In OSPFv3, Router-LSA is generated by each router, which describes the interface address and cost of the router's links, as well as the RouteriD of the neighbor router.
HW users are transferring a very large number of files via TFTP. What protocol does TFTP rely on for transmission?
There are two Communily filters: ip comimuniy-lite lpemit 101201 ip community fiter 2permit101 ip commmuriyfilter 2pemit21 Regarding the above ommuniyfiter, the correct description is ?( Multiple choice questions).
Router HW cannot access hosts in the remote network, router HW runs routing protocols and only pings the remote file server address 105401 on router HW with extensions through a default route remote network , the result of ping on the router HW is rendered as 'requ.' est time out', according to the above description, the error in the following analysis is ?
In a shared network, what mechanism does PIM-SM use to prevent duplicate traffic?( Single choice questions).
Host HW1 in the HW device network Wants to join a video conference, so what does that host do?
If you need to configure routing policies on one router. Which of the following parameters does an administrator use to route when deploying a routing policy?( Multiple select).
A Protocol B. Application
C. Size of the packet D. Throughput
E. Identification of a specific terminal system
An advanced access control list is a sequence of rules consisting of permit |deny statements that can match IP messages based on which attributes ?(). Multiple select).
A router receives a BGP route with the community attribute NO-Export , how will the router handle the BGP route?
The following statement about the Security Alliance SA in IPSec is wrong with ?
Which IPV6 address would you ping to confirm that OSPFv3 is capable of pastoring unicast messages over the link?
A company's two-layer phase network architecture as shown in the figure, when the engineer is configured to find that the business between departments can not communicate, through the command to view the status of the equipment as follows, please determine the possible causes?
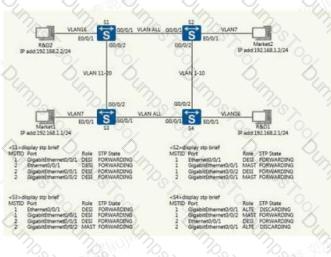
The switch can suppress traffic by suppressing traffic and extremely other failures can affect operations, which of the following traffic suppression configurations is the wrong configuration

The following statement about IPv6 Over VXLAN is wrong as ?( Single choice questions).
Traditional BGP-4 can only manage IP4 unicast routing information, and MP-BGP extends BGP-4 to provide support for multiple network layer protocols. Among them, MP-BGP's support feature for IPv6 unicast networks is called BGP4+, BGP4+ via NextHop The route next hop address information is carried by the attribute.
To build a loopless Layer 2 network, which of the following schemes is optimal?( Single Choice)
In the multi-level RR scenario, the first-level RR will be connected to a large number of second-level R, which may cause the BGP circuit of the first-level RR to overflow from the table Risk of R BGP routing table overflow?( Radio).
In the laboratory network, the network is built according to the following topology diagram, SWI is the default configuration, and SW2 disables the switch STP function.

Each DD message has a sequence number for data confirmation, and a DD sequence number is 2 bytes long
Man-in-the-middle attacks or IP/MAC spoofing attacks can lead to information leakage and other hazards, and are more common in the intranet, in order to prevent man-in-the-middle attacks or IP/MAC spoofing attacks, you can take the configuration method
If there is a switch running RSTP, which interface on that switch sends the BPDU with the Proposal logo??
Which of the following sequences can be matched by the regular expression [^100|200]$?
Which address prefix in the following options indicates that the address is globally unique and globally routable among unicast addresses in IPv6, similar to a public address in IPv4?(). Single choice questions).
If all the public IP addresses are used by a company's intranet users to access the Internet using NAT's No-pat method, what will happen to subsequent intranet users who access the Internet?
In the evolution from IPv4 networks to IPv6, some transition technologies have emerged, which of the following are common types of transition technologies?
You want only his telnet stream to be able to access the server (address 1011.100). Then, you add the following ACL to the routing ring: nule5pemit cp source ny destination 1011.100000destination-porteq 23 rule 1l0 deny ip source any destination any Then you apply that ACL to the ingress direction of the router's seial interface. What type of message is allowed to pass through the router?( Multiple choice questions).
One of the things you're doing is compressing the length of ip6 addresses as much as possible . The existing IP6 address is
2013xX0C130F006009cO87641308, to be able to make this P6 address more concise, you can compress the IP6 address into which of the following?( Single choice questions).
In the VXLAN implementation, the mapping relationship between VNI and BD is
As shown in the figure, all routing diagrams declare the loopback address in OSPF, where R2 does not return the address is 10022/32, it is advisable to tell AraD. The R3 loopback address is 10033/321001.1.0/24 external routing, in order to reduce the burden on the RI router, the configuration command is as follows:( Multiple choice questions)[Rlip ip-prefix 1 permit 001.1.024 [RLIJospfl [RL-ospf-1]filter-policy ip-prefix l import please ask the following description is correct?
Level-1-2IS transmits Level-2LSP to the Level-1 area if the AT location 1 in Level-2LSP is delivered It means that the Level-1lS in the area can be accessed to the outer area through Level-1-2IlS
If the Option field value in the 0SPFv3 Hello message issued by the router's GIgabit Ethermet0/0 interface is 0x000013, the following description is correct
OSPFv2 is an IGP running on an IPV4 network; OSPFV3 is an IGP running in an IPV6 network
IGP, OSPFv3 in the network has a similar LSA type compared to OSPFV2, but the functionality is slightly different, osPFv3LSA type does not include which of the following?
Regarding the site in the BGP/MPLSIP VPN network architecture, the following description is correct?
If a router only needs to forward iPv6 packets, you do not need to configure any IPV4 agreements and addresses on that router.
Deploying the ISIS protocol in an IPv6 environment is true in the following statement (radio).
Regarding the sliding window of TCP, what are the following descriptions that are enough to be wrong? ( Multiple choice question)
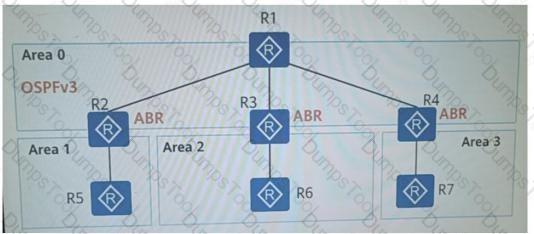
In the topology shown in the figure. Running the OSPFv3 protocol over the entire network does not produce what type of LSA on R1 without external route introduction?
When troubleshooting a local area network, you notice a large number of frame alignment errors, FCS errors and LAG conflicts, and the possible cause of these problems is ?
The firewall has created some security zones by default, which of the following security zones does not exist by default on the firewall?( Radio).
In route-policy, what are the BGP attributes that can be used for the apply clause?
There is a new HW office that needs to use their router as a DHCP server. When configuring the DHCP server to provide DHCP services to the current office, what of the following items need to be configured?
When running OSPFv3 on a Huawei router, the OSPFv3 process automatically selects an interface address as the process router id
Regarding the certification of the ISIS protocol, there is a correct statement
In a VXLAN network, traffic is connected to the VXLAN network, and it can also be used to communicate with the same subnet within the same XLAN network
The following description of the characteristics of Huawei device Eth-trunk link aggregation is correct?
What improvements have been made to the IGMPv2 protocol compared to IGMPv1? ( Multiple Choice)
The BSR/RP mechanism described below describes the correct determination ?( Multiple choice questions).
There can be multiple C-BSRs in the
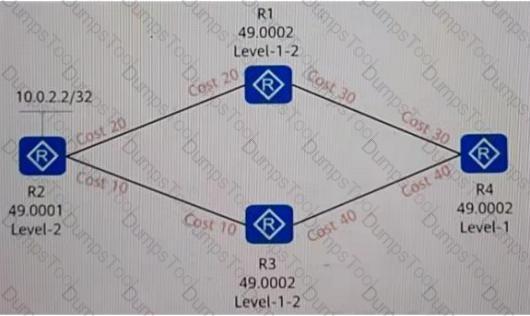
If four routers run ISIS and have established an adjacency relationship, and the area code and router rank are marked as shown in the figure, what is the cost value of R4 reaching 10022/32?
CMPv6 uses the Type field to identify the message type, and according to the value of the type field, we can divide the ICMPv6 message into two categories, one is the error message and the other is the information message
If you delete a declared route entry on a BGP router, the BGP routing ring is triggered to send an Update message for route scattering, which carries the accepted mandatory attribute of the route entry that was discarded.
Which SNMP message type sent to NMS reports events that are reliable? ( Single choice questions).
The following description of IGMPv1 and IGMPv2 is correct?( Multiple select).
The following description of the characteristics of cross-domain VN-Optionc is correct?
The following statement about EVPN Type5 routing is wrong?( Single choice questions).
Dual-bucket, two-speed is used in traffic governance, where the number of tokens in a C bucket is TC and the number of tokens in a P bucket is TP. When a message of length B enters, which of the following sentences is correctly described? (Multiple choice questions).
ION NO: 272
The rules for RR to publish routes break the rules for horizontal segmentation of IBGP, so it is possible to cause loops within the AS. What routing attributes does RR use to prevent loops?
There are three port roles defined in RSTP, with alternative ports and backup ports flags in STP messages The port role values within the fields are consistent, all of which are 01
Regarding the description of the encapsulation format of the labels in MPLS, the correct one is ?
Regarding route introduction, what is the following description of the error?