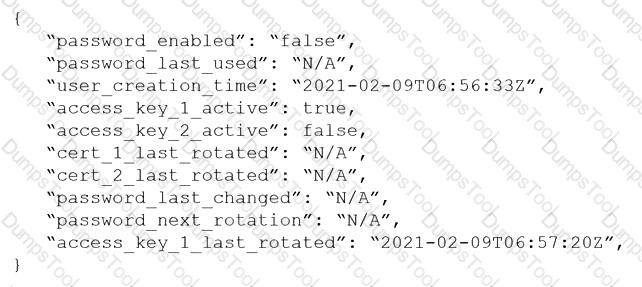
Which RQL detected the vulnerability?
A)

B)

C)

D)

Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
A customer has serverless functions that are deployed in multiple clouds.
Which serverless cloud provider is covered be “overly permissive service access” compliance check?
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User: $ADMIN_USER
Which command generates the YAML file for Defender install?
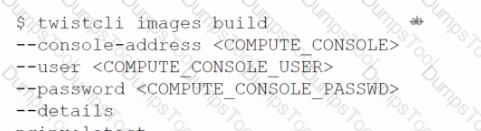
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
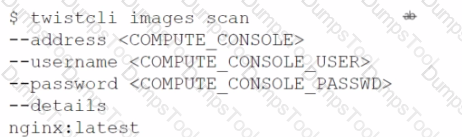
B)
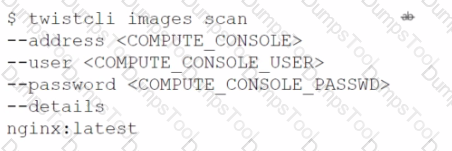
C)
D)
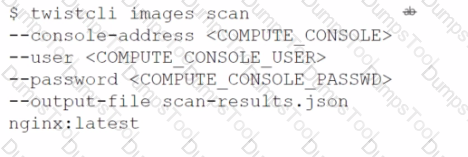
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
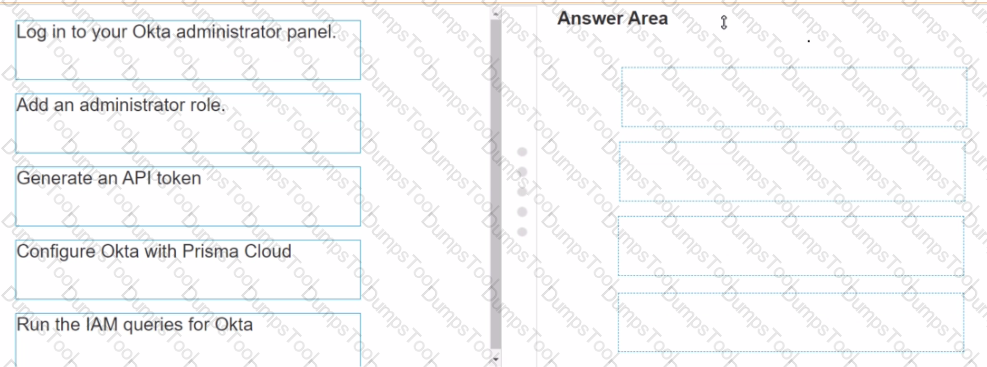
Put the steps of integrating Okta with Prisma Cloud in the right order in relation to CIEM or SSO okra integration.
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
A security team has a requirement to ensure the environment is scanned for vulnerabilities. What are three options for configuring vulnerability policies? (Choose three.)
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds.
What does the administrator need to configure?
On which cloud service providers can new API release information for Prisma Cloud be received?
What are two alarm types that are registered after alarms are enabled? (Choose two.)
In which two ways can Prisma Cloud images be retrieved in Prisma Cloud Compute Self-Hosted Edition? (Choose two.)
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Which three public cloud providers are supported for VM image scanning? (Choose three.)
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)