When an application is designed that requires high availability, what is a reason to use a cross-region cloud?
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
Which configuration stop must be performed on a Cisco IOS XE device to present collected data in Cisco DNA Center?
A web application has those requirements for HTTP cache control:
Which header must the engineer use?
A developer has issued git add file1 and file2 test.py command to add the three files for the next commit, but then decides to executed test.py from this command. Which command needs to be used to exclude test.py from this commit but keep the rest of the files?
Which Puppet manifest changes the NTP server and generates the traffic from VLAN 15?
A)

B)

C)

D)

Refer to the exhibit.

A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices. What is the appropriate password storage approach?
Refer to the exhibit.
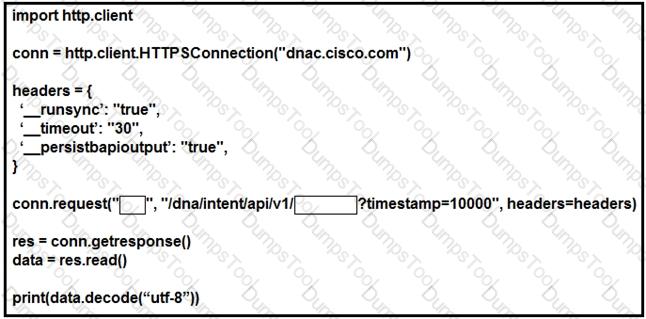
Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?
What are two benefits of using a centralized logging service? (Choose two.)
Refer to the exhibit.
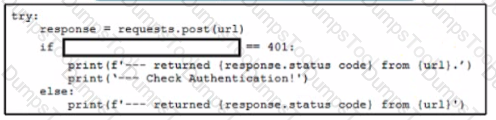
A network engineer writes a script to test authentication workflow using Python and REST API. The engineer wants to ensure that the script handles expected errors by matching output to HTTP status codes The scnpt uses the Python requests module. Which line of code must be added on the snippet where the code is missing?
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
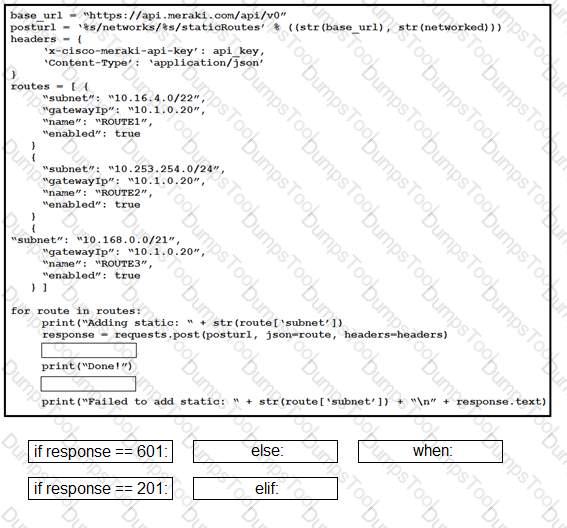
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
What is the unique identifier in the 0Auth2 three-legged authorization code flow?
Refer to the exhibit.
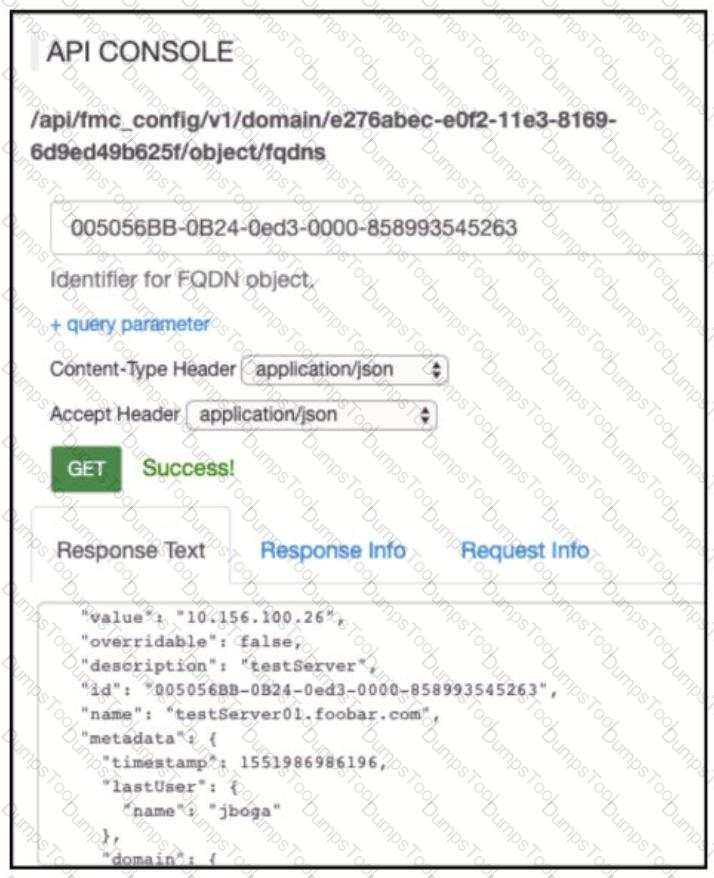
Which AP! call does an engineer use to delete the FQDN object?
Refer to the exhibit.

An application is being developed as an information repository. The application will be used to store details about television shows, including the scenario, year, and category. Which database type must used for high performance for the data structure?
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
Refer to the exhibit.
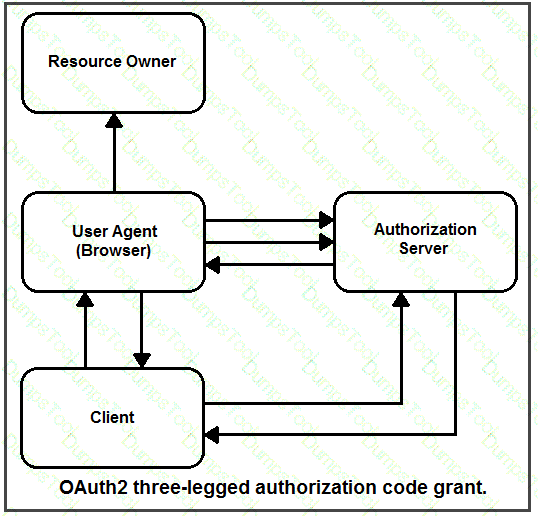
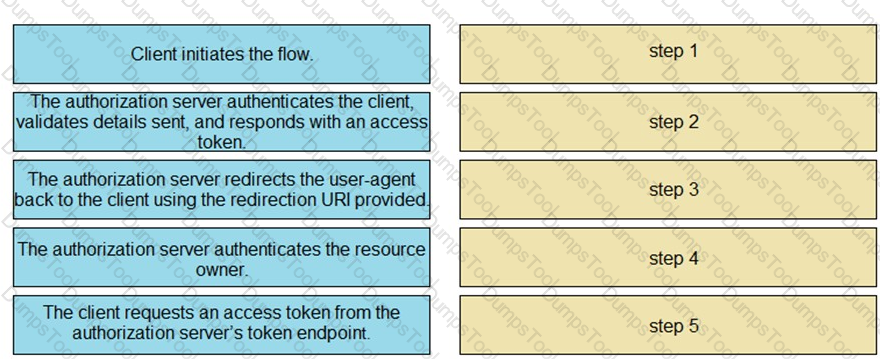
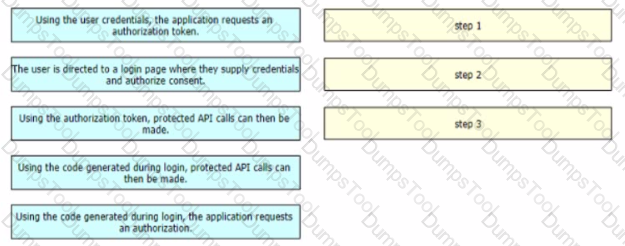
Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow.
Where mus! the data be encrypted to ensure end-to-end encryption when using an API?
A developer needs to build a new Docker image and has created a tag by using the command:
$ docker tag 32df423320458 local/app.1.2
Which command must be executed next to build the Docker image using the tag?
A)
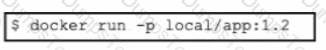
B)
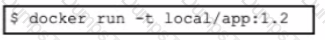
C)

D)

Refer to the exhibit.

A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
Refer to the exhibit.
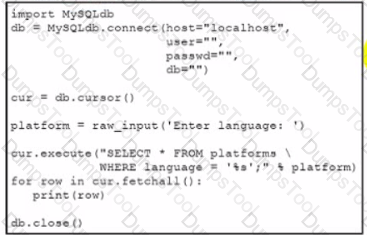
Which action should be performed to avoid an SQL injection attack?
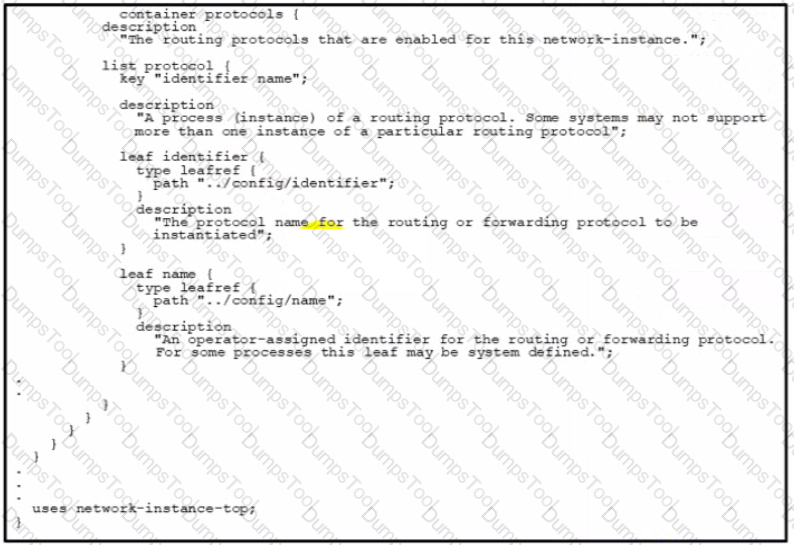
Refer to the exhibit. Which URI string retrieves configured static routes in a VRF named CUSTOMER from a RESTCONF-enabled device?
A)

B)
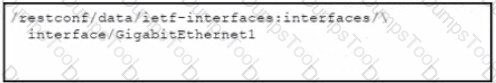
C)

D)
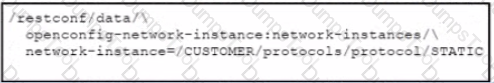
Drag and drop the steps from the left into the sequence on the fight to implement an OAuth2 three-legged authorization code flow grant type in an application Not all options are used.
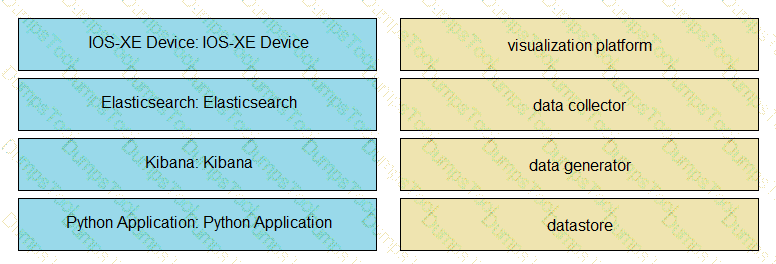
An application is being built to collect and display telemetry streaming data. Drag and drop the elements of this stack from the left onto the correct element functions on the right.
Refer to the exhibit.
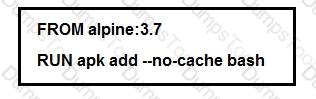
Which additional line results in the output of Test 1 upon execution of the docker run --rm devnet 1 command in a Dockerfile with this content?
Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS XML API. Options may be used more than once. Not all options are used.
A developer is deploying an application to automate the configuration and management of Osco network files and routers The application must use REST API interface lo achieve programmability. The security team mandates that the network must be protected against DDoS attacks What mitigates the attacks without impacting genuine requests?
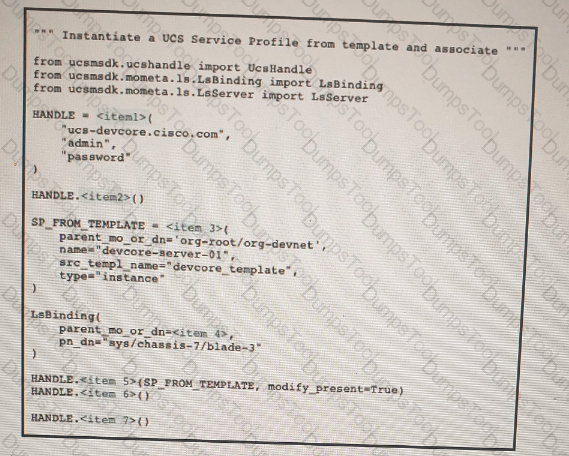
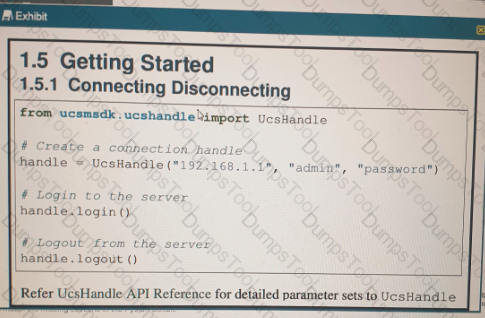
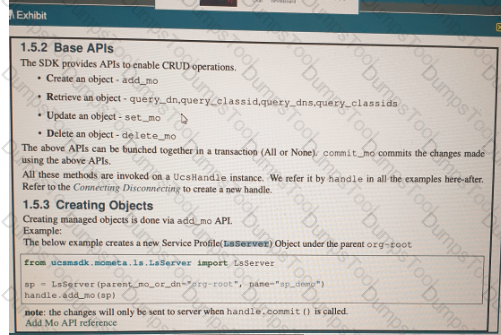
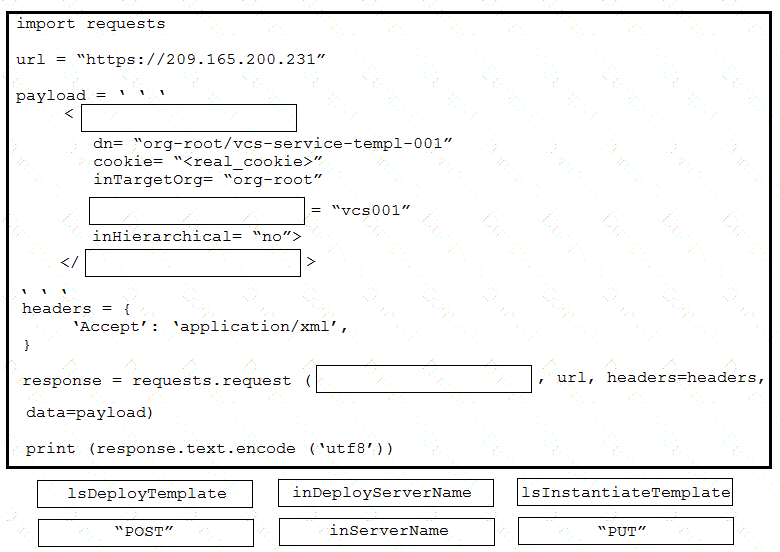
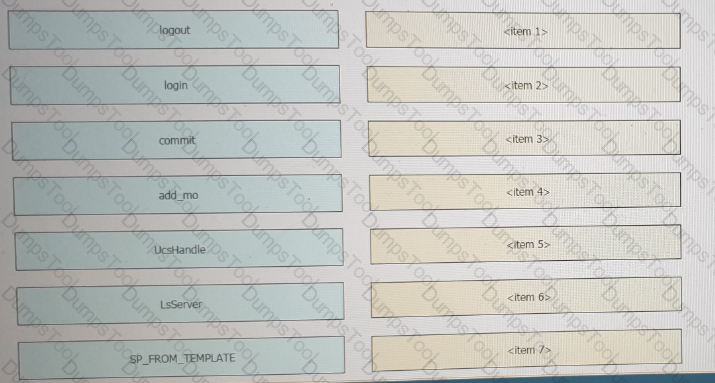
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Python code that uses the UCS Python SDK is instantiating a service profile named ''devcore-server-01'' from service profile template ''device-template'' , then associating the service profile instance to blade 3 in chassis 7. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the Python exhibit.
Refer to the exhibit.
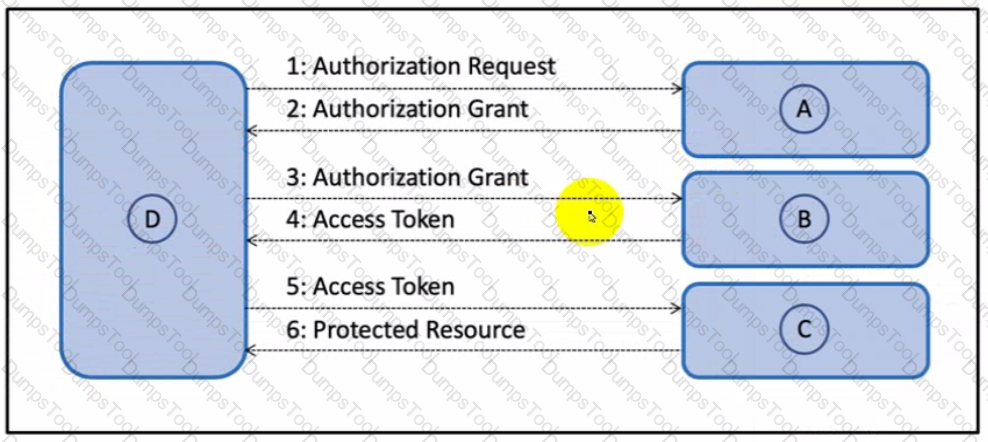
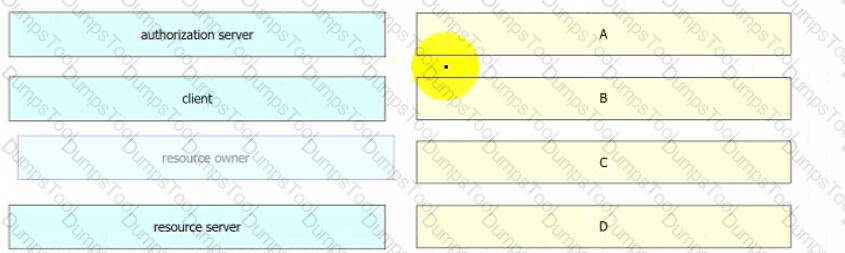
Drag and drop the components from the Oauth2 authorization protocol flow on the left onto the letter that matches the location in the exhibit.
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.

A container running a Python script is failing when it reaches the integration testing phase of the CI/CD process. The code has been reviewed thoroughly and the build process works on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?
The response from a server includes the header ETag: W/”7eb8b94419e371767916ef13e0d6e63d”. Which statement is true?
A developer releases a new application for network automation of Cisco devices deployed m a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability-driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
Refer to the exhibit.

Interface Lookback 1 must be created with IP address 10.30.0.1/24 in a Cisco IOS XE device using RESTCONF. The schema that is defined by the exhibit must be used. Which body and URI should be used for this operation?
A)

B)
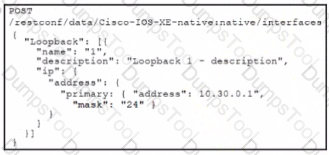
C)
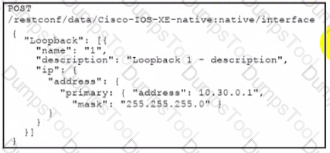
D)
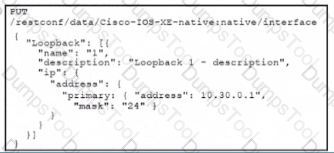
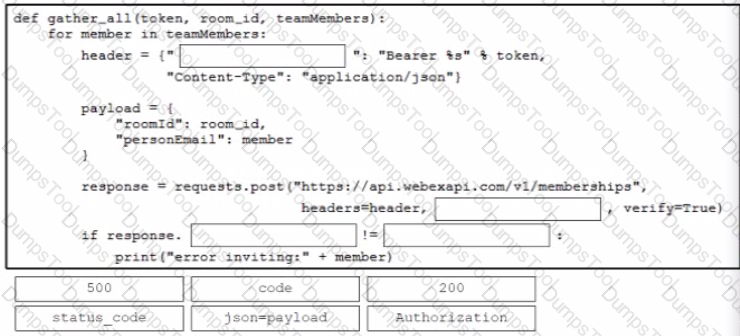
A developer is creating a Python function that adds network engineers to a Webex room to troubleshoot after a monitoring alert Drag and drop the code from the bottom onto the box where the code is missing in the Python function to add the engineers to the room. Not all options are used.
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
Drag and drop the code from the bottom onto the box where the code is missing to construct a contact tracking application that dynamically returns all the Bluetooth clients on a given Meraki network. Not all options are used.

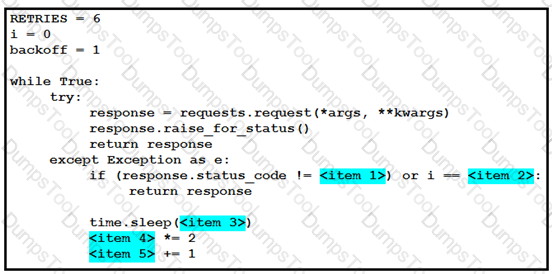
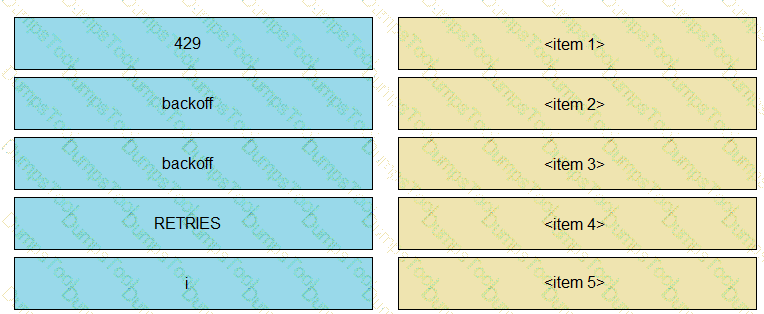
Refer to the exhibit. The self-service Webex Teams bot is failing when many users attempt to interact with it at the same time. Drag and drop the code snippets from the left onto the correct item numbers on the right that match the missing sections in the exhibit to complete this code to handle this high-load situation.
What is a capability of the End User Monitoring feature of the AppDynamics platform?
Refer to the exhibits. Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?
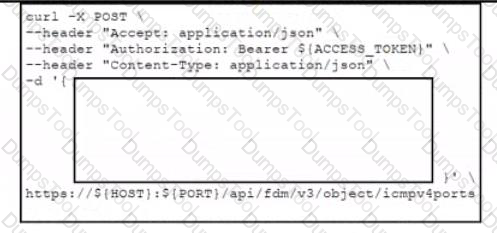
Refer to the exhibits. Which data payload completes the CURL command to run the create port object API call In Cisco Firepower Threat Defense?
A)

B)

C)

D)
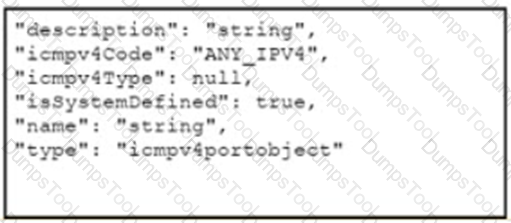
A developer must containerize a Python application to integrate into a prebuilt CD environment by creating a Docker image. It will be hosted as a web application to enable end users from accessing it remotely. Drag and drop the code from the bottom onto the box where the code is missing in the Docker file Not all options are used.
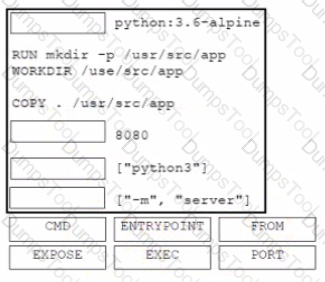
Drag and drop the git commands from the left into the correct order on the right to create a feature branch from the master and then incorporate that feature branch into the master.
Refer to the exhibit.
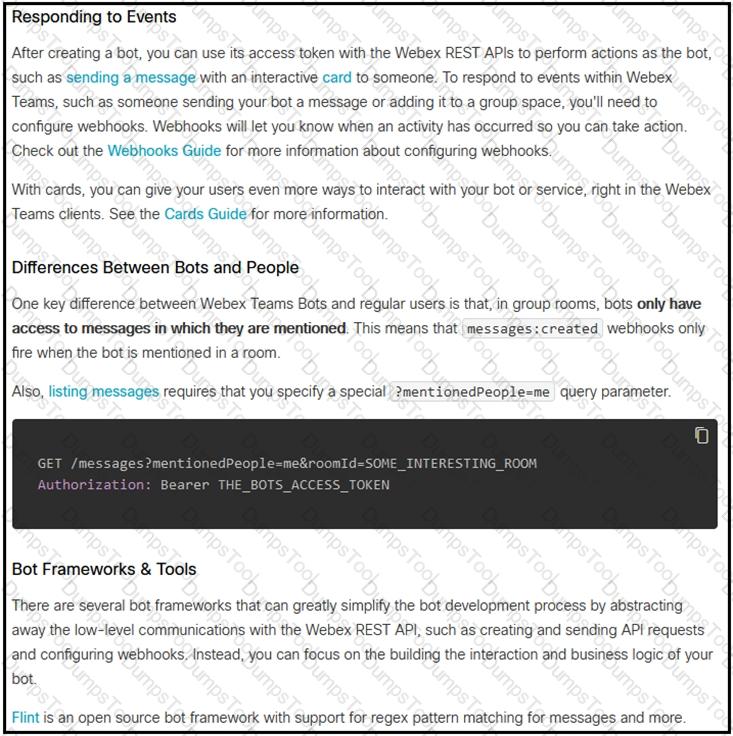
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
Refer to the exhibit.
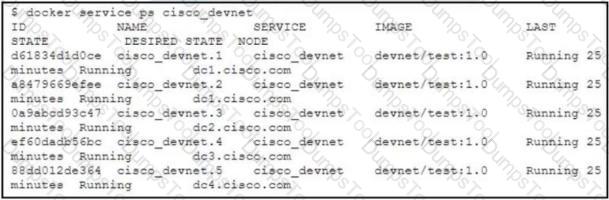
The cisco_devnet Docker swarm service runs across five replicas.The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container.There must be no service outages during the upgrade process. Which two design approaches must be used? (Choose two.)