An engineer must connect a new remote site to an existing OSPF network. The new site consists of two low-end routers, one for WAN, and one for LAN. There is no demand for traffic to pass through this area. Which area type does the engineer choose to provide minimal router resources utilization, while still allowing for full connectivity to the rest of the network?
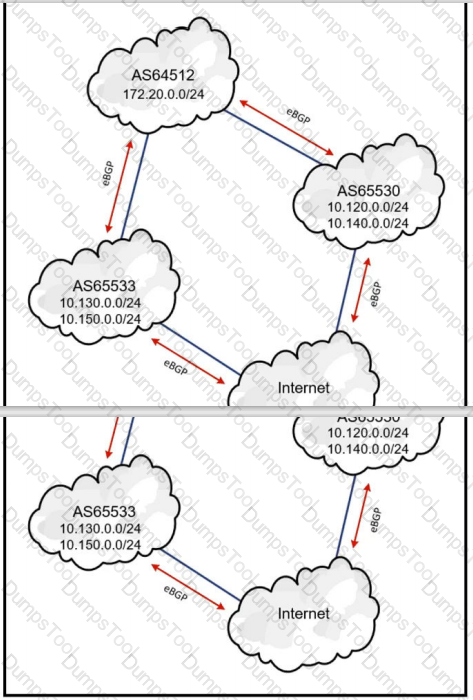
Refer to the exhibit. AS65533 and AS65530 are announcing a partial Internet routing table as well as their IP subnets. An architect must create a design that ensures AS64512 become a transit AS. Which filtering solution must the architect choose?
How is internet access provided to a WAN edge router that is connected to a MPLS transport link?
A company is running BGP on a single router, which has two connections to the same ISP. Which BGP
feature ensures traffic is load balanced across the two links to the ISP?
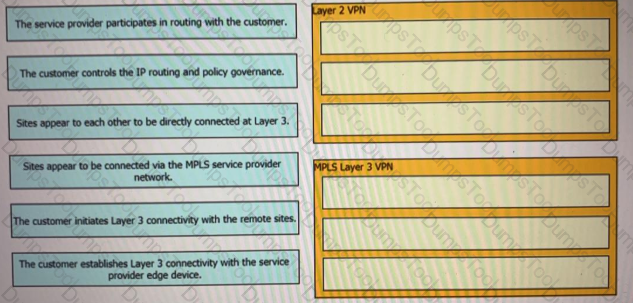
Drag and drop the descriptions from the left onto the corresponding VPN types on the rights.
Which consideration must be taken into account when using the DHCP relay feature in a Cisco SD-Access Architecture?
Which feature must be incorporated into the campus LAN design to enable Wake on LAN?
How is end-to-end microsegmentation enforced in a Cisco SD-Access architecture?
Company A recently acquired another company. Users of the newly acquired company must be able to access a server that exists on Company A’s network, both companies use overlapping IP address ranges. Which action conserves IP address space and provides access to the server?
An infrastructure team is concerned about the shared memory utilization of a device, and for this reason, they need to monitor the device state. Which solution limits impact on the device and provides the required data?
What is the role of a control-plane node in a Cisco SD-Access architecture?
A company uses cloud-based applications for voice and video calls, file sharing, content sharing, and messaging. During business hours, these applications randomly become slow and unresponsive. However, other applications work smoothly with the current applied QoS polices. Which solution must the company choose to resolve the issue?
Which two statements describe source trees in a multicast environment? (Choose two.)
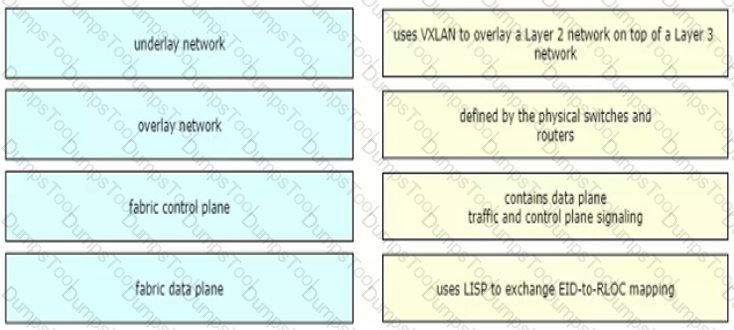
Drag and drop the components in a Cisco SD-Access architecture from the left onto their descriptions on the right.
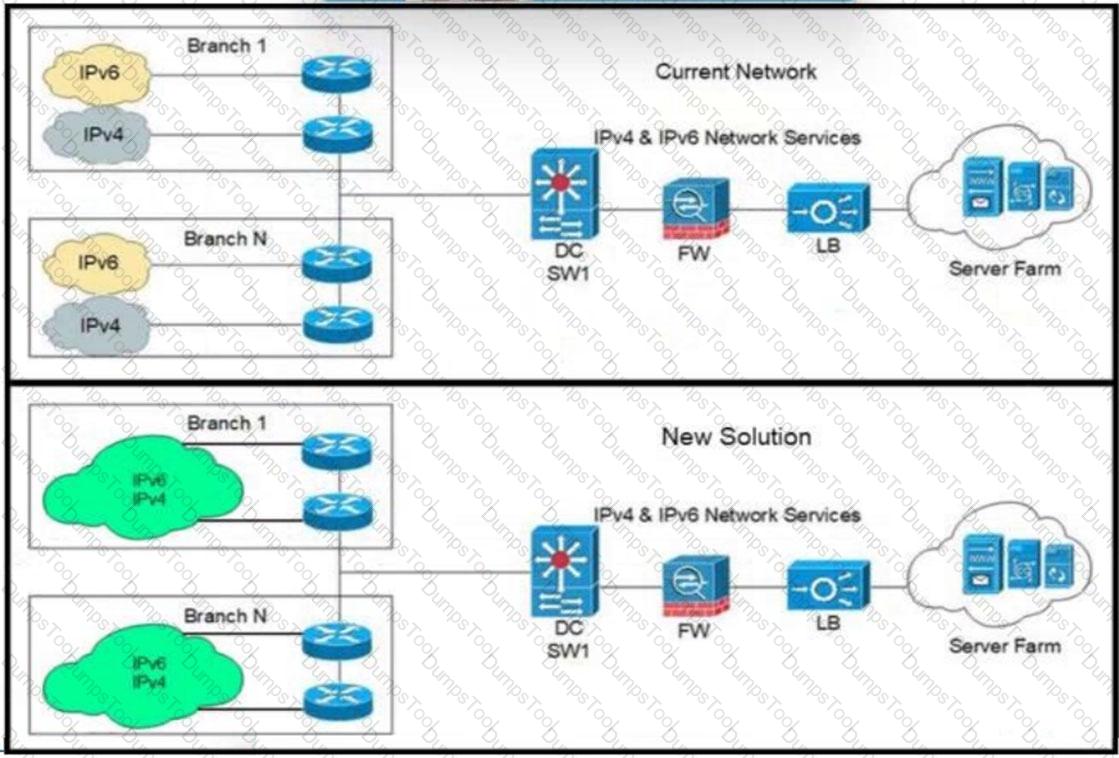
Refer to the exhibit. An architect is developing a solution to consolidate networks while retaining device redundancy. The routing protocol for the WAN routers must be open standard, ensure high availability, and provide the fastest convergence time. Which solution must the design include?
When a network is designed using IS-IS protocol, which two circuit types are supported? (Choose two.)
A network administrator is troubleshooting a DMVPN setup between the hub and the spoke. Which action should the administrator take before troubleshooting the IPsec configuration?
Refer to the exhibit.
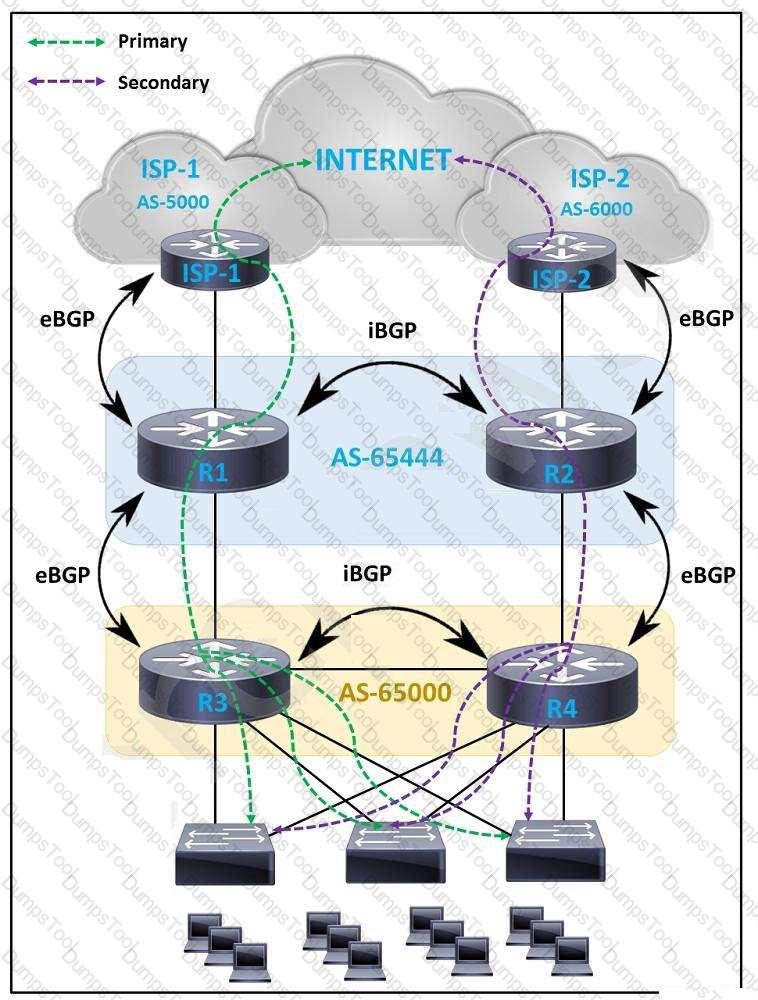
An engineer must design a WAN solution so that ISP-1 is always preferred over ISP-2. The path via ISP-2 is
considered as a backup and must be used only when the path to ISP-1 is down. Which
solution must the engineer choose?
In an SD-WAN architecture, which methods are used to bootstrap a vEdge router?
An engineer must peer with an ISP for internet connectivity using BGP, initially, the engineer wants to receive only specific prefixes from the ISP and a default route. However, the solution must provide the flexibility to add prefixes in the future at short notice. The ISP has a two-week change process in place. Which route filtering solution must the engineer employ?
An organization plans to deploy multicast across two different autonomous systems. Their solution must allow RPs to:
•discover active sources outside their domain
•use the underlying routing information for connectivity with other RPs
•announce sources joining the group
Which solution supports these requirements?
An engineer is designing an IPv4 addressing plan for an enterprise with 1000 branches. Each branch requires a prefix for data and a prefix for voice. Each prefix must accommodate up to 128 hosts, and prefixes must facilitate summarization at aggregation points in the network. The security team requires a simple method for identifying voce prefixes. Which allocation does the engineer recommend from the RFC1918 address space?
An engineer is designing an enterprise campus network. The LAN infrastructure consists of switches from multiple vendors, and Spanning Tree must be used as a Layer 2 loop prevention mechanism. All configured
VLANs must be grouped in two SIP instances. Which standards-based Spanning Tree technology supports this design solution?
Refer to the exhibit.
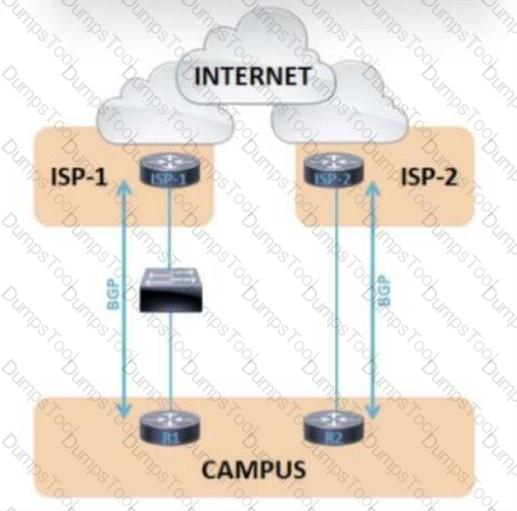
The failover time of ISP-2 is significantly shorter than ISP-1 when an interface on the ISP router toward the campus network fails. Which solution minimizes the downtime to the sub-second?
An architect must design an IPv6 migration solution for a corporation with remote offices to support:
* The customer has IPv4 peering with their service provider.
* IPv6 users need access to IPv4 and IPv6 resources.
* Existing content providers will migrate to IPv6 in the next two years.
* Users will be migrated in a phase-by-phase approach.
Which migration solution must the architect choose?
Refer to the exhibit.
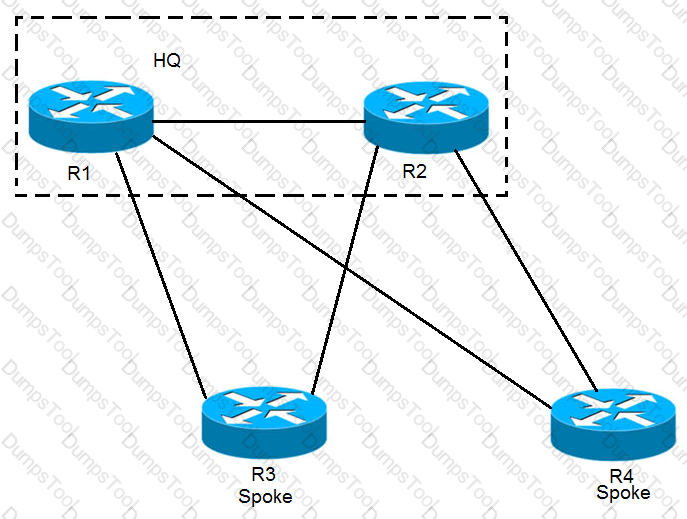
EIGRP has been configured on all links. The spoke nodes have been configured as EIGRP stubs, and the WAN links to R3 have higher bandwidth and lower delay than the links to R4. When a link failure occurs at the R1-R2 link, what happens to traffic on R1 that is destined for a subnet attached to R2?