When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of?
Which port is used for vBond under controller certificates if no alternate port is configured?
An administrator wants to create a policy to add a traffic policer called "politer-ccnp" to police data traffic on the WAN Edge. Which configuration accomplishes this task in vSmart?

An engineer is configuring a shaping rate of 1 Mbps on the WAN link of a WAN Edge router Which configuration accomplishes this task’?

A network administrator configures SNMPv3 on a Cisco WAN Edge router from CLI for monitoring purposes How many characters are supported by the snmp user
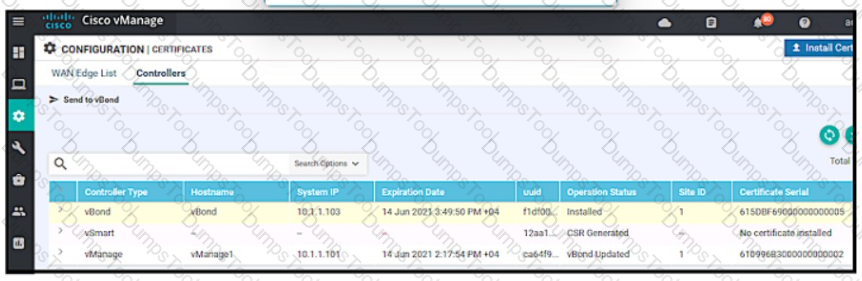
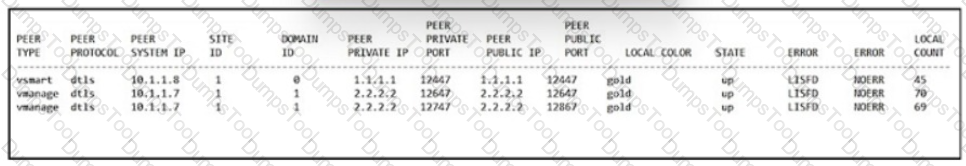
Refer to exhibit. An engineer is troubleshooting tear of control connection even though a valid CertificateSerialNumber is entered. Which two actions resolve Issue? (Choose two)

An enterprise needs DIA on some of its branches with a common location ID: A041:B70C: D78E::18 Which WAN Edge configuration meets the requirement?
A)
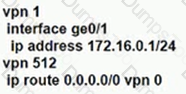
B)
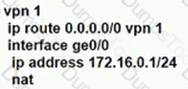
C)
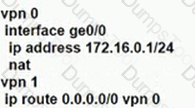
D)
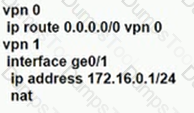
What is the maximum number of IPsec that are temporarily created and converged on a new set if IPsec Sas in the pairwise keys process during a simultaneous rekey?
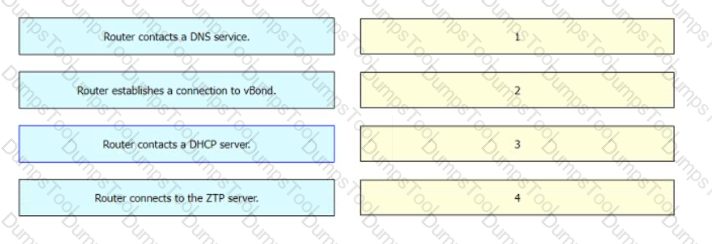
Drag and drop the steps from the left into the sequence on the right for a WAN Edge router after powering on for zero touch provisioning.
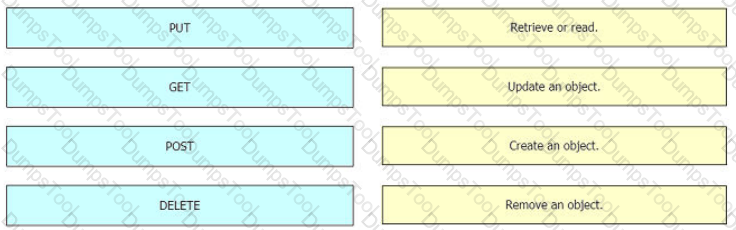
Drag and drop the REST API calls from the left onto the functions on the right.
Refer to the exhibit vManage and vBond have an issue establishing a connection to vSmart Which two actions does the administrator take to fix the issue? (Choose two)
Install the certificate received from the certificate server.
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
A network administrator is creating an OMP feature template from the vManage GUI to be applied to WAN edge routers. Which configuration attribute will avoid the redistribution of the routes back into the OMP from the LAN side?
How many concurrent sessions does a vManage REST API have before it invalidates the least recently used session if the maximum concurrent session number is reached?
Which action is performed during the onboarding process when a WAN Edge router is connected to ZTP server ztp.viptela com?
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
An enterprise has these three WAN connections:
An engineer must configure two available links to route traffic via both links. Which configuration achieves this objective?
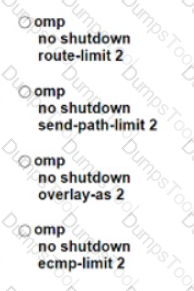
Which protocol is used to measure loss latency, Jitter, and liveliness of the tunnel between WAN Edge router peers?
A network administrator is configuring a centralized control policy based on match action pairs for multiple conditions, which order must be configured to prefer Prefix List over TLOC and TLOC over Origin?
Which two hardware platforms support Cisco IOS XE SD-WAN images'' (Choose two)
A network administrator is configuring an application-aware firewall between inside zones to an outside zone on a WAN edge router using vManage GUI. What kind of Inspection is performed when the ‘’inspect’’ action is used?
Which plane builds and maintains the network topology and makes decisions on traffic flows?
Which two services are critical for zero touch provisioning on-boarding? (Choose two)

Refer to the exhibit, Which configuration routes Site 2 through the firewall in Site 1?
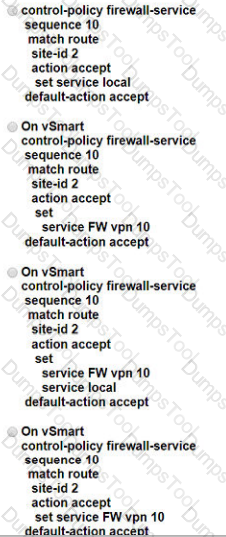
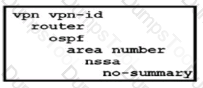
Which OSPF command makes the WAN Edge router a less preferred exit from a site with a dual WAN Edge design?
A)

B)

C)

D)
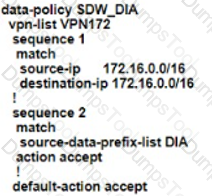
An engineer is configuring the branch office with a 172.16.0.0/16 subnet to use DIA for Internet traffic. All other traffic must flow to the central site or branches using the MPLS circuit Which configuration meets the requirement?
A)

B)
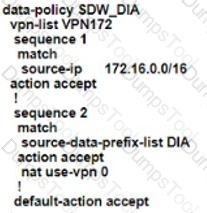
C)

D)
Which protocol is used to propagate multicast join requests over the Cisco SD-WAN fabric?
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
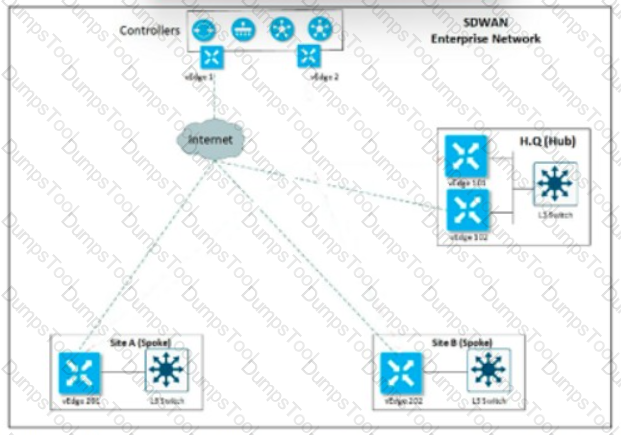
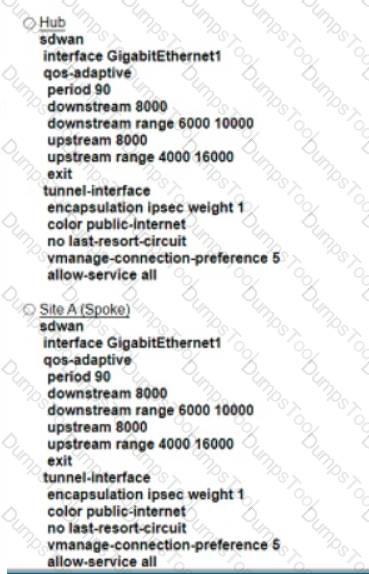
Refer to the exhibit An engineer must configure a QoS policy between me hub and site A (spoke) over a standard internet circuit where traffic shaping is adjusted automatically based on evaiiabk» bandwidth Which configuration meets the requirement?

Which two resource data types are used to collect information for monitoring using REST API in Cisco SD-WAN? (Choose two.)
Which two metrics must a cloud Edge router use to pick the optimal path for a SaaS application reachable via a gateway site? (Choose two.)
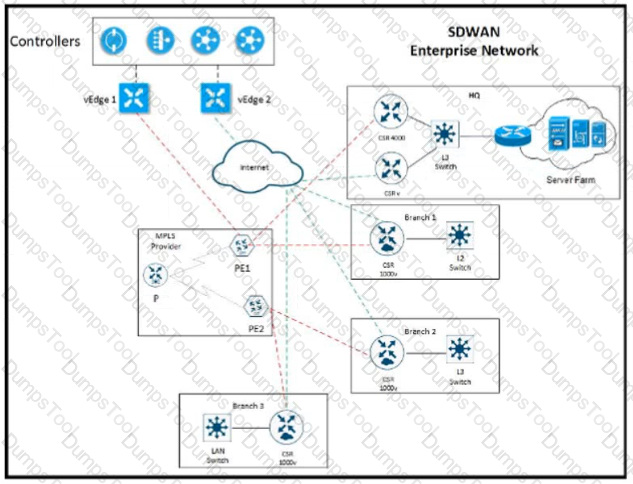
Refer to the exhibit The network team must configure ElGRP peering at HQ with devices in the service VPN connected to WAN Edge CSRv. CSRv is currently configured with
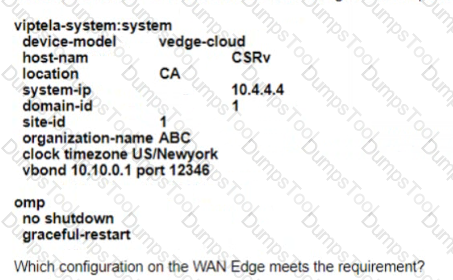
Which configuration on the WAN Edge meets the requiremnet
A)
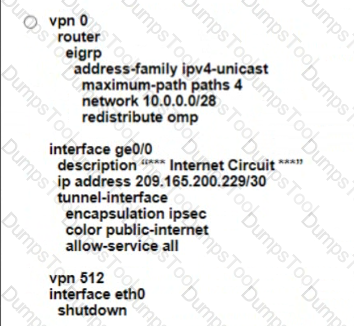
B)
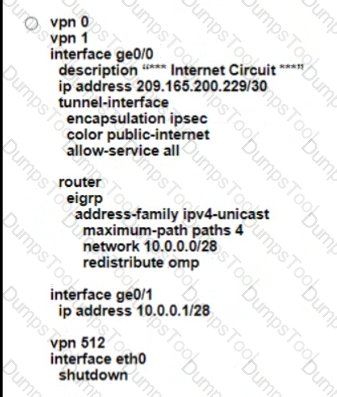
C)
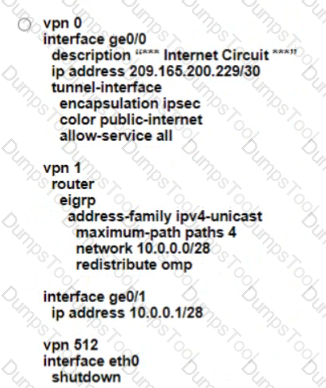
D)

Refer to the exhibit.
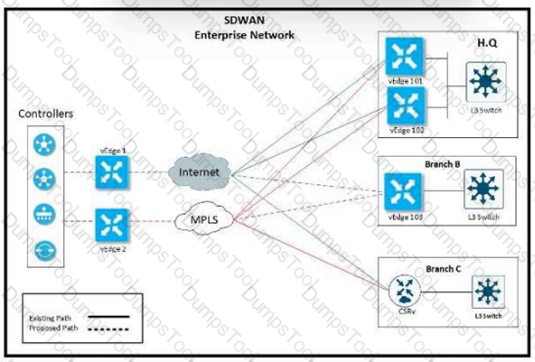
The network team must configure branch B WAN Edge device 103 to establish dynamic full-mesh IPsec tunnels between all colors with branches over MPLS and Internet circuits. The branch ts configured with:

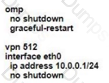
Which configuration meets the requirement?
A)
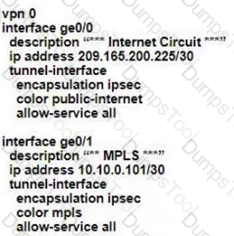
B)
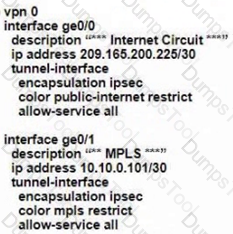
C)
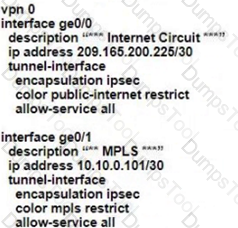
D)

A bank is looking for improved customer experience for applications and reduce overhead related to compliance and security. Which key feature or features of the Cisco SD-WAN solution will help the bank to achieve their goals?
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue?
At which layer does the application-aware firewall block applications on a WAN Edge?
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?
An engineer must configure local redundancy on a site. Which configuration accomplish this task?
Which timer specifies information in the cache after all OMP sessions are lost at location S0123T4E56F78?
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center?
Which OMP route is selected for equal OMP route preference values on WAN Edge routers?
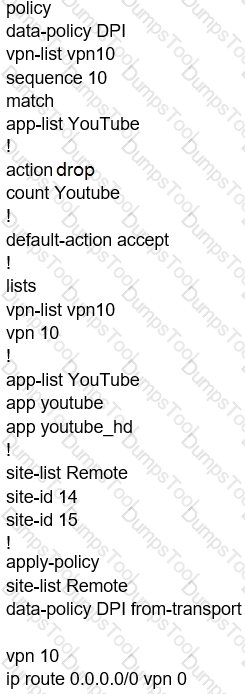
Which configuration allows users to reach YouTube from a local Internet breakout?
A)
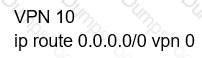
B)
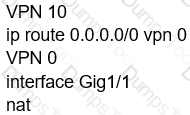
C)
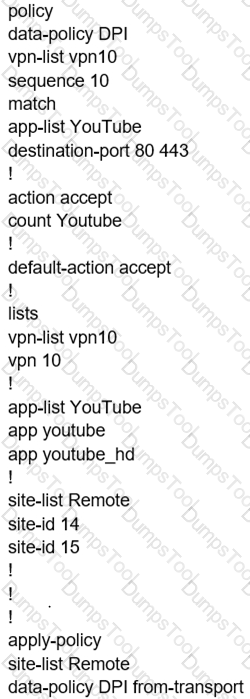
D)
Where on vManage does an engineer find the details of control node failure?
Refer to the exhibit.
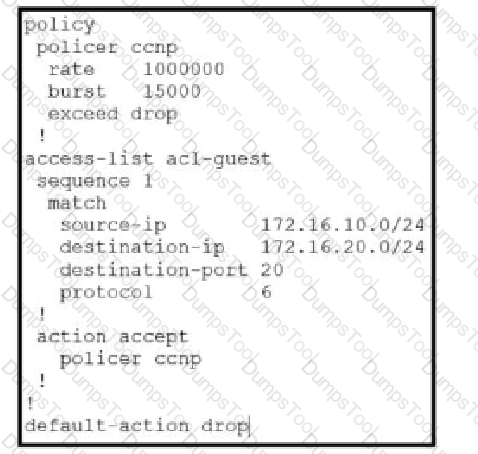
Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
An administrator is configuring the severity level on the vManage NMS for events that indicate that an action must be taken immediately. Which severity level must be configured?
An engineer configures policing with a rate of 125 Bps and a burst rate of 8000 bits, as shown here:
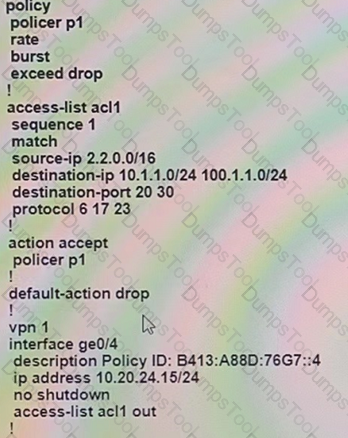
Which configuration completes this task?
What is the purpose of ‘’vpn 0’’ in the configuration template when onboarding a WAN edge node?
Which policy allows communication between TLOCs of data centers and spokes and blocks communication between spokes?
Drag and drop the functions from the left onto the correct templates on the right.
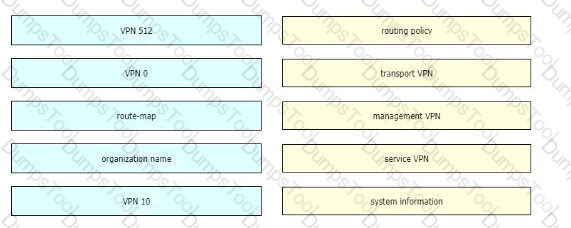
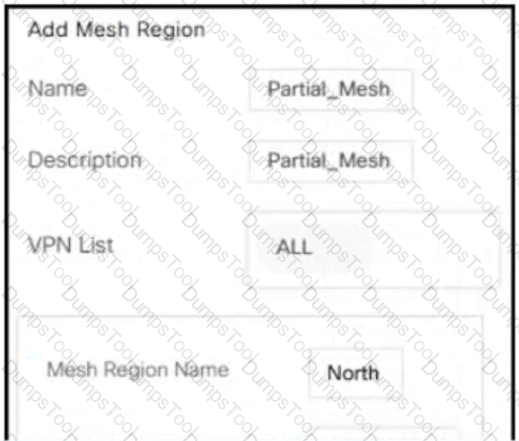
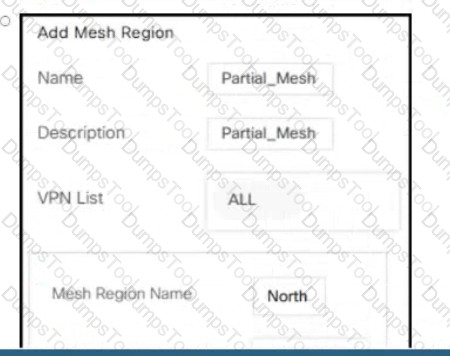
In a customer retail network with multiple data centers, what does the network administrator use to create a regional hub topology?
A network administrator configures SNMPv3 on a Cisco WAN Edge router from CLI for monitoring purposes How many characters are supported by the snmp user
Drag and drop the steps from the left into the sequence on the right for a WAN Edge router after powering on for zero touch provisioning.

Which two REST API functions are performed for Cisco devices in an overlay network? (Choose two)
Refer to the exhibit.
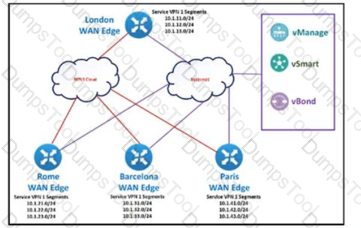
The SD-WAN network is configured with a default full-mesh topology. The SD-WAN engineer wants the Barcelona WAN Edge to use MPLS TLOC as the preferred TLOC when communicating with Rome site. Which configuration must the engineer use to create a list to select MPLS color toward the Rome TLOC?
A)
B)
C)

D)
What is the minimum Red Hat Enterprise Linux operating system requirement for a Cisco SD-WAN controller deployment via KVM?
Refer to the exhibit The network team must configure application-aware routing for the Service VPN 50.0.0.0/16 The SLA must prefer MPLS for video traffic but the remaining traffic must use a public network What must be defined other than applications before the application-aware policy is create?
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI?
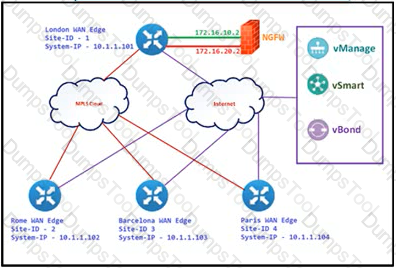
Refer to the exhibit. The Cisco SD-VYAN is deployed using the default topology. The engineer v/ants to configure a service insertion policy such that all data traffic between Rome to Paris is forwarded through the NGFW located in London. Which configuration fulfills this requirement, assuming that the Sen/ice VPN ID is 1?
A)

B)

C)
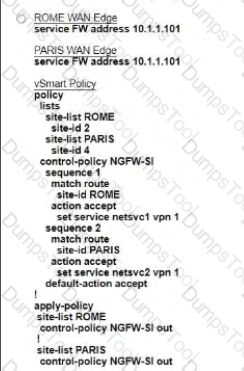
D)

Drag and drop the steps from the left into the order on the right to upload software on vManage repository that is accessible from maintenance > Software Repository.

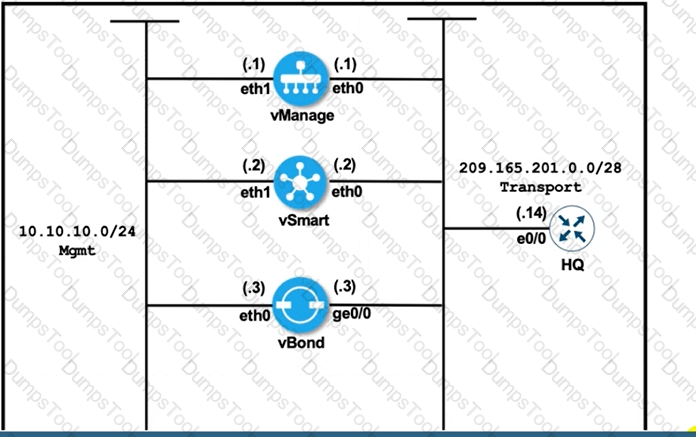
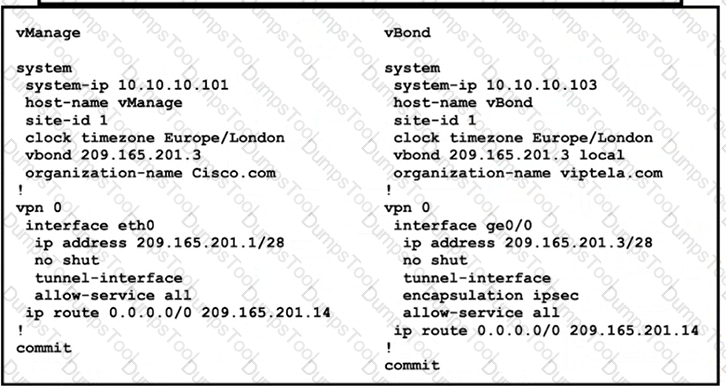
Refer to the exhibit vManage and vBond have an issue establishing a connection with each other Which action resolves the issue?
Which hardware component is involved in the Cisco SD-WAN authentication process for ISR platforms?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
Drag and drop the devices from the left into order on the right to upgrade the software from version 19 to version 20.
A large retail organization decided to move some of the branch applications to the AWS cloud. How does the network architect extend the in-house Cisco SD-WAN branch to cloud network into AWS?
Refer to the exhibit. An engineer must block FTP traffic coming in from a particular Service VPN on a WAN Edge device Which set of steps achieves this goal?
When software is upgraded on a vManage NMS, which two image-adding options store images in a local vManage software repository? (Choose two.)
The Cisco SD-WAN engineer is configuring service chaining for a next-generation firewall located at the headquarters. Which configuration creates the service?
A)
B)
C)
D)
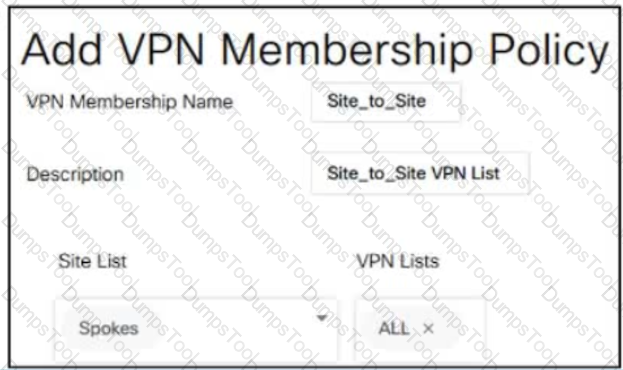
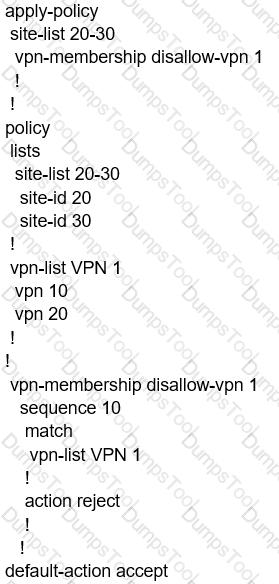
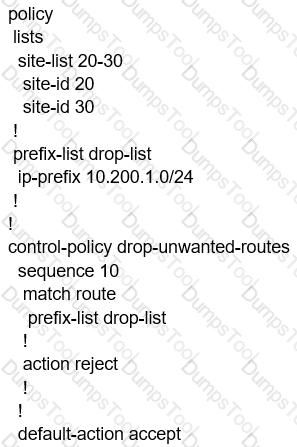
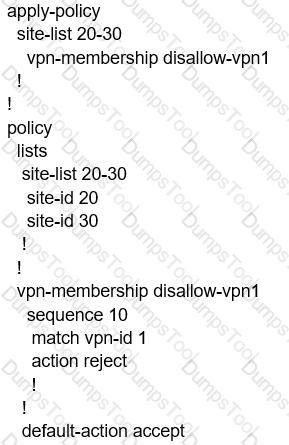
When the VPN membership policy is being controlled at the vSmart controller, which policy disallows VPN 1 at sites 20 and 30?
A)
B)
C)
D)
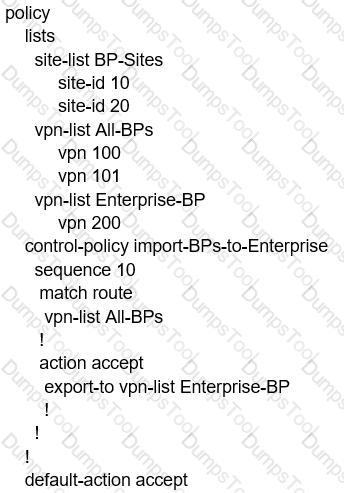
Refer to the exhibit.

vManage and vSmart have an issue establishing a connection to vBond. Which configuration resolves the issue?
An engineer wants to track tunnel characteristics within an SLA-based policy for convergence. Which policy configuration will achieve this goal?
Refer to the exhibit.
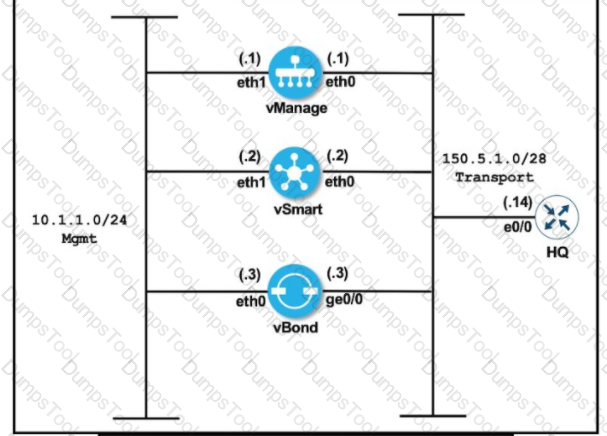

An engineer is troubleshooting an issue where vManage and vSmart have a problem establishing a connection to vBond. Which action fixes the issue?
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
An engineer is troubleshooting a vEdge router and identifies a “DCONFAIL – DTLS connection failure” message. What is the problem?
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
Which hardware component is involved in the Cisco SD-WAN authentication process for ISR platforms?
A network administrator is tasked to make sure that an OMP peer session is closed after missing three consecutive keepalive messages in 3 minutes. Additionally, route updates must be sent every minute. If a WAN Edge router becomes unavailable, the peer must use last known information to forward packets for 12 hours. Which set of configuration commands accomplishes this task?

How should the IP addresses be assigned for all members of a Cisco vManage cluster located in the same data center?
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%. otherwise MPLS should be used Which configuration wizard fulfils this requirement?
A network administrator configures SNMFV3 on a Cisco WAN Edge router from CL I for monitoring purposes How many characters are supported by the snmp user username command?
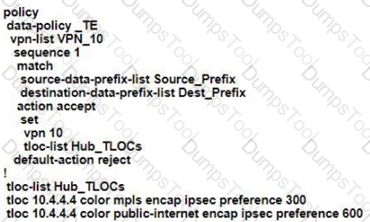
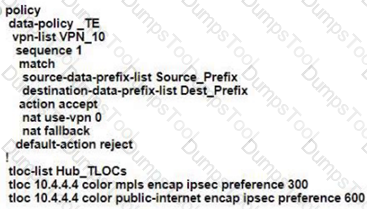
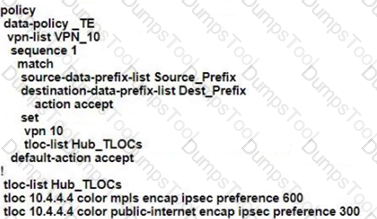
An engineering team must prepare a traffic engineering policy where an MPLS circuit is preferred for traffic coming from the Admin VLAN Internet should be used as a backup only. Which configuration fulfill this requirement?
A)
B)
C)
D)
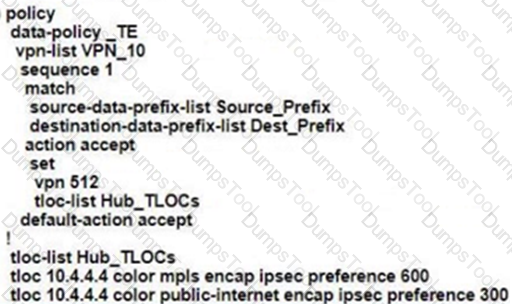
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality?
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer?
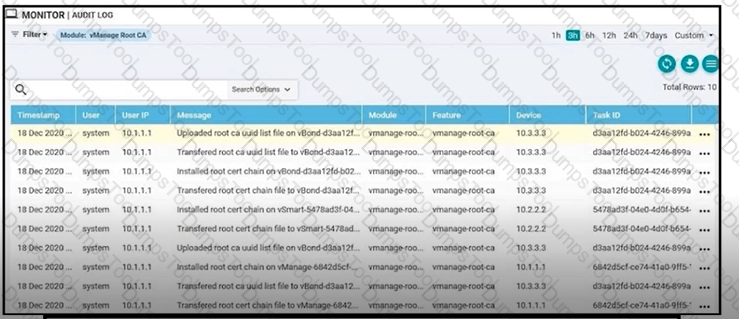
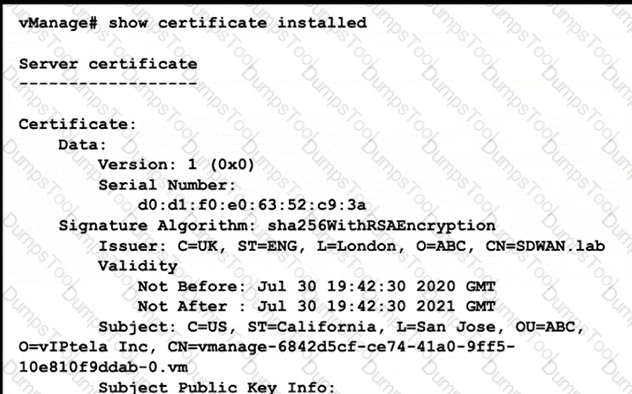

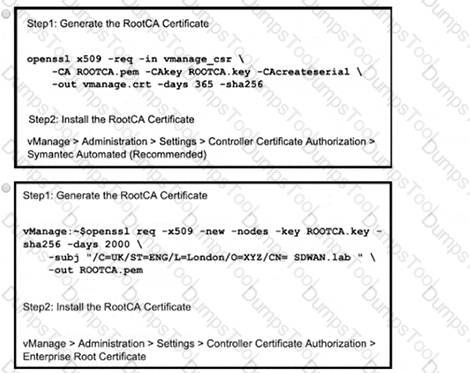
Refer to the exhibit A small company was acquired by a large organization As a result, the new organization decided to update information on their Enterprise RootCA and generated a new certificate using openssl Which configuration updates the new certificate and issues an alert in vManage Monitor | Events Dashboard?
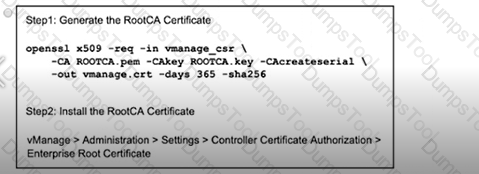

Which protocol is used for the vManage to connect to the vSmart Controller hosted in Cloud?
What is an advantage of using auto mode versus static mode of power allocation when an access point is connected to a PoE switch port?
Which protocol detects path status (up/down), measures loss/latency/jitter, and measures the quality of the IPsec tunnel MTU?
Refer to exhibit.

An engineer is troubleshooting tear down of control connections even though a valid Certificate Serial Number is entered Which two actions resolve the Issue? (Choose two)
What are the two impacts of losing vManage connectivity to fabric in the Cisco SD-WAN network? (Choose two)
On which device is a service FW address configured to Insert firewall service at the hub?
Which two mechanisms are used to guarantee the integrity of data packets in the Cisco SD-WAN architecture data plane? {Choose two)