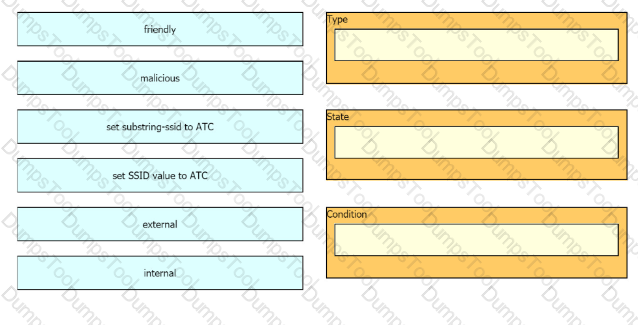
The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used.
Refer to the exhibit.
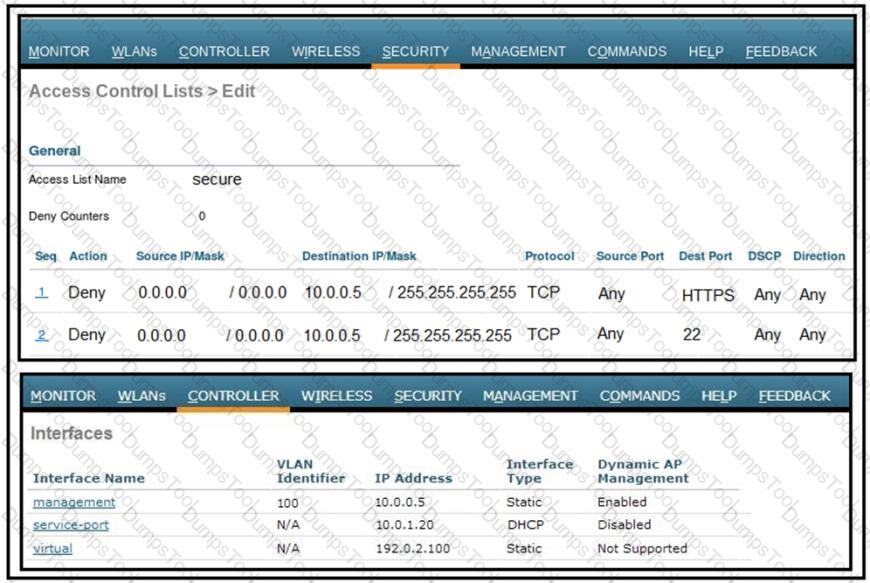
An engineer implemented the CPU ACL on your Cisco 5520 Series Wireless LAN Controller, and the controller is no longer manageable via the network. What must be changes on this CPU ACL to enable it to manage the controller again?
An IT administrator deploys Cisco 2802i APs in all office locations, including main campus and branch offices. The WLC that manages the APs is located at the data center on the main campus. The APs on the main campus are configured to use Local mode and the APs in the branches use FlexConnect mode. Which configuration must be applied to the APs for corporate devices on the main campus to be mapped to the local LAN switch on different VLANs according to the VLAN tag ID and WLAN?
When configuring a Cisco WLC, which CLI command adds a VLAN with VLAN ID of 30 to a FlexConnect group named BranchA-FCG?
An engineer is in the process of implementing Fastlane on a wireless network with a Mobility Express AP installed. The network must support voice and video applications for Apple devices. Due to a security concern, all iPhones are updated to version 14.5.432302546. Which QoS profile must the engineer configure on the user WLAN?
A customer is deploying local web authentication. Which software application must be implemented on Cisco ISE to utilize as a directory service?
A wireless network has been implemented to enable multicast video to be streamed reliably over the wireless link to the wireless users. After a client reports that the video is unable to stream, the administrator determines that the client is connecting at a data rate of 12 Mbps and is trying to stream to a valid multicast address on the network. Which two actions must be applied? (Choose two.)
An engineer must run a Client Traffic Stream Metrics report in Cisco Prime Infrastructure. Which task must be run before the report?
A customer is concerned that their wireless network is detecting spurious threats from channels that are not being used by their wireless infrastructure. Which two technologies must they deploy? (Choose two.)
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A wireless engineer is configuring LWA using ISE. The customer is a startup company and requested the wireless users to authenticate against a directory, but LDAP is unavailable. Which solution should be proposed in order to have the same security and user experience?
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices.
Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
A wireless administrator must assess the different client types connected to Cisco Catalyst 9800 Series Wireless Controller without using any external servers. Which configuration must be added to the controller to achieve this assessment?
Refer to the exhibit.
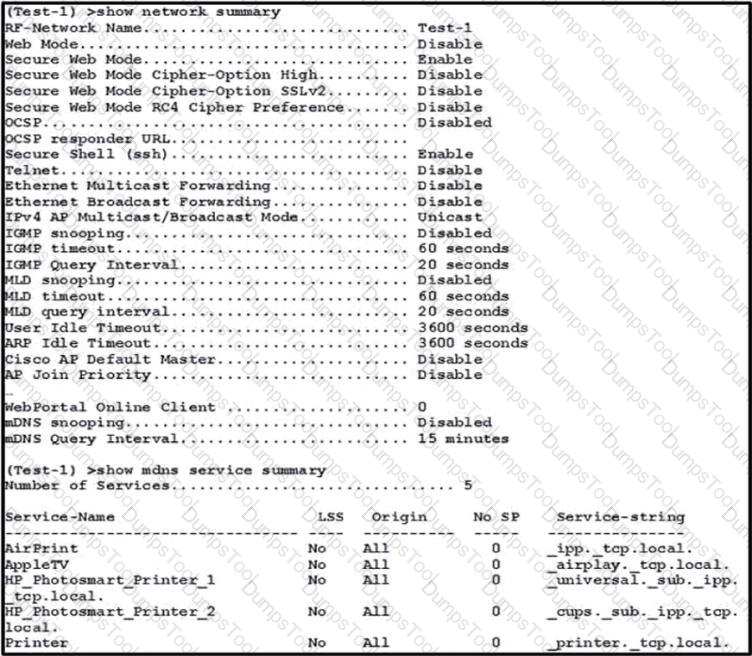
An engineer configured a BYOD policy that allows for printing on the WLAN using Bonjour services. However, the engineer cannot get printing to work. The WLC firmware is 8.x. What must be implemented on the controller?
An engineer is troubleshooting a Cisco CMX high-availability deployment and notices that the primary and backup Cisco CMX servers are both considered primary. Which command must the engineer run on the backup server?
An engineer has configured passive fallback mode for RADIUS with default timer settings. What will occur when the primary RADIUS fails then recovers?
A network administrator just completed the basic implementation of Cisco CMX and tries to implement location tracking. The administrator is having trouble establishing connectivity between one of the WLCs through NMSP. What must be configured to establish this connectivity? (Choose two.)
A network engineer needs to configure multicast in the network. The implementation will use multiple multicast groups and PIM routers. Which address provides automatic discovery of the best RP for each multicast group?
Refer to the exhibit.
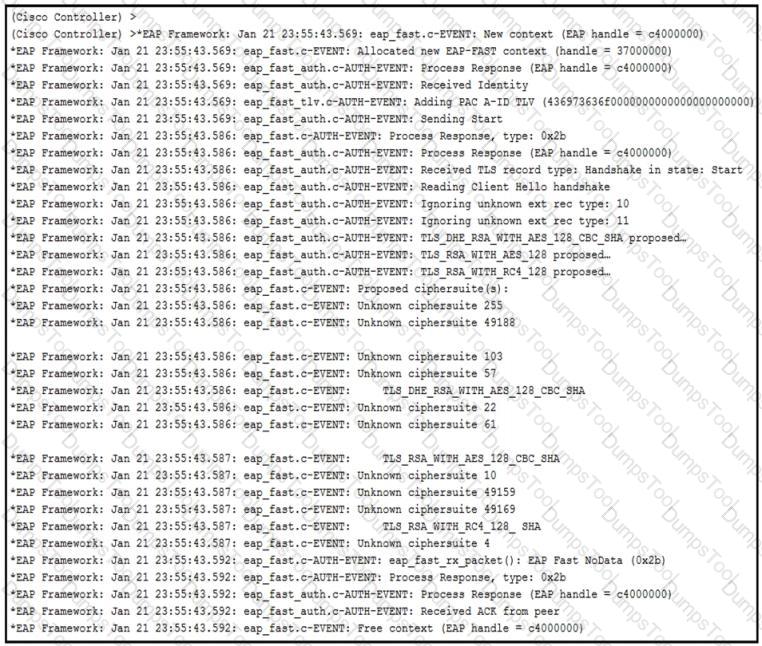
An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
An engineer set up identity-based networking with ISE and configured AAA override on the WLAN. Which two attributes must be used to change the client behavior from the default settings? (Choose two.)
An engineer must perform a Layer 2 survey for a mining facility. Which type of antenna does the
engineer use in the mine shaft?
The IT manager is asking the wireless team to get a report for all guest user associations during the past two weeks. In which two formats can Cisco Prime save this report? (Choose two.)
An engineer is setting up a WLAN to work with a Cisco ISE as the AAA server. The company policy requires that all users be denied access to any resources until they pass the validation. Which component must be configured to achieve this stipulation?
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
An engineer is configuring a BYOD deploymernt strategy and prefers a single SSID model.
Which technology is required to accomplish this configuration?
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)